KB ID 0000919
Problem
SHA CERTIFICATE WARNING: Note This article was written some time ago, ensure your CA environment does NOT use SHA1 for your certificates, if it does, Please visit the following link for migration instructions;
Upgrade Your Microsoft PKI Environment to SHA2 (SHA256)
I need to setup wireless authentication based on computer certificates, I’ve done similar jobs before by manually issuing certificates for Cisco AnyConnect, but this will be for NAP/RADIUS authentication to MSM. I’ll be working with Server 2008 R2 and Windows 7 clients. So task one was getting my head round ‘auto enrollment’. As stated I’m deploying Computer certificates but the process is practically the same for issuing User certificates (I’ll point out the differences where applicable).
Solution
Prerequisites: A Windows domain environment, with working DNS.
Setup a Certification Authority
1. Launch Server Manager (Servermanager.msc) Roles > Add Roles > Active Directory Certificate Services > Next > I’m going to accept all the defaults.
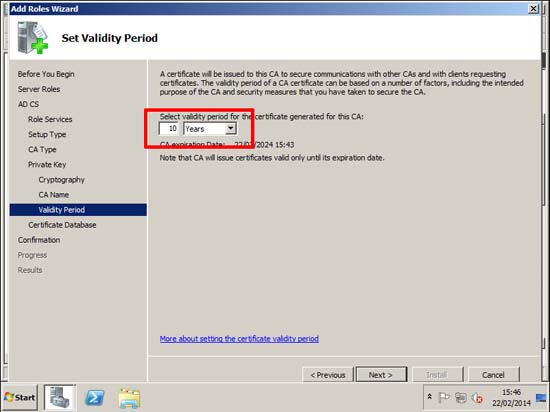
2. The only thing I’m going to change is the lifetime, I usually change that from 5 to 10 years (force of habit, after 5 years it will probably still be my problem, in 10 years it will be replaced, or in a skip!)
Create a Computer Certificate Template and Issue it.
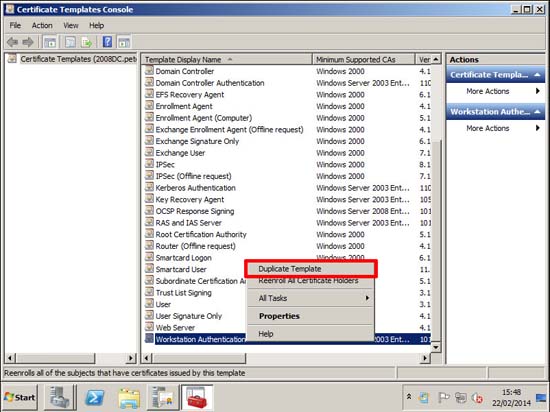
3. Start > Administrative Tools > Certification Authority > Certificate Templates > Manage.
4. Locate and make a copy of the Workstation Authentication template. If you were using User certificates the you would copy the User template.
Note: I got an email a few months ago form someone who had an argument about whether to make copies or edit the originals, and was asking what I thought was best practice. Well I would ALWAYS copy a template and edit that copy. Then if you ‘stuff it up’ you still have the original. It’s always best practice to avoid looking like a cretin!
