KB ID 0001250
Problem
A client had moved a domain joined server into their DMZ, and while they had opened the correct ports for Domain Authentication on their firewall, no one had considered the certificates on the server which had expired, and could not be renewed.
Some research, pointed me towards Certificate Enrolment Web Service. Its job is to let clients enrol and renew certificates, from either non domain joined machines, or machines that cannot contact your PKI environment. This was just what I needed, I just need to test the concept. So I built a domain, setup a CA, and a DMZ (with the same firewall as my client, a Cisco ASA). Then moved a domain client into the DMZ, domain authentication as setup as follows;
Cisco ASA – Allowing Domain Trusts, and Authentication
Solution
Before starting I would suggest creating a ‘service account’ to run the enrolment service, you need to be an admin to install the services but this account does not need to be. (It does need to be in the LOCAL IIS_USERS group on your CES/CEP server(s)). Below you will see I’ve named my user svc_ca.
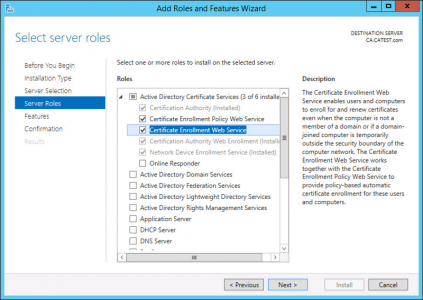
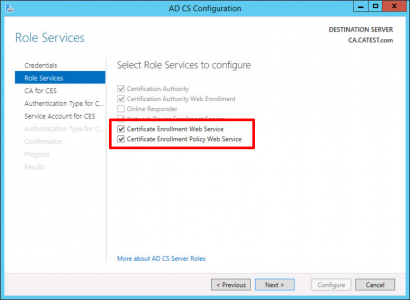
You need to already have a PKI/CA setup. You can split the CES ‘Web Service’ and CEP ‘Policy Web Service’ across different hosts if you want, but for this example I’m simply putting both roles on the same server.
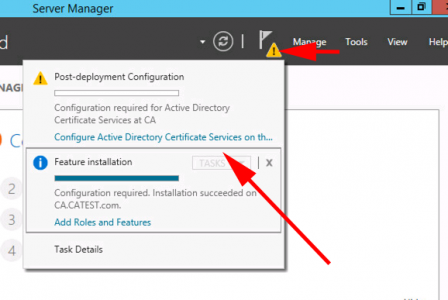
Then you need to run the post deployment configuration.
Again I’m configuring both roles at the same time.
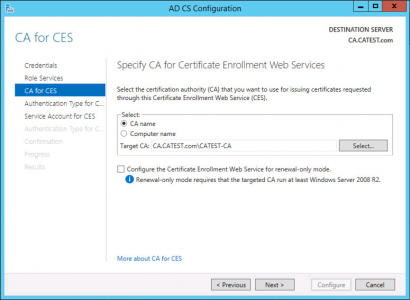
I’ve only got one, but choose the CA server on which to house the CES role.
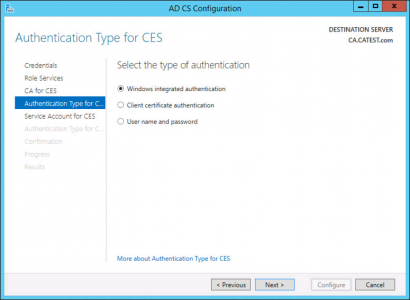
As I mentioned above, I’m using Windows authentication, if you are deploying certs to a DMZ, yours may be better set to username/password.
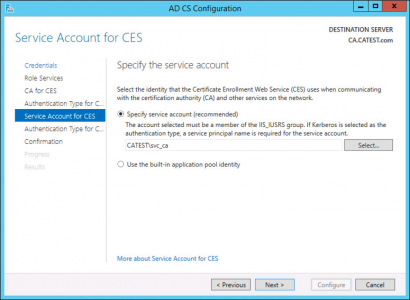
Specify your service account, you created earlier.
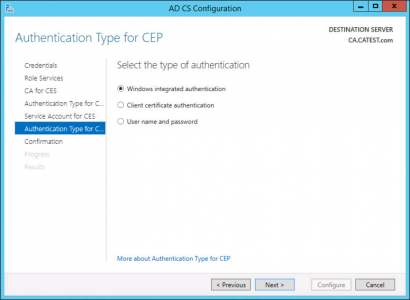
Again choose your authentication method.
