KB ID 0001473
Problem
If you are retiring a CA Server, or there’s a problem with the server and you want to move Microsoft Certificate Services to another server, the procedure is pretty straight forward.
BE AWARE: We are moving the CA Server Name , NOT the Server Name (FQDN), the two things are NOT the same, (you might have called them the same thing!) But a Certificate Authority has a name of its own, and that’s what we are going to move.
So the new server doesn’t have to have the same name? No, it can do if you really want, but that’s an added layer of complication I can’t see the point of?
In the video below, I’m migrating from Server 2008 R2 to Server 2019, and I’m also moving CRLs and OSCP responders. In the screenshots below I’m moving from Server 2016 to Server 2016, but the process is pretty much identical all the way back to Server 2003.
Can I migrate from Server 2008 (NON R2) to 2016 (or newer): Yes, but not directly, you need to upgrade to Server 2012 R2 first. If you don’t, the database wont mount and you will get this error.
Solution
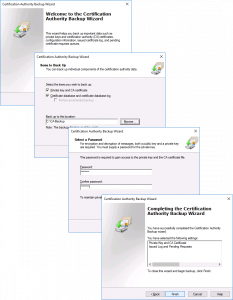
On the ‘Source‘ server, open the Certificate Services management console > Right click the CA NAME > All Tasks > Back up CA.
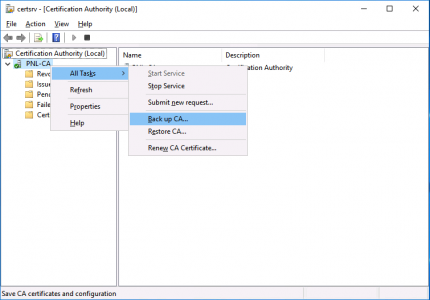
The backup wizard will open, Next > Tick BOTH options > Select a Backup Location > Next > Set a password (you will need this to set the new CA up!) > Next > Finish.
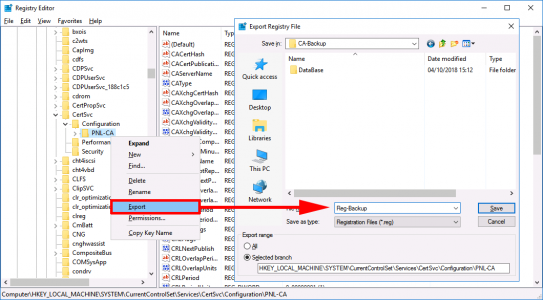
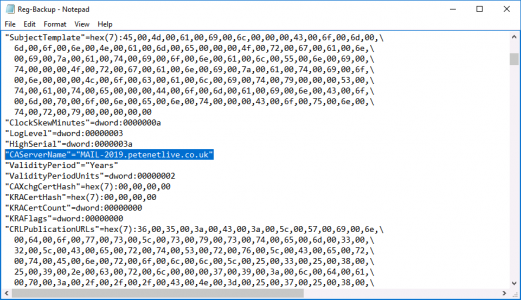
Now we need to take a backup of the Registry key that holds the information for this CA server. Run ‘regedit’ > Navigate to;
Export a copy of this key, (save it in the same folder that you backed up to earlier).
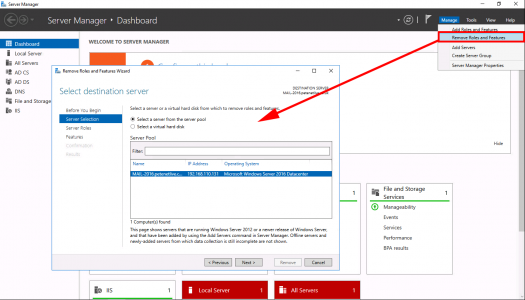
Now we need to uninstall CA Services from this server. Server Manager > Manage > Remove Roles and Services > Next.
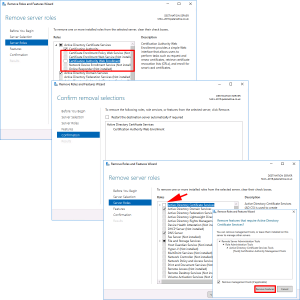
REMOVE all the CA role services > Complete the Wizard, then launch the wizard again and select ‘Active Directory Certificate Services’ > At the pop-up select ‘Remove Features’ > Next.
Next > Next > Next > Close.
Setup Certificate Services on the Target/New Server
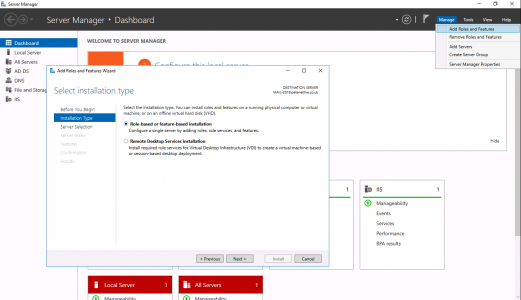
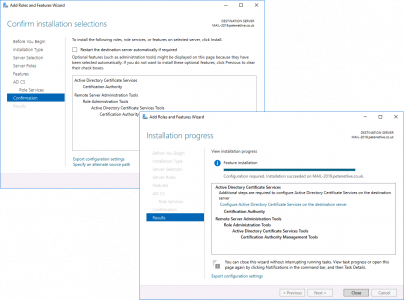
Server Manager > Add Roles and Features > Next.
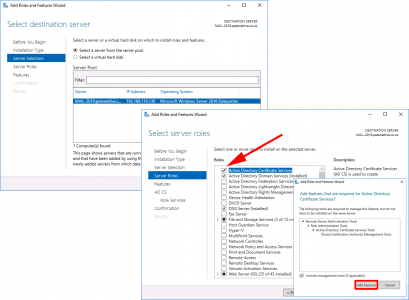
Next > Select ‘Active Directory Certificate Services’ > Add Features > Next.
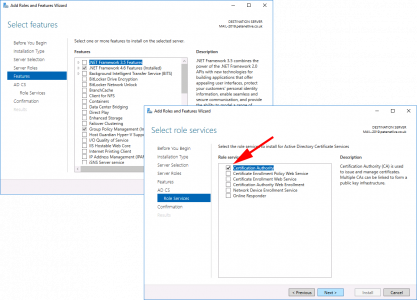
For now let’s just stick with the Certification Authority > Add the other role services later* > Next.
*Note: I’ve written about all these role services before, just use the search function, (above), if you are unsure what they all do.
Next > Close.
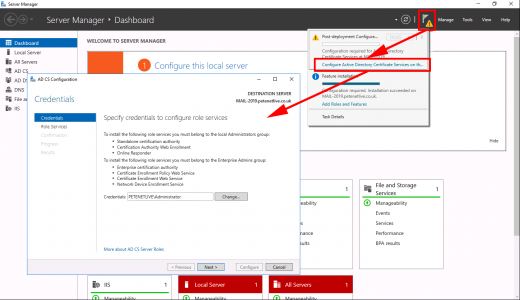
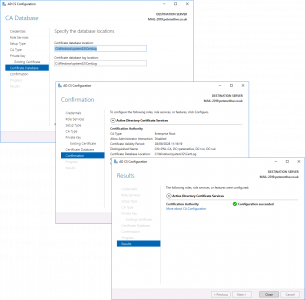
Warning > Configure Active Directory Certificate Services > Next.
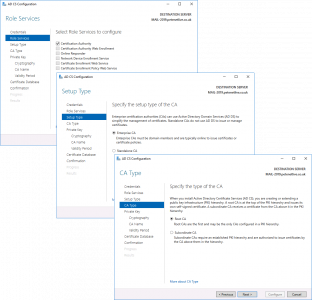
Next > Enterprise CA (Unless it’s an offline non domain joined CA) > Root CA (unless it’s a subordinate CA!) > Next.
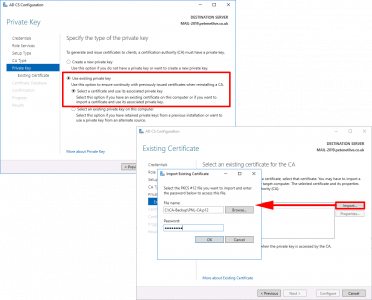
> Select ‘Use existing private key‘ > Select ‘Select a Certificate and use its associated private key‘ > Next > Import > Browse > In your backup folder locate the certificate (it will have a .p7b extension.) > Enter the password > OK > Select the Cert > Next.
Next > Next > Configure > Close.
Stop Certificate Services;
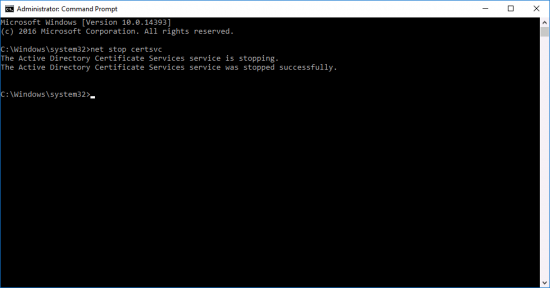
If your new server has a different hostname/FQDN open the registry file you exported above with Notepad, locate and change the CAServerName entry to the name of the NEW server.
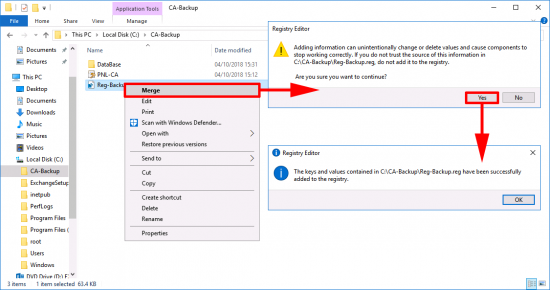
Right click the registry backup > Merge > Yes > OK.
