KB ID 0001675
What are these protocols?
Both SSL and TLS are cryptographic protocols designed to secure communications over a network (remember the internet is just a network). Originally we had SSL version 1 and version 2. But they were, (to be honest) ‘a bit bobbins’ and full of security holes, so never really took off. Version 3 however did and was widely supported. The problem with version 3 was, (again) that was also ‘bobbins’. All this came to a head with the Poodle exploit and people started getting rid of SSLv3.
So, what about TLS? Well TLS v1.0 was largely based on, (but not compatible with) SSLv3. TLS 1.1 replaced v1.0 (circa 2006). Problems with it prompted TLS 1.2 (circa 2008). Then that was the standard until TLS v1.3 (circa 2018).
However: Just because you use the newest protocols does not necessarily mean you are more secure: Most documentation you read says TLS 1.2 ‘Should’ be secure (that’s reassuring eh!) This is because these protocols are built on cryptographic ciphers and they are only as secure as those ciphers. You can corrupt a strong protocol with a weak cipher and render it less secure. In some cases, you may need to do this, or you might simply enable a web cipher to fix a ‘problem’ without understanding the consequences.
You are ‘Probably’ Reading this Because…
If you’ve had a security audit, or a company had scanned your network and produced a report that says you are running insecure protocols and you need to do something about it.
THINK: Security is a good thing, (I’m all for it,) BUT just rushing to turn things off, can cause you problems, where possible test any remediation in a test environment, many old legacy (for legacy read ‘applications that are business critical, and you can no longer update or get support on’) may still be using these old protocols. Simply disabling SSLv3.0, TLS v1.0,1.1, and/or 1.2 can have some negative effects, either on YOUR applications or in the browsers of your clients. Remember if you provide a web based service it will also need testing with any browser that your staff, or even the public may be using to access your web based platforms.
TLS 1.0 and TLS 1.1 might be ‘depreciated’ but it’s still widely used, disabling them will probably cause you more problems than the older SSL protocols, so test, test, and test.
ISOLATE: If you have old legacy applications and you need to retain them for compliance or financial reasons, then consider simply MITIGATING the risk by taking them off the local network, and running them in isolation.
DOCUMENT: If you need TLS 1.1 then that’s fine just because a scan picked it up, does not mean that you HAVE TO run to the server room and disable it. Most compliance standards are fine with you not fixing something, providing you document what it is and why it’s still enabled.
Windows TLS 1.2 Support: Clients from Windows Vista, and Servers from Server 2008 support TLS 1.2. but all the way to Windows 8.1 and Server 2012 R2 it requires an update, so make sure you are fully up to date before attempting to use TLS 1.2.
Exchange: Support for TLS 1.1 and 1.2 wasn’t added until Exchange 2013 (CU8) and Exchange 2010 (SP3 RU9). Beware Some (Older) Microsoft Outlook clients will only work with TLS 1.0
Windows Client (Internet Explorer) Disabling SSL3 and TLS 1.0, TLS 1.1
Before disabling protocols on the server, it’s good practice to disable those protocols on the clients, some time beforehand, the easiest way to do this is via Group Policy.