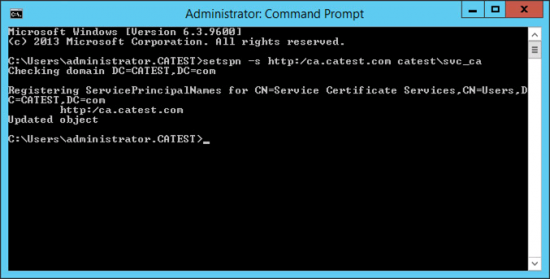
Now you need to create a ‘Service Principle Name’ SPN for your service account, that’s tied to your Certificate Enrolment Web Services server. Open an Administrative Command Window on the CES server and issue the following command;
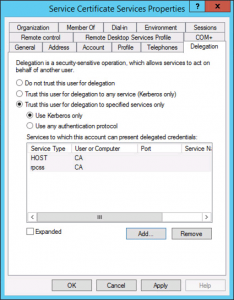
Now your user has an SPN, they will get another ‘Tab’ on their user object, called ‘Delegation‘ Add in the CES server for the following service types.
- HOST
- rpcss
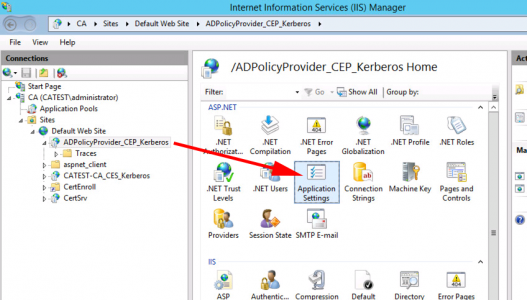
On your certificate enrolment policy server, open the Internet Information Servers (IIS) Management console. Expand {Server-Name} > Sites > Default Web Site > ADPolicyProvider_CEP_Kerberos > Application Settings.
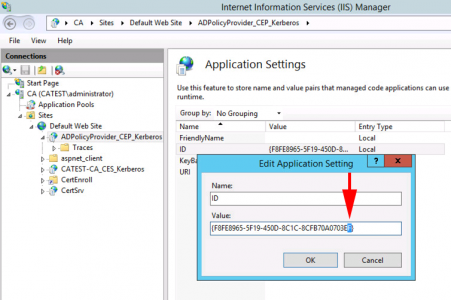
Locate the Friendly Name section > Locate the ‘Value‘ > Change its last hexadecimal character (0 to 9 or A to F) from what it is currently > OK.
Open an Administrative Command Window > Issue an IISRESET command.
Setup Enrolment Policies
To actually use the CES/CEP service your client needs to know where it is, there are TWO methods of letting them know, you can either use the certificate snap-in, or use a ‘Local Group Policy’ on the target machines.
Managing Enrolment Policies With Certificates Snap-In
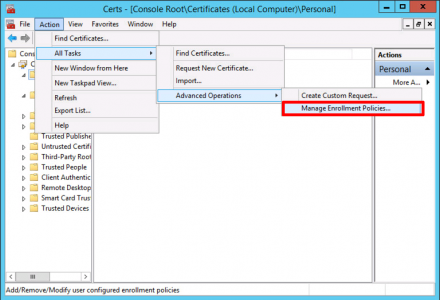
Windows Key+R > MMC {Enter} > File > Add/Remove Snap-In > Certificates > Local Computer > When the console opens > Action > All Tasks > Advanced Operations > Manage Enrolment Policies.
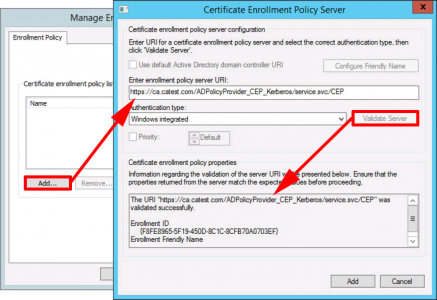
Add > Enter the URI of the CEP Server;
Note: To access via https, you may need to manually add a Web Server certificate for the URL/Common name of the CEP server. See the following article;
IIS: How to Create a Certificate Request
Validate Server > Add-
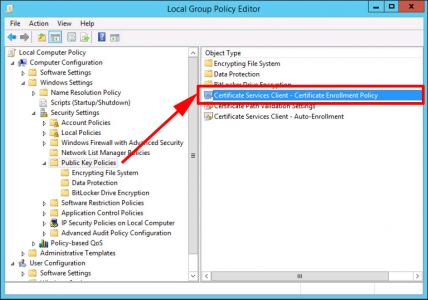
Managing Enrolment Policies With Certificates Local Group Policy
Windows Key+R > gpedit.msc {Enter} > Computer Configuration > Windows Settings > Security Settings > Public-Key Policies > Certificate Services Client – Certificate Enrolment Policy.
