KB ID 0001446
Problem
I’ve seen this pop up a few times in forums, and I’ve even seen people post “It cant be done, you will need to change one of the subnets,” but to be honest, it’s not that difficult.
We simply have to do some NAT. This is the bit people struggle with, with VPNs usually we need to STOP NAT being applied to VPN traffic, and we still do, we simply NAT the traffic before we sent it over the tunnel.
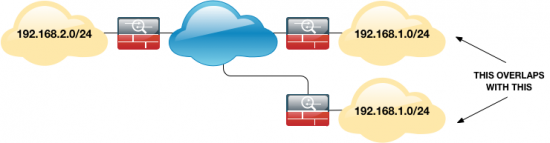
Normally overlapping networks can trip you up, in one of TWO scenarios;
Scenario 1 (The other end overlaps with YOU)
Scenario 2 (Two endpoints overlap with EACH OTHER)
Solution
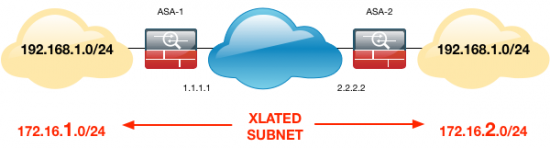
Scenario 1 (The other end overlaps with YOU)
Firstly you need to pick another subnet for BOTH ends, and this is the subnet the other end will THINK it’s talking to, sometimes this is called an XLATED subnet, or a PSEUDO subnet, or a MASQUERADE subnet.
ASA-1 Config
Firstly we need THREE objects creating, (instead of the usual TWO). Then take note the syntax of the NAT statement;
! object network OBJ-Site-A subnet 192.168.1.0 255.255.255.0 object network OBJ-Site-A-XLATE subnet 172.16.1.0 255.255.255.0 object network OBJ-Site-B-XLATE subnet 172.16.2.0 255.255.255.0 ! nat (inside,outside) source static OBJ-Site-A OBJ-Site-A-XLATE destination static OBJ-Site-B-XLATE OBJ-Site-B-XLATE !
Note: Above, I’m assuming your interfaces are called inside and outside!
Now you need to create the ACL that will be used to define ‘interesting traffic’, i.e. traffic that will be encrypted, but unlike normal you will specify the XLATED addresses.
! access-list VPN-INTERESTING-TRAFFIC line 1 extended permit ip object OBJ-Site-A-XLATE object OBJ-Site-B-XLATE !
The rest of the VPN config is the same as normal, here I’m using IKEv2. If you have to use IKEv1 see the link at the bottom of the page.
! crypto ikev2 policy 10 encryption aes-256 integrity sha256 group 19 prf sha256 lifetime seconds 86400 crypto ikev2 enable outside ! tunnel-group 2.2.2.2 type ipsec-l2l tunnel-group 2.2.2.2 ipsec-attributes pre-shared-key 1234567 ikev2 remote-authentication pre-shared-key 1234567 ikev2 local-authentication pre-shared-key 1234567 isakmp keepalive threshold 10 retry 2 ! crypto ipsec ikev2 ipsec-proposal VPN-TRANSFORM protocol esp encryption aes-256 protocol esp integrity sha-1 ! crypto map CRYPTO-MAP 1 match address VPN-INTERESTING-TRAFFIC crypto map CRYPTO-MAP 1 set peer 2.2.2.2 crypto map CRYPTO-MAP 1 set ikev2 ipsec-proposal VPN-TRANSFORM crypto map CRYPTO-MAP interface outside !
WARNING: If you already have VPNs then change CRYPTO-MAP (above) to the name of your existing crypto map.
