KB ID 0001429
Problem
Note: This is for Cisco ASA 5500, 5500-x, and Cisco Firepower devices running ASA Code.
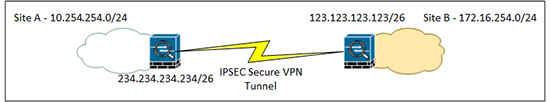
You want a secure IPSEC VPN between two sites using IKEv2.
Note: If the device you are connecting to does not support IKEv2 (i.e. it’s not a Cisco ASA, or it’s running code older than 8.4) then you need to go to the older version of this article;
Cisco ASA 5500 Site to Site VPN IKEv1 (From CLI)
Solution
Before you start – you need to ask yourself “Do I already have any IPSEC VPN’s configured on this firewall?” Because if it’s not already been done, you need to enable ISAKMP IKEv2 on the outside interface. To ascertain whether yours is on or off, issue a “show run crypto ” command and check the results, if you do NOT see “crypto ikev2 enable outside” then you need to issue that command.
PetesASA# show run crypto crypto ikev2 enable outside << Mines already enabled and its IKE version 2 crypto ikev2 policy 10 encryption aes-256 integrity sha256 group 19 prf sha256 lifetime seconds 86400 crypto ikev2 enable outside
1. I’m going to create access control lists next, one to tell the ASA what is “Interesting traffic”, that’s traffic that it needs to encrypt.
So below I’m saying “Don’t NAT Traffic from the network behind the ASA (10.254.254.0) that’s going to network behind the VPN device at the other end of the tunnel (172.16.254.0).
PetesASA(config)#object network Site-A-SN PetesASA(config-network-object)#subnet 10.254.254.0 255.255.255.0 PetesASA(config)#object network Site-B-SN PetesASA(config-network-object)#subnet 172.16.254.0 255.255.255.0 PetesASA(config)#access-list VPN-INTERESTING-TRAFFIC line 1 extended permit ip object Site-A-SN object Site-B-SN PetesASA(config)#nat (inside,outside) source static Site-A-SN Site-A-SN destination static Site-B-SN Site-B-SN no-proxy-arp route-lookup
2. Now I’m going to create a “Tunnel Group” to tell the firewall it’s a site to site VPN tunnel “l2l”, and create a shared secret that will need to be entered at the OTHER end of the site to site VPN Tunnel. I also set a keep alive value.
Note: Ensure the Tunnel Group Name is the IP address of the firewall/device that the other end of the VPN Tunnel is terminating on.
PetesASA(config)# tunnel-group 123.123.123.123 type ipsec-l2l PetesASA(config)# tunnel-group 123.123.123.123 ipsec-attributes PetesASA(config-tunnel-ipsec)# ikev2 remote-authentication pre-shared-key 1234567890 PetesASA(config-tunnel-ipsec)# ikev2 local-authentication pre-shared-key 1234567890 PetesASA(config-tunnel-ipsec)# isakmp keepalive threshold 10 retry 2 PetesASA(config-tunnel-ipsec)# exit
3. Now we need to create a policy that will setup how “Phase 1” of the VPN tunnel will be established. It sets the encryption type (AES-256), the hashing/integrity algorithm (SHA-256), The Diffie Hellman group exchange version, and the Level of PRF (Pseudo Random Function). Finally it sets the timeout before phase 1 needs to be re-established. It sets the timeout value to 86400 seconds (That’s 1440 Minutes – or 24 hours if your still confused 🙂 ).
PetesASA(config)# crypto ikev2 policy 10 PetesASA(config-ikev1-policy)# encryption aes-256 PetesASA(config-ikev1-policy)# integrity sha256 PetesASA(config-ikev1-policy)# group 19 PetesASA(config-ikev1-policy)# prf sha256 PetesASA(config-ikev1-policy)# lifetime 86400
4. We stated above that we are going to use AES-256 and SHA-256, for Phase 1, so let’s use the same for the IPSEC proposal (Phase 2), ‘Transform Set’.
PetesASA(config)# crypto ipsec ikev2 ipsec-proposal VPN-TRANSFORM PetesASA(config-ipsec-proposal)# protocol esp encryption aes-256 PetesASA(config-ipsec-proposal)# protocol esp integrity sha-1
5. Finally we need to create a “Cryptomap”, this is the ‘thing’ that fires up the tunnel, when the ACL INTERESTING TRAFFIC is used, it also defines the transform set for “Phase 2” of the VPN Tunnel, that will also use 3DES and SHA and PFS. And last of all we apply that Cryptomap to the outside interface.
