KB ID 0001420
Problem
Ah certificates! If I had a pound for every time I’ve heard “I don’t like certificates”, I could retire! The following run through is broken down into the following parts;
- Setup the Cisco WLC (WLAN)
- Setup NAP (RADIUS).
- Setup Certificate Auto Enrolment.
- Setup Group Policy to Deliver the Wireless Settings.
Note: If you are scared of certificates, sometimes it’s easier to setup password (PEAP) Authentication, get that working then migrate to EAP-TLS, but I’ll leave that to you.
Setup The Cisco WLC (WLAN)
I’m assuming your WLC is deployed, and working, and all your AP’s are properly configured, we are simply going to add a RADIUS Server and configure a new wireless LAN to use that RADIUS server for authentication.
WLC RADIUS Setup
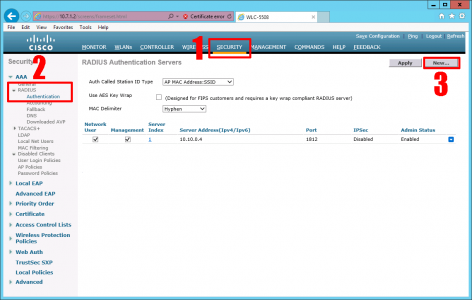
Log into the WLC web console > Security > AAA > RADIUS > authentication > New.
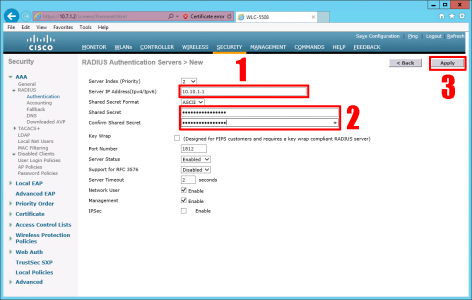
Specify the IP address of the RADIUS server and a shared secret (you will need to enter this on the Windows RADIUS server, so write it down!) > Apply.
WLC WLAN Setup
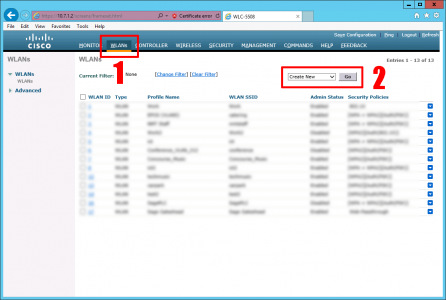
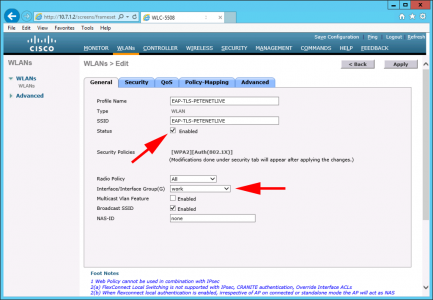
WLAN > Create New > Go.
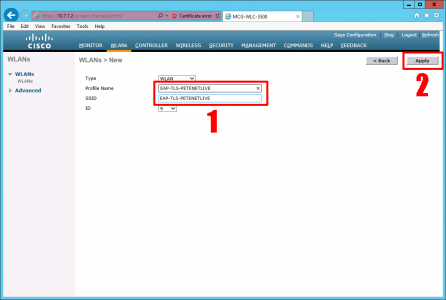
Specify a profile name, and SSID for the new WLAN > Apply
Edit your new WLAN > Select enabled. If your WLC has many VLANs/Interfaces select the one you want your wireless clients to egress on. Note: you can also turn off SSID broadcast if you wish, remember your GPO will need an additional setting if you do this.
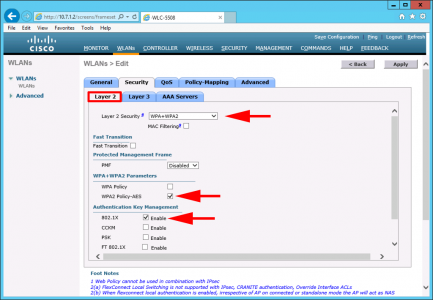
Security > Layer 2 >Set the following;
- Layer 2 Security: WPA+WPA2
- WPA +WPA2 Parameters: WPA2 Policy-AES
- Authentication Key Management: 802.1x
Security Tab > AAA Servers.
