KB ID 0001279
Problem
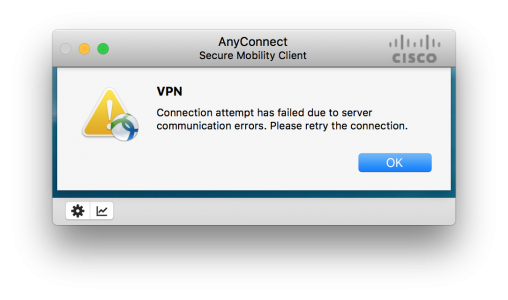
We had a firewall fail at work this week, as part of the rebuild the latest OS was put on it, version 9.7(1). I thought no more about it until I tried to VPN in and got this;
I used my Windows 10 VM and that connected fine, only my MacBook could not connect, this VPN tunnel is a big deal I need it to get onto client’s networks. I tried my other VPN connections and every one was fine, only the recently rebuilt one didn’t work? Ive seen OSX throw a wobbly with AnyConnect in the past so I did a complete uninstall, deleted the opt/cisco folder and put on the latest version (4.4.00243 at time of writing) no change.
VPN
Connection attempt has failed due to server communication errors. Please retry the connection
A look in the client message history showed me this..
Connection attempt has failed.
No valid certificates available for authentication.
I checked my certificates, and the certificate on the firewall both they, (and the certificate chain,) were fine.
Debugging AnyConnect gave NO OUTPUT at all, but debugging SSL showed me this;
Petes-ASA#dedug ssl 255
debug ssl enabled at level 255.
Petes-ASA# error:06067099:digital envelope routines:EVP_PKEY_copy_parameters:different parameters@p_lib.c:143
error:1415FFA5:SSL routines:SSL_accept:pkp error@ssl_engine.c:2832
error:06067099:digital envelope routines:EVP_PKEY_copy_parameters:different parameters@p_lib.c:143
error:1415FFA5:SSL routines:SSL_accept:pkp error@ssl_engine.c:2832
error:06067099:digital envelope routines:EVP_PKEY_copy_parameters:different parameters@p_lib.c:143
error:1415FFA5:SSL routines:SSL_accept:pkp error@ssl_engine.c:2832
error:06067099:digital envelope routines:EVP_PKEY_copy_parameters:different parameters@p_lib.c:143
error:1415FFA5:SSL routines:SSL_accept:pkp error@ssl_engine.c:2832
error:06067099:digital envelope routines:EVP_PKEY_copy_parameters:different parameters@p_lib.c:143
error:1415FFA5:SSL routines:SSL_accept:pkp error@ssl_engine.c:2832
error:06067099:digital envelope routines:EVP_PKEY_copy_parameters:different parameters@p_lib.c:143
error:1415FFA5:SSL routines:SSL_accept:pkp error@ssl_engine.c:2832
Try Googling that and getting a result! In fact that’s probably what brought you here.
Solution
If you change a Cisco OS and things like this stop working normally it’s because they’ve dropped support for something that’s got a security hole in it. In the wake of the Poodle Exploit I assumed it was an SSL/TLS problem, but that wasn’t it.
I was in the right ball park though, and a bit of lateral thinking and SSL cipher problems I’ve had with ASDM, made me think, what if it’s SHA that’s been dropped because everyone is dropping SHA1 cause it’s the hashing algorithm of Satan?
Well as soon as I added a SHA1 ciphers back in, everything started working again!
Petes-ASA(config)# ssl encryption aes256-sha1 aes128-sha1
WARNING: This command has been deprecated; use 'ssl cipher' instead.
INFO: Converting to: ssl cipher default custom "AES256-SHA:AES128-SHA"
INFO: Converting to: ssl cipher tlsv1 custom "AES256-SHA:AES128-SHA"
INFO: Converting to: ssl cipher dtlsv1 custom "AES256-SHA:AES128-SHA"
Disclaimer: SHA1 is bad, where practical all cert ciphers should be at least SHA256
Related Articles, References, Credits, or External Links
NA


15/02/2017
Awesome.. added the command in ASA and it worked
13/05/2017
This fixed my problem as well. An excellent tip.
Thank you
17/04/2019
Hi guys,
I’m not an IT specialist, how to add SHA1 ciphers in ASA. I’m using linux as a native system.
17/04/2019
You would need to connect to the ASA at command line (via the serial cable or SSH)
Login
configure terminal
ssl encryption aes256-sha1 aes128-sha1
exit
write memory
But if you are using a purchased third party certificate simply renew it for one that’s signed with SHA256 – most certificate vendors will do this for free!
24/05/2019
Great article, I was banging my head on this as well and the instructions didn’t work.
At home we are using Disney Circle for internet security for the kids. Recently I bought a new laptop which I attach to my docking almost every time. Today I did it on the wifi and Circle defined it as new device with the standard blocking rules because the wifi nic is a different mac address.
So check you internet security on this problem as well! I had the strangest issues due to this.
08/01/2021
that is a wonderful answer! appreciated!
But my AnyConnect is an App on my iPad. I don’t know how to add SHA1 ciphers directly on it.
11/01/2021
No you need to enable the Ciphers on the Firewall. Or update your iPad so it uses newer ones.
18/01/2021
I didn’t create it using ASA SSLVPN ,it used to be 7200 router This problem has come up。 webvpn again interior Using the “ssl encryption aes-sha1 3des-sha1 ” But is invalid my window 7 is ok. BUT windos 10 no. help me
17/06/2021
Hi
Am Using windows 10 with mcafee livesafe antivirus,it blocks the cisco any connect client
when ever i installed ,it working fine after the reboot of the system am facing the below error.
“Connection attempt has failed due to server communication errors.
Please retry the connection.”
i have turned off the antivirus and then try connecting the antivirus.it shows error only.
Please do the needful.
10/01/2022
Hello,
I’m facing the same issue “Connection attempt has failed due to server communication errors”
I’m using MacBook Pro with the Apple M1 Pro chip. The OS is macOS Monterey.
Anyconnect I’m using is version 4.10.03104
I’d like to know how to add the SHA1 ciphers back in. Is this something I need to do in my MacBook? What commands should I use in Terminal?
Any help would be truly appreciated.
10/01/2022
No that command needs entering onto the the device at the head end (the firewall) and your IT will probably say no, or like mine, just say “We don’t support macs”.
08/08/2023
Hey bro, do you find the resolutions for macOS?? I’m facing the same issue now.
08/08/2023
Remember it has to be supported on the head end, and on your Mac – that means doing this also https://www.petenetlive.com/kb/article/0001245
20/10/2022
Awesome!!!!Very GOOD!!