KB ID 0001471
Problem
This is essentially part-two of deploying encrypted virtual machines, in a vSphere VMware (6.5 and above) environment. Back in part-one we deployed a KMS server and registered it with vCenter. Now we will create a storage policy that enforces encryption, then apply that policy to a virtual machine.
Solution
While logged into vCenter > Home > Policies and Profiles > VM Storage Policies > Create VM Storage Policy > Give it a name > Next.
Next.

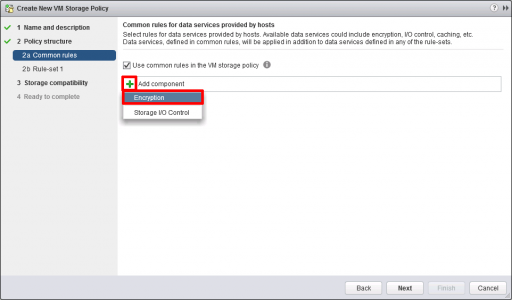
Add > Encryption. Note: On some versions of vCenter, Select Encryption > Custom.
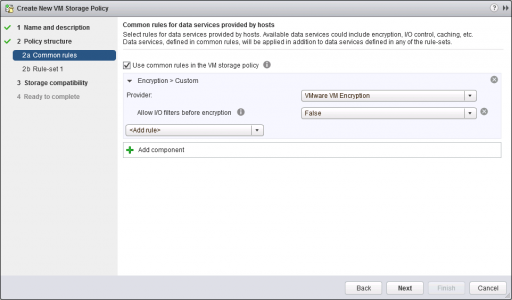
Accept the defaults > Next.
Untick “Use rule-sets in the storage policy” > Next.
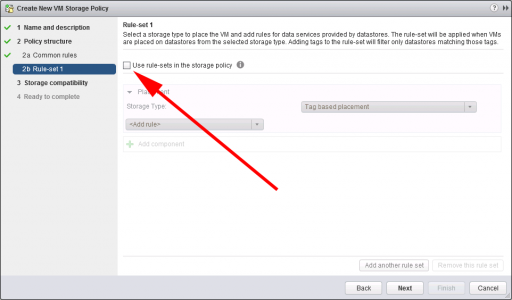
This just shows you which ‘Datastores‘ are compatible, (it’s not going to encrypt them, or format them, or anything!) > Next
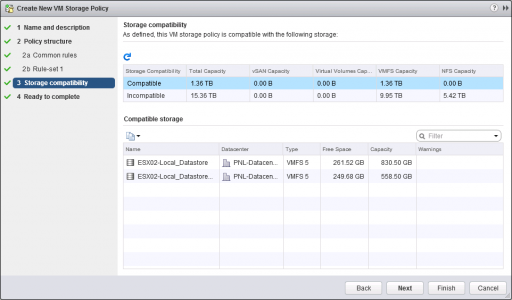
Finish.