- Authentication Servers: Enabled
- Server1: {Your RADIUS Server}
- EAP Parameters: Enable
Note: You may wish to scroll down, and remove Local and LDAP authentication methods, but you dont have to.
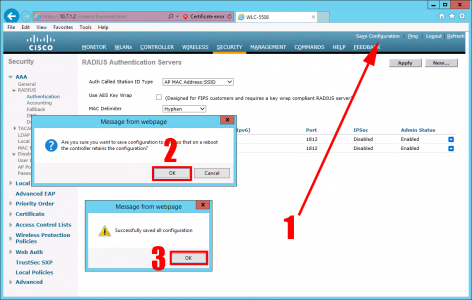
Click APPLY.
Save Configuration > OK > OK.
SETUP Windows NAP (RADIUS)
Network Access Protection is a server ‘Role‘, Launch Server Manager > Local Server > Manage >Add Roles and Features > If you get an initial welcome page, tick the box to ‘skip’ > Next > Accept the ‘Role based or feature based installation’ > Next > Next > Add ‘Network Policy and Access Server’ > Next > Add Features > Next > Next > Network Policy Server > Next Install.
Go and have a coffee, when complete open administrative tools ‘Network Policy Server.’ Right click NPS > Register server in Active Directory.
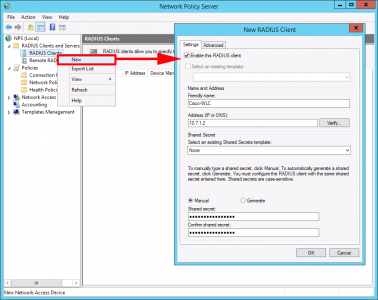
Radius Clients > New > Enter a friendly name >Enter the IP address of the WLC > Enter, and confirm the shared secret you used above > OK.
Note: This may be a different IP to the management IP of the WLC, ensure you enter the correct IP that the AAA requests will be coming from.
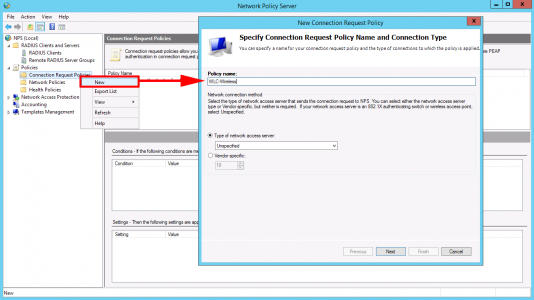
Connection Request Policies > New > Give it a sensible name > Next.
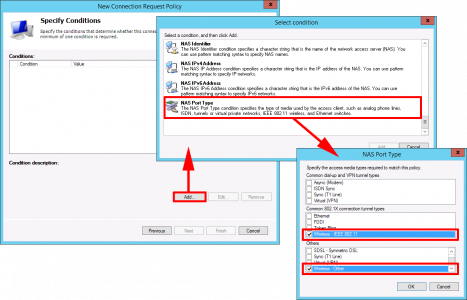
Add > NAS Port Type > Wireless- IEEE 802.11 > Wireless Other > OK > OK.
Note: You don’t actually need ‘Wireless other’, I usually add it for Meraki and it’s force of habit.
Next > Next > Next.
Next > Finish.
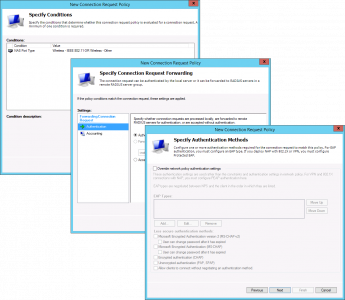
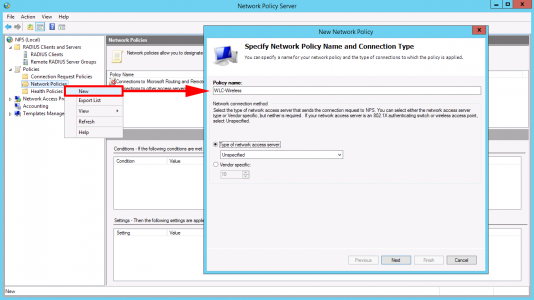
Network Polices> New > Give it a sensible name > Next
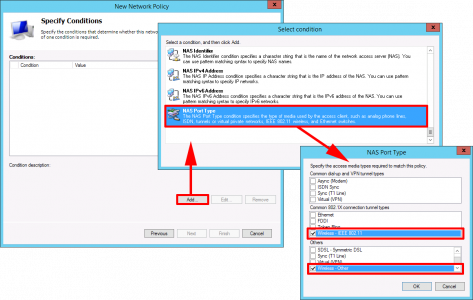
Add > NAS Port Type > Wireless- IEEE 802.11 > Wireless Other > OK > OK.