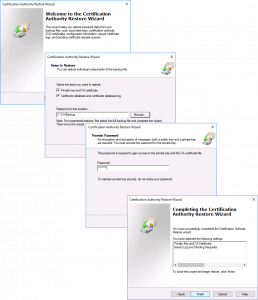
Launch the Certificate Services management console > Right Click the CA NAME > All Tasks > Restore CA.
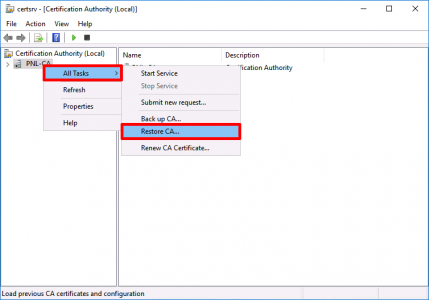
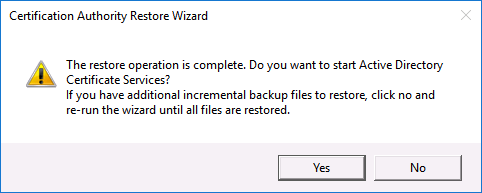
The restore wizard will start > Next > Browse to the folder with your backup in > Next > Enter the password you used (above) > Next > Finish.
You will be prompted to start the Certificate Services service > Yes.
What About Certificate Templates? Do I need to Move Them?
No! Certificate templates are actually stored in Active Directory, NOT in/on the actual Certificate Services server, (that’s why sometimes they take a while to appear after you create them!) You can see them here;
Related Articles, References, Credits, or External Links
Digital Certificates Explained
Certificate Services – Migrate from SHA1 to SHA2 (SHA256)

09/02/2019
Thank you for submitting the new hostname CA server Fix.
09/08/2021
Thanks! extremly usefull!!!
15/05/2019
Nice and clear walkthrough
I used this to perform a move for the CA service on a pair of 2012 R2 servers.
No issues were experienced beyond ensuring *NOT* to select the “database” sub-directory when performing the final restore, use the parent directory.
Thanks for taking the time to write and present this so well.
Stu
16/05/2019
No problem Stu, thanks for the feedback.
30/05/2019
Thanks for the nice and concise write-up. I’ll be using it to migrate a 2008R2 CA to a 2016 server. Quick question, do I need to back up and restore the cert templates too?
-George
30/05/2019
Cheers George, the templates are actually stored in AD, not in cert services, (providing they have been published of course!)
P
28/06/2019
George, did you complete your migration? I’m seeing some sources (https://social.technet.microsoft.com/wiki/contents/articles/37373.migrating-ad-certificate-services-from-windows-server-2008-to-windows-server-2016.aspx) saying you can’t migrate CA from 2008 to 2016, although the source wasn’t clear whether 2008 or 2008 R2. I wanted to know if you were successful with your 2008 R2 to 2016 CA migration; I’ll be making that leap here soon as well.
OB
08/07/2019
::bump:: please
I have the same question, thank you.
08/07/2019
I ended up finding this today from technet, according to this article 2008 R2 can be migrated to 2016 / 2019.
https://techcommunity.microsoft.com/t5/ITOps-Talk-Blog/Step-By-Step-Migrating-The-Active-Directory-Certificate-Service/bc-p/700730#M270%3FWT.mc_id=ITOPSTALK-blog-abartolo
20/06/2019
Any downtime for this? Considering doing this during the day.
20/06/2019
Only for the PKI service while you swap over 🙂 Users probably won’t even notice.
25/03/2021
How did you make out? Thinking about doing this during the day myself? Was concerned it might trigger something the users can see.
30/07/2019
Worked on 2019 as well
13/08/2019
Can you install the new CA role but not restore the services prior to doing the swap? Would speed up the process not fully removing old and then installing new etc.
16/10/2019
It is not possible because:
It is important to remove the CA role service from the source server after completing backup procedures and before installing the CA role service on the destination server. Enterprise CAs and standalone CAs that are domain members store in Active Directory Domain Services (AD DS) configuration data that is associated with the common name of the CA. Removing the
CA role service also removes the CA’s configuration data from AD DS. Because the source CA and destination CA share the same common name, removing the CA role service from the source server after installing the CA role service on the destination server removes configuration data that is required by destination CA and interferes with its operation. The CA database, private key, and certificate are not removed from the source server by removing the CA role service. Therefore, reinstalling the CA role service on the source server
restores the source CA if migration fails and performing a rollback is required. See Restoring AD CS to the source server in the event of migration failure.
17/10/2019
I’ve seen a couple different takes on this…
One states that the removal of the CA roles on the one server is absolutely necessary prior to adding and configuring them on the replacement server.
Another states that one can simply force the one server offline (e.g. disable the NIC) so it’s not available when the replacement server comes online.
You clearly take the first position, and it makes sense. It’s a bit nerve-wracking, even with the rollback options, but it makes sense.
Question: If the replacement server has a different hostname, and the certificates show the original server’s hostname as part of their CRL Distribution Point, will the steps in this article account for those, or will I need to take additional steps such as creating a CAPolicy.inf file?
Alternatively, I’ve considered just making a separate DNS entry for the old hostname pointing at the new IP.
13/08/2019
Excellent ! I would have never figured that out, especially the registry modification.
Move a 2012R2 over to 2019 Server not issues.
20/08/2019
Some articles say to change the name of the new CA Server to match the old CA server after you decommission the old CA server… so this is NOT necessary right? The only thing is the new server name will not match the CA name right? Oh and you would not need to modify CAServername registry entry….
22/08/2019
I don’t (usually) and I’ve never had a problem?
P
18/01/2020
You can’t. The add roles/features wizard specifically states that once you add the CA role, you can’t change the hostname and or domain afterwards.
26/08/2019
Thanks for the article, good work!
What about the AIA and CDP distribution points, and the CRL urls? Do you need to do anything to those to change them etc?
27/08/2019
That is a great point! If you are retaining the server name, things like AIA will probably be the same, but CRL and OSCP may well need to man manually recreated (with the same paths, or changed to the new server name).
29/08/2019
Thanks the article is very straight forward. My question as I prepare to move my CA to a new server is how do the clients find the CA?
If the CA was one name or on one server how do they find it when I move to a new server with a different name?
Thanks,
Dave
29/08/2019
They will find it in Active Directory 🙂
29/08/2019
So it will replicate the changes with AD?
I only ask because its a huge move considering if things don’t work my users wont be able to login.
And thanks so much for taking the time to answer me.
29/08/2019
Even if you are doing 801.x authentication the root CA cert will be the same, all previously issued certs will remain trusted. 🙂
11/09/2019
Awesome, thank you so much
12/09/2019
Is it safe to assume same steps would work migrating from 2008 R2 to 2016 Server?
I already have prepped 2016 server that is domain joined.
Would you also recommend making it a domain controller since my 2008 CA is also a domain controller
with schema master role assigned? I was planning on moving that role ahead of time, but should I still make it a domain controller ?
Thank You
16/09/2019
Yes in fact I’ve done it in anger 🙂
22/09/2019
PeteLong when you say Yes to Luke, which question are you saying Yes to? I was thinking of taking this opportunity to move my CA off of my 2012 DC and moving it to a member server. Everything I see says to keep it off of a CA so that is why I’m looking at it.
I was thinking I could bring up a new DC2019 and then demote the DC2012 (that has the CA on it). Now it’s just a member server. I could then install a new MemberServer 2019 and move the CA from the 2012 server to it.
What are your thoughts on this process?
23/09/2019
I mean the upgrade/migration process will work.
I don’t recommend making it a domain controller, (unless you have no choice).
Treat migrating domain controllers and migrating CA’s as a separate thing!
24/09/2019
I have something similar to this but I wanted to see if someone can comment on this: i have a CA server on an old 2008 R2 enterprise domain controller which I want to retire I also have two additional one is 2012 R2 and the other one is a 2016. all roles are managed by the 2012 DC
is it advisable to just install CA services on both 2012 and 2106 DCs and retire the 2008 DC or do i need to migrate the DB from the 2008 into one of the other two domain controllers?
Any feedback would be greatly appreciated. thanks, Wil
24/09/2019
Migrate the Root CA, then simply remove the CA roles from the SubCA servers and create some new ones, take a backup of them before you kill them in case you need to retain the intermediate CA certificates for any reason (i.e. 802.1x, or NDES, or appliances you manually put certificates on).
P
14/10/2019
What an excellent article. I’ll be using this as a guide to migrate a 2012 R2 CA to 2016 this week.
One quick (I hope) question: We’ll be changing the hostname and IP address of our CA. Is it strictly necessary to remove the CA roles from the original CA prior to installing those roles on the new CA? Or, can the original CA be shut down pending successful migration?
14/10/2019
Well no it’s not strictly necessary, but the CA can only exist in one place, the sever-name and the CA name are NOT the same, as soon as the CA is imported and online on the new server it CANNOT be online on the old one 🙂
P
14/10/2019
Perfect. Thanks again! Sounds like the best way to ensure some fallback plan (or management peace-of-mind, anyway) is to disable the NIC on the server hosting the old CA so, even powered on, it can’t talk to others. Out-of-Band-Management is obviously key to being able to do this.
Then, once we’ve got green light on the new CA on the new server, we can remove the roles from the old server.