Apply an Encryption Storage Policy to a VM
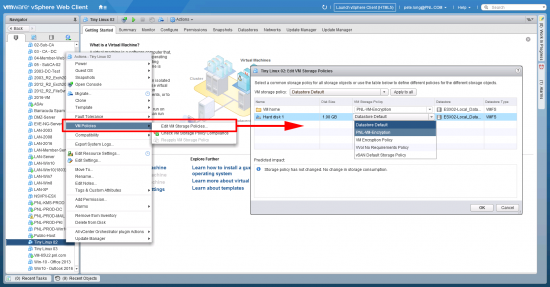
There are a couple of ways to do this. Before you start, make sure the VM is in a compatible Datastore > Right click the (powered off) VM > VM Polices > Edit VM Storage Policies > Select VM Home (to encrypt the entire VM), or the individual disks (to encrypt them only) > Change the policy to the encrypted one you just created > OK.
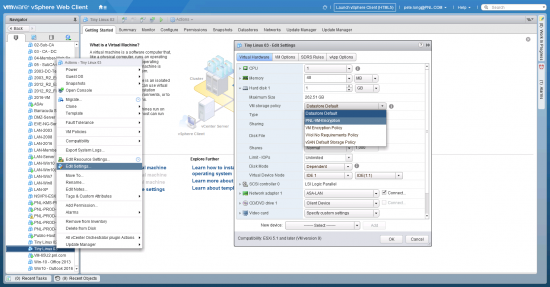
Or to encrypt the drives manually > Right Click the VM > Edit Settings > Expand the hard drive > VM Storage Policy > Change the policy to the one you created above. (Note: this only encrypts the drives, NOT the entire VM).
Check Virtual Machine Encryption
If a VM is encrypted then it will tell you on its ‘Virtual Hardware‘ tab, you will also notice that encrypted drives have a small ‘padlock’ over them.
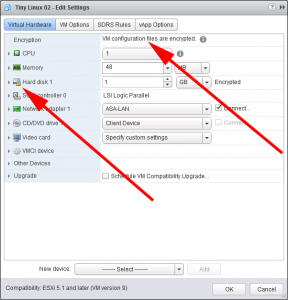
Additionally: Under VM Options, you will notice that Encrypted vMotion is now set to ‘Required‘.
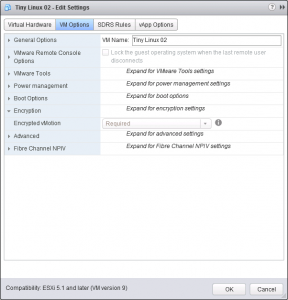
You can also tell at a glance from the virtual machines ‘Summary tab‘.
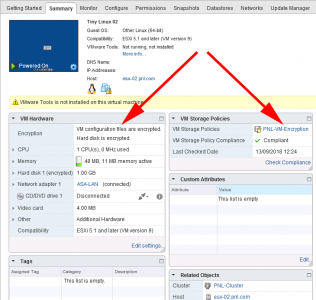
Things You Need To Know About Encrypted Virtual Machines
- To encrypt a VM it must be Powered off.

The attempted operation cannot be performed in the current state (“Powered On”).
- To encrypt an VM it must have No Snapshots.
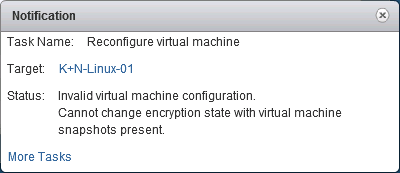
Invalid virtual machine configuration.
Cannot change encryption state with virtual machine snapshots present.
- Fault Tolerance is Not Supported.
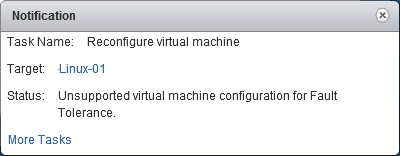
Unsupported virtual machine configuration for Fault Tolerance
- vSphere replication is Not Supported.
- Cloning Is Supported, but the cloned VM has the same encryption keys as the source.
- Snapshots Are Supported, but, you will see the following error if you attempt to snapshot of an encrypted VM.
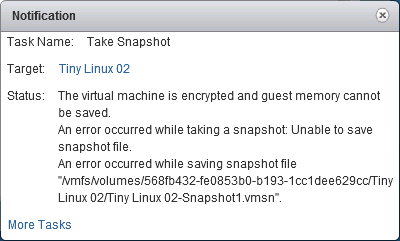
The virtual machine is encrypted and guest memory cannot be saved.
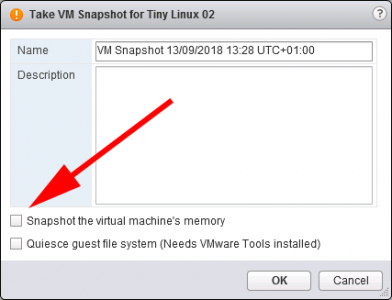
You need to ‘untick’, Snapshot the virtual machine memory.
- You cant ‘Suspend‘ an encrypted virtual machine.
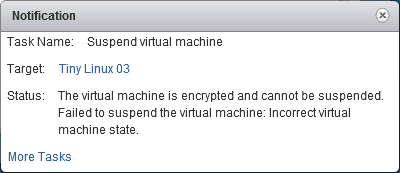
The virtual machine is encrypted and cannot be suspended. Failed to suspend the virtual machine. Incorrect virtual machine state.
- You cannot export an encrypted virtual machine to OVF file.

Provider method implementation threw unexpected exception: %s VapiStructureProxy.cause
The operation failed due to the operation is not supported on the object
Related Articles, References, Credits, or External Links
NA

03/08/2020
Say after 3 years you decide to change another KMS provider, with the encrypted VM, how are we suppose to move the config so it recognize the new KMS cluster?
03/08/2020
I’ve never done this, but I don’t see why you cant swap a KMS server out? It only checks the keys when you power on a VM.