KB ID 0001503
Problem
With the newest version of AnyConnect (4.7) there’s an added feature called ‘Management VPN’. It’s there, so that if you have remote users who don’t VPN in very often, then you may struggle to mange them, e.g. put software updates, AV updates, SCCM packages etc. down to them.
Before version 4.7 you could configure ‘Automatically Connect’, or ‘Start before Logon’ to handle these problems, well now you can use Management VPN. What it does is, it automatically connects (using the computer certificate to authenticate), and it automatically disconnects when a remote user brings up a normalAnyConnect VPN user connection. When they disconnect again, the Management VPN (after a few seconds) will re-establish again.
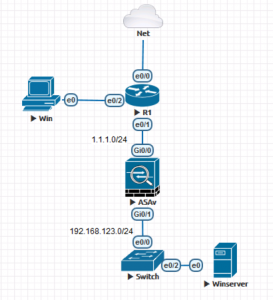
As usual the Cisco documentation is not brilliant! So I built it out in EVE-NG to test. Here’s the Lab I used;
I’ve got a Windows 2012 R2 Server that’s doing Certificate services and DHCP, I’ve also got an external (Windows 7) client with AnyConnect 4.7 installed.
Solution
My first task was to setup normal user AnyConnect, which I secured with certificates, (user certificates), I sent the certificates out using auto-enrollment. Also while I had my certificate hat on, I generated a certificate for the outside of the ASA as well. (I didn’t bother setting up NDES I just imported the CA Certificate eon the ASA).
Note: If you already have working AnyConnect, then you can skip this section.
Deploying Certificates via ‘Auto Enrollment’
Cisco AnyConnect – Securing with Microsoft Certificate Services
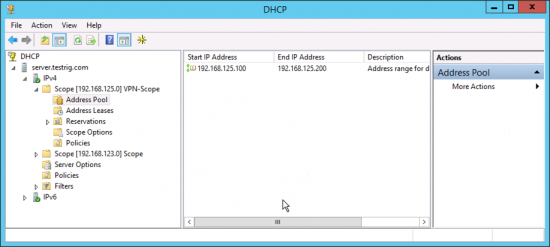
I’m also leasing my remote client’s IP addresses from my Windows DHCP server, so I’ve setup a DHCP scope on there as well (192.168.125.0/24)
As a pointer here is the config I’m using;
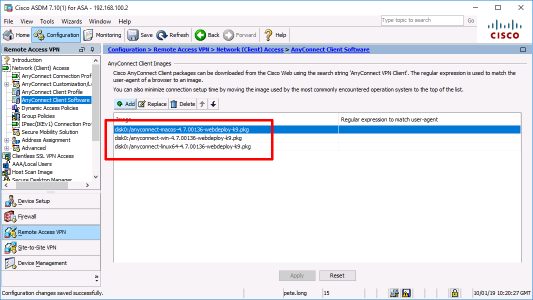
object network OBJ-AnyConnect-SN subnet 192.168.125.0 255.255.255.0 ! access-list SPLIT-TUNNEL standard permit 192.168.123.0 255.255.255.0 ! nat (inside,outside) source static any any destination static OBJ-AnyConnect-SN OBJ-AnyConnect-SN no-proxy-arp route-lookup ! webvpn enable outside anyconnect image disk0:/anyconnect-win-4.7.00136-webdeploy-k9.pkg 1 ! group-policy GP-AnyConnect internal group-policy GP-AnyConnect attributes wins-server none dns-server value 192.168.123.10 dhcp-network-scope 192.168.125.0 vpn-tunnel-protocol ssl-client split-tunnel-policy tunnelspecified split-tunnel-network-list value SPLIT-TUNNEL default-domain value testrig.com ! tunnel-group TG-AnyConnect type remote-access tunnel-group TG-AnyConnect general-attributes default-group-policy GP-AnyConnect dhcp-server 192.168.123.10 tunnel-group TG-AnyConnect webvpn-attributes authentication certificate group-alias TG-AnyConnect enable group-url https://vpn.testrig.com/AnyConnect enable
In addition, (much as I prefer to work at CLI, you need to go into the ASDM to do the following). Create a new connection profile and associate it with the group policy we just created (above).
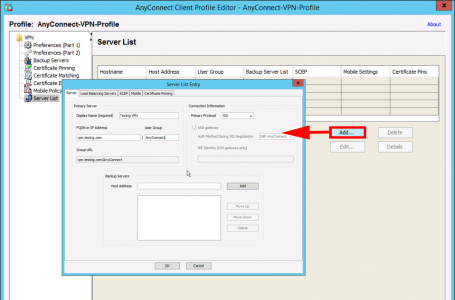
Add to the ‘Server list‘ the URL you specified (above).