30/01/2020
Even easier to disconnect Ethernet cable from old server. 🙂
22/10/2019
Thank you
31/10/2019
Thank you for a great article. Worked perfect. Just a quick comment, I had CNAME’s for CRL and AIA in my local DNS pointing to the old server hostname. I updated those to the new server hostname.
15/11/2019
When installing CA on the new server, when I go to configure it, the option for Enterprise CA is grayed out. Do you know why that is?
18/11/2019
Is it already a domain member server?
21/11/2019
We have root offline CA (Non Domain Joined) and Intermediate CA (Domain Joined) both are on 2008 R2
can we follow same process to migrate both server?, first migrate Root offline CA to 2019 and then migrate intermediate CA to 2019
is there anything else required.
21/11/2019
I’ve not done this, but I don’t see why not, as we are moving the CA, not the server. You can Test it in a virtual sandbox, but I can think of any problems.
11/08/2021
Hi, We also have offline root CA non domain joined and two sub servers. What is the order to do things? Root CA first and then do we do one sub at a time or take both offline at the same time?
11/08/2021
Hi Tim, Always start with the root and work down.
25/11/2019
work this on domain controllers servers ?
i have DC where is running CA and need migrate to new server with new FQN name.. but CA name will be same as old..
thanks for help 😉
25/11/2019
The fact its a DC does not matter its the “CA name” you are moving 🙂
06/12/2019
Correct me if I am wrong – it may be a good idea to make a note of and then remove all certificate templates on the old server prior to taking a backup of the existing CA to ensure that no certificates are issued between the time you take the backup on the original server and restore on the new server. The templates could then be re-added after the restore is done.
06/12/2019
Templates don’t live on the CA server, they are stored in AD, that’s why if you have a lot of domain controllers, you need to wait a few minutes before you can issue a ‘new’ template. You are waiting for domain replication to occur.
13/12/2019
Perhaps I was not as clear as I could have been. I was suggesting that you could unpublish the templates to prevent certificates being issued between the moment you take the CA backup and disable/remove Certificate Services on the old server. The chance of this happening is small, but couldn’t it result in an ‘orphan’ certificate being issued?
16/12/2019
The worst that would happen is you would not be able to revoke it.
13/12/2019
Everything seems to have worked except the registry import, is it a requirement or can we run without it?
16/12/2019
No you definitely need that to work!
16/12/2019
Great information!
My team and I are ready to execute this Migration from a 2008 Server to a 2012R2. Our main concerns are:
1. If the server has a different name, even if we change the name in the registry export to the new name, how does that affect any currently issued certificates with the old name embedded into it?
2. How do you get all computer objects on the domain to update the certificate once the new cert is up and running?
I’m a bit novice to Managing a Certificate Store, but the project is mine to undertake and i certainly want to learn, so please Jedi Masters, give this Padawan Guidance! Thanks!
16/12/2019
1. Man Im sure I’ve mentioned this six thousand and seven times, stop worrying about server names, server names are not important at all, you are moving the CA name. So changing the server names affects nothing.
2. Assuming your computers are auto-enrolling, (if not then they wont have any certificates?) then they will renew from the CA NAME which they will find in active directory, and which hasn’t changed from the last time they got a certificate, it’s just on a different server 🙂
Imagine ‘Boots the chemist’ moves from the middle of town, to the out of town shopping centre, your question would read how do we buy paracetamol now Boots has changed its address.
P
17/12/2019
PeteLong, If the server name is irrelevant, then why is the cert server name embedded in the local workstation and server certificates? See the ProdCert1v server name in the certificate below:
(ldap:///CN=xxxxxxxxx%20xxxxxxxxxxxx%20Certificate%20Authority,CN=PRODCERT1v,CN=CDP,CN=Public%20Key%20Services,CN=Services,CN=Configuration,DC=xxxxxxxxxxx,DC=com?certificateRevocationList?base?objectClass=cRLDistributionPoint)
17/12/2019
Thats a CRL pointer.
18/01/2020
It’s the CRL URL in your reference, the person that originally installed that chose that URL/hostname. If you wish to support existing CRL lookups using this FQDN it either needs to be replicated or redirected from the original server.
However, within an AD environment LDAP is used first. This is why if your CA services non-domain members, it’s probably best to remove the LDAP location and just use HTTP to speed up resolution.
Hope this makes sense!
26/12/2019
To PeteLong…. Thank you!
Christmas Gift for me to have an easy path!
30/12/2019
Very Clean walkthrough. Thanks
02/01/2020
Hi,
I am in process of upgrading existing CA environment – 2008 -> 2019. Offline Root CA and 3 domain member SUB CA’s. After upgrade I will only need one SUB CA.
My idea is to migrate the Root CA using backup/restore as described here to a new server with new name (I think straight forward). On the current 3 SUB CA’s I want to disable auto-enrolling – and keep them alive until latest issued certificate have expired. Install a new sub CA with with auto-enrolling enabled?
Any pitfalls doing it this way?
Torben
02/01/2020
Not that I can see, as long as they are left up for the same amount of time that the certificates are valid 🙂
07/01/2020
This worked well for me thank you. On the original CA I had created a “User VPN” template for auto-enrollment. I am not sure if it was necessary, but I did reissue this certificate template on the restored CA. The User VPN template was not listed until I had selected “New -> Certificate Template to Issue”
07/01/2020
Thanks for the slick write up. I really appreciate this and the other articles you have contributed to the community Pete!
Sam
07/01/2020
Thanks Sam!
08/01/2020
Pete,
Great work, great write up.
Quick question.
I’m planning on upgrading a rootCA and a SubCA (2008r2 to 2019).
I follow the steps that you laid out for the root, I understand that.
What about the sub?
Do I do the same (ie backup the sub and the sub’s reg then restore to 2019)?
Or did I see in the comments to just install a brand new sub (even though many certs issue from sub)?
Thanx!
09/01/2020
Same procedure for the SubCA if you want to migrate it, you can also create a new one just as easy 🙂
09/01/2020
Great write up Pete!
Just a quick question, We have our CA on a 2008 DC which we want to decommission and shut down for good. Once we move the Certificate Services over to a new domain member server are we able to then demote the DC and then kill the server for good?
Just wanted to check demoting and killing the server wouldn’t cause issues with the CA on the new server?
09/01/2020
Yes – providing theres nothing else on it (DHCP, DNS, Terminal Services Licence server etc,)
09/01/2020
Put me in the same boat as those scrambling to remove 2008R2 servers from their environment. Followed these steps last night. All quiet in the office today. Would add that i was seeing errors in ‘pkiview’ referencing the old CA server, and i needed to publish my revoked certificates and then refresh the pkiview screen and that cleared those.
im still getting ‘unable to download’ on the delta crl #3 and cdp location #2 where the location is file://NEW_CA_SERVER….. but if i copy the url and browse in explorer its working, so not sure what to do there
in any case, kudos to PeteLong for actually reading and responding to so many people, after this post has been up all this time. top bloke!
10/01/2020
Thanks Jono M8!
10/01/2020
I have a Server 2008R2 and CA is running on a DC. I am planning to move CA role for DC to on its own new 2019 Server. Hostname will be different. Do I need to change any registry value if it has a different hostname? or do I need to perform any further steps apart from what is in the article.
Thanks and very helpful write up.
10/01/2020
Yes you DO need the change the server name in the registry key backup, to the new server name 🙂
P
19/02/2020
I am having the same idea like Bhav. I have a 2008DC with CA Role installed. I want to take the CA Role out and put it on 2019 Server with different hostname. Could you tell me how to change the server name in the registry backup?
24/02/2020
That information is in the post.
10/01/2020
Hello pete
First of all thx for the guide, will help a lot to guys like me that do not usually play with CA’s, are on a small business and have an inherited problem from his predecessor.
what you would recomend in a case that there is a CA server on a w2008r2 DC with a cert using a deprecated SHA1 hash algorithm?
first migrate it using your guide to a w2019 and then upgrade the SHA1 cert to a SHA256 or
First upgrade the SHA1 to SHA256 and then migrate to the new server?
Just check it with certutil -store my the provider is Microsoft Software Key Storage, so at least i dont have to upgrade from CSP to KSP, which is a little relief.
10/01/2020
Great Question!
You can do it either way, I personally would sort the SHA1 problem out first, but theres no reason at all not to do it the way round you suggest.
And thanks for the feedback!
17/01/2020
Thanks for the great article. My brain is teflon when it comes to retaining CA knowledge. Definitely one of my weaker skillsets.
I’m not sure this was made clear in the comments posted, so I’ll spell it out just in case.
Firstly, one of my pet peeves is when people don’t quote R2 when talking about that version of Server 2008. Where I work we have a Windows Server 2008 migration project when the vast majority (if not all) are 2008r2 – drives me crazy.
Anyway, since I don’t want to assume all comment posters are good techies and referencing their OSes properly in their questions, I want to clarify:
If you have Windows Server 2008 CAs (not R2) and you want to migrate to 2016 or 2019, you MUST first do a migration to 2012r2
If you have 2008r2 CAs, you can go straight to 2016 or 2019.
18/01/2020
I’ve updated this post (above) and linked to what will happen if you attempt to upgrade 2008 (non R2) to 2016/2019.
Pete
23/01/2020
Hello.
Can we use this procedure for a subordinate CA?
Should we start updating root ca first or it does not matter?
23/01/2020
Hi Victor, I would always do the root first, but that’s just my OCD. I cant really think of a good reason not to do it that way, as its a hierarchical system.
24/01/2020
Pete,
This was an absolutely great article and made going from a Server 2012R2 DC CA to a 2019 one easy-peasy-lemon-squeezy.
