KB ID 0001689
Problem
Note: This WONT WORK if you ‘force-tunnel’ or ‘tunnel-all’ remote VPN traffic, (if you are unsure Google ‘what’s my ip’ > Take note of it > Connect to AnyConnect and repeat the procedure, if your public IP address has changed to the IP address of the ASA then you force-tunnel/tunnel-all traffic).
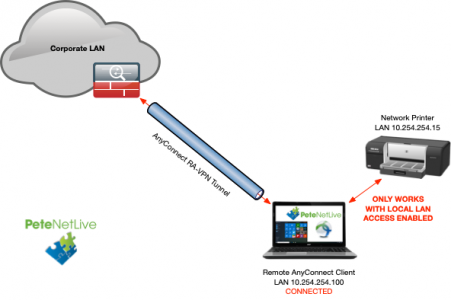
With more people remote working now, I’m getting a lot more questions about RA-VPN and particularly AnyConnect. By default when connecting to any Cisco remote access VPN, it pretty much stops you connecting to anything outside the VPN tunnel, (unless you enable Split Tunnelling). This includes stopping you talking to assets on your remote network also.
This is basically ‘Good practice’, as a corporate entity you have authenticated a remote machine NOT the entire network it is on! But what happens when your MD want to print a work document on his/her home printer? Or you have a NAS drive at home with documents on it you can access while connected to the VPN?
Well, then you can ‘make a judgement call’ to whether or not you want to enable ‘Local LAN Access’ for your remote clients.
Full Disclosure: While this does not let everything on the remote clients LAN connect to the corporate network. If another client on a remote network was infected and compromised, and it proliferated its infection via the LAN, (to your authenticated remote client), then that client could infect the corporate network. This is what’s known as a ‘pivot attack’.
Solution
Assuming you are happy to enable local LAN access its a TWO STEP procedure. Firstly you enable Local LAN Access on the AnyConnect Client Profile, then you enable split tunnelling and allow all networks, (because you don’t know what all the remote network addresses may be).
Step 1: Add Local LAN Access to the AnyConnect Client Profile
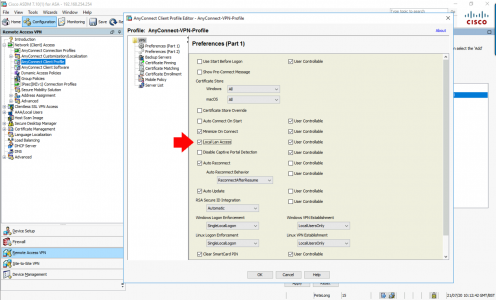
If you are unfamiliar with ‘AnyConnect Client profiles’, they are simply XML files that are applied to to an AnyConnect Connection Profile, I already have one so I just need to edit it, And tick ‘Local LAN Access’.
What If you Don’t Already Have One? Not a problem. In the ASDM > Configuration > Remote Access VPN > Network (Client) Access > AnyConnect Client Profile > Add > Give it a name > Set the Group Policy to your AnyConnect Group Policy > OK > Apply > Edit.
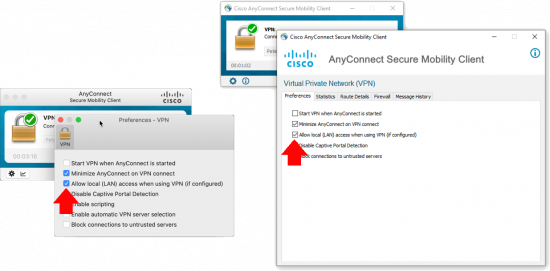
What Does User Controllable Mean? It means your users can enable or disable it, (see below.) If you untick this then they wont have that option.