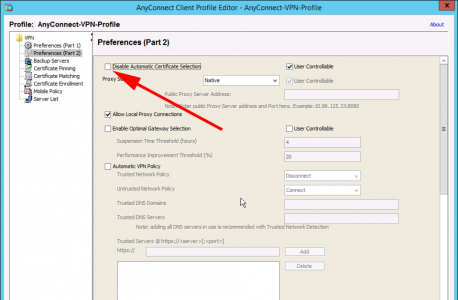
To avoid being prompted for which certificate to use, untick ‘Disable Automatic Certificate Selection’ (Yes the name makes no sense to me either!) Save the profile.
Then make sure the VPN works as expected.
Setup AnyConnect Management VPN
Prerequisites
Your ASA needs to be running newer than version 9, and your ASDM image needs to be 7.10(1) or newer.
You need to have the Anyconnect client software (4.7 or newer!)
I’ve already mentioned certificates, but you will need to have the CA certificate from the CA that’s generating your COMPUTER certificates installed and trusted, mine’s already there, as I’m already authenticating my USER certificates with it.
Add another Tunnel-Group and Group-Policy for your Management-VPN, I’ll drop back to CLI to do that (to keep things neat and tidy).
! group-policy GP-Management-VPN internal group-policy GP-Management-VPN attributes dns-server value 192.168.123.10 dhcp-network-scope 192.168.125.0 vpn-tunnel-protocol ssl-client split-tunnel-policy tunnelspecified split-tunnel-network-list value SPLIT-TUNNEL default-domain value testrig.com ! tunnel-group TG-Managemet-VPN type remote-access tunnel-group TG-Managemet-VPN general-attributes default-group-policy GP-Management-VPN dhcp-server 192.168.123.10 tunnel-group TG-Managemet-VPN webvpn-attributes authentication certificate group-alias TG-Managemet-VPN enable group-url https://vpn.testrig.com/Management-VPN enable !
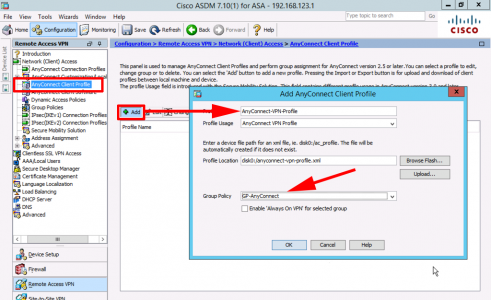
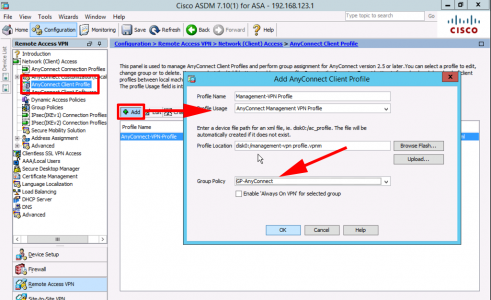
Add a new connection profile, set the type to ‘AnyConnect Management VPN Profile’, and link it to the Group-Policy for your AnyConnect USER connections.
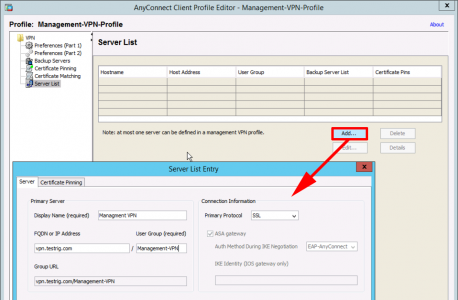
As before add an entry to the server list with the same URL you specified in the Management VPN tunnel group.
Add an Automatic VPN policy, to connect whenever you are on a network that is NOT your corporate network. Here if a client sees my server, on the same network, or gets my domain name via DHCP it WONT connect.