Note: You don’t actually need ‘Wireless other’, I usually add it for Meraki and it’s force of habit.
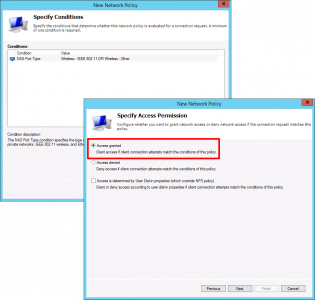
Next > Access granted > Next.
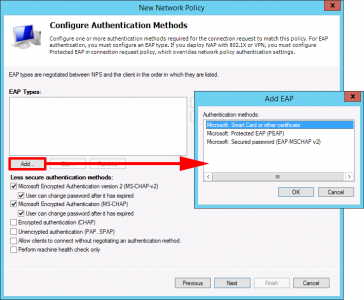
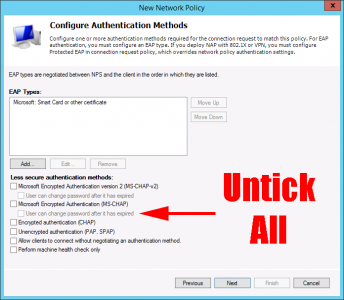
Add > Microsoft Smart Card or Other certificate > OK
Note: If you wanted to use PEAP then then you would add this here instead!
Untick all the bottom options, (unless you are using PEAP, which would need MS-CHAP-v2) > Next.
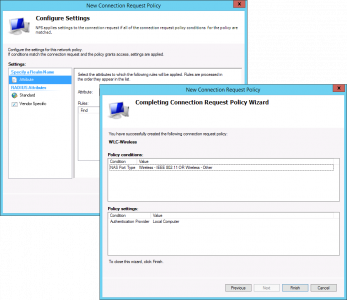
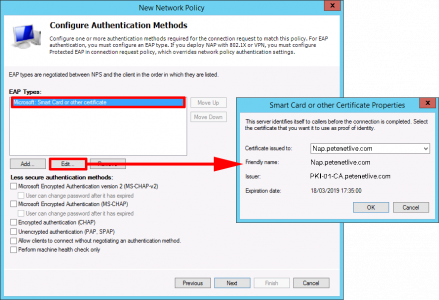
Edit > Ensure the certificate information for the NAP server is correct > OK > Next.
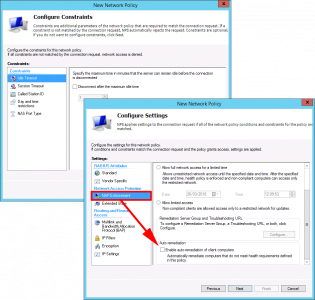
Next > Nap Enforcement > Untick ‘Enable auto remediation…’ > Next.
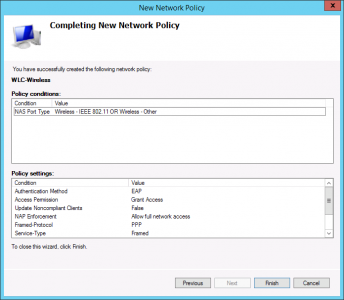
Finish.
Setup Certificate Auto Enrolment
Again I’m assuming you have a domain PKI/Certificate Services deployment already, if not, then follow the instructions in the post below;
Microsoft PKI Planning and Deploying Certificate Services
So rather than reinvent the wheel, I’ve already covered computer certificate auto enrolment, see the following article, then come back here when you are finished.
Deploying Certificates via ‘Auto Enrolment’
At this point: You might want to connect to the WLAN manually to make sure everything is OK before deploying the settings via GPO!
