KB ID 0001113
Problem
Cisco DNS doctoring is a process that intercepts a DNS response packet as it comes back into the network, and changes the IP address in the response.
Why Would you want to do this? Well lets say you have a web server on your network, and its public IP is 111.111.111.111, and on your LAN its internal IP address is 192.168.1.100, its public DNS name, (or URL) is www.yoursite.com. When a user types www.yoursite.com into their browser, DNS will respond with the public IP of 111.111.111.111, and not the IP address thats on your LAN (192.168.1.100). The client can’t send the traffic out of the firewall, ‘hairpin’ it though 180 degrees and send the traffic back in again. So it fails. What DNS does is look for DNS response packets that have 111.111.111.111 in them and dynamically changes the ip in the packet to 192.168.1.100.
Are there any prerequisites? Only that the DNS server sending the response sends it response though the ASA, i.e. if you have your own DNS server onsite that serves the request (without a forward lookup or a root hint). then the DNS response does not go though the ASA so it can’t doctor it. This happens if you public website and your internal domain have the same name, or if your DNS server is authoritative for a domain with an IP address outside your network. To solve that problem your best bet is to setup ‘Split DNS’
How to Setup DNS Doctoring
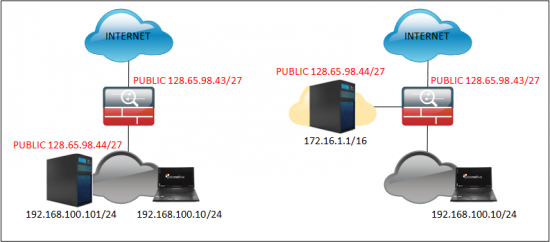
If you read the preamble you know that the DNS response needs to go though the firewall, and the public IP that gets resolved needs to be on your network. This can be either a host on your network with a public IP, or a host in your DMZ that has a public IP (both examples are shown below).
It takes longer to explain what DNS doctoring is, than it does to actually set it up. Essentially you simply add the ‘dns’ keyword to the end of the static nat statement for the internal host to its public address.
Option 1 – DNS Doctoring for a host on your LAN
This is simply a one-to-one static nat with the dns keyword added onto it, so using the example above (on the left), lets take a look at our NATs.
Petes-ASA# show run nat
!
object network obj_any
nat (inside,outside) dynamic interface
object network Obj-Static-128.65.98.44
nat (inside,outside) static 128.65.98.44
You may have a lot more output, but this tells me theres a dynamic NAT for all network traffic (PAT everything to the outside interface dynamically). And a static translation for your internal host, that’s the one we need to add the dns keyword to.
Petes-ASA# configure terminal Petes-ASA(config)# object network Obj-Static-128.65.98.44 Petes-ASA(config-network-object)# nat (inside,outside) static 128.65.98.44 dns Petes-ASA(config-network-object)# exit Petes-ASA(config)# write mem Building configuration... Cryptochecksum: de650019 1f1583f7 70121512 e1d093e8 15724 bytes copied in 3.430 secs (5241 bytes/sec) [OK] Petes-ASA(config)#
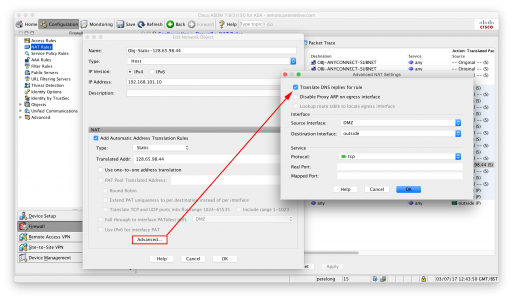
How Do I Set Up DNS Doctoring In The ASDM?
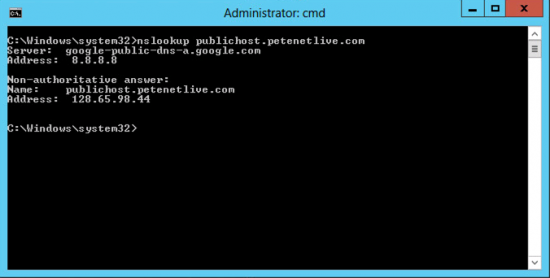
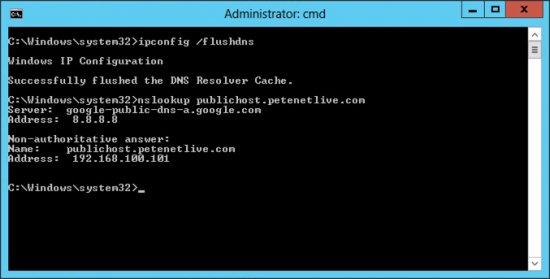
Testing DNS Doctoring
Heres an example of what happened before we setup DNS doctoring, (or where DNS doctoring is not working).
And once its been configured do the same and note the difference;
Option 2 – Host in the DMZ
The process is identical to above only the NAT stamens is different, i.e.
Note: I’m assuming the object host already exists, if NOT then add the line in BLUE.
Petes-ASA# configure terminal Petes-ASA(config)# object network Obj-Static-128.65.98.44 Petes-ASA(config)# host 172.16.1.1 Petes-ASA(config-network-object)# nat (DMZ,outside) static 128.65.98.44 dns
Option 3 – Split DNS
Windows – Setting Up Split DNS
Related Articles, References, Credits, or External Links
Original Article Written 09/12/15

18/10/2016
Is there a means to do this when your public IP is issued via DHCP? I can’t seem to find a way to either hairpin or DNS doctor when accessing a the resources of a server on the same interface as the client when using the public IP.
Thanks!
20/10/2016
Pretty sure you CANT do this if you are port forwarding from DHCP. There is no mechanism for the ASA to re-write an address that its obtained automatically. This process is for Static One-To-One NAT translations only. Your only option would be internal DNS.
P
05/02/2018
Yes it does require the dns keyword because;
>>provided by public DNS service
Would give the internal clients 64.128.192.x as the IP address and connections would fail