KB ID 0001781
Problem
Imagine the following scenario, you have a PUBLIC web server and it’s either in the same network your uses are or attached to a DMZ on your FortiGate.

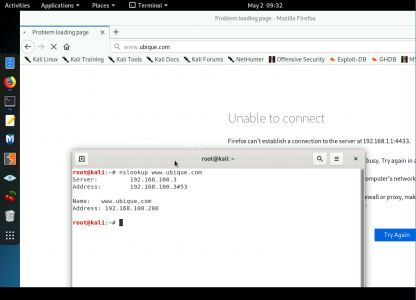
So above our users open a web browser and attempts to go to www.ubique.com (1) Their PC will do a DNS lookup for www.ubique.com and (in this case) a public web server returns an ip of 192.168.100.200 (2). The browser then attempts to HAIRPIN to that IP which is external to your FoirtiGate and the traffic is blocked.
FortiGate Hairpin Solution
If you have internal DNS servers you can of course solve this problem with Split DNS with a Cisco firewall, you could also solve this problem with DNS Doctoring, In fact if your from a Cisco background then even the name Hairpin is confusing because in Cisco when we mention Cisco Hair pinning we are usually talking about VPN traffic. Anyway I digress.
So to replicate the scenario above, i.e. it being broken on my LAN PC, I cannot browse to that site, and you can see my DNS is resolving to its public IP.
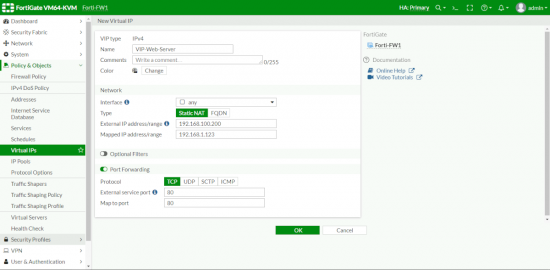
Polices and Objects > Virtual IPs > New > Virtual IP > Give it a Name > Interface = any > Set External IP > Set Internal IP > Note: You don’t have to set port forwarding but I’m only using TCP 80 > OK.
I already Have a Virtual IP: If your existing web server already has a Virtual IP object MAKE SURE it’s NOT bound to the outside interface, (or you won’t be able to select it in a minute). If you can’t edit it (because it’s in use), then you might need to remove it from the existing policy, and recreate it.
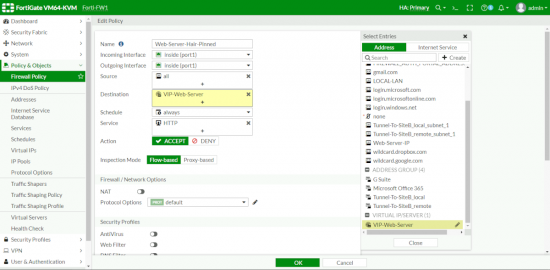
Policy and Object > Firewall Policy > Create New > Give the Policy a Name > Set the incoming and outgoing interface to the internal one > Source = All > Destination > the Virtual IP you just Created > Schedule = always > Service = HTTP > Disable NAT > OK.
I can’t see Virtual IP in the Policy: Then it’s either bound to an interface that ISN’T the inside one, or you have Central NAT enabled. If you don’t want to change your global NAT policy create an address object for the internal IP and use that instead.
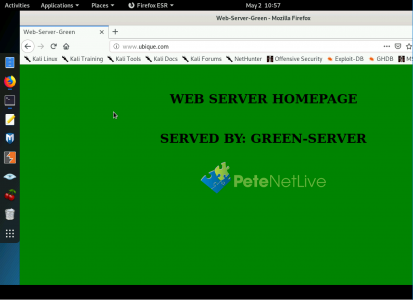
Now the website should work
Related Articles, References, Credits, or External Links
NA

25/08/2023
Thanks Pete, I found this helpful. I need to implement this but the server is on a different subnet from my user, I’ve tried a couple of variations but could not get it to work, any ideas?
User is on vlan1, server is on vlan 10 and has a public address.
06/10/2023
Hello Pete, one vicious caveat that took me an afternoon to debug.
If you use policy route it will break hairpint nat in the context of accessing internal ressources from a different internal sunet.
There is a KB that explains what to do if you are in this situation and don’t understand why hairpin nat doesn’t work for you (and the solution is a mindtwister)
https://community.fortinet.com/t5/FortiGate/Troubleshooting-Tip-Application-inaccessible-through-NAT-hairpin/ta-p/247040
20/10/2023
ThanQ