Deploy Wireless Settings via Group Policy
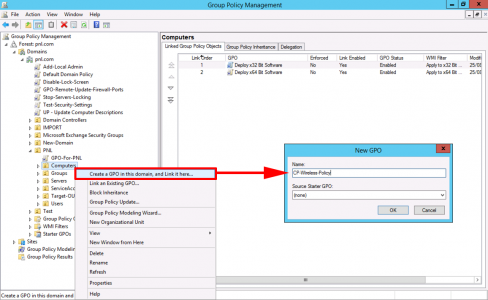
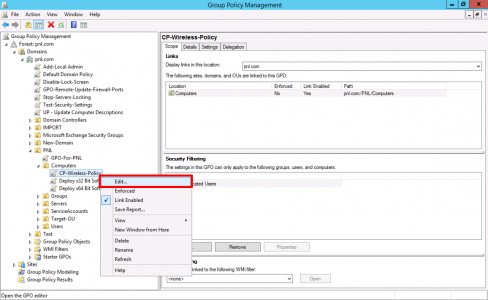
Remember this is a Computer Policy, so it needs to link to an OU that has computer (not user) in it, create and link a new GPO > then give it a sensible name.
Edit the GPO.
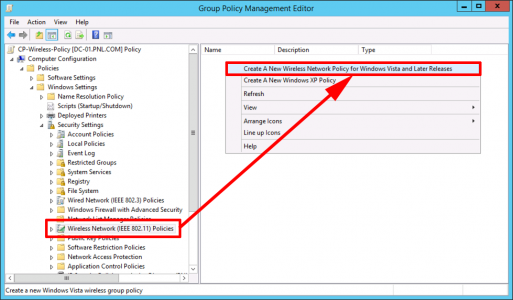
Navigate to: Computer Configuration > Policies > Window Settings > Security Settings > Wireless Network (IEEE 802.11) Policies > Create A New Wireless Network Policy for Windows Vista and Later Releases.
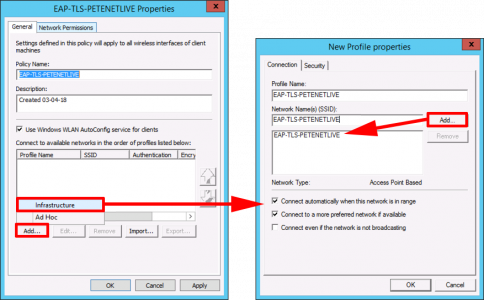
Give it a name > Add > Infrastructure > Supply the Profile name and SSID, (I keep them the same to avoid confusion).
Note: As mentioned above, if you are not Broadcasting the SSID, then also tick the bottom option also.
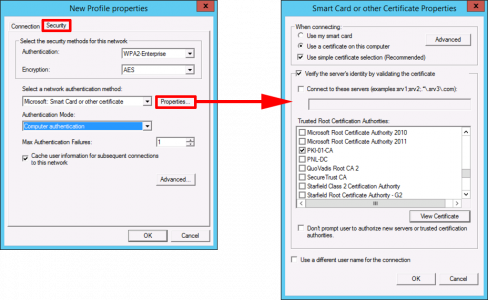
Security Tab: Authentication = WPA2 Enterprise > Encryption = AES > Change Authentication Method to Microsoft Smart Card or other certificate > Properties > In here you can choose to verify the NAP server via its certificate, if you do then locate and tick your CA server cert in the list (as shown). Though I do not ‘verify the servers identity…’ So I would untick this option (your choice) > OK > OK > Close the Policy Editor.
Then either wait fo the policy to apply for force it.
Windows – Forcing Domain Group Policy
Troubleshooting RADIUS Authentication
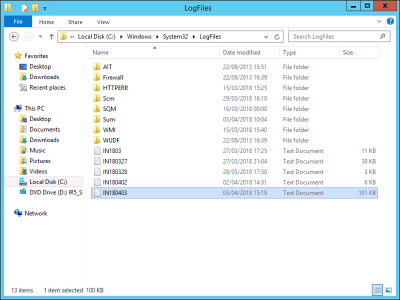
On the NAP server in C:\Windows\System32\Logfiles you can find the RADIUS logs they look like INI{number}
You can also use the Event Log (Security Log) and there’s a dedicated logging section under Windows Logs. In extreme cases install Wireshark on the NAP server and scan for traffic from your WLC
Related Articles, References, Credits, or External Links
Configure Wireless Network Stings via Group Policy


12/02/2019
Could you point me to configuring both the NPS/RADIUS server’s and the client’s certificate template that resides on my MS Server 2012R2? I’m pretty sure the other parts are correct, but I’m getting authentication errors on both my client and NPS, saying that there are problems with the certs.
12/02/2019
Just search the site for auto-enrollment and NAP RADUS, Ive covered these subjects (a lot)
P