Mac SSH Error KB ID 0001245
Problem
Certified working all the way up to macOS Ventura version 13.6
Certified working all the way up to macOS Sonoma version 14.1
Certified working all the way up to macOS Sequoia version 15.6
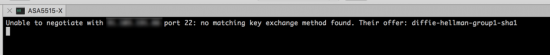
I thought my RoyalTSX had broken today, I upgraded it a couple of weeks ago, and I upgraded to macOS Catalina 10.15 the other day. After this, all my SSH sessions refused to connect with this error;
Unable to negotiate with x.x.x.x port 22: no matching key exchange found. Their offer diffie-hellman-group1-sha1
Note: You may also see the following error;
Unable to negotiate with x.x.x.x port 22: no matching cipher found. Their offer: aes128-cbc,3des-cbc,aes192-cbc,aes256-cbc
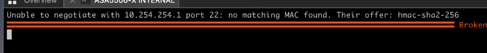
Update: 10/04/20: With newer equipment you may see the following error;
Unable to negotiate with x.x.x.x port 22: no matching MAC found Their offer: hmac-sha2-256
Update 08/12/21: With newer Cisco equipment you may see the following error;
Unable to negotiate with x.x.x.x.1 port 22: no matching key exchange method found. Their offer: diffie-hellman-group-exchange-sha1,diffie-hellman-group14-sha1
Update 21/08/25 When attempting to SSH to a Debian/Ubuntu based Linux server, you may see the following error;
Unable to negotiate with x.x.x.x port 57066: no matching host key type found. Their offer: ssh-dss,ssh-rsa
This was fixed by adding the HostKeyAlgorythms below
Mac SSH Error – Fix
WARNING: My usual fix for this is to edit the macs ssh_config file directly and allow the older (less secure) connection methods. It has been (correctly) pointed out, that this is the ‘least preferred‘ method, as it will allow these less sure methods for ALL SSH connections. The preferred fix, is to create a new file in your own home folder, with the connection settings for EACH SSH CONNECTION. However, I manage hundreds of firewalls. routers and switches so that method is a little unwieldy for me. But I will include it at the end of the article, for the more security conscious of you.
Not Apple’s fault to be fair, it’s OpenSSH version 7. SHA1 is weak, so support for it has been removed. Which is fine, but all my clients Cisco Firewalls, Routers, Switches are probably all using RSA/SHA1. So until they re all updated I’m going to need to re-enable SHA1.
Open a terminal windows and execute the following;
sudo nano /etc/ssh/ssh_config
ENTER YOUR PASSWORD
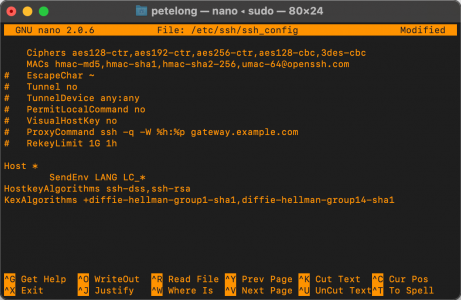
Locate the line ‘ # MACs hmac-md5,hmac-sha1,hmac-sha2-256,umac-64@openssh.com,hmac-ripemd160′ and remove the Hash/Pound sight from the beginning, and add the extra hashing algorithm that I’ve shown above in red.
Locate the line ‘ # Ciphers aes128-ctr,aes192-ctr,aes256-ctr,aes128-cbc,3des-cbc’ and remove the Hash/Pound sight from the beginning.
Then paste the following on the end;
HostkeyAlgorithms ssh-ed25519,ecdsa-sha2-nistp256,rsa-sha2-256,rsa-sha2-512,ssh-rsa,ssh-dss
KexAlgorithms +diffie-hellman-group1-sha1,diffie-hellman-group14-sha1
Like so;
Mac SSH Error – Quitting Nano
To quit nano, use the Ctrl-X key combination. because you are working on has been modified since the last time you saved it, you will be prompted to save the file first. Type y to save the file.
Theres no reason to reboot, it should work straight away.
But Wait – Theres More!