Windows Server Disabling SSL3 and TLS 1.0, TLS 1.1
Note: Before disabling anything enable TLS 1.2
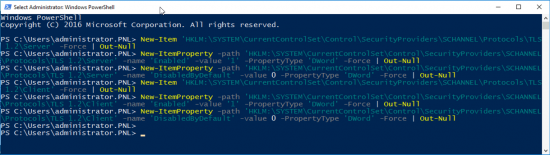
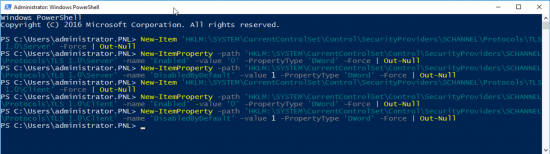
Enable TLS 1.2
Execute the following PowerShell commands;
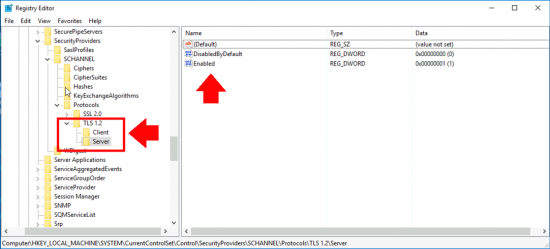
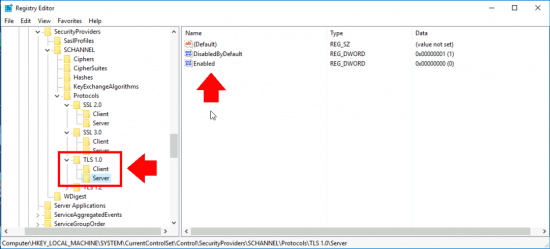
New-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server' -Force | Out-Null New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server' -name 'Enabled' -value '1' -PropertyType 'DWord' -Force | Out-Null New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server' -name 'DisabledByDefault' -value 0 -PropertyType 'DWord' -Force | Out-Null New-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client' -Force | Out-Null New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client' -name 'Enabled' -value '1' -PropertyType 'DWord' -Force | Out-Null New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client' -name 'DisabledByDefault' -value 0 -PropertyType 'DWord' -Force | Out-Null
What this actually does is create some registry settings;
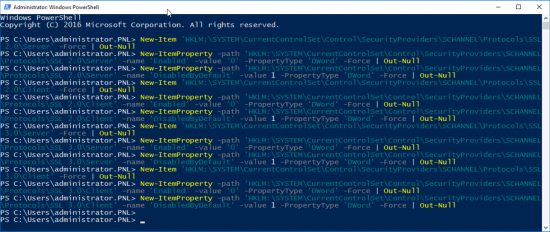
Disabling SSL v2.0 and SSL v3.0
Note: SSL 2.0 is normally disabled by default on modern versions of Windows.
Execute the following PowerShell commands;
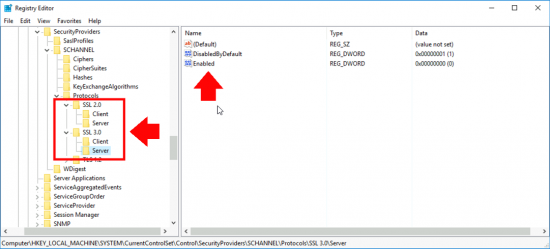
New-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Server' -Force | Out-Null New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Server' -name 'Enabled' -value '0' -PropertyType 'DWord' -Force | Out-Null New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Server' -name 'DisabledByDefault' -value 1 -PropertyType 'DWord' -Force | Out-Null New-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Client' -Force | Out-Null New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Client' -name 'Enabled' -value '0' -PropertyType 'DWord' -Force | Out-Null New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Client' -name 'DisabledByDefault' -value 1 -PropertyType 'DWord' -Force | Out-Null New-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Server' -Force | Out-Null New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Server' -name 'Enabled' -value '0' -PropertyType 'DWord' -Force | Out-Null New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Server' -name 'DisabledByDefault' -value 1 -PropertyType 'DWord' -Force | Out-Null New-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Client' -Force | Out-Null New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Client' -name 'Enabled' -value '0' -PropertyType 'DWord' -Force | Out-Null New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Client' -name 'DisabledByDefault' -value 1 -PropertyType 'DWord' -Force | Out-Null
What this actually does is create some registry settings;
Disabling TLS 1.0
Note: Depending on your setup this may impact production, test it first!
Execute the following PowerShell commands;
New-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Server' -Force | Out-Null New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Server' -name 'Enabled' -value '0' -PropertyType 'DWord' -Force | Out-Null New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Server' -name 'DisabledByDefault' -value 1 -PropertyType 'DWord' -Force | Out-Null New-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Client' -Force | Out-Null New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Client' -name 'Enabled' -value '0' -PropertyType 'DWord' -Force | Out-Null New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Client' -name 'DisabledByDefault' -value 1 -PropertyType 'DWord' -Force | Out-Null
What this actually does is create some registry settings;
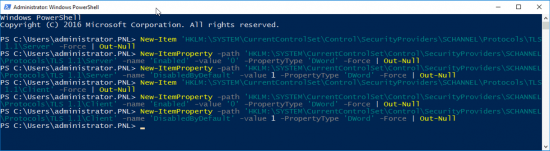
Disabling TLS 1.1
Note: Depending on your setup this may impact production, test it first!
