KB ID 0001432
Problem
I did an article a while back on doing this with UNL, so I thought I’d revisit it today for EVE-NG. I really like EVE-NG, for proof of concept work, testing, and just learning new products I cant think of any product better.
But what if you want to connect your labs to the outside world?
Solution
In all honesty a lot of this article you can skip, I’m just showing you what’s going on down at the Linux level (so you can be sure yours will be OK).
I’m assuming you already have EVE-NG installed and some images in it, and know how to create a lab, and that you want to connect that lab to the internet.
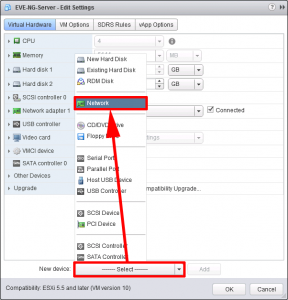
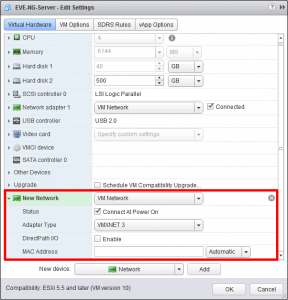
Unlike UNL, EVE-NG will deploy with only one vNIC, (below I’m using vSphere 6), so to keep things nice and simple I’m just going to add one more;
VMXNet3 is fine, just make sure it’s connected to the correct port-group.
Note: You can probably skip down to allowing promiscuous mode below. As the good folk at EVE-NG have configured all the hard stuff for you!
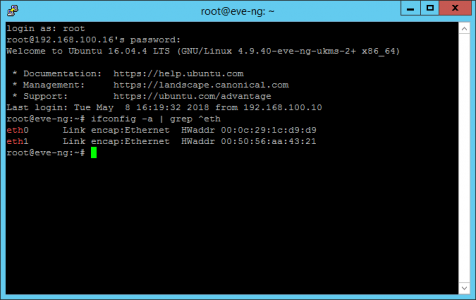
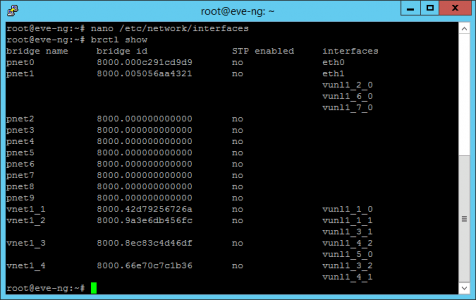
SSH into your EVE-NG server > log on as the root user, and make sure it can see BOTH network cards, with the following command;
Above you can see the original eth0, and the one I just added eth1.
You probably already have nano installed, (it’s a text editor). But just in case, run the following command;
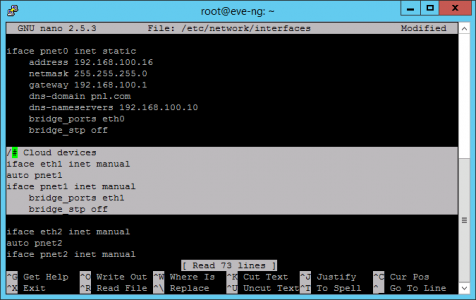
Use nano to edit/view the network card settings;
Scroll down to the settings for eth1 and make sure it is tied to, (bridged to) pnet1 (as below). Repeat for any additional network cards.
To exit nano Press CTRL+X, (then if you have made any changes save them).