Additional Settings Required for Management VPN
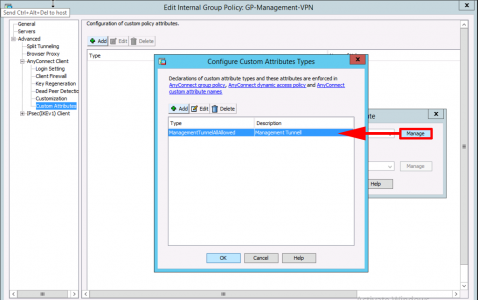
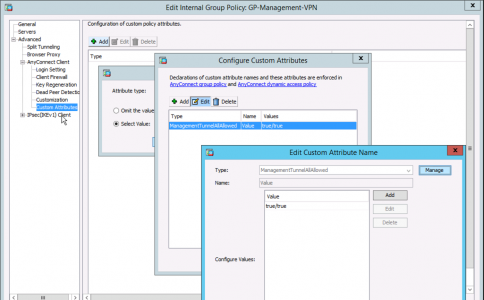
Edit the Group-Policy you are using for Management VPN > AnyConnect Client > Custom Attributes > Add > Create an Attribute called: ManagementTunnelAllAllowed.
Create a value for it called true/true.
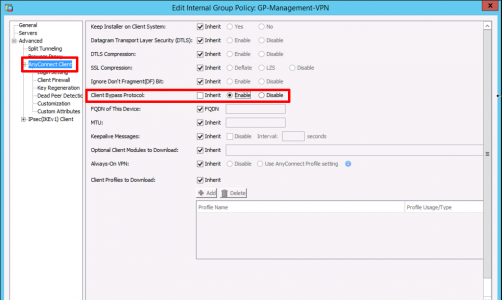
In the ‘AnyConnect Client‘ section, ENABLE ‘Client Bypass Protocol’.
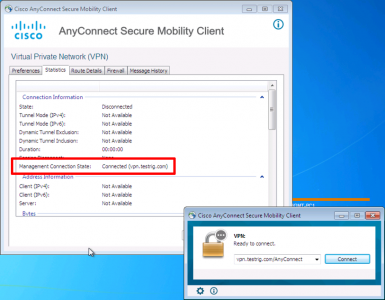
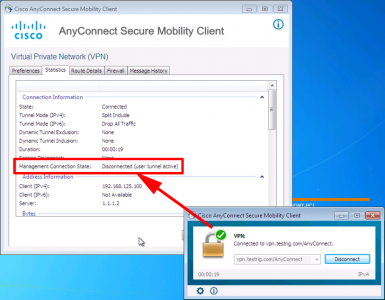
Your client will need to connect at least once to get the new settings, once they have when they disconnect the Management VPn will establish.
As soon as the user tunnel comes up, the Management VPN tunnel will drop.
Related Articles, References, Credits, or External Links
NA


16/01/2019
Thank you for the article. I am trying to think of a use-case for this setup. It seems that if your resources are not segregated, little benefit is gained with this setup vs Automatically Connect feature.
However if your internal resources are well segregated and you do not want to use auto connect feature, this setup will at least allow continuous access to management resources for group policy updates, client call-home, av/windows updates etc…
Most high-security organizations these days require full-tunnel VPN with automatically connect to VPN when on untrusted network so that is why I am asking the question.
To summarize: If organization wants to enable auto VPN for management purposes, but also wants to protect other resources with User based/2FA authentication requirements this solution is for them. But if organization has management apps (DC/AV/SCCM/WSUS etc…) and other applications which they do not want to protect with additional authentication, they gain little with this solution?
17/01/2019
Agreed, or you may want to deploy force tunnelled on your user tunnels and split tunnelled on your machine tunnels. Either way try and deploy Microsofts Machine tunnel feature! I’ve still not got it to work 🙂
25/07/2019
I am the lead VPN Design Engineer for a number of fortune 500 companies and most of them have a split-tunnel VPN as their default or available. Large companies do this since many have a large remote workforce and want to save on internet circuit cost. Split-tunnel means internet bound traffic is not passing through the company’s web proxy and internet connection. This feature is a great add.
25/03/2019
I have a situation where I have a remote server in a secure facility that allows me to establish a client VPN session out, but I cannot have a static public IP NAT’d through to my LAN firewall segement. i.e. I have a private LAN behind my building owner’s firewall. I need remote access to this server – especially after restarts, etc. I’m thinking this solution would meet this need, as it allows me to have a client VPN session to this device without having anyone logged in.
Other than this, many orgs have techs or remote workers that only occasionally need access to resources behind the VPN and may go for months without using it, yet still need group policy updates, etc. The increasing use of SaaS apps over https minimizes the need for daily vpn needs – this seems like a way to control the desktop without requiring them to actually use the vpn. And you don’t have to remind them of their credentials or renew certs when they realize it expired.