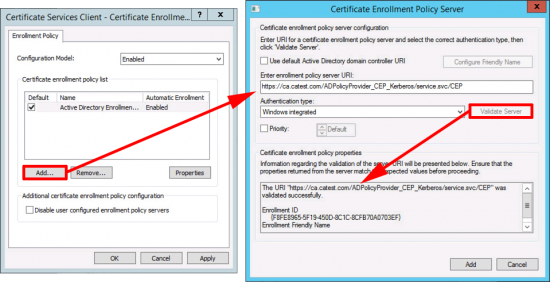
Add > Enter the URI of the CEP Server;
Validate Server > Add.
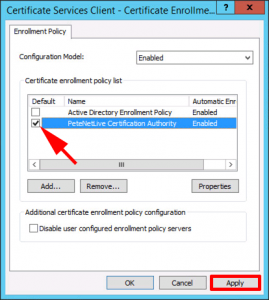
If you already have an Active Directory Enrolment Policy listed, make sure it’s NOT selected, and your newly created CES policy is set as default > Apply.
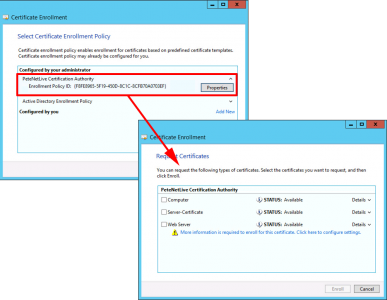
Enrol Or Renew Certificates From CES
Now if you attempt to enrol for a certificate, your machine will use the CES policy.
Related Articles, References, Credits, or External Links
URI Was Validated Successfully But there Was No Friendly Name Returned
Certificate Enrolment – URI This ID conflicts with an Existing ID


06/06/2019
After the line “Open an Administrative Command Window > Issue an IISRESET command.” Is that the correct screenshot?
07/06/2019
Good Spot – No it wasn’t, Fixed. ThanQ
11/11/2019
Your screen shot where you go into Application Settings and find the “Friendly Name”, the verbiage does not match the screen shot. I learned this because you really need to access the ID and change the GUID by a couple characters or you get an error similar to: “The URI entered above has ID: “{GUID}”. This ID conflicts with an existing ID.” The remedy is to change the ID of the Application in IIS per the screen shot but not per the copy above it.
12/11/2019
Updated – Thanks for the feedback, sorry if it caused you some Grief!
P
09/01/2020
Hi Pete;
I still see confusing information about the friendly name setting and the application GUID. BTW, I have learned you need to change the GUID for CEP/CES because it will default to the same GUID used by the default AD certificate enrollment policy.
07/08/2024
I have an issue at this point where there is no ID listed just URI and CAConfig.
Also it doesnt say Friendly name just Name. Thanks!!
11/11/2019
This document does not mention that an SSL certificate is required before you configure CEP, or you’re into the Bindings of IIS in general to select the SSL certificate you run out and get right after that section.
12/11/2019
Updated, ThanQ
27/11/2019
Thanks, PeteLong!
09/01/2020
Hey Pete;
One more thing for ya, and this could be a little piece of gold – If you use WS2016 as a CA and also want to use CEP/CES, CEP cannot handle a template with a CA compatibility above WS2012R2.
Learned this the really hard way.
10/01/2020
TopTip Thanks Beth!
22/06/2021
Pete, on your step where you set the SPN, your instructions omit the colon (:), however your screenshot includes the colon.
“setspn -s http/{FQDN-OF-Server} {Domain-Name}\{User-Name}”
23/06/2021
Well spotted thankQ
24/01/2023
From other MSFT Articles, this is a great post but has both services running on same node.. should CEP be separated as this indicates?
“If both CES and CEP are using Kerberos (Integrating authentication), then they cannot be installed on the same server, as simply there will be SPN collision (both using same IIS application pool, and same protocol). That is why we recommend installing them on separate machines.”
02/02/2023
I had no problems, but I’ll throw it open for comment 🙂
P