Thank you for such a well-written article.
27/01/2020
Thanks for the feedback Doug 🙂
P
26/01/2020
Awesome post – thanks for that…Just one stupid question (since I followed your post exactly), for peace of mind, what is the best process for verifying the migration was successful?
It’s noon on a Sunday, all my CA skillset is horrible…Thanks …/Mike
27/01/2020
Request/Issue a certificate is the simplest way to test the system. 🙂
29/01/2020
I’m about to do this migration but i do have a question. Do i need to export the Certificate Templates from the 2008r2 server and import them into the new 2016 server? I cant find anywhere online if that is needed to be done
29/01/2020
I think I mentioned this above, templates are stored in Active Directory NOT on the CA
P
04/02/2020
Thanks you for this article. I am retiring a site hosting a virtual subordinate CA server. I am wondering if cloning the CA server, restoring it to the new VM infrastructure and re-IPing will cause an issue? Or, build a new CA in the new site and following your above process. Thx so much.
04/02/2020
As long as you don’t change the server name, and remember to add the new subnet to ‘AD sites and services’ you should be ok 🙂
12/03/2020
Hi Pete, this is a great article. Thank u for replying to all guys. I have a question ref migration from CA 2008 r2 to 2016. After we remove the CA role from the 2008 r2 dc and install on 2016. We want to keep the old server as it is a DC for maybe a few weeks after the migration. Is it necessary to power off the server after CA migration or can we simply keep it running without the CA role and act as a backup DC? Appreciated
13/03/2020
No the old server can remain, that’s fine as long as i’ts got a different name of course 🙂
18/03/2020
Hi
Thx very much for your wonderful article.
When moving from 2008r2 to 2012r2/2016/2019 AND with different hostname is it required to reissue the template certificate ?
I see as per official microsoft doc that is a require step BUT You don’t mention it on your article
18/03/2020
NO templates are stored in AD! (I’ve updated the article to show you where).
P
18/03/2020
Like many I have a PDC that is AD CS. I would like it to remain the AD CS and remove AD DS. Is there any reason you can think of that I wouldn’t be able to transfer the FSMO, demote and remove ADDS and leave the CA installed?
19/03/2020
None at all, what you propose wont be a problem 🙂
02/04/2020
I don’t think you can Demote a DC while its a certificate server
02/04/2020
You are correct attempting to demote a DC running CS will result in it stoping, and asking you to remove Certificate Services first.
P
03/05/2020
Hi, is it supposed that is possibile to demote the OLD DC holding the CS AFTER the migration on the new server (with different hostnames) . In other words: is it safe to remove the cs service from the old server once the new server with the new cs is up and running in production ? Thx
06/05/2020
You cant demote a DC if its a CS Server it will not let you. Migrate CS, when that’s done demote the server.
01/04/2020
Hey Pete,
First off, a big thanks the excellent guide.
I was just wondering if you also know if I could change the displayed name in the CA management console, just so no confusion arises amongst my coworkers for example.
Changing the ‘Active’ and ‘Common Name’ REG_SZ keys in the Configuration registry settings as well as the name of the registry folder caused ‘file not found’ errors when trying to restart certsrv.
Would be awesome if you know a trick for this!
02/04/2020
This is why I name my CA’s differently to the Hostname(s) they are residing on 🙂 ASFAIK (and I’m happy for someone to pitch in and say I’m wrong,) you can’t change a ‘CA Name’ You would need to remove it an create a new CA, which has many other inherent pitfalls in a working domain.
02/04/2020
Thanks for the excellent article and video Pete. I will use it for our next migration
18/01/2021
Thanks for a great write up. It’s very clear and concise. I also appreciate the time you have taken to answer and answer again all the posted questions. You have more patience than I have.
09/04/2020
Thank you for the article, great help, i did notice on the server that you were migrating to that Active Directory Services was also selected in the screenshot, is this required? I am migrating the CA from an existing Domain Controller which I am also demoting, i believe that this needs to be done prior to that. With the new server, i just want to confirm if AD services are also required?
10/04/2020
No it’s not, that was done on the test bench and it saved me building two servers.
11/04/2020
Hi Pete
As suggested just trying to the backup of certificate server on windows 2008R2 ent. But wizard completes with an error that some of the CA server certs private key is unexportable. I even checked the certs in certificate MMC for computer account and cant even export them from there.
Error is like windows cannot backup one or more private key because CSP doesnt support key export.
would you know something about this.
thx
shishir
25/04/2020
Thank you Pete for your detailed articles and they have been a life savor!
I have recently moved a Windows 2008 R2 CA to a new Server 2019 OS with a new host name. The move went well with one major issue. I am unable to create a SHA-2 CA cert and on SHA-1. This is causing all of our internal sites and other issued certs to issue Weak Cipher warnings and other issues.
I noticed in the registry the item “CAServerName” has the imported old 2008 R2 OS host name since that was exported and imported into the new 2019 CA. Is it safe to stop the certsvc, update the Reg key “CAServerName” and start the service if this is already issuing certs?
The CSP Reg key already has a CNGHashAlgorithm of SHA256 and Provider of “Microsoft Strong Cryptographic Provider” data set.
28/04/2020
I’ve covered upgrading CA’s to SHA2/256 elsewhere on the site?
12/05/2020
Hi Pete,
Is it possible to migrate a subordinate CA before RootCA? I am planning a migration for CA roles from 2003R2 to 2012R2 and wondering if I Can migrate the Subordinate CA server before the RootCA server?
15/05/2020
Technically yes, as long at its SubCA certificate stays in date through the procedure, but I’ve never done it that way.
12/05/2020
Excellent post and I really admire the way you addressed everyone’s questions:
I have a question…
For future management and ease of upgrades, we wanted to separate CA from a 2016 serverA DC, which is also has other roles like (DHCP and DNS), to a newly built 2016 ServerB,
1. Is it possible to keep both ServerA and ServerB After migration following your post?
2. If it is a must to rename the source server ServerA, what would be your suggestion/recommendations? s there a clean way to do it?
15/05/2020
1: Yes
2: Assuming it’s not doing something important (like Exchange or SQL for example,) then simply rename the server, (and then reboot it, to reregister its DNS entries). Then check your DNS servers do not have any old ‘static entries pointing to the ‘old’ name.
13/05/2020
Man I am dying here…
Cannot renew NPS Cert. Because the CA Certificate templates was showing the server I was going to move it to I thought that was probably the problem. So I went ahead and moved it to that machine even though it isn’t where I would like it to reside. It is now on server2 and the templates reflect server2 but I still get the same error when NPS trys to renew. “The requested template is not supported by this CA”. A valid certification authority (CA) configured to issue certificates based on this template cannot be located, or the CA does not support this operation, or the CA is not trusted.
Man I could use some help. There is so little info on the internet.
13/05/2020
Figured it out. For some reason the Backup and restore process did not restore all of the Certificates to Issue area of the CA, and since I originally set it up 7 years ago an essential piece of basic CA setup was forgotten. Although the template for NPS radius was in manage certificates, it was not in the main window when clicking on the manage certificates folder for certificates to issue. Now in my defense, this was available in the certificates to issue area of the original CA. Why it didn’t transfer with the backup/restore process i do not know.
13/05/2020
When moving CA back to 2012 Server that is now NOT a Domain Controller, The ability for the CA to issue an NPS RADIUS Certificate goes away. When you manage certificates you can see the template, but you cannot add it to the Templates this CA can serve. It would appear for a CA to issue NPS Radius Authentication Certificates, the CA must reside on a DC.
15/05/2020
I’m pretty sure the CA does NOT have to be a DC, in fact in my example here, the CA and NPS server is on the same server and its NOT a DC and it worked? https://www.petenetlive.com/KB/Article/0000685
18/05/2020
Hi Pete
Hope you’re well.
Can i use this guide to migrate from a 2012 R2 to 2019 standard? The 2012 R2 is also a DC plus DHCP and obviously DNS so i’ll need to migrate all roles to the new 2019 Server
Thanks
18/05/2020
Yes treat each migration separately, and don’t move the DC role until after certificate services has moved, I’ve covered DHCP migrations, (use the search above) and DNS will move with the DC role.
18/05/2020
Hi Pete, great article and youtube video, thank you! I think you might laugh and cringe at the same time when you read this question. My boss threw me into the middle of their CA migration project and wanted me to finish it up, problem is they just stood up a brand new Root CA server while leaving the old Root CA still up and running (we dont have any subordinate CAs). They began creating new certificates for just the web servers we host on the new CA. After reading your article and many others I told them to pump the breaks!
My question is, on a scale from 1 – 10 how screwed are we? What would happen if we continued with the new CA and just turned off the old one? Would all the servers and client PCs auto enroll with the new CA? I just want to understand the implications of the direction we took. Thank you in advance.
18/05/2020
🙂 Theres no reason I can think of that you are ‘screwed’, essentially as long as your clients trust BOTH old and new root CA servers and the CRLS stay online then nothing will break?
18/05/2020
GREAT news to hear! As of right now all clients trust both CAs. So if we turn off the old CA and all the servers check in with GP, will they all auto-enroll with a new certificate from the new CA? No moving of the old database and reg key required?
18/05/2020
Yes, just make sure if theres a CRL stamped on certificates issued by the OLD CA Server, you will need to maintain that until all the certs issued from that CA server have expired, or are no longer needed.
02/06/2020
Thanks for sharing the steps to move CA, I need to move the CA root server from 2003 to 2019 OS and we have a CA subordinate which is on Active directory server, can follow the same steps for 2003?
