KB ID 0001428
Problem
I got asked to put in a VPN for a client, this week, it went from a simple site to site, to a site to site with a Fortigate firewall at one end, to a VPN from and ASA to a Fortigate ‘through’ another ASA.
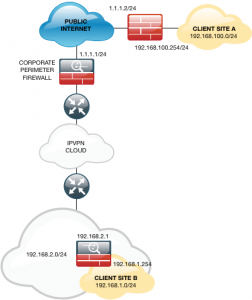
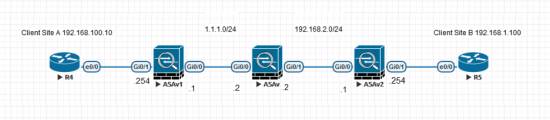
It’s been a few years since I had to tunnel ‘through’ a firewall, and experience tells me, if you don’t have control of BOTH ends of a new VPN tunnel, anything that stops the tunnel coming up, MUST be my fault. So I thought I’d build it on my test bench, (admittedly without a Fortigate, but thankfully that’s not my problem, so I used another ASA instead.) This is what I built.
Note: The routers are just there, so I can ping the other site to test the tunnel.
Solution
So what I’m worried about, is how to configure the ASA in the middle (The Corporate Perimeter Firewall). This is not an exercise in setting up the VPNs, if that’s what you require, then see the link at the bottom of the page.
There are FIVE things you need to do;
- Create a Static (One-To-One) NAT so that the ASA that has a private IP on its outside interface, (192.168.2.1) has a PUBLIC IP mapped to it, (I’m using 1.1.1.3).
- Allow UDP 500 (ISAKMP) from the ASA (1.1.1.1) to the ASA (192.168.2.1)
- Allow UDP 4500 (NAT-TRAVERSAL) from the ASA (1.1.1.1) to the ASA (192.168.2.1)
- Allow UDP 500 (ISAKMP) from the ASA (192.168.2.1) to the ASA (1.1.1.1)
- Allow UDP 4500 (NAT-TRAVERSAL) from the ASA (192.168.2.1) to the ASA (1.1.1.1)
That’s It! You DON’T need to allow ESP or AH, (protocols 50 and 51,) nor do you need to enable ‘ipsec-pass-through’. I’ve brought up the tunnel with both IKEv1 and IKEv2.
Config;
! object network OBJ-ASA-SITE-1 host 1.1.1.1 object network OBJ-ASA-SITE-2 host 192.168.2.1 nat (inside,outside) static 1.1.1.3 ! access-list outbound extended permit udp object OBJ-ASA-SITE-2 object OBJ-ASA-SITE-1 eq isakmp access-list outbound extended permit udp object OBJ-ASA-SITE-2 object OBJ-ASA-SITE-1 eq 4500 ! access-list inbound extended permit udp object OBJ-ASA-SITE-1 object OBJ-ASA-SITE-2 eq isakmp access-list inbound extended permit udp object OBJ-ASA-SITE-1 object OBJ-ASA-SITE-2 eq 4500 ! access-group inbound in interface outside access-group outbound in interface inside !
WARNING: Read the following article before executing the access-group commands;
Cisco ASA – ‘access-group’ Warning
Related Articles, References, Credits, or External Links
Cisco ASA Site To Site VPN IKEv2 “Using CLI”
Cisco ASA5500 Site to Site VPN from ASDM
Add a Static (One to One) NAT Translation to a Cisco ASA 5500 Firewall

22/05/2018
Nice one! I did not know that you would only require that phase-1 part through and ESP would take care of itself somehow. Something on the router side that is often forgotten is that when building IPSec tunnel the router on the other side should be including the private pre-NAT’s IP in the identity of the isakmp profile.
22/05/2018
If you think about it – the phase 1 tunnel establishes, then two IPSEC tunnels are created ‘within’ that tunnel (each with its own SPI), the firewall does not actually see any ESP traffic (the one in the middle).
12/05/2021
Hi asa to hp router VPN tunnel status down, but both sides same configuration, any protocol use?
10/10/2018
Quick question, I already have IPSec setup and running, but didn’t need an ACL to allow UPD/500/4500 inbound.
Shouldn’t it be built-in? Just like all my “inside” ACL are permits, because the denies are already by default, correct!?
10/10/2018
If you are sure that one end of the VPN tunnel will ALWAYS be the initiator then yes, but you want both ends of the tunnel to be able to establish the tunnel.
02/04/2020
I have Road Warriors (IKEv2 client on windows using certificates) connecting from anywhere on the internet to a Mikrotik VPN router connected to the DMZ interface of the ASA. I need to know how to configure DMZ nat? so road warriors can get to inside network. The connection from Road Warriors to Mikrotik with Certificates works well, just can’t access inside netwrk thru ASA. Any recommendations?
07/04/2020
This would be a horrible solution, why would you want to do this? terminate them on the ASA outside interface that’s what the ASA is designed for?
P
16/07/2020
I’m labbing a similar situation in GNS3 and I’ve done it with one ASA and two IOS routers either side, between which a VTI is establised.
I found that apart from a 1:1 NAT on the ASA I did not need to allow ESP. UDP 500 or UDP 4500 inbound to the ASA.
17/07/2020
Hi Bill
That’s probably because you have a permit IP (which shouldn’t matter at these are protocols!) But on an ASA it does.
25/12/2020
Hi got think my problem similar this. I got error during set up vpn site to site in asa fire power.
error message: Crypto ikev1 nable outside failed to open “udp/localized/2/500”
Error: crypto ike2 port 500 on interface outside
…
Anyone can help ?
Thanks
27/12/2020
You are not port forwarding UDP port 500 anywhere are you?
20/12/2023
Assuming we have a limit for public IP (/30). Can we create a NAT using 1.1.1.2 (outside interface from Perimeter Firewall) ?
20/12/2023
Hi
I’m not sure that would work – IKE phase 1 might establish, but I suspect IPSEC phase 2 would fail. I’ll happily be proved wrong if you want to test it.