Step 2: Add 0.0.0.0/32 to Split Tunnelling
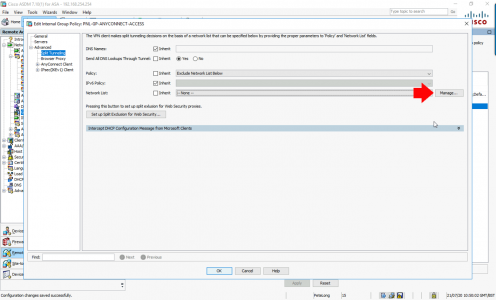
You configure split tunnelling in your AnyConnect Group-Policy (ASDM > Configuration > Remote Access VPN > Network (Client) Access > Group Policies) Locate yours and edit it, navigate to Advanced > Split Tunnelling > Policy: Untick inherit, and set to Exclude Network List Below > Network List: Untick Inherit and click Manage.
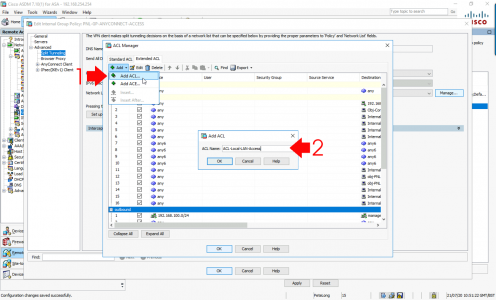
Firstly: Create an ACL and call it “ACL-Local-LAN-Access’ > OK
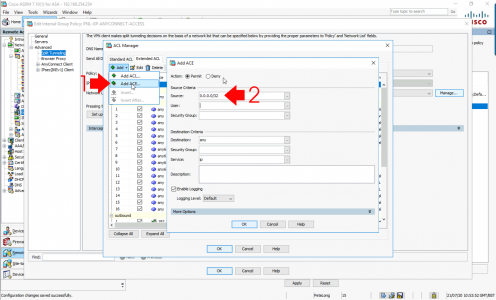
Secondly: Select the ACL you just created and add an ACE to it > permit 0.0.0.0/32 > OK > OK > OK > Apply > File > Save Running Configuration to Flash.
Your remote workers will need to disconnect and reconnect before it will take effect. In some cases with older clients they need to reboot, (or have the AnyConnect service stopped and restarted.) If you experience problems make sure your clients have got the new XML file with;
<LocalLanAccess UserControllable="true">true</LocalLanAccess>
inside it, to find out where those files are stored see THIS POST.
Related Articles, References, Credits, or External Links
NA

25/05/2022
Hello,
Is there a way to connect to the Local Lan of a remote Client if you are an administrator?
My idea would be to use the AnyConnect SSLVPN at special Location, and allow other AnyConnect Clients to connect to that special location LAN while they are connected to same VPN Tunnel-Group on the same ASA.
Thanks
In addition, the remote special client would have two NICs, and I would like to reach its subnet
on its secondary NIC.
26/05/2022
No really to get access to a a remote AnyConenct client typically you would use https://www.petenetlive.com/KB/Article/0001503 but that wont give you “remote LAN Access”
The only Cisco product that ever did that (without a site to site VPN) was EZVPN. https://www.petenetlive.com/KB/Article/0001261 but it’s old technology now.
24/02/2023
Also remote cisco wireless ap that tunnelled the wifi back from an untrusted network to the controller. For example:
wifiWP (broadcast Corp.WIFI)—-> wired to untrusted network with internet ->>>> (internet)—> Corp WLC
When a device joins the Corp.WIFI in a remote location, could be at a CEO home or temp office or customer site with permanent corp contractors for example, the wifi devices get corporate access.
I set this up for a CEO SOHO
30/09/2022
Hello Pete,
I have a problem with a RA VPN on Firepower 1010. the problem is that the remote users they have access on the LAN but they don’t have access on the Internet i want the remote users to access the internet through VPN. On the VPN settings the option split tunneling is ¨Allow all traffic over tunnel” but still they cannot access the Internet.
Please help me
30/09/2022
If it running ASA code then see this: https://www.petenetlive.com/KB/Article/0000977
If it’s running FTD code – wrap it in plastic and throw it in a skip (Sorry I can’t help there)
I’m guessing you’re missing a NAT statement my friend.
P
30/09/2022
It is running FTD code. Thank you for the reply