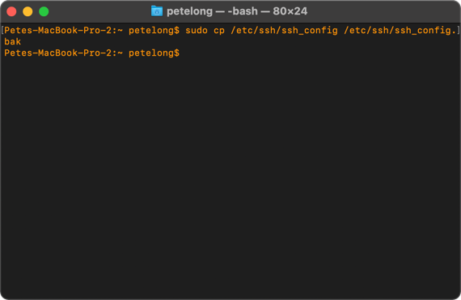
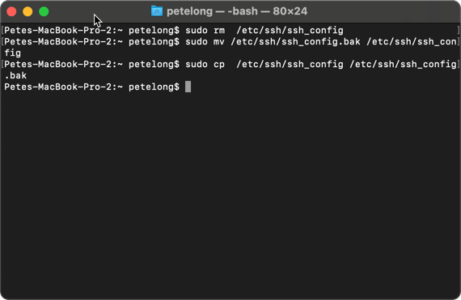
It’s going to happen every time you upgrade your mac, I’ve started taking a backup of the ssh_config file, then I can just restore it back again, like so;
Backup macOS SSH Settings & Ciphers
sudo cp /etc/ssh/ssh_config /etc/ssh/ssh_config.bak
Restore macOS SSH Settings & Ciphers
sudo rm /etc/ssh/ssh_config sudo mv /etc/ssh/ssh_config.bak /etc/ssh/ssh_config sudo cp /etc/ssh/ssh_config /etc/ssh/ssh_config.bak
Mac SSH Error (The More Secure & Preferred) Fix
Using this method you will create a connection (entry) for each asset you want to connect to. This will be saved in your Home directory so if multiple people use the Mac you will need to do this for each user.
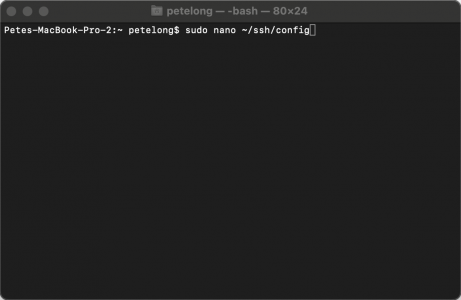
Firstly create a config file in you home directory.
sudo nano ~/ssh/config
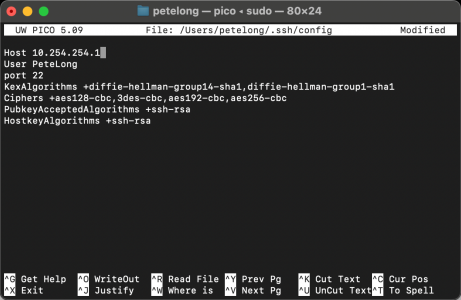
What this does is create a blank file that you can then create an entry for each of the assets you want to connect to. Firstly specify the hostname, then the settings for that particular asset, like so:
Host YOUR-SWITCH User YOUR-USER port 22 KexAlgorithms +diffie-hellman-group14-sha1,diffie-hellman-group1-sha1 Ciphers +aes128-cbc,3des-cbc,aes192-cbc,aes256-cbc PubkeyAcceptedAlgorithms +ssh-rsa HostkeyAlgorithms +ssh-rsa
Note: Simply add new host entries at a new line in the SAME config file.
Related Articles, References, Credits, or External Links
SSH: Host Identification Has Changed

28/11/2016
I tried your work around, but it only gives me a different error. Is it possible that something more needs to be changed? Thanks
29/11/2016
What Error did you get?
P
05/07/2017
Fixed the issue immediately. Thanks
12/05/2018
2018 and this advice is still good. Fixed my problem too. Thanks!
26/07/2018
nice it works and solve the issues…
thanks,
28/10/2019
Worked for me, 2019
16/01/2020
2020 still working !! I fixed my problem too.
08/12/2020
End of 2020, and this still works to get me on legacy systems.
20/09/2021
Is it possible you forgot a comma , after typing in hmac-sha2-256? Because that’s what I did at first try 😛
02/12/2021
Hi, I got a new Macbook pro with M1 chip and I am trying to SSH into my cisco switches. I tried your fix, but I still get the same error.
Below is the error I am getting,
Akhils-MacBook-Pro:~ akhilb$ ssh bwadmin@10.8.64.1
Unable to negotiate with 10.8.64.1 port 22: no matching key exchange method found. Their offer: diffie-hellman-group-exchange-sha1,diffie-hellman-group14-sha1
08/12/2021
Fixed see comments above ^^^
04/05/2022
2022 and this still works immediately! Thank you!
Curious, instead of a `.bak` file, could you make a symlink to somewhere else? And would that symlinked file then be “updated” with each mac update? I don’t know, just asking
01/12/2016
Thanks a lot for this. Helped me straight away!!!