ASA-2 Config
As with most site to site VPN configs, the ‘other-end’ should be a mirror image, like so;
! object network OBJ-Site-B subnet 192.168.1.0 255.255.255.0 object network OBJ-Site-B-XLATE subnet 172.16.2.0 255.255.255.0 object network OBJ-Site-A-XLATE subnet 172.16.1.0 255.255.255.0 ! nat (inside,outside) source static OBJ-Site-B OBJ-Site-B-XLATE destination static OBJ-Site-A-XLATE OBJ-Site-A-XLATE ! access-list VPN-INTERESTING-TRAFFIC line 1 extended permit ip object OBJ-Site-B-XLATE object OBJ-Site-A-XLATE ! crypto ikev2 policy 10 encryption aes-256 integrity sha256 group 19 prf sha256 lifetime seconds 86400 crypto ikev2 enable outside ! tunnel-group 1.1.1.1 type ipsec-l2l tunnel-group 1.1.1.1 ipsec-attributes pre-shared-key 1234567 ikev2 remote-authentication pre-shared-key 1234567 ikev2 local-authentication pre-shared-key 1234567 isakmp keepalive threshold 10 retry 2 ! crypto ipsec ikev2 ipsec-proposal VPN-TRANSFORM protocol esp encryption aes-256 protocol esp integrity sha-1 ! crypto map CRYPTO-MAP 1 match address VPN-INTERESTING-TRAFFIC crypto map CRYPTO-MAP 1 set peer 1.1.1.1 crypto map CRYPTO-MAP 1 set ikev2 ipsec-proposal VPN-TRANSFORM crypto map CRYPTO-MAP interface outside !
WARNING: If you already have VPNs then change CRYPTO-MAP (above) to the name of your existing crypto map.
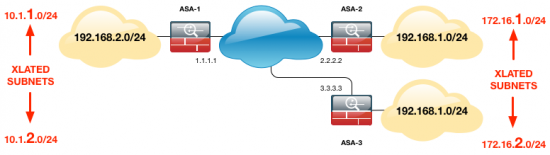
Scenario 2 (Two endpoints overlap with EACH OTHER)
Firstly you need to pick another subnet for BOTH of the ends with the overlapping subnet, and this is the subnet that your end will THINK it’s talking to, sometimes this is called an XLATED subnet, or a PSEUDO subnet, or a MASQUERADE subnet.
Then you will need to create TWO more, for the remote ends to TALK BACK TO.
Note: If you already have a VPN to one of the sites, then this process will replace that, and create one for the second site. So If you already have one tunnel you are going to need to either REMOVE it or change the NAT and Interesting traffic ACL. (Note: If you delete the ACL used by a crypto map, then it disapears from the crypto map! So you need to manually add it back). From this point forward I will assume we are creating BOTH tunnels from scratch.
ASA-1 Config
We need four objects for each XLATE, and two objects for the actual endpoints, (as two sites have the same REAL subnet we can use the same object for both). Then we create the NAT statements for each tunnel.
! object network OBJ-Site-A subnet 192.168.2.0 255.255.255.0 object network OBJ-Site-B-and-C subnet 192.168.1.0 255.255.255.0 object network OBJ-Site-A-B-XLATE subnet 10.1.1.0 255.255.255.0 object network OBJ-Site-A-C-XLATE subnet 10.1.2.0 255.255.255.0 object network OBJ-Site-B-XLATE subnet 172.16.1.0 255.255.255.0 object network OBJ-Site-C-XLATE subnet 172.16.2.0 255.255.255.0 ! nat (inside,outside) source static OBJ-Site-A OBJ-Site-A-B-XLATE destination static OBJ-Site-B-XLATE OBJ-Site-B-and-C nat (inside,outside) source static OBJ-Site-A OBJ-Site-A-C-XLATE destination static OBJ-Site-C-XLATE OBJ-Site-B-and-C !
Now you need to create the ACL that will be used to define ‘interesting traffic’, i.e. traffic that will be encrypted. But unlike normal you will specify the XLATED addresses.
! access-list VPN-2-Site-B extended permit ip object OBJ-Site-A-B-XLATE object OBJ-Site-B-and-C access-list VPN-2-Site-C extended permit ip object OBJ-Site-A-C-XLATE object OBJ-Site-B-and-C !
The rest of the VPN config is the same as normal, here I’m using IKEv2. If you have to use IKEv1 see the link at the bottom of the page.