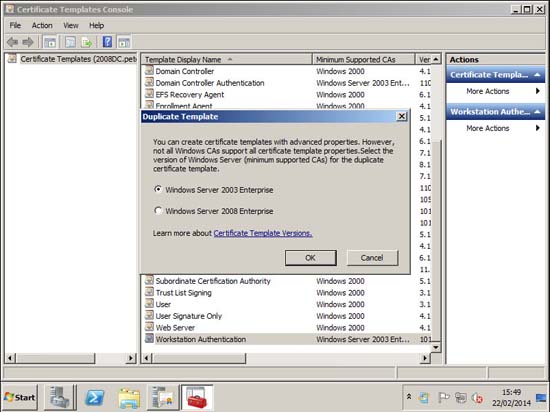
5. If you still have Server 2003 servers choose the default, if not pick 2008 > OK.
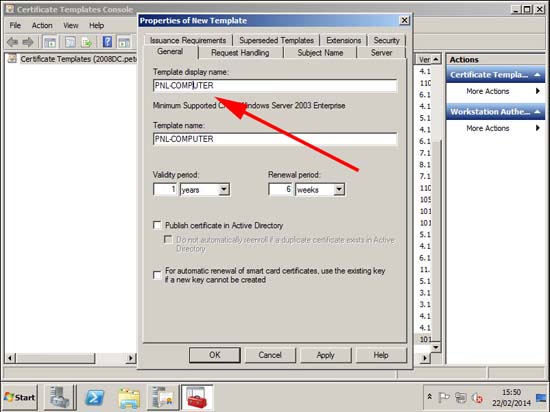
6. General Tab > Give the template a sensible name.
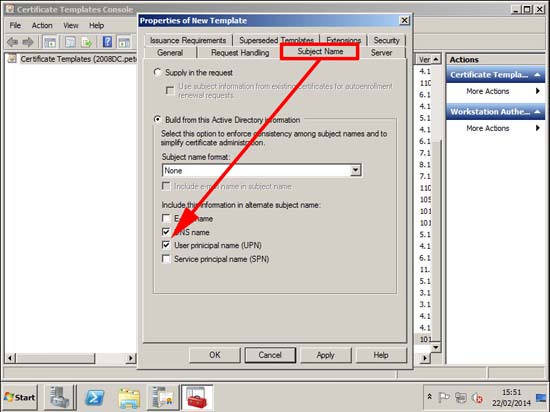
7. Subject Name Tab: Tick User principle name (UPN).
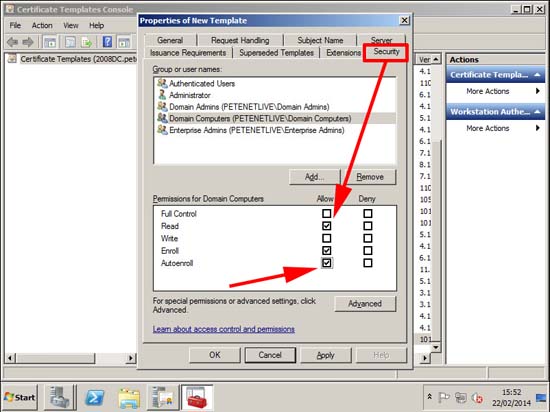
8. Security Tab: Ensure Domain Computers have the rights to Read and Autoenroll > OK > Close the template console.
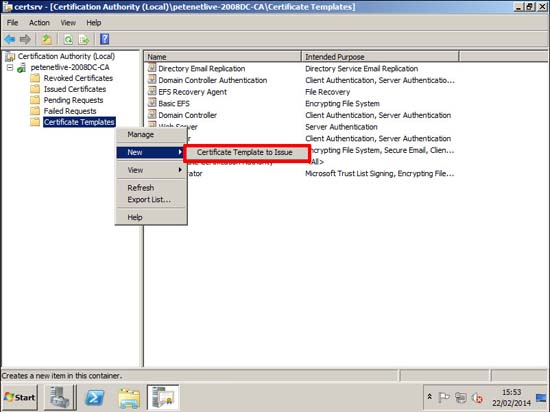
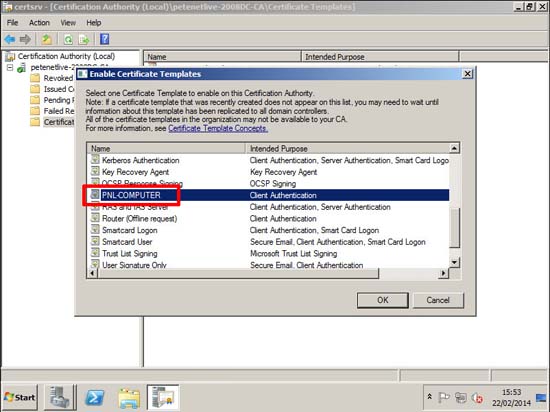
9. Certificate templates > New > Certificate Template to Issue.
10. Pick the one you just created > OK.
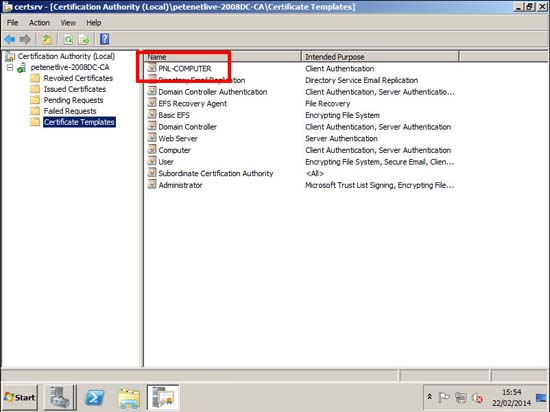
11. Make sure it’s listed > Close the Certificate Authority management console.
Deploy Auto-enrolled Certificates via Group Policy
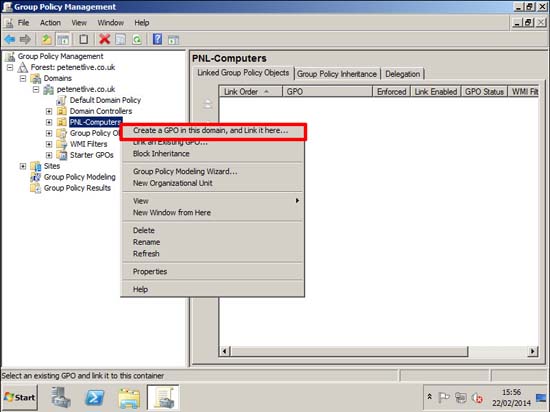
Note: You could just add this to the to the default domain group policy, and all computers would get a certificate, but for this exercise I’ve created an OU, and I’m going to create a new policy and link it there.
12. Select an OU or container that contains the computer objects you want to send certificates to.
Note: Obviously if you are sending out User certificates then link it to a user OU, (you would be surprised!)
13. Navigate to;