01/12/2016
No Probs – Glad to help 🙂 P
07/12/2016
Still perfect.
Thanks For all.
07/12/2016
Thanks for this.Work just as described!
28/12/2016
Worked like a charm – Thanks!
29/12/2016
It Works! Thanks
04/01/2017
It didn’t like me allowing that line. It kept throwing up a new error, though to be fair, my line was longer and looked different.
However, putting the pound sign back and just adding that bit to the bottom worked straight away.
Thanks for the help.
05/01/2017
Using all 3 changes will invalidate all host-keys in ‘known_hosts’.
Only the last line was actually needed for me: KexAlgorithms diffie-hellman-group1-sha1
With the caveat that this will force all ssh negotiations down to this less secure protocol.
A better option is to leave /etc/ssh/ssh_config alone alltogether, and create ~/.ssh/config in your home-dir (alongside the known_hosts file)
In ~/.ssh/config create an entry as follows for the equipment that use this key-exchange. Use as identification the name or ip you actually use on your commandline. (i.e. use ‘192.168.0.1’ or ‘firewall’ if you use ‘ssh 192.168.0.1’ or ‘ssh firewall’)
#force key exchange:
host 192.168.0.1 firewall.local firewall
KexAlgorithms diffie-hellman-group1-sha1
10/02/2017
That worked also. Thanks!
26/12/2018
This is great. I updated my Mac to 10.13.6 on 12/26/2018 and both my SSH and Sublime Text SFTP stopped working. (But my Cyberduck SFTP and Microsoft Remote Desktop continued to work.)
Using the steps in the initial post didn’t work for me. It resulted in an alert that I would be open to a “Man in the Middle” attack and it didn’t allow me to continue.
However, this comment helped me fix this issue. Now my SSH and Sublime Text SFTP work by creating a ~/.ssh/config file in my local user folder and adding the lines at the end of the file. (Note: 999.999.9.9 is the IP address of the remote server you want to log into.)
# force key exchange:
host 999.999.9.9 firewall.local firewall
KexAlgorithms diffie-hellman-group1-sha1
05/01/2024
my .ssh/config file looks like this :
#force key exchange:
Host 192.16.4.203
KexAlgorithms +diffie-hellman-group1-sha1
[It failed with the error Unable to negotiate with 192.168.0.2 port 22: no matching key exchange method found. Their offer: diffie-hellman-group1-sha1]
31/01/2017
Thanks a lot, this worked a treat for me. : )
07/02/2017
Thanks a lot.. IT worked for me..
07/02/2017
Muchas Gracias, Work
14/02/2017
Perfect!! Thanks so much!!
17/02/2017
Fabulous. Best Cisco resource on the Internet.
18/02/2017
ThanQ!
06/03/2017
Just what I needed, thanks!
07/03/2017
Worked PERFECTLY!!!! Thank you.
24/03/2017
Thanks for the pointers. I only needed the last line in order to SSH onto my legacy Cisco switches. Also, it’s more secure to use a “+” which appends SHA1 to the usable set of algorithms, rather than using SHA1 as the default algorithm.
KexAlgorithms +diffie-hellman-group1-sha1
25/03/2017
Hi, Great response! I’ve update the article accordingly ThanQ
P
25/03/2017
Fantastic! Helped when I needed it!
29/03/2017
It only happens if the Cisco device is using IOS version 12 or older. Version 15 works fine. If you have smartnet contract with Cisco, just upgrade to the recommended software. Instead of messing around with ssh file, I just ssh to an unix server and then ssh to Cisco device.
03/04/2017
Thats fine, but what about Cisco ASA? The problem is inherently a client one, some people don’t have modern code on their devices.
Pete
08/04/2017
I’ve run into this problem with Arris products as well.
21/05/2017
We’re going to secure ourselves right out of being able to work!
Thanks for this – you were the first result when I Googled the problem!
02/06/2017
Thanks a lot ! It’s work for me.
13/06/2017
Just adding the KexAlgorithms +diffie-hellman-group1-sha1 lines to the end of my ssh_config file worked on Mac OSX 10.12.5 (16F73)
Thanks !