Could you help me to upgrade the hash algorithm as well from SHA1 to SHA2.
02/06/2020
Wow 2003? Back then I wasn’t that deep into this stuff, I’d need to build it all in VMware and test it, Sorry I just dont have the time to work that out for you.
02/06/2020
Logically I think it is possible only I am worry about CA Database Jet engine whether it will be directly migrated on 2019 or I have to go thru 2003>2008>2012>2019, not sure but what is your opinion on this?
02/06/2020
Agree I’d go to > 2008 > 2008R2 > 2019 personally
10/08/2020
Keep in mind Microsoft’s upgrade recommendations. While it may be technically possible to upgrade in-place from 2008R2 > 2019, the new supported method is only upgrading from 2 versions back. (i.e. should only upgrade to 2019 from either 2016 or 2012R2)
https://docs.microsoft.com/en-us/windows-server/upgrade/upgrade-overview#which-version-of-windows-server-should-i-upgrade-to
01/07/2020
Hi there,
Many thanks for sharing your knowledge.
I am in a process of migrating our cert role from Server 2008 32bit, upgrade to 2008R2, then migrate the role to server 2016, but it seems that the architecture is not compatible.
Do you happen to know a way i could follow for this migration, please?
Regards
Tedy
02/07/2020
Ah OK – If you are 2008 x32 you need to migrate to 2008 x64, then migrate to 2008R2 (Google “Active Directory Certificate Services Migration Guide”)
16/07/2020
Thank you for the guide, like many others Im on the same boat working on upgrading RootCA with two SubCA and another RootCA their all in 2008 R2 and your guide is a great help in this endeavor. I have been reading a lot of guides and really I would like to side with caution and try upgrading them in stages from 2008 R2 to 2012 R2 then 2019 and instead of migrating/moving them to a new server or upgrading them one time to 2019. I dont think its an issue whichever route we take in place upgrade vs backup and restore to a new server but wanted to get your thoughts on it.
Also our DC is currently running on 2012 R2 would it be an issue if CAs are ahead?
17/07/2020
Hi Jonathan,
Indeed, you are only as good as you last backup! Your DC wont be a problem, and wont trip you up.
If you super cautious P2V (or V2V) the boxes and, sandbox the upgrade to test it first.
As you are at 2008R2 then theres no ‘gotchas’ as you are running on a newer DB, and wont be x32 bit.
Good Luck
P
21/07/2020
Successfully migrated ADCS, CA and CAWE from 2012 (DC) to 2019.
Thank you very much
08/08/2020
First of all, thank you for the article, very useful.
I have a different requirement, however: the environment I manage has a root CA (not-domain joined server) and a dependent subordinate CA, not autoenrolling. I need to get rid of both, as we have a new enterprise-wide offline root CA and in this particular environment I want to replace the existing subordinate CA with another having different root CA, different name (and different server name). The number of certificates issued by the old sub CA is quite low, indeed all of them need to be gradually ceased as well as the hosts requesting them (we are in a migration phase).
Can the new sub CA, depending on a different root CA (a new PKI, indeed), coexist with the dying PKI until all the old stuff is made obsolete? Or would the AD get messed by that?
Thank you very much.
11/08/2020
Yes of course, you can run the new alongside the old until such time as all certificates have expired to been revoked.
11/08/2020
Thank you very much for this Pete,
I re-read the article and comments here and had most of my questions answered. I do have a question however regarding moving the CA off of a domain controller that we plan on keeping around. Is it possible to keep the domain controller with the same name moving forward after migrating the CA services off of it over to its own member server?
Thanks again.
12/08/2020
Either will work 🙂
14/09/2020
Hi Pete,
We’re planning to migrate our CA from 2008 R2 Ent server to 2019 DC. Just a couple of points, as I haven’t done so in a relatively large/complex environment.
We also have NDESinstalled. Also SCEP service for Macs. Are there any consideration to be taken around this?
Also, what would be the rollback scenario of this (backup/restore to new server) scenario if things do not go at planned?
Thanks for your advise in advance.
15/09/2020
Awesome question – NDES can be a pain, especially if you are using it for anything Cisco related? If you are only using it for macOS then just check that it will support the cyphers in the new environment, macOS can be a bit picky (or more secure depending on your view). Id p2V the DC/CA Servers and sandbox them and give it a thorough testing before going live.
Good Luck
07/10/2020
Hi, Peter.
Thank you for the great article!
The CA I’m planning to move to other server is using HSM. So the Private Key is being kept on HSM and I will be able to export the key to the new server from HSM.
Do I still need to check the ‘Private key and CA certificate’ check-box when creating the old CA backup?
Thank you.
08/10/2020
I’ve not done the with an HSM – but I dont see why not?
17/11/2020
Hi Pete, great guide thank you! I have just followed to the letter and I cannot seem to create new templates, nor can I see the ones visible. This is in a lab environment which I tested moving from DC to its own dedicated server. Equally, the web enrolment references the old server which I cannot seem to change…I am not sure this migrates in the typical sense.
17/11/2020
Templates actually live in AD not on the CA server! If you migrated and can’t see them, the templates have not moved!
17/11/2020
Thanks for such a prompt response. I can see the certificates on the DC via ADSI edit. When trying to Manage the templates I get an error “Windows could not create the object identifier list. The specific domain either does not exist or could not be contacted. Certificate templates are not available.”
Any other nuggets of help would be highly appreciated.
17/11/2020
And the new server is a domain member, and in the correct AD groups, and has the correct DNS settings, and you are logged in as an admin?
23/11/2020
Hi Pete, echo everyone else’s thanks for a clear, concise article/video and for taking time to answer follow-up questions.
I recently moved a domain off an old SBS 2011 server to 2012R2 Standard. I followed your steps to migrate the CA and it all went swimmingly… or so it seemed, until I realized that all of the existing certificates now have invalid CDP paths. This was of course after removing the CA role from SBS (in addition to every other role), removing it from the domain and powering it off for good.
I wish I had seen and followed your recommendations on setting up an http path way back when, but was (and still am) quite ignorant and just used the SBS default configuration, which only included an ldap URL for the CDP.
I’m wondering if I have any options other than reissuing all of the existing certificates. I tried setting a CNAME in DNS to point the name of the old server to the new one, but this didn’t appear to make any difference–perhaps that’s only works for http CDP paths?
Is there any way to redirect the ldap path to the new server? Or am I stuck with having to reissue the existing certificates?
Here’s what the CRL Distribution Points field looks like now on all the existing certificates:
[1]CRL Distribution Point
Distribution Point Name:
Full Name:
URL=ldap:///CN=mydomain-SBSServer-CA,CN=SBSServer,CN=CDP,CN=Public Key Services,CN=Services,CN=Configuration,DC=mydomain,DC=net?certificateRevocationList?base?objectClass=cRLDistributionPoint (ldap:///CN=mydomain-SBSServer-CA,CN=SBSServer,CN=CDP,CN=Public%20Key%20Services,CN=Services,CN=Configuration,DC=mydomain,DC=net?certificateRevocationList?base?objectClass=cRLDistributionPoint)
Seems the problem is the CN=SBSServer part.
Many thanks.
24/11/2020
http CDPs you can just setup a new one with the old URL. LDAP ones will only be a problem if the web CDP does not work, I’m pretty sure it does not need to check all of them?
17/12/2020
This is hte second time I have used this post to move my CA. 6 Months ago to a temp server, now to a new server. This time however the server is 2019 and it broke my NPS. I added a new host after moving the CA and it got a certificate. The NPS worked for 36 hours but fails now because the CRL is not found. Even the new host, with the certificate issued by the new server is failing. Not much info out there on how to fix this. ANYBODY???
14/01/2021
Hi Pete, great post!
I’ve adopted a network that has a CA on a 2012 dc. While doing the backup, I got the message that one or more private keys could not be backed up because the keys cannot be exported. It turns out they are the CA’s main 2 certificates also mentioned in CACertHash in the registry. I can’t seem to export them with their private keys. I am not aware of any passwords for them, as the previous admin was not big on documenting. Can I still restore the CA with the information that was able to be exported, or would it come down to creating a new CA?
Thanks man!
14/01/2021
It it were mine I’d build a new PKI infrastructure, take a note of the last issued cert expiry date of the old one. Then kill the old one and remove it from AD at a sensible date.
(Stop and disable the services on the old one to stop it issuing new certs!)
26/02/2021
3 Windows CA servers – needs to consolidate into one
—————————————————-
Currently, we have 3 CA servers (two Windows 2012 servers one of which is also DC and one Windows 2016). We would like to export all active certificates from two Windows 2012 servers and then remove CA services from those two servers. We just want to have one CA server – Windows 2016. Right now, all three servers are issuing certificates. When we have new computer setup, any one of these CA servers issue the license.
On first Windows 2012 CA server (also DC), it has about 1300 certificates with 900 already expired (so about 400 active).
On the second Windows 2012 CA server, it has about 800 certificates and half of them are already expired.
On 3rd Windows 2016 CA server that we would like to keep, it has about 900 certificates with 450 already expired. What is the best way to handle this situation? Any recommendation would be greatly appreciated.
01/03/2021
I’ve never ‘consolidated’ CA’s I’d migrate one and let the others expire.
19/03/2021
Hi There Pete,
Firstly, thanks for the article and all the helpful reponses in the comments.
Just one question about a computer name change – what about the dNSHostName value stored in AD?
AD sites and services > Public key services > Enrollment Services > CA name > Properties > Attribute editor tab.
This is the dns name clients will go to, to enrol their certs right? So i imagine this would need updating?