25/03/2019
That would be a use case, I did something similar, a few years ago when AWS didn’t support VPN to Cisco ASA, I had a AWS host that AnyConnect VPN’d to a clients site as soon as it booted up, and then I had one IP in the remote pool so it always got the same IP.
22/04/2019
I had to configure the custom attribute ‘ManagementTunnelAllAllowed’ to use ‘name’ set to ‘true’ and ‘configure valuse’ set to ‘true’ in order to have a fulltunnel management tunnel.
This differs from your screenshot.
30/04/2019
Thanks for this it helped get me started but I was trying to work out how to link my user vpn with the management tunnel, which seems to be missing from your post.
I found this in the cisco docs –
Associate the Management VPN Profile to Group Policies
You must add the management VPN profile to the group policy associated with the tunnel group used for the
management tunnel connection.
Similarly, you may also add the management VPN profile to the group policy mapped to the regular tunnel
group, used for the user tunnel connection. When the user connects, the management VPN profile is
downloaded, along with the user VPN profile already mapped to the group policy, enabling the management
VPN tunnel feature.
Alternatively, you can deploy the management VPN profile out of band: ensure it is named
VpnMgmtTunProfile.xml, copy it to the above mentioned management VPN profile directory, and restart the
Cisco AnyConnect Secure Mobility Agent service (or reboot).
28/01/2021
Just want to thank you.
I was deploying OOB and the mgmt tunnel was not coming up.
The key information that seems to be missing from Cisco’s documentation is that the Management Tunnel XML Profile on client devices, should be in the proifile\MgmtTun directory and called VpnMgmtTunProfile.xml
Thanks again.
03/11/2019
Hi,
I have the management VPN tunnel deployed. When a user connects, the Management VPN tunnel kicks in and it’s all good. Different applications like Outlook and all starts getting used but as soon as the User Anyconnect comes in, the applications face error and stays like that unless user tunnel is connected and the application issues are manually cleared out.
How can we get rid of such application errors?
Is it because we lose internet access during the transition from management tunnel to User-Anyconnect tunnel and the applications face error?
Thanks in advance.
04/11/2019
Sounds like you just need to enable split tunnelling for these users 🙂 search for it above.
30/06/2020
Could be an issue with split DNS also.
17/12/2019
Has anybody tried to use the management tunnel with two or more ASA’s doing load balancing?
Any tricks to getting it to work?
Thanks In Advance
25/05/2020
Hi Pete,
Can you help with what is ‘Automatically Connect’feature you mentioned initially, you meant SBL and Automatically connect are same ?
Also need clarification if we configure SBL does it mandates user to login to VPN everytime they restart the laptop ?
Thanks & Regards,
Krupi.
29/05/2020
Hi Krupi, No ‘Always-On’ connects as soon as the machine detects a network connection, ‘Start Before Logon’ is not really an Anyconnect term, the functionality you are looking for is called ‘Retain VPN on Logoff’. Both these options require you configure them in the XML profile, and will also require a certificate based logon.
09/06/2020
Hi Pete, great articles – thank you.
I would just add that you should ensure that the Mansgement-VPN Group Policy does not have a Banner enabled.
To be sure, its best to include :-
group-policy GP-Management-VPN attributes
banner none
If the GP Banner setting is inherited from a GP which has it enabled, then the Management Connection State will try to connect but each time will show ‘Disconnected’ (Connection failed).
I now have a problem where the Mgmt-VPN connection is up, a user logs out, and it stays up – which is what we desire.
However, when a user logs back in, they are presented (eventually) with an Anyconnect user login box (and the Mgmt-vpn connection is disconnected).
The Start VPN when AnyConnect is started is unchecked.
Not sure why atm.
Client version 4.8.03052
10/06/2020
Thanks for the heads up!
18/02/2021
Most probably the same thing we run into. Solution for us was the configuration in the Management tunnel Client profile.
Solution was:
Anyconnect Client profile ->> Preferences Part 2 ->> Automatic VPN policy ->> Untrusted Network Policy== Choose “Do nothing”
We had it set to “connect” earlier but this will create a “loop” when the anyconnet try to connect when on untrusted network. Default “autoreconnect” is checked on Preference part1 and thats is enough.
18/02/2021
Thanks for the feedback – the untrusted network setting has only cause me a problem once, I had a big public sector client, that wanted it enabled. Months later they added a new DNS server and removed the old one – Boom, every employee dropped off the network across the entire country 🙂
30/06/2020
How do you handle consultants using the same profile? I mean they’re using their company issued devices and not ours. But connecting to our network and recieves the management profile. Since they don’t have a certificate they’re unable to connect. But will their client try to connect? (And fail the authentication of course)
What if they also use anyconnect as their vpn-software choice? And also has deployed the management VPN feature. Will our config break/override their config?