Dan
11/06/2017
Hi,
I had to do this to make it work:
Ciphers aes128-ctr,aes192-ctr,aes256-ctr,arcfour256,arcfour128,aes128-cbc,3des-cbc
MACs hmac-md5,hmac-sha1,umac-64@openssh.com,hmac-ripemd160
KexAlgorithms +diffie-hellman-group1-sha1
HostkeyAlgorithms ssh-dss,ssh-rsa
11/06/2017
Thanks so much… this works PERFECTLY.
12/06/2017
No problem glad to help
P
03/07/2017
Big ups to my dawg. This worked like a charm. And I’m computer illiterate.
03/07/2017
No worries – Glad to help!
Pete
25/09/2017
Thank you
26/10/2017
Worked perfectly on High Sierra. Thanks 🙂
26/11/2017
Just upgraded to High Sierra and started getting this when connecting to an ASA. Thanks for the workaround!
07/12/2017
This worked perfectly. Have you had any issues getting usb-c port support serial connection? unable to get my macbook pro running Sierra to support belkin usb to serial cable for connection my Cisco console cable. I tried adding drivers and using suggestions on web. None work. Love your input. Maybe you can do a post on it. – thanks Isha
14/12/2017
I’ve not, I’ve got a standard USB converter (bought cheap off eBay) and I’ve never had any problems?
P
19/12/2017
So ran into this again after upgrading to High Sierra 10.13.2…
This time I had to add to /etc/ssh/ssh_config
Ciphers aes128-ctr,aes192-ctr,aes256-ctr,aes128-cbc,3des-cbc
KexAlgorithms diffie-hellman-group1-sha1
04/03/2018
Hi
I work with 10.3.3 and had problems accessing Cisco equipment in the network. With these two lines it works. Thank you very much everyone for the contribution.
20/12/2017
Thanks, fixed the issue!
26/01/2018
Thank you so much!!!!
16/02/2018
Was pulling my hair out with this at work. Issue compounded by everything by being Dockerized with very minimal Linux installations. This was the missing piece of the puzzle. Thank you so much for documenting this and putting it out there!
26/02/2018
👍👍👍
05/03/2018
Thanks! That works!
16/03/2018
Thanks a million
10/04/2018
Thanks!
17/04/2018
Worked like a charm.
Thanks a lot!
01/05/2018
That worked great for my Adtran AOS equipment!
I was getting an error Bad SSH2 Mac spec ‘hmac-md5,hmac-sha1,hmac-ripemd160’, so I removed hmac-ripemd60, which fixed the issue.
sudo nano ~/.ssh/config
#force key exchange:
host 192.168.1.54
Ciphers aes128-ctr,aes192-ctr,aes256-ctr,aes128-cbc,3des-cbc
MACs hmac-md5,hmac-sha1,umac-64@openssh.com
KexAlgorithms +diffie-hellman-group1-sha1
HostkeyAlgorithms ssh-dss,ssh-rsa
13/06/2018
Thanks!
31/08/2018
This works great, thanks
31/08/2018
I am now getting an error “port 22: Invalid key length”
01/09/2018
Check what you are connecting ‘to’ does not have a short key length on the certificate, either 1024 or 768 is too short.
26/09/2018
Got it to work on 10.13.6 by only using these two lines:
Ciphers aes128-ctr,aes192-ctr,aes256-ctr,aes128-cbc,3des-cbc
HostkeyAlgorithms ssh-dss,ssh-rsa
Having all four lines resulted in a “connection closed by host” error (too many ciphers offered).
thanks!
19/10/2018
Grateful, Thanks
05/11/2018
Thanks, you are a life saver!!
23/11/2018
Thanks
04/12/2018
+1 Thanks
31/01/2019
On MarBook Pro 2018.
Tried the solution, but make the changes in /etc/ssh/ssh_config affect other exciting known_hosts.
Specifying accepting additional key exchange method in ~/.ssh/config for the target seems the better way.
Host ASAv
Hostname myASAv.my.com
User admin
KexAlgorithms +diffie-hellman-group1-sha1
IdentityFile ~/.ssh/asav-private-key
Then you can ssh
ssh ASAv
31/01/2019
Hi, if you have one to two ASAs to connect to that fine, I’ve got literally hundreds of the things, across multiple clients 🙂
Pete
15/03/2019
Thank You my friend.
It´s working perfect.
Thanks a lot.
21/05/2019
how do you use the shortcut keys at the bottom… I tried using ^6 + enter and does not work…
22/05/2019
CTRL+{The letter indicated}
P
07/06/2019
perfetto grazie
20/06/2019
2019 Still works, fixed my issues.
11/09/2019
Sep 2019, and the solution works!