Or does this get updated when the service is reinstalled and the registry restored?
Cheers
19/03/2021
ASFAIK thats the CA name, though it might look the same as the servers DNS name it’s not?
19/03/2021
I used this once before when we had a DC fail on us. This weekend I will be doing the same again moving DC’s to another site using your guide.
Just to say thank you for putting this straight forward guide together it saves a lot of headaches.
19/03/2021
Thanks for the feedback Christopher
21/04/2021
Another great guide for real world use. It made the migration process quick and painless. I am a consultant and use your articles quite a bit for project work. Thanks for all of the time and dedication that you devote to sharing knowledge with others. Its very much appreciated.
26/04/2021
Thanks Bob
19/05/2021
Worked fine for migrating from 2003 to 2012R2
in that case, the cert format has p10 ext.
Thank you very much!
06/06/2021
Very clear tutorial!
I’m doing like Itzik, migrating from 2003 to a temp 2012r2 then finally reach a 2019. But this SBS2003 have not been maintained for years, It’s not possible to export the certs because the the ca service is not running since in the SBS since the certificates are expired, the backup is a must? Or its possible to install the CA in the 2012r2 and configure it from the scratch?
21/06/2021
This was a fantastic article…and the YouTube video that accompanied it was really helpful as well. In my adventure to cutover my CA from 2008R2 to 2019, I found a couple of things and would be curious as to if my observations are accurate.
1. The old CA had an expired certificate still associated with the Certificate Authority (#0) with the current certificate in spot #1. The backup didn’t include the private key with it (it was expired, why would it?). When I imported the registry, the certificate services wouldn’t start. I had to go into the registry and replace CACertHash value and replace the expired certificate #0 thumbprint with a dash ‘-‘ on the first line, with the certificate #1 hash remaining on the second line. Then the certificate services would start up.
2. I was unable to get OCSP going because all my templates in Active Directory (other than what was built-in), were unable to be published. I had to go into ADSIEdit and change the Services>Public Key Services>Enrollment Services>-ca name- flags value to 10 (it was set by default on the new server to 2), replicate AD, and then restart certificate services for the templates to be issued by the new CA. I guess it’s a known bug since 2008 that occasionally pops up.
23/06/2021
Thanks for the feedback! Glad we could help you out.
19/07/2021
Hi Pete,
No doubt best article on migrating a CA out there. I have 2012 DC CA server. I’m seeing errors on the server and want to move the CA to a member server and remove the old DC server. I have NPS install on another DC server. Do you see any issues with moving the CA to a member server and breaking NPS?
21/07/2021
If the NPS is just doing RADIUS/EAP/EAP-TLS then no.
P
20/07/2021
After completing this I could not issue any of my custom certificates.
Turns out I had to change the flag below using ASDIEDIT from 2 to 10.
ADSI\Configuration\Services\Public Key Services\Enrollment Services\right sub CA name->Properties->flags.
21/07/2021
That not tripped me up before? But thanks for the heads up Linda.
21/07/2021
One more note that may help someone in the future:
Scenario – Migrate CA server from 2012 R2 to 2019 Server; moved NPS from 2012 Server to 2019 Server. Everything seemed to be working, but when clients when to connect, NPS was rejecting them with error “”Error The revocation function was unable to check revocation”. Everything looked operational. Solution: On the CA, open PowerShell and run Certutil -crl then went into C:WindowsSystem32CertSrvCertEnroll and copy the new CRL certificates from this folder to a location on the NPS server. On NPS server, open MMC, add Certificates, Local Computer snap-in, and import these certificates into Trusted Root Certificate Authorities. Restarted NPS; clients could now connect fine.
05/08/2021
Hi Pete
Great write-up, but I have experienced issues. I just tried this in production. Everything seems to work okay until I import my registry key from my old (2008 R2) CA. As soon as I do, Certificate Services stops and when I try to restart it, I get an error:
The system cannot find the file specified. 0x2 (WIN32: 2 ERROR_FILE_NOT_FOUND)
The policy module for a CA is missing or incorrectly registered. To view or change policy module settings, right-click on the CA, click Properties, and then click the Policy Module tab.
Any ideas what in my Registry Key could be causing this issue??
25/08/2021
HI Pete,
Thanks for this. Once you move over how do the machines in the forest about the new certificate server? Do we have to use a GPO to point them to the new server? I must addmit when it comes to PKI stuff I am completely at sea and I would like to understand a little bit more as to how the new server is known by the rest of the members of the AD domain. Thanks.
21/09/2021
If your in a domain environment they will pick it up automatically.
31/08/2021
Thank you for the comprehensive write up, greatly appreciated.
I’ve followed the documentation, but it seems the custom templates I created aren’t showing up after the migration. I read in some of the previous comments that some time is needed for the templates, but it’s been a couple of days. Any advice as to how I can fix this?
This all in a lab environment, but would be great to know just in case this were to happen in production.
21/09/2021
The templates exist in AD rather than on the CA server? Can you manually add them?
08/09/2021
Great article, thanks for the walkthrough.
Now, I read it through in a rush and missed the part about exporting the registry file before removing the old CA role.
I’ve been into the reg on the new server and changed the CAServerName by hand while the service was off, is this going to break anything?
21/09/2021
I’ve never had to do that myself – but I ‘think’ you will be OK.
18/11/2021
Hey Pete, hope you’re well..
I had an issue with my CA server, where even a DC at the same network range cannot renew its certificates and returns a stupid RPC error. no Network or Firewall issue.
I’ve migrated the CA to a new server, so maybe things start to work again, but the results are the same..
It’s an inherited environment, and the CA were moved from a 2k8 server to 2k12R2 before. not sure if all the CA feature-roles were migrated or not.
symptoms are just like this:
https://social.technet.microsoft.com/Forums/windows/en-US/67492ab1-fa7d-48fd-9d88-e46b1fca61cc/certificate-enrollment-for-local-system-failed-to-enroll-the-rpc-server-is-unavailable-0x800706ba?forum=winserversecurity
except problem is not Policy! that is mentioned there..
I hope you can give me some advise on this
25/11/2021
I’m experiencing the same issue. I’ve been at this all day. Any ideas from anyone else?
06/12/2021
Thanks for the guide, very useful, thank you!
I’ve had a slightly weird issue on this, would love to know your thoughts! I set the permissions as per your article on setting up a CRL (https://www.petenetlive.com/KB/Article/0000957), but was still getting access denied when publishing my CRL.
I discovered that under the ntauthority\system account I could write to C:\CRDL, but not the share \\machinename\CDP$ (Access denied).
What worked, in the end, was adding the SYSTEM object to the share permissions, this then worked even if I removed the machine object domain\machinename from the share permissions. Ie. my permissions are ‘Everyone : Read’ and ‘SYSTEM : Full control/Change/Read’
Is this something you’ve come across before?
My previous AD CS (on WS2016) was a domain controller, configured exactly as in your guide on CRL setup, so not sure if that has any bearing on things? Do those computer accounts behave differently, perhaps?
Current machine is a fresh built 2019 server, domain joined and with the roles as described above.
All working, but slightly nervous whenever I don’t know *why* something is working!
08/12/2021
Hi Daniel,
I’ve not seen this but it will help someone, thanks for the feedback!
P
05/02/2025
Same. It’s not enough to give ComputerObject Full permission for me on WS2022.
Access denied. Works only when:
1. I give share full/modified permission to Everyone
2. Or adding SYSTEM full permission
09/12/2021
Hi Pete,
Thank you very much for detail guide.
I have one root CA server (Windows 2012) and one issuing Sub CA (intermediate CA) server (Windows 2012). I am going to migrate them to one root CA (Windows 2019) and two issuing Sub intermediate CA servers (Windows 2019). Two issuing Sub CA servers are not in Windows cluster. They are in different data centers for redundancy purpose. They are in one AD tree.
I do not want to decommission existing issuing Sub CA before testing new issuing CA servers.
Below are what I want to do:
1. Export issuing Sub CA from existing server (Windows 2012)
2. Add two new Sub CAs servers (2019) in the AD tree
3. Import backup Sub CA cert from step 1 to two new Sub CA servers. There will be three Sub CA servers with same Sub CA cert in the AD.
4. Test new Sub CAs in NDES server to see if the existing issued device certs are working and new cert can be created.
5. After successful tests, change NDES to use two new Sub CAs servers and decommission the old one (Windows 2012).
Do you see any issue with above procedures?
Will Step 2 and 3 cause any issues to existing Sub CA (Windows 2012) since they have same Sub CA cert?
Thanks in advance!
Hong
09/12/2021
You approach seems sensible, just be careful with the NDES – who are your NDES clients? Some Cisco equipment requires old signing algorithms and it’s ‘problematical’ to troubleshoot, why it does not work. I’d work through that on the test bench to make sure a modern CA will give you the NDES/SCEP service your clients require before migrating over.
19/01/2022
I would like to migrate the certificate from 2008R2 to 2016. Do I face any issue if the new server has the new name. In that case, how clients machine will understand the new certificate since the client machines are configured with OLD cA server name. Please assist.
20/01/2022
Server names are not important, it’s the CA name that’s important that should not change – the CA name might look like the old server name, but if there’s two people called Bob Smith they are not the same person. If we shoot the second Bob Smith the first Bob smith does not die, and his mail still gets to him.
20/01/2022
We are testing this in the lab. Getting this error when we attempt to publish the Revoked Certificate. “Access is denied 0x800700005 (Win32: 5 ERROR_ACCESS_DENIED).” We added the computer name to the share and ntfs permissions with full control. Any thoughts?