01/07/2020
Hi Jocke,
Brilliant question! Typically for external contractors and consultants – I’d create a different AnyConnect Group Policy and connection profile. But if you didn’t then your Management VPN settings WOULD override theirs. You can manage multiple AnyConnect connections if your an external Contractor like this. But not all consultants are ‘Cisco Savvy’ of course.
01/07/2020
What would be the best way to make a VPN profile for internel users and one for external (contractor)?
Usually the instructions to the contractor is to go to use vpn.company.com in anyconnect if they already have it installed or browse to the url and login in to down the client. As I understand this, they will get the default profile? If I use anonther url I need a different public certificate.
Is there a possibility to control the profile getting downloaded using an AD-group?
02/07/2020
You could get up a specific url for them vpn.company.com/external for example or have a different AD group for them then use a Dynamic Access Policy or simply an LDAP attribute map to make sure they get a different firewall group policy, I’ve covered this elsewhere on the site, search is top right buddy.
04/08/2020
Hi Pete,
Are there any troubleshooting tools you can run client side? Our machines connect once a user (either domain or local account) has logged on, but don’t seem to connect at ctrl+alt+del as non-cached domain accounts are unable to login.
30/09/2020
We are in the same situation so I’m curious to see if you resolved your issue with un-cached domain accounts. We installed and enabled SBL thinking that would work for us but it does not. SBL does establish a VPN connection, however, it does not trigger the ‘System Scan’ which is required to give full network access until the user authenticates and reaches their desktop. I haven’t found a way to configure the System scan to run at SBL. I’m just starting to investigate other options such as Always On.
04/02/2021
Hi Pete,
I have created the management tunnel without issue. We have remote users that very rarely connect to their user VPN. My issue is I am using a filter ACL to prevent them access to anything except what I permit (AD, AV, SCCM, WSUS and DNS), but I cannot remote control their laptop from the SCCM server.
Seem like all the services running on the laptop can initiate a session to their respective servers but when I try to initiate a session from the server to the laptop (in this case remote control) the filter ACL denies it even though it is configured to permit traffic.
Cisco tell me this is how the management tunnel is supposed to be and sessions can only be established one way. I find this hard to believe.
Have you experienced the same thing? Any ideas what could be wrong?
05/02/2021
I have to admit its a surprise to me. even if you allow the traffic in ACL (from outside) it does not work?
05/02/2021
Correct. I have opened up the outside acl and am not doing any NAT. It’s a pretty straightforward set up and clearly the traffic is reaching the firewall as the Cisco guy did a capture and could see the packets from the server. He couldn’t explain why it was being blocked so went away to discuss with his colleagues. He then came back and said it was not possible.
I cannot find any answers online and the Cisco documentation can be hard to decipher. The Cisco guy pointed out in the docs the line – User interaction is not supported – and claimed this was Cisco’s way of saying it won’t work as I would like. Guess I will have to go with the ‘always on’ option if I want two way access…
05/02/2021
>>Cisco documentation can be hard to decipher.
Agreed, but I’d get less traffic if it wasn’t 🙂
>>Guess I will have to go with the ‘always on’ option if I want two way access
That’s the best way forward, been a while since I set it up, but it was pretty straight forward.
P
05/07/2021
Hi Pete,
i noticed when you’re creating the Profile a normal AnyConnect VPN Profile is being selected, but shouldn’t this be a AnyConnect Management VPN Profile that one actually has to select? (.vpnm instead of .xml). Bunch of Thanks and keep up the good work!
05/07/2021
Nevermind….it is correct just as presented here, but for me it started working only after I also created the Management VPN Profile as well!
02/02/2022
Hi Pete,
Thank you for brilliant article (among your others)!
I got Management tunnel working for Windows but I just can’t get it working for MacOS.
Do you have any experience on that you could share?
04/02/2022
I do not, but I’ll happily post your question….
03/05/2023
Can you explain what is “ENABLE ‘Client Bypass Protocol’.” for?
01/06/2023
Hi
Will I be able to reset password for an expired user password with AnyConnect Management VPN Tunnel ?
06/06/2023
Not tested in anger so I can’t comment.
P
27/06/2023
If your management gp and your normal gp have the same split-tunnel acl, then the user doesn’t need to connect to normal vpn at all, right? Shouldn’t the management policy only allow minimal traffic to allow management and domain stuff?