Computer Certificate Auto-Enrollment Computer Configuration > Windows Settings > Security Settings > Public Key Policies > Certificate Services Client - Auto-Enrollment User Certificate Auto-Enrollment User Configuration > Windows Settings > Security Settings > Public Key Policies > Certificate Services Client - Auto-Enrolment
WARNING: If deploying user certificates read this article.
14. Enable the policy > Select the two options available > Apply > OK > Close the GPO management editor.
Test Windows Certificate Auto-Enrollment
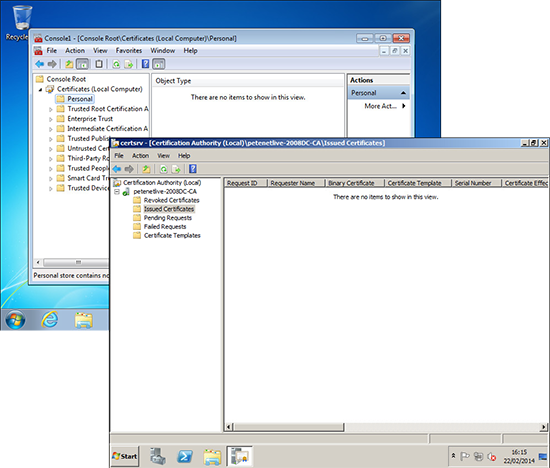
15. Before we do anything else, you can see there are no certificates on the Windows 7 client machine, and there are no certificates ‘issued’ from the server.
Note: To see a computers certificates, you need to be logged in with administrative rights, run mmc and add in the certificates snap-in for ‘local computer’.
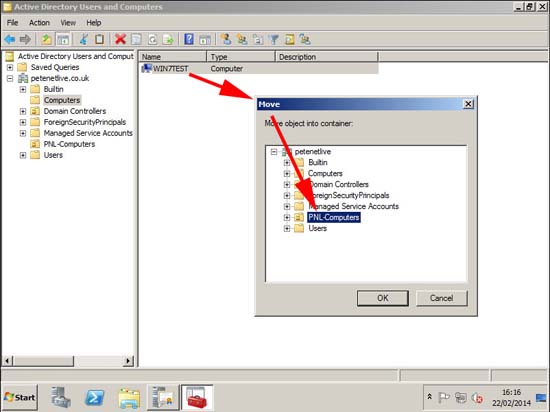
16. Now if I move this machine into the OU that I’ve linked the GPO to.
17. And then force that client to refresh its group policies, (or reboot it).
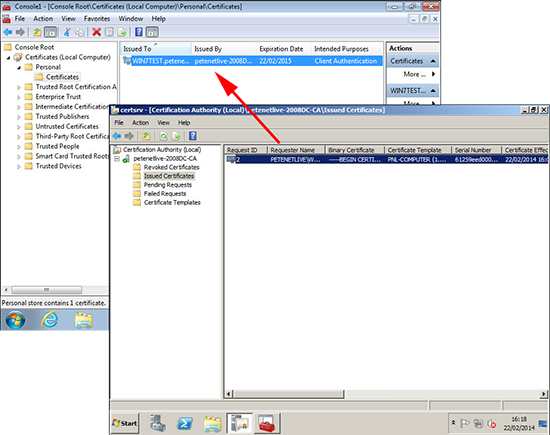
18. Now when you check, you can see it has received a certificate, and the server is now showing one certificate issued.
Now I’ve got to work out NAP and RADIUS and force them to use the certificates, but I’ve got a headache and I need a brew, watch this space….