! crypto ikev2 policy 10 encryption aes-256 integrity sha256 group 19 prf sha256 lifetime seconds 86400 crypto ikev2 enable outside ! tunnel-group 2.2.2.2 type ipsec-l2l tunnel-group 2.2.2.2 ipsec-attributes pre-shared-key 1234567 ikev2 remote-authentication pre-shared-key 1234567 ikev2 local-authentication pre-shared-key 1234567 isakmp keepalive threshold 10 retry 2 ! tunnel-group 3.3.3.3 type ipsec-l2l tunnel-group 3.3.3.3 ipsec-attributes pre-shared-key 1234567 ikev2 remote-authentication pre-shared-key 1234567 ikev2 local-authentication pre-shared-key 1234567 isakmp keepalive threshold 10 retry 2 ! crypto ipsec ikev2 ipsec-proposal VPN-TRANSFORM protocol esp encryption aes-256 protocol esp integrity sha-1 ! crypto map CRYPTO-MAP 1 match address VPN-2-Site-B crypto map CRYPTO-MAP 1 set peer 2.2.2.2 crypto map CRYPTO-MAP 1 set ikev2 ipsec-proposal VPN-TRANSFORM crypto map CRYPTO-MAP 2 match address VPN-2-Site-C crypto map CRYPTO-MAP 2 set peer 3.3.3.3 crypto map CRYPTO-MAP 2 set ikev2 ipsec-proposal VPN-TRANSFORM crypto map CRYPTO-MAP interface outside !
WARNING: If you already have VPNs then change CRYPTO-MAP (above) to the name of your existing crypto map.
ASA-2 Config
Unusually, the remote end (sometimes referred to as a ‘spoke’) does not need to be a mirror image of the main site, this is because we are sending VPN traffic ‘back’ from 192.168.1.0/24, to the XLATED subnet 10.1.1.0/24.
! object network OBJ-Site-B subnet 192.168.2.0 255.255.255.0 object network OBJ-Site-A-XLATE subnet 10.1.1.0 255.255.255.0 ! nat (inside,outside) source static OBJ-Site-B OBJ-Site-B destination static OBJ-Site-A-XLATE OBJ-Site-A-XLATE ! access-list VPN-INTERESTING-TRAFFIC extended permit ip object OBJ-Site-B object OBJ-Site-A-XLATE ! crypto ikev2 policy 10 encryption aes-256 integrity sha256 group 19 prf sha256 lifetime seconds 86400 crypto ikev2 enable outside ! tunnel-group 1.1.1.1 type ipsec-l2l tunnel-group 1.1.1.1 ipsec-attributes pre-shared-key 1234567 ikev2 remote-authentication pre-shared-key 1234567 ikev2 local-authentication pre-shared-key 1234567 isakmp keepalive threshold 10 retry 2 ! crypto ipsec ikev2 ipsec-proposal VPN-TRANSFORM protocol esp encryption aes-256 protocol esp integrity sha-1 ! crypto map CRYPTO-MAP 1 match address VPN-INTERESTING-TRAFFIC crypto map CRYPTO-MAP 1 set peer 1.1.1.1 crypto map CRYPTO-MAP 1 set ikev2 ipsec-proposal VPN-TRANSFORM crypto map CRYPTO-MAP interface outside !
WARNING: If you already have VPNs then change CRYPTO-MAP (above) to the name of your existing crypto map.
ASA-3 Config
Unusually the remote end (sometimes referred to as a ‘spoke’) does not need to be a mirror image of the main site, this is because we are sending VPN traffic ‘back’ from 192.168.1.0/24, to the XLATED subnet 10.1.2.0/24.
! object network OBJ-Site-C subnet 192.168.2.0 255.255.255.0 object network OBJ-Site-A-XLATE subnet 10.1.2.0 255.255.255.0 ! nat (inside,outside) source static OBJ-Site-C OBJ-Site-C destination static OBJ-Site-A-XLATE OBJ-Site-A-XLATE ! access-list VPN-INTERESTING-TRAFFIC extended permit ip object OBJ-Site-C object OBJ-Site-A-XLATE ! crypto ikev2 policy 10 encryption aes-256 integrity sha256 group 19 prf sha256 lifetime seconds 86400 crypto ikev2 enable outside ! tunnel-group 1.1.1.1 type ipsec-l2l tunnel-group 1.1.1.1 ipsec-attributes pre-shared-key 1234567 ikev2 remote-authentication pre-shared-key 1234567 ikev2 local-authentication pre-shared-key 1234567 isakmp keepalive threshold 10 retry 2 ! crypto ipsec ikev2 ipsec-proposal VPN-TRANSFORM protocol esp encryption aes-256 protocol esp integrity sha-1 ! crypto map CRYPTO-MAP 1 match address VPN-INTERESTING-TRAFFIC crypto map CRYPTO-MAP 1 set peer 1.1.1.1 crypto map CRYPTO-MAP 1 set ikev2 ipsec-proposal VPN-TRANSFORM crypto map CRYPTO-MAP interface outside !