Execute the following PowerShell commands;
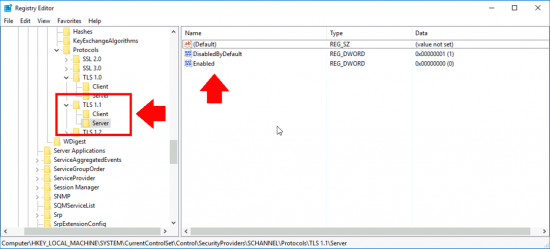
New-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Server' -Force | Out-Null New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Server' -name 'Enabled' -value '0' -PropertyType 'DWord' -Force | Out-Null New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Server' -name 'DisabledByDefault' -value 1 -PropertyType 'DWord' -Force | Out-Null New-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Client' -Force | Out-Null New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Client' -name 'Enabled' -value '0' -PropertyType 'DWord' -Force | Out-Null New-ItemProperty -path 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Client' -name 'DisabledByDefault' -value 1 -PropertyType 'DWord' -Force | Out-Null
What this actually does is create some registry settings;
Then REBOOT THE SERVER. Because NONE OF THE ABOVE WILL TAKE EFFECT until you do
Help Something’s Broken!
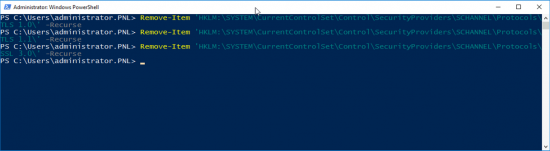
To revert your settings, execute the following PowerShell;
Remove-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\' -Recurse Remove-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\' -Recurse Remove-Item 'HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\' -Recurse
Then REBOOT THE SERVER.
Related Articles, References, Credits, or External Links
NA


20/05/2020
We also use IIS Crypto by Nartac. Great software and we haven’t had any issues with the software itself, but it helped us discovered vulnerabilities and issues after using it!
22/05/2020
Hi Alvan, yes great tool. I have seen it before, it also shows you a great deal more detail.
05/06/2020
Pete, thanks for the great articles, I follow all your stuff… It’s like you work in my office! For me, on a Windows Server 2012, the script installed the TLS 1.2 folder and “Client” subfolder in the Registry but didn’t install the “Server” subfolder.
I’m researching a solution in the event others have the same issue. Here is the error:
+ New-Item ‘HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Prot …
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : InvalidArgument: (:) [Out-Null], ParameterBindingException
+ FullyQualifiedErrorId : PositionalParameterNotFound,Microsoft.PowerShell.Commands.OutNullCommand
New-ItemProperty : Cannot find path ‘HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server’ because it does not exist.
At line:2 char:1
+ New-ItemProperty -path ‘HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders …
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : ObjectNotFound: (HKLM:\SYSTEM\Cu…\TLS 1.2\Server:String) [New-ItemProperty], ItemNotFoundException
+ FullyQualifiedErrorId : PathNotFound,Microsoft.PowerShell.Commands.NewItemPropertyCommand
05/06/2020
This snippet from https://www.jorgebernhardt.com/disable-ssl-and-tls-on-winserv/ actually did the trick for me:
**********
New-Item ‘HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server’ -Force | Out-Null
New-ItemProperty -path ‘HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server’ -name ‘Enabled’ -value ‘1’ -PropertyType ‘DWord’ -Force | Out-Null
New-ItemProperty -path ‘HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server’ -name ‘DisabledByDefault’ -value 0 -PropertyType ‘DWord’ -Force | Out-Null
New-Item ‘HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client’ -Force | Out-Null
New-ItemProperty -path ‘HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client’ -name ‘Enabled’ -value ‘1’ -PropertyType ‘DWord’ -Force | Out-Null
New-ItemProperty -path ‘HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client’ -name ‘DisabledByDefault’ -value 0 -PropertyType ‘DWord’ -Force | Out-Null
Write-Host ‘TLS 1.2 has been enabled.’
**********
15/09/2021
its same as pete’s
pete just miss new line on first command.
he smush 2 command to 1 line command
03/08/2020
Hi Pete,
please take note i set the mentioned registry key but when i test the TLS 1.0 and TLS 1.1 both of them show enabled, do they registry settings work on Windows Server 2016/2019?
03/08/2020
Yes, did you reboot the host?