PetesASA(config)# crypto map CRYPTO-MAP 1 match address VPN-INTERESTING-TRAFFIC PetesASA(config)# crypto map CRYPTO-MAP 1 set peer 123.123.123.123 PetesASA(config)# crypto map CRYPTO-MAP 1 set ikev2 ipsec-proposal VPN-TRANSFORM PetesASA(config)# crypto map CRYPTO-MAP interface outside
5. Don’t forget to save your hard work with a “write mem” command.
PetesASA(config)#
PetesASA(config)# write mem
Building configuration...
Cryptochecksum: 5c8dfc45 ee6496db 8731d2d5 fa945425
8695 bytes copied in 3.670 secs (2898 bytes/sec)
[OK]
PetesASA(config)#
6. Simply configure the other end as a “Mirror Image” of this one.
ASA 5500 Site to Site IKEv2 VPN Copy and Paste Config
Note: This uses AES-256 and SHA-256. It also assumes your outside interface is called ‘outside’. Check! I’ve seen them called Outside (capital O), wan, and WAN.
! crypto ikev2 policy 10 encryption aes-256 integrity sha256 group 19 prf sha256 lifetime seconds 86400 crypto ikev2 enable outside ! object network OBJ-SITE-A subnet 10.0.0.0 255.255.255.0 object network OBJ-SITE-B subnet 10.0.3.0 255.255.255.0 ! access-list VPN-INTERESTING-TRAFFIC extended permit ip object OBJ-SITE-A object OBJ-SITE-B nat (inside,outside) source static OBJ-SITE-A OBJ-SITE-A destination static OBJ-SITE-B OBJ-SITE-B no-proxy-arp route-lookup ! tunnel-group 2.2.2.2 type ipsec-l2l tunnel-group 2.2.2.2 ipsec-attributes ikev2 remote-authentication pre-shared-key 1234567 ikev2 local-authentication pre-shared-key 1234567 isakmp keepalive threshold 10 retry 2 ! crypto ipsec ikev2 ipsec-proposal VPN-TRANSFORM protocol esp encryption aes-256 protocol esp integrity sha-1 ! crypto map CRYPTO-MAP 1 match address VPN-INTERESTING-TRAFFIC crypto map CRYPTO-MAP 1 set peer 2.2.2.2 crypto map CRYPTO-MAP 1 set ikev2 ipsec-proposal VPN-TRANSFORM crypto map CRYPTO-MAP interface outside !
Simply change the values in red where;
- 10.0.0.0 255.255.255.0 is the network behind the ASA you are working on.
- 10.0.3.0 255.255.255.0 is the destination network behind the device you are connecting to.
- 2.2.2.2 is the peer IP address of the device you are attempting to connect to.
- 1234567 Is the shared secret you will use at both ends.
Related Articles, References, Credits, or External Links
NA

22/09/2018
Fantastic article Pete. I love coming here because my name is Pete as well 😉
note: on step 2, you need to add ‘ikev2’ before the ‘remote-authentication’ and ‘local-authentication’
a small stumbling block when i used yours as a template, otherwise flawless!
Thanks for the aticle!
18/03/2019
Excellent. You are showing routing
11/04/2019
Hi Pete, great article. Do you know if this configuration can be applied to an ASA that is already serving remote access client VPNs via Cisco AnyConnect? Im worried as some of the configs are already in place and i dont want to add them again causing an outage.
13/04/2019
Yes of course, that will be fine, the only time an ASA has a problem running multiple VPN types is is its at a branch site and running EZVPN.
16/04/2019
Hmm, unfortunately not.
When you apply the following from your config:
crypto map CRYPTO-MAP interface outside
It wipes out the existing crypto map for Anyconnect on the outside interface.
16/04/2019
Anyconenct does not use crypto maps, they are for ISAKMP VPNs? It will replace an existing crpyto map is one exists.
17/04/2019
Hi Pete. You’re correct I’ve solved that issue now, many thanks.
One last thing I’m having a problem with is pinging. My client devices on the remote end seem to pass most traffic fine with the domain (DNS, HTTPS etc etc) but for some reason I can’t ping over the vpn from LAN to LAN. I’m guessing it’s an issue with ICMP, but I’ve added ICMP within the interesting traffic acl.
Any ideas?
17/04/2019
Is ‘inspect icmp’ on the default inspection map?
11/05/2021
Pete –
We have a branch office pair of ASA 5515’s in HA (soon to be replaced with a pair of 5516-X’s) that currently hosts site-to-site ikev1 tunnels and EZVPN connections to ~35 remote workers on 5505’s.
We have 2 clients that would like to convert their S2S tunnels to ikev2. Noting your reply comment, is this technically possible without breaking the ikev1 EZVPN connections?