WARNING: If you already have VPNs then change CRYPTO-MAP (above) to the name of your existing crypto map.
Related Articles, References, Credits, or External Links
Cisco ASA 5500 Site to Site VPN IKEv1 (From CLI)
Cisco ASA Site To Site VPN IKEv2 “Using CLI”


30/06/2018
Good article, please keep up good work.
20/11/2018
Excellent explanations!
I agree that we find these scenarios in real life.
Good job.
21/01/2020
Hi Pete,
I am sorry, but have 3 questions:
1. Scenario 2, OBJ-Site-B and OBJ-Site-C on ASA-2 and ASA-3 respectively, shouldn’t it have subnet address 192.168.1.0/24.
2. Is the understanding correct of encryption domain on each firewalls:
> ASA-1 Tunnel to B, source subnet 10.1.1.0/24 and remote subnet 192.168.1.0/24
> ASA-1 Tunnel to C, source subnet 10.1.2.0/24 and remote subnet 192.168.1.0/24
> ASA-2 Tunnel to A, source subnet 192.168.1.0/24 and remote subnet 10.1.1.0/24
> ASA-3 Tunnel to A, source subnet 192.168.1.0/24 and remote subnet 10.1.2.0/24
3. While accessing any resources behind ASA-2 and ASA-3, I would access using 172.16.1.x and 172.16.2.x respectively (pseudo subnets) which will get translated to 192.168.1.x in respective tunnels, is the understanding right?
22/01/2020
I think you might be mixing up the examples Ahin, In scenario 2 the actual destination subnets are covered by OBJ-Site-B-and-C
and the source/destination nat is then covered by;
nat (inside,outside) source static OBJ-Site-A OBJ-Site-A-B-XLATE destination static OBJ-Site-B-XLATE OBJ-Site-B-and-Cnat (inside,outside) source static OBJ-Site-A OBJ-Site-A-C-XLATE destination static OBJ-Site-C-XLATE OBJ-Site-B-and-C
Pete
16/07/2020
Hi Pete!
First of all thank you for taking you time and making such detailed and great looking documentation.
I have a question about Scenario 2.
With everything in place and configured according your scenario let’s imagine that there is a host behind:
1. ASA-1 with IP 192.168.2.100
2. ASA-2 with IP 192.168.1.100
3. ASA-3 with IP 192.168.1.100
What destination IP should I use on the host 192.168.2.100 to reach specific host behind ASA-2 and then host behind ASA-3.
Thank you,
Riad G.
17/07/2020
Hi Riad,
What a great question! (Even if it made me pull a face, until I understood what you were asking!) The ASA will encrypt based on the interesting traffic URL – For Scenario 2 you would connect to 172.16.1.100
P
18/10/2020
Thank you Pete for this, your articles are really helping me a lot with real life fault on the ASA.
19/10/2020
Glad to help 🙂
10/01/2022
Hi Pete,
This is a great article. I have a few questions.
I need to add a newly acquired business to our infrastructure with an overlapping subnet (10.1.1.0/24). The newly acquired business (and subnet) only needs to communicate with the hub site. Can I just masquerade (NAT) the overlapping subnet from the new business to an unused subnet and leave the existing 10.1.0.0/16 for the pre-existing site-to-site in place? or do I need to re-do that too?
Also what about DNS responses from the translated subnet… If I enable the DNS rewrite feature. Will this actually inspect DNS response packets and re-write them with the translated address?
Many thanks,
Will
10/01/2022
1. Yes that seems like a sensible approach.
2. Mmm good question, my feeling is, it should ‘just work’, but 20 minutes on the test bench should tell you if you’re concerned.
P
10/01/2022
Wow! That was quick!
Fantastic… thank you for the sanity check and thank you for providing such a great resource.