21/01/2022
Great article. But what do you do when you want to migrate from a sub domain into root of the forest?
I migrated succesfully but when accessing the web portal I get a certificate mismatch. In the certificate, under “issuer” the sub domain is listed under “DC”. Any new certs issued also include this in the path.
24/02/2022
Has anyone tried this moving the CA from 2008r2 to 2022standard with a new name?
15/04/2022
Awesome write-up, thanks Pete. Wanted to grab your brains if I can. In my environment the vendor originally installed 1 offline Root CA and 1 sub-CA (domain member) both running 2012R2.
Then after some time another Enterprise PKI server 2012R2 was installed. All 2012R2 servers need to be upgraded to 2019. I am planning to follow your recommendations to migrate the Root CA first and then sub-CA and also get rid of enterprise CA server as it just complicates setup. What is your advise on removing enterprise server and steps? Do you see any impact?
Thanks, Ed
20/04/2022
I’d simply decomission it and leave all mention of it in AD, just in case it;s issued anything important!
P
05/05/2022
PeteLong. I have created 2 new DC’s for my buisness. Microsoft 2019 for both. Upgrading from 2012 R2. All has gone fine. I have the roll’s running properly on both new DC’s and they are working just fine. My last step is to cross over my AD CS. What I didnt bother to look at was what DC ran the CS. Well come to find out both of my 2012 DC’s (DC01 (old one) and DC02 (Old one) are running the CS roll’s. I have certs on both old DC’s. I want to put CS roll on my new DC2 (2019) and move my certs to it. What problem I have before I pull the trigger is. I can use your instructions listed above to move the CS roll form (old) DC02 onto (2019) DC2. and I believe I can do this without problems. But how do I get just the certs from (old) DC01 off, and onto DC2 so I can shut down both CS services on the old DC’s? Any help on this would be much appreciated. Thank you so much.
06/05/2022
OK so the question is “what’s left nn DC01” and do you need to keep it? If it’s an enterprise CA your clients will be getting it’s root CA from AD and will continue to trust certs issued from it (for the life of its RootCA cert anyway). So what you actually losing is the ability to ‘revoke’ certs that DC01 issued.
09/05/2022
So what your saying is I should be able to just shut down DC01? Leaving everything as is? and just work at crossing over DC02?
11/05/2022
As long as there’s no CRL paths pointing to it. (look on the issued certs to check)
15/07/2022
Great article Pete! Many thanks for that!
What’s the reason you wrote to remove CA role service first and after that the ADCS role itself?
“REMOVE all the CA role services first! > Complete the Wizard, then launch the wizard again and select ‘Active Directory Certificate Services’ > At the pop-up select ‘Remove Features’ > Next.”
15/07/2022
Yeah – not sure why I wrote ‘first!’ – I’ve removed that.
P
19/09/2022
Awesome article Pete!
We’re planning to follow the above guide to migrate the current CS role from server A to B, our CS role is primarily for 802.1x authentication for wireless clients. Can you foresee any issue with the proposed CS migration to Server B which will eventually become the PDC with NPS installed?
Server A: 2012 R2 (PDC) with DHCP, NPS, DNS, Print and others
Server B: 2022 (DC) With DNS, Print, Files Shares and NPS roles installed
21/09/2022
Not really – unless NDES is in the mix?
05/10/2022
After the migration to a new server, is there any issue in keeping the old server running?
06/10/2022
Not that I’m aware of?
19/10/2022
hi,
I am planning to do a snapshot then do an inplace upgrade from 2012R2 to 2019. anyone tried that ? would there be any problem doing it? if things go wrong would i be able to restore the snapshot.
R
21/10/2022
Hi Ahmed,
Great question! I’ve not done that myself although I did an article o 2012R2 > 2019 in place upgrades the other day. I’d be really interested to see how that goes. Please feed back.
21/10/2022
Hi Pete,
i just finished upgrading the server and all looks good/green with no issues at all. Tested joining a computer to the domain and testing requesting a certificate from a template.
1- took a snapshot
2- uninstalled the graphics driver (windows 2019 doesnt like vmware graphic driver for 2012R2)
3- uninstalled microsoft antivirus (the old one)
4- took a backup of the certificate database and the registry files
5- took a backup of the firewall rules (i upgraded many 2012R2 and some lost their filewall rules so took a habbit orf backing up the rules just in case.
6- mounted the 2019 ISO and ran the setup. after one hour everything was running fine.
R
Ahmed
26/10/2022
Awesome, thanks for the feedback!
Pete
21/10/2022
Hi Pete, thanks for the great article,
I do have a situation, where I migrated a SUBCA from an Active Directory Subdomain to a root AD domain, changing dns hostname and keeping the CA Name.
When issuing certificates to servers from the newly migrated subca, the Certificates contain in the Issuer Field the old cn of the the subca, like cn=subcaname, DC=sub,DC=dom,DC=pki.
Regards Sidney
21/10/2022
Remember the CA name should not change, so that’s normal behaviour.
24/10/2022
Hi Pete, thanks for the great article,
I do have a situation, where I migrated a SUBCA from an Active Directory Subdomain to a root AD domain, changing dns hostname and keeping the CA Name.
When issuing certificates to servers from the newly migrated subca, the Certificates contain in the Issuer Field the old cn of the the subca, like cn=subcaname, DC=sub,DC=dom,DC=pki.
Regards Sven
26/10/2022
Thank you and Thank you – I am migrating 2003 CA server to 2012 R2 server (I know, ugh) and you have answered so many of the questions my boss will be asking me. I feel so much more confident after reading your article and these questions/responses. You ROCK!
26/05/2023
Hi Pete,
I’m a PKI rookie who is working for a client that want their Root CA and Enterprise CA migrated to Server 2022. I was wondering if this guide would be suitable to follow for both CA servers?
Another question I had, is it required for me to uninstall the ADCS role on the old servers BEFORE I install ADCS role on the new servers? Reason I ask this is because this is a production environment and me being a rookie in the certificate world, would be in a world of trouble if something breaks after the uninstallation of all the CA role services on the old servers.
Thanks a ton! I really appreciate all the help and knowledge you’ve shared with the community!
30/05/2023
Yes it would be suitable as long as the source is newer than 2008
Yes you DO need to uninstall the role off the old server first.
05/06/2023
Thanks so much Pete,
I’m migrating one NPS server as well from 2012 to 2022. Would there be any special considerations to keep in mind after I migrate the CA servers? The guides online are seemingly very straightforward for an NPS server, exporting and importing the NPS configs but I was wondering if there is anything else I should look out for? (certificates that are already issued should still work)
06/06/2023
Good question – NPS on its own should not present a problem, if the exisitng certs were a problem they can be simply renewed
20/06/2023
I am doing the same as Austin but our current CA and NPS roles are on the same 2012R2 server. Is it advisable to separate these roles onto two separate servers or is it okay to stay with the same setup and just migrate both to a new server?
27/06/2023
Your choice – I see no danger or merit in doing either?
07/07/2023
Hey Pete, loved the detailed guide. Used it for migrating my standalone CA from Server 2012 R2 to Server 2022. One thing I faced an issue was the New CA custom templates not appearing to be issued. Easy fix. Just need to make sure on the new CA Server that you add Domain and Enterprise Admins to the Local Group “Certificate Service DCOM Access”. Once I did that, any new templates I made worked like a charm. Guessing it is a good step to include, as it is easily missed and takes a while to figure out.
10/07/2023
Cheers Scott
11/07/2023
briliant! made it to migrate my CA; the destination server was a core server so we end up the restore process with the certutil command as the gui cant be used in that case, thanks!!!
26/07/2023
this was one of the most detailed guides I have seen in my years as an IT googler of solutions.
the steps were clear and the screenshots very helpful. now to wait and see if something is broken
04/08/2023
Hi Pete, I have a 2012 R2 Enterprise root CA in a sub domain. We’re decommissioning this sub domain in the near future.
I would like to move this CA into the parent domain. Using a sandbox for testing, during the import of the CA, I get an error “The imported cert does not match the chosen CA type”. I’ve tried all types.
The first time I tested this it appeared to be succesfull but, received an error of mismatch cert, also the issuer and subject both point back to the path dc=sub domain, dc=rootdomain.
If succeful import – what happens when the sub domain is decommissioned?
If failure of import – can I just rebuild a new CA server and what are the steps to rebuild?
Thank you so much in advance.
07/08/2023
I’ve never attempted this – I’d suggest you simply build a new CA on the root domain (https://www.petenetlive.com/KB/Article/0001309) and before you blow away the existing CA, get your root domain to trust its CA cert so if there’s any overlap at least the issued certificates wont error (assuming there plenty of life left in the CA cert of course).
07/08/2023
Couple questions.
Have you heard of any issues with migrating from 2012R2 to 2022? Seen plenty of guides to 2019, but I just want to know if there has been success with going to 2022.
Second, after the migration, the hostname will be different. Can we just add another DNS alias to the new server’s IP to make sure there are no problems with certificates referencing the CDP? I ask because ideally we would want to decommission the old CA after the migration is done. Would hate to keep an old 2012 server just for the CDP. Reissuing all of the certificates after migration would not be possible in our environment considering how many thousands are out there in use. Some are auto-enrolled through AD and others are manual requests.
07/08/2023
1. I have seen no issues – anything after 2008 is pretty much the same all the way up to 2022
2. Yes you can ad an A host record or even a CNAME to cover the naming difference – REMEMBER check you CDP entries they are not always URL related – you might have one that’s points to a service record in AD – just look at an issued certs properties to make sure.