19/05/2021
I cant see that being a problem TBH, EZVPN is just old IPSEC RA in a pretty dress, and that still works 🙂
23/05/2019
Hi Pete
If I dont create a new Group policy when configuring IKEv2 will it drop the exsisting IKEv1 Tunnels,
also can I just edit IKEv1 crypto maps etc when I want to migrate from IKEv1 to IKEv2.???
or is it better to start from scratch when migrating to IKEv2 ???
Thanks
23/05/2019
>>will it drop the exsisting IKEv1 Tunnels,
No
>>also can I just edit IKEv1 crypto maps etc when I want to migrate from IKEv1 to IKEv2.???
Easier than that! 🙂 See https://www.petenetlive.com/KB/Article/0001196
29/05/2019
Hey Pete, Do you have an example of the config when you have multiple sub nets on both sides? Can we just use object-group for all the lines instead? Would that run into an issue with the Nat statement or ACL?
29/05/2019
That’s a great question! yes you can use object groups and group them together for use in Nat statements, I didn’t like to do this because I originally assumed that either it would be a problem, or hard to troubleshoot, but it works fine 🙂 I’ve done another post on adding a subnet to a VPN somewhere!
15/07/2019
Hi Pete,
This is a great article, I’ve just set up a new IKEv2 tunnel and I wanted to query the following line.
protocol esp integrity sha-1
In your article you said lets assume for Phase2 we use AES-256 and SHA-256 which was precisely what I was looking to do but only having the “sha-1” option caught me out.
Will this use SHA-256 or Sha-1 ?
18/07/2019
For Phase it is 🙂 this is for IPSEC (the two tunnels that get created inside the ISAKMP Tunnel) look see…..
Petes-ASA(config-ipsec-proposal)# protocol esp integrity ?ipsec-proposal mode commands/options:
md5 set hash md5
null set hash null
sha-1 set hash sha-1
are your only options 🙂
Pete
03/10/2019
Hi Pete
Im using ASA version 9.8 and I have additional options:
XXXXXXXX/admin(config-ipsec-proposal)# protocol esp integrity ?
ipsec-proposal mode commands/options:
md5 set hash md5
null set hash null
sha-1 set hash sha-1
sha-256 set hash sha-256
sha-384 set hash sha-384
sha-512 set hash sha-512
03/10/2019
Correct 🙂 As long as both ends are set the same, the proposals will match, you will have other options for IKEv2 Phase 2 policy as well 🙂
Pete
24/07/2019
Hi Pete!
I created several ikev2 Site2Site tunnels in one of my routers which is supposed to be the central router for a service provider. One of the tunnel survives while the other 2 dont stay up for long. Do you know why this happens?
27/08/2019
Why use this instead of route based with the tunnel interfaces?
28/08/2019
Because not all versions of ASA support VTI interfaces m8.
P
03/10/2019
Hi Pete
1) Under the tunnel group, do we have to define the pre-shared key as well and the local and remote authentication keys ie
ikev2 pre-shared-key **********
ikev2 local-authentication pre-shared-key **********
ikev2 remote-authentication pre-shared-key **********
I have seen VPNs configured with just The local and remote preshared keys only
2) Under the cryptomap, is it not good practice to change the SA lifetime?
crypto map outside_map 1 set security-association lifetime seconds 3600
3) Where would I enable or disable PFS, is this under the cryptomap
4) Under the phase 1 proposal for IKEv2, Can we just configure a single proposal with multiple ciphers
ie
crypto ikev2 policy 10
encryption 3des des
integrity sha md5
group 5 14
prf sha sha256
lifetime seconds 28800 86400
Thanks
03/10/2019
1) Correct you only need a local and remote PSK, the other one is only ever used for IKEv1 so in this case it’s redundant.
2) Personal Preference, but if you can break AES-256 in under 86000 seconds then, you are a better man than me!
3) Like so;
crypto map outside_map 1 set pfs group5
4) Yes-but it you only have two firewalls and 1 VPN, and are setting the tunnel up yourself, why bother, multiple policies are an advantage if you are doing multivendor VPNs and you don’t have access sot the other end!
25/12/2019
Excellent Post!
Very informative for experienced novice to follow.
29/05/2020
Hey, Pete, greate post, It helped me a lot, I’m new with Cisco Fws.
Just something that I think is missing from this guide is, to assign a group policy permitting IKEv2 to the tunnel group. It was driving me crazy because auth for phase 1 and 2 was succesful but the vpn was son unstable and I wasn’t able to found the root cause.
Anyway, thanks a lot for this work!!
01/06/2020
You don’t need to have a Group-Policy (I’m confused). I use these configs all the time?
02/06/2020
Hi, Pete. What happened to me is that after some troubleshoot, I wasn’t able to find why the vpn was not stable.
A Cisco engineer from TAC helped with the troubleshoot. After he ran the command “show logging | i [Peer ip] we saw on the logs something similar to “Ikev2 not allowed on group-policy”
He checked the tunnel-group, because there was no group-policy assigned to it, it was appliying the “DfltGrpPolicy” and in that group-policy it was only allowed ikev1. With that in mind, he decided to add a new group-policy allowing ikeV2 and assigned to the tunnel-group. After that the Vpn stablished successfully. The ASA is running software version 9.12(3)
P.S. Your posts are been very helpful to me that I’m new at Cisco FWs. I really appreciate what you’re doing. Thanks Pete.
17/06/2020
Hi Pete
Great articles, I realized I seem to foget some fundamentals when not touching VPNs for a while so Im back for advice. When setting up a ikev2 VPN between 2 ASAs,
1. do the encryption maps need to be like for like?
2. Does the natting need to match (this may be a stupid question, i don’t believe they would as i need to hide some addressed behind a PAT, just wanted confirmation)
Thanks
17/06/2020
1. Crypto-maps should be a mirror image.
2. Nat should be exempt (no-nat) for traffic you want to traverse the tunnel. (Assuming your firewall performs NAT/PAT of course not everyone does!)
P
10/07/2020
Hello Pete, thanks,
Question
I have done a ikv2 VPN but the vpn phase1 does not up, I check all my configurations and configurations with friends and the only difference was this:
My Config
group-policy DfltGrpPolicy attributes
vpn-tunnel-protocol ikev1 l2tp-ipsec ssl-clientless
My Networking friends
group-policy DfltGrpPolicy attributes
vpn-tunnel-protocol ikev1 ikev2
the difference is that ikv2 between my friends and mine.
can you tech me something may be I dont see.
Att
10/07/2020
What version ASA Code? My ASA (9.1(7)) does not have this entries?
simply add ikev2
Petes-ASA(config-group-policy)# vpn-tunnel-protocol ?
group-policy mode commands/options:
ikev1 IKE version 1
ikev2 IKE version 2
l2tp-ipsec L2TP using IPSec for security
ssl-client SSL VPN Client
ssl-clientless SSL Clientless VPN
10/07/2020
Hello Pete
I have version 9.2,
ok Im gonna add ikv2 there when I add it write to you again.
A lot of thanks
03/09/2020
Excellent Post!
It helped me a lot…
17/10/2020
Hi Pete,
When I followed your instructions, line for line, my IKEv1 Crypto Maps disappeared and I had to restore the running-config from backup. Can IKEv1 and IKEv2 crypto maps exist together? Any idea what might have happened? Asa version 9.1(7)32.
Thanks for all these great articles!
19/10/2020
Absolutely IKEv1 and IKEv2 can co-exist quite happily, No command listed here should affect your IKEv1 config?
P
08/06/2021
Hi, I stumbled upon this while searching for a possible fix for an issue I have.
I have an IKEv2 IPSEC site to site VPN and every time it disconnects it doesn’t reconnect automatically. I need to reboot one of the routers in order for it to connect again.
Have you ever encountered this?
09/06/2021
I’ve not, you mean you need to reboot the router outside one of the firewalls? If so I’d be updating/replacing the router?
11/06/2021
only thing missing is group-policy,
create separate group-policy or enable ikev2 in DefaultGroupPolicy
15/09/2022
hey pete, this worked perfectly on a 5525x!
my question is if you have anyconnect setup on your laptop to connect to site a asa, how would you access site b directly from the laptop?
i am able to use remote desktop and access devices in site a but cannot connect to devices in site b.
thank you !
21/09/2022
Hi bud, use the search bar above, annd look for spoke to spoke VPN 🙂
05/09/2023
PetesASA(config)# tunnel-group 123.123.123.123 type ipsec-l2l
PetesASA(config)# tunnel-group 123.123.123.123 ipsec-attributes
PetesASA(config-tunnel-ipsec)# remote-authentication pre-shared-key 1234567890
PetesASA(config-tunnel-ipsec)# local-authentication pre-shared-key 1234567890
PetesASA(config-tunnel-ipsec)# isakmp keepalive threshold 10 retry 2
PetesASA(config-tunnel-ipsec)# exit
In the above commands ikev2 is missing infront of remote-authentication and local-authentication
also, what does the isakmp keepalive threshold 10 retry 2 does? if I may ask
08/09/2023
ikev2 – You are correct – wonder if that always been incorrect, or the code has changed? Updated and thank you!
The keepalive command sets the thresholds for DPD (Dead Peer Detaction), It’s not manditory.