02/10/2019
Just took the leap to Mojave and SSH was broken. Now it is fixed. Way to go!!
18/10/2019
On Mojave and still works. Thanks!!
14/11/2019
That fixed it for me! Thanks!
16/12/2019
Hi OSX 15.2 has deleted Protocol 1 even from the comments ..
please post how to get it back.. or are the LIB’s gone for ever?
{ssh_config content supplied but removed}
18/12/2019
I’ve just updated to macOS Catalina 10.15.2 and this still works fine
28/12/2019
Worked like a charm. Many thank youz 🙂
02/01/2020
Perfect!
28/01/2020
Thank you!!! Worked Perfectly!
03/02/2020
Thank you!!, Worked!
13/02/2020
It worked perfectly
15/02/2020
Dear PeteLong,
It worked for me also on Mojave!
Thanks,
Ev. Drikos
21/03/2020
Excelente , funciona el fix….Gracias
03/04/2020
Thank you!! Worked Perfectly
06/04/2020
Been looking for a solution to SSH to my Cisco Catalyst 3650 for about an hour.
Your solution worked instantly! Can’t thank you enough. Great tutorial!
27/04/2020
Thank’s a lot best regards
merci a toi pour ce fabuleux travail heureusement qu’il y a des personnes comme toi
Merci beaucoup
11/09/2020
Awesome workaround
Many thanks!
02/10/2020
Simple solution to a common problem on Macbooks trying to connect to older devices. Thanks!!
14/10/2020
Cheers Mate! Many Thanks! Was about ready to chuck my mac book.
MacOSX High Sierra October 2020 – works to ssh to my older Cisco switches.
I could change cipher suite on all the hundreds of switches, but easier to do in in one place from my desk.
14/10/2020
Your welcome – bookmark the link because every update you will need to do it again!
29/10/2020
Done and Done.
Thanks again Mate! Brilliant.
23/10/2020
Pete — cannot get this working under Catalina 10.15.7. I’ve worked this fix many times and re-checked my new config. Error I get is this:
kex_exchange_identification: read: Connection reset by peer
26/10/2020
Im on 10.15.6 – Ill await the next update to see if it breaks.
20/12/2020
Pete,
Please let me know how to save and exit.
23/12/2020
Article updated with this info.
01/02/2021
Thanks a lot! it worked
07/04/2021
works in 2021 on M1 Mac, thank you!!
23/04/2021
Thank you
18/10/2021
To make the file immutable (uneditable by anything even OS.
Type chattr +i /etc/ssh/sshd_config
If you need to change it just type chattr -i /etc/ssh/sshd_config
This will stay even on OS upgrades.
22/10/2021
Hi Alex,
That’s a great tip, I’ll do that today and test it over the next upgrade!
Pete
22/10/2021
Hmmm: chattr is not recognised ‘command not found’ should we not be using chflags?
I’ve used “sudo chflags schg /etc/ssh/sshd_config” let’s see how that works!
Pete
20/10/2021
Worked for me .. Thank you
26/10/2021
macOS Monterey upgrade and newer Cat9k switches. Had to use “KexAlgorithms +diffie-hellman-group1-sha1,diffie-hellman-group14-sha1” for the last line to get everything working.
03/11/2021
Worked for me to fix SSH problems after upgrade to Monterey.
Although I also had to comment out old host SHA fingerprints in ssh/known_hosts.
05/01/2024
I’m on Sonoma and this solution is not working:
ssh -oKexAlgorithms=+diffie-hellman-group1-sha1 -c aes256-ctr user@192.168.4.203
ssh: connect to host 192.168.4.181 port 22: Operation timed out
07/12/2021
Outstanding… worked like a charm. I just added a key for diffie-hellman-group14-sha1, because that was also popping up for me as well. Thank you very much!
26/01/2022
Thank you very much.
Works perfect!!!
24/02/2022
This worked great for getting SSH working thank you!
What I am still having trouble with is SCP on the same router from the same computer that can SSH. Any thoughts?
01/03/2022
Your SCP client might not ee using the same Crypto as the MacOS host – Try a different SCP software.
03/03/2022
Ran into this issue when my company replaced my Macbook for a new one running Monteray. Happy to say this fix is still working in March 2022. Thanks a lot for this!