07/08/2023
So we just have the two CDPs on our certificates. I would imaging just updating DNS for the new hostname to add the old hostname as an alias should work. Would we need to update something in AD as well?
Our URI is a separate web enrollment server that should be unaffected other than having to update the WebClientCAMachine value on the web enrollment server to point to the new CA hostname.
ldap:///CN=CAname,CN=oldserverhostname,CN=CDP,CN=Public%20Key%20Services,CN=Services,CN=Configuration,DC=domain,DC=com?certificateRevocationList?base?objectClass=cRLDistributionPoint
URI: http://location.subdomain.domain.com/CertEnroll/CAName.crl
16/09/2023
Good morning,
Great article!!, it has helped me a lot.
One question, is it possible to have two root CAs on a Windows server?
Thanks greetings.
18/09/2023
Not that I’m aware of, why would you want to do that?
18/09/2023
Hi, you didnt mention anything about the root ca or sub ca in your guide.
Is there any steps you have to take on the root ca, to confirm the new sub ca is allowed to issue certs?
Thanks
18/09/2023
Hi Bob the root CA is a CA, SubCAs get thier auth from the CA above them, move the root CA first then any sub ordinate CA afterwards.
18/09/2023
Thanks Pete.
Our root CA is on server 2019, our sub CA is 2012. That is the reason for the question. The root is staying put.
18/09/2023
Understood – so the CA Cert for the SubCA will have bene ussined by the RootCA, – so you need to migrate the SubCA – (which is essentially moving the CA name and the SubCA cert to a new servers – (which can be called whatever you want)).
18/09/2023
Ok thanks. Do we not need to change anything on the Root CA though?
E.g. is there not a trust relationship between the Root CA and Sub CA and will we not need to update the Root CA to have a new trust with the new Sub CA?
19/09/2023
No as long at the RootCa is the next cert in the subCA certificate chain
19/09/2023
If we have a 2 Tier PKI setup , one offline ROOT CA ( Windows server 2012) & online CA ( Windows server 2012). Does it matter if I upgrade the online CA server first?
Kind regards,
Johnny
20/09/2023
In all honesty – I dont think so, as long as you retain the SubCA cert on the online CA and the SubCA name remains the same name. I’ve not done this in anger though, I usually start at the root and work downwards.
03/10/2023
Awesome article, thanks for writing it.
I was wondering if AD replication needs to be taken into consideration when removing the role from the old server and then installing/restoring on the new server?
We have remote sites on a longer AD replication time, so should we manually start a replication after removing the old server role? Or does this not matter?
20/10/2023
Valid point – but the tmeplates are stored intenrally in AD anyway and the internal LDAP referneces dont change – I would guess it does not matter (but that is a guess!)
15/01/2024
Thanks Pete.
Worked like a charm from 2012R2 to 2019.
04/03/2024
Pete,
Have you ever since this message before?
“The imported certificate does not match the chosen ca type and will not be used. however, the imported key can still be used.”
I was following your steps for migrating the CA from Server 2012R2 to Server 2022. I am selecting the correct CA type, which is enterprise and root. But for some reason this message just keeps popping up and can’t continue the process unless I fix that first.
25/03/2024
I was about to follow your instructions to migrate our root CA and sub CA from 2012R2 to 2019/2022. I then found out that I could do in place upgrades. I made server image backups and did in place upgrades. Upgraded from 2012R2 to 2016 first with sub CA and then root CA. Let them run for a couple of days. Then upgraded sub CA and root CA to 2019 and let them run a couple more days. CA service works after the upgrades. Finally, I did in place upgrade to 2022. No issues were encountered. It took a few days to complete. Now I don’t have to worry about the OS for several years.
Post it here in case anyone wants to try the in place upgrades.
26/03/2024
Hi, I’ve mentioned this elsewhere (at least once here https://www.petenetlive.com/kb/article/0001761) As long as you observe all the other caveats for in place upgrades, then in-place upgrades of Certifificate Services / PKI (even multi level PKI deployments). Are a quicker and safer alternative. (Usual backup warnigns apply).
30/05/2024
Thanks for the detailed guide!
After migrating from an old 2003 machine to a 2012 R2, I’m seeing warnings in the event logs for CertificateAuthority 80. Is that something to worry about?
Active Directory Certificate Services could not publish a Certificate for request 36001 to the following location on server [redacted]: CN=[redacted],OU=Domain Controllers,DC=[redacted],DC=local. Insufficient access rights to perform the operation. 0x80072098 (WIN32: 8344 ERROR_DS_INSUFF_ACCESS_RIGHTS).
ldap: 0x32: 00002098: SecErr: DSID-03150E49, problem 4003 (INSUFF_ACCESS_RIGHTS), data 0
There is the same warning for all of our domain controllers
03/06/2024
Hmm normally you should go to 2008 then migrate to 2012 – though that looks like a certificate template persmissions issue TBF.
P
04/06/2024
That specific error hasn’t happened again – I think it just needed time.
I had a separate issue where some devices were still checking the old server for CRL and saying the revocation server offline. I’m not able to completely decommission the server yet (hopefully can within a week), so I put an http redirect in IIS on the old server to point \CertEnroll\ to the new server. That let all the old certs check revocation without error.
11/06/2024
We are inheriting a 2012 environment and migrating to server 2019 and have not worked with CA Servers previously. Is there a way to determine why one might have been setup a CA to begin with? And would, it’s not needed just remove that role?
12/06/2024
Look in issued certificates thats your best bet – see what certificate tmeplates are being used.
P
21/06/2024
I went ahead and followed your process above and moved the CA role. However, when demoting the old server, I receive and error message “Certificate Server is Installed” after clicking “Demote” to demote old DC. Thank you.
02/07/2024
All the roles have to be removed – and the server rebooted before you can demote.
20/09/2024
Amazing post, thanks!
How would you rename the Certificate Authority name (not FQDN) ?
Thanks!
24/09/2024
Dont! if you need another name buid a cnew one – and run them in parrallel.
03/10/2024
This article is brilliant, delighted to have found it.
I’m trying to get a RADIUS server set up to use for Wi-Fi authentication. As far as I have been able to figure out, this will require an enterprise CA be running somewhere.
We apparently tried this years ago, before I even joined the company. We have an old server running RADIUS and a CA concurrently on a VM running Server 2012R2. Aside from it being on a server that old, it’s also rapidly aging hypervisor we want to retire.
Thing is, I’m not sure if that old CA is actually doing anything at all.
The last certificates it issued were to our DCs in June 2024. There is a list of them all issued at various dates going back to October 2023 running through June 2024. All of them expired on the same date in June 2024. Some expired the same date they were issued.
No pending requests are present. There are several failed requests for the same period as the issued certs, all also from our DCs.
So, I guess two questions then:
1. Is this existing CA really doing anything at all?
2. Is the safest play to migrate the existing CA to a new server by the steps in this article?
Thanks so much!
07/10/2024
I’ve setup NPS/RADIUS to do this before (for Cisco WLC) https://www.petenetlive.com/KB/Article/0001420
>>Is this existing CA really doing anything at all?
Difficult for me to to tell – if you got to aDC and attmept to renew the Kerberos certificate doe sonr get issued from your CA? Or run this command certutil –config – -ping
>>Is the safest play to migrate the existing CA to a new server by the steps in this article?
It’s what I usually do, and its not blown up in my face yet!
04/12/2024
Hi,
I have a situation.
I’m new to the company and I inherited an old IT manager.
I set up a new domain controller. The old one was demoted.
But I didn’t know that there was a CA server on an old file server. That old server is down/offline.
Now I have a problem because the new domain controller is telling me that it is missing a CA server certificate.
Can I just set up a new CA role on that new domain controller?
12/12/2024
It’s better prictice to put it on a seperate ‘member’ server.
23/01/2025
Hello Pete ,Thanks for your valuable article
We have two tier PKI hierarchy as below
Offline Root CA ( WorkGroup )
Sub CA ( Domain Joined )
OCSP ( Work Group )
Can we follow the same process you mentioned above for Root and Sub CA and we are planning to use the same hostnames
Is there any challenges while backup & restoring the configuration and Certificate Templates
And I want to check the migration process for OCSP server migration , any configuration backup we have to take like CRL , AIA , help out with the Process
02/03/2025
Thank you. This just made my migration so smooth. 2012 R2 to 2019…flawless. Thank you.
10/04/2025
Great step by step, Move win2012 to win2022 with success
28/05/2025
I was able to follow your instruction and everything worked as it should but now when I try to request a new personal cert for kerberos authentication, I am getting a request denied about the request subject name is invalid or too long
28/05/2025
Not seen that myself have you had an Event ID 22 to look at, to give you any more information?
30/06/2025
Just done it without any issue from 2012r2 to 2022.
Thank you for the tuto Pete !!!
20/08/2025
This was very helpful! I inherited an infrastructure where CA services was installed on a DC. I had to install a new DC (server 2025) and followed your instructions – they seemed to have worked. However, although I can view the templates in AD using ADSIEdit, they are not available in the CA Services console – the error I am seeing is, “Template information could not be loaded: Element not found”. All the regular tests come back OK — so I’m a but stumped! Anyone seen this one before?
20/08/2025
What does running certtmpl.msc show you?
How old was the old DC/CA server? if it’s older than 2019, try extending the AD scheema.
Assuming it’s an entrpise CA?
-Run ADSIEdit.msc, then expand CN=Configuration | CN=Services | CN=Public Key Services | CN=Enrollment Services.
-Right click the CA in the right pane that you want to enroll from and click properties. Find the flags attribute;
-and verify that it is set to 10
Any help?