You can also see a summary of bridged interfaces with the following command;
brctl show
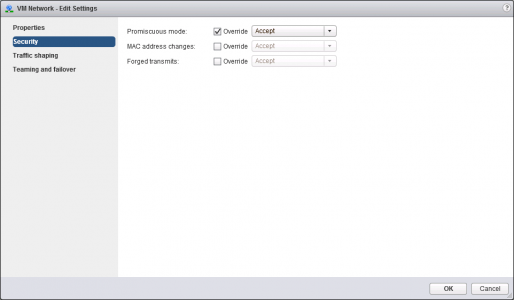
Enable Promiscuous Mode
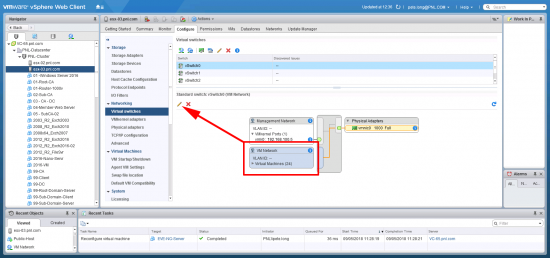
Your Hyper Visor (VMware) needs to be able to see traffic from your EVE-NG devices, coming out though the vNIC we added earlier, that means a lot of MAC addresses are going to be coming from the MAC address of that vNIC. By default VMWare will block that. so we need to enable promiscuous mode on the port-group that we connected to earlier, (mine was called VM Network).
If you are using the older VMware (Fat) client, see the link at the bottom of the page for the older UNL article.
Edit the port group;
On the Security tab > Tick ‘Override’, and set it to ‘Accept’ > OK.
Forged Transmits: You will also need to enable this, (if you use VLAN tagging in your network!)
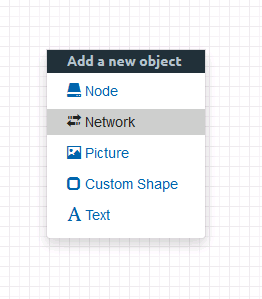
Add Cloud Objects to EVE-NG
Above, (if you remember) the vNIC (eth1) was bridged to pnet1. These used to be labelled pnet1, pnet2, etc. Now they are labelled Cloud1, Cloud2, etc.
In your lab workspace add a ‘Network’ object.
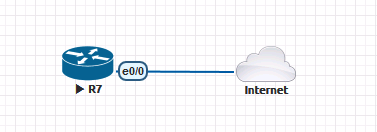
Select Cloud1 (remember this is mapped to pnet1, which is bridged to eth1.). You may want to change the name from Net, to something like ‘Internet’.
Connect a device to it, (I’m using a router, because they are quick and easy to setup).
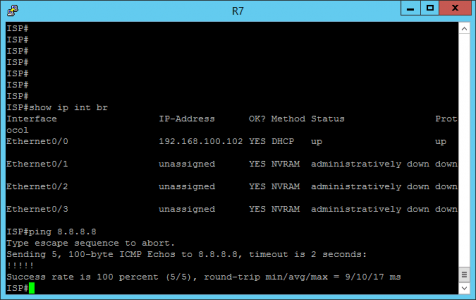
My Network has DHCP on it, so my router picked up an IP from my LAN, and once I’d given it a default route, I now have full internet access from the lab.
Related Articles, References, Credits, or External Links
Unified Networking Lab – Connecting ESX VM to the Internet


20/06/2018
Thank you! This post saved me some time and nerve!
05/10/2020
Hi, I have multiple NICs in my ESXI host but have an issue where only cloud0 is woking.
I have configured a router with 3 cloud connections for testing (cloud0,cloud1, cloud2) to receive IP’s from a directly connected cisco switch and only cloud0 is picking up an IP. Promiscuous mode is on for the vSwitch and port group.
My goal is to use real switches without trunking all VLAN’s to a single port.
10/07/2021
Hi Lee, I got the same issue, just wondering have you fixed it? thanks
07/09/2022
Thomas and Lee,
I noticed that the mac addresses on EVE-NG were not in the same order as they were in vSphere. They are as follows:
EVE Nic 0 = VMNet Adapter 1 (as expected)
EVE Nic 1 = VMNet Adapter 5 (not expected)
EVE Nic 2 = VMNet Adapter 2 (not expected)
EVE Nic 3 = VMNet Adapter 3 (not expected)
EVE Nic 4 = VMNet Adapter 4 (not expected)
I’m assuming at somepoint I must have deleted a VMNet adapter, and then when I added another, all VMnet adapters (as seen from EVE) ‘moved up a spot’. You can verify the NIC MAC address by using the ifconfig -a | grep ^eth that Pete mentioned, and then verify the MAC address in vSphere by expanding each VMNet adapter. Once I corrected the portgroups to the correct EVE Nics, everything started working.
The weird thing that I noticed is when I had a packet capture running on the interface of a router/switch, and I would run a ping command, the pings did not show up in the packet capture. However, once I corrected the portGroups based on how EVE sees them, then the pings (and other traffic showed up as expected).
24/06/2018
HI,
Thanks a lot for this post, very helpful.
For your information, I use vlan tagging on my home lab. and I needed also ‘Accept Forged transmits” on top of “Promiscous mode” on my lab to make it work.
07/03/2019
Thanks
06/12/2019
what a great help !! thanks alot greg !!!
17/11/2018
This was a lifesaver, thanks!
26/11/2018
Thank you very much, sir!
18/12/2018
Thanks a lot.
19/04/2019
I am running EVE-NG on Azure (baremetal installation) and this method is not working for me.
could you please let me know if i need to make any other change?
26/04/2019
Try this.
root@eve-ng1:/etc/network# vi interfaces
# This file describes the network interfaces available on your system
# and how to activate them. For more information, see interfaces(5).
# The loopback network interface
auto lo
iface lo inet loopback
# The primary network interface
iface eth0 inet manual
auto pnet0
iface pnet0 inet dhcp
bridge_ports eth0
bridge_stp off
# Cloud devices
iface eth1 inet manual
auto pnet1
iface pnet1 inet static
address 192.168.0.1
netmask 255.255.255.0
network 192.168.0.0
bridge_ports eth1
bridge_stp off
iface eth2 inet manual
auto pnet2
iface pnet2 inet manual
bridge_ports eth2
bridge_stp off
iface eth3 inet manual
auto pnet3
iface pnet3 inet manual
bridge_ports eth3
bridge_stp off
iface eth4 inet manual
auto pnet4
iface pnet4 inet manual
bridge_ports eth4
bridge_stp off
iface eth5 inet manual
auto pnet5
iface pnet5 inet manual
bridge_ports eth5
bridge_stp off
iface eth6 inet manual
auto pnet6
iface pnet6 inet manual
bridge_ports eth6
bridge_stp off
iface eth7 inet manual
auto pnet7
iface pnet7 inet manual
bridge_ports eth7
bridge_stp off
iface eth8 inet manual
auto pnet8
iface pnet8 inet manual
bridge_ports eth8
bridge_stp off
iface eth9 inet manual
auto pnet9
iface pnet9 inet manual
bridge_ports eth9
bridge_stp off
06/05/2019
Thank you for posting this. I’ve been pulling my hair out for hours.
16/07/2019
Hi, Can you please explain for VMware, I was able to follow steps successfully before “Enable Promiscuous Mode” but, don’t know how to do on VMware® Workstation 12 Pro?
Screenshots you have added, it is for the vSphere web client.
I am not sure how to enable promiscuous mode on VMware Workstation.
Please help!
26/07/2019
There is no vSwitch concept in VMware Workstation, you enable it directly on a vmic on the machine, by editing the vmx file;
ethernet%d.noPromisc = “FALSE”
(replace %d with the vNIC ethernet number)
Regards,
25/03/2020
Thanks so much about this answer, I keep fighting with the problem until I found this message. Maybe it would be useful to put in the tutorial the commentary to avoid this issues. Thanks a lot
05/11/2019
Thanks for this post. I set up my Lab on ESX today and have been troubleshooting this particular problem since install complete. Enable Promiscuous mode worked for me.
25/11/2019
Very informative.
The EVE-ng that is used, is it Pro or is it the Community Edition?
25/11/2019
Community m8, I tend not to pay for things 🙂
27/12/2019
Thanks, my friend: was very useful!
20/05/2020
Hi Pete,
I used your guide, however no internet connectivity. Using VMware ESXi 6.7.
12/09/2022
Hi AK,
Did you try to resolve the issue? Please help me if resolved.
03/06/2020
Thank you for posting this. It solve my problems
29/07/2020
Awesome article, really helped me
02/08/2020
wow it worked for me.. thanks a tone!!
20/08/2020
Cloud1 should be pnet1 right?