04/03/2022
Fixed the issue immediately. Thank you! March 2022
08/03/2022
Looked in many places, this is by far the best solution! Many thanks…
11/03/2022
Worked perfectly allowing me to access an old ReadyNAS NAS storage device which I could no l longer get to after upgrading to MacOS Monterey. Thank you so much!
11/04/2022
This worked like a charm until last weekend update broke it again on Monterey 12.3.1
11/04/2022
It will happen every time you update my friend!
P
28/04/2022
Note this still works with Monterey 12.3.1; I had the .bak file from a previous update so just copied it and it worked immediately; no reboot necessary.
28/05/2022
may 2022, macOS 12.4, this saved my ass more than one time. Thanks a milion 🙂
01/07/2022
July 2022 and this still works (on macOS Monterey v12.4)!
15/07/2022
Hi Edward,
Agreed, next time I have to do this I’ll update the article. Thanks for the feedback!
P
24/08/2022
Still works on macOS Montery 12.5.1, thanks
15/11/2022
Thanks, It worked for me on MacOS Ventura 13.0.1
21/02/2023
Hi, thanks for the good article and all the comments and insights.
I’m on Ventura 13.1 and needed to use the following in my ~/.ssh/config file
host 192.168.1.150
HostkeyAlgorithms ssh-dss,ssh-rsa
Ciphers aes128-ctr,aes192-ctr,aes256-ctr,aes128-cbc,3des-cbc
KexAlgorithms +diffie-hellman-group1-sha1,diffie-hellman-group14-sha1
22/03/2023
Thanks Bart! I just updated to Ventura and encountered this problem trying to ssh to my old Cisco router and switch.
Your version of the fix worked perfectly for me
29/06/2023
Still working in 2023
06/07/2023
Works on macos monterey 2023, thanks
07/12/2023
Hi,
I need your advice. After adding all the suggested configs there is sill an error coming up and I can’t ssh into my 3850.
Unable to negotiate with x.x.x.x port 22: no matching host key type found. Their offer:
Here is how my ssh_config looks like:
# StrictHostKeyChecking ask
# IdentityFile ~/.ssh/id_rsa
# IdentityFile ~/.ssh/id_dsa
# IdentityFile ~/.ssh/id_ecdsa
# IdentityFile ~/.ssh/id_ed25519
# Port 22
Ciphers aes128-ctr,aes192-ctr,aes256-ctr,aes128-cbc,3des-cbc
MACs hmac-md5,hmac-sha1,hmac-sha2-256,umac-64@openssh.com
# EscapeChar ~
# Tunnel no
# TunnelDevice any:any
# PermitLocalCommand no
# VisualHostKey no
# ProxyCommand ssh -q -W %h:%p gateway.example.com
# RekeyLimit 1G 1h
# UserKnownHostsFile ~/.ssh/known_hosts.d/%k
Host *
SendEnv LANG LC_*
HostkeyAlgorithms ssh-dss,ssh-rsa
KexAlgorithms +diffie-hellman-group1-sha1,diffie-hellman-group14-sha1
and the error on the switch is:%SSH-3-NO_MATCH: No matching hostkey algorithm found: client ssh-dss,ssh-rsa server
It is a MAC apple chip Sonoma 14.1.2 (23B92)
Any advice is very welcome
17/12/2023
Fixed in the local ssh config file (~/.ssh/config) with the following settings:
Host *YOUR_SWITCH*
HostName *YOUR_SWITCH*
User *YOUR_USER*
port 22
KexAlgorithms +diffie-hellman-group14-sha1,diffie-hellman-group1-sha1
Ciphers +aes128-cbc,3des-cbc,aes192-cbc,aes256-cbc
PubkeyAcceptedAlgorithms +ssh-rsa
HostkeyAlgorithms +ssh-rsa
20/12/2023
No need to remove the Hash/Pound sight for following:
#KexAlgorithms +diffie-hellman-group14-sha1,diffie-hellman-group1-sha1
#Ciphers +aes128-cbc,3des-cbc,aes192-cbc,aes256-cbc
Just add following two lines:
PubkeyAcceptedAlgorithms +ssh-rsa
HostkeyAlgorithms +ssh-rsa
Confirmed with Ubuntu ssh client.
28/03/2024
For Royal TSX users specifically, I found a much simpler way to “solve” this issue. Open the connection’s properties page and go to Advanced > SSH > Advanced > Additional SSH Options and copy/paste in the following line
-o KexAlgorithms=+diffie-hellman-group