21/08/2020
I typically just select Cloud1 from the lab node options?
29/09/2020
Can we enable virtualized eve ng on google cloud to connect to the internet?
Thanks
30/09/2020
Good question, it comes as an OVA So I don’t see why not, but I’ve never tried it so I cant comment.
15/10/2020
Thank you very much for the post. I have tried this steps but my router didnt get DHCP ip address.Is there anything I have to enable to get DHCP.Iam running eve-ng on top of exsi7.
16/10/2020
I’ve seen this sometimes with particular router/hardware types try a Dynamips one, and an IOL one, then try a firewall.
05/11/2020
Hi,
I get an IP Address through DHCP, but if I try to SSH to the router I get
PuTTY – Unexpected Error closed connection
Python – Netmiko – paramiko.ssh_exception.SSHException: Error reading SSH protocol banner
HTTPS – Error 401 unauthorised when I try to browse
I can ping the router fine, but cannot SSH or HTTPS.
I have EVE on ESXi. I’ve googled like crazy, but canot figure it out
03/06/2021
Here is some more input on this. I have enabled promiscuous and forged transmits.
The issue is with broadcast traffic. It seems the vswitch doesn’t forward the broadcasts when using nic teaming. I can’t imagine why there is an issue only with EVE-NG as other VM’s must be able to send broadcasts.
The reason I say this is because of analyzing a pcap on the nic of the IOL router connected to cloud0. For the sake of clarity we will name the router ISP1. Whenever the ISP1 sends an arp there isn’t any reply unless the destination exists within the esx-i itself. I can ping the EVE-NG ip and the ESX-I host as they are on the same network.
There are two ways around the issue.
Remove one link from the team or configure a static arp entry on ISP1 for the desired destination.
07/06/2021
Thanks Garry!
20/09/2024
this little post saved my server from going out the window, 2+ days searching… deleted the nic teaming boooom fixed…FML… Thanks very much!
13/06/2021
Thank You. Man this was just what I needed.
13/07/2021
This is awesome. Decent effort and clear logic.
Thanks.
Keep one thing in mind if you are doing this via a Cisco vios router: do NOT use local interface as your default gateway next hop, use the server IP address.
Also, for professional version users, you can use Cloud-NAT option without requiring two NIC setup.
18/01/2022
Thanks for this tutorial, much appreciated! I wanted to ask what tweaks I would need to make to these steps to connect a real(physical) Cisco router to eve-ng?
Say I wanted to connect my physical Cisco 2911 router to a virtual Juniper router that I have in my eve-ng lab and maybe establish a routing protocol over the link…would this be possible?
I have played around with different vSwitch configurations/settings and even port groups but cant seem to get this to work. Any feedback you can provide would be awesome.
18/01/2022
As long as you have a cloud object connected to your lab theres not reason why should not be able to do this?
P
07/02/2022
Thx for the info. I followed your instructions but I can’t still ping outside the EVE-NG lab. I use VMWare ESX with Vsphere 6.7.
Do I missed something?
07/02/2022
I solved it. I added a extra NIC on the EVE-NG VM.
12/09/2022
Hi,
Did you try to resolve the issue? Please help me if resolved.
17/09/2022
My esxi network was connected to a vswitch with 2 uplinks, the node’s traffic within eve-ng can’t get out of esxi. A workaround is removing the redundant link.
04/02/2023
February 2023, with VMware ESXi 8.0 and EVE-NG – It also didn’t work for me, even if I had Promiscuous mode with “Accept”. But I found how to make it work – I simply enabled the “Forged transmits” option to “Accept” and it started working. Via the same physical interface that both ESXi and EVE-NG are using to connect to my home network.
Why it needs the “Forged transmits” to be enabled and set to “Accept” I don’t know. In VMware ESXi 8.0 these three settings for Security on the vSwitch0 are on “Reject” by default.
23/10/2024
Thank you so much. With EVE-NG running on an ESXi server, added ‘Accept Forged transmits’ and also turned on ‘Promiscuous mode’ in my lab to make it work. I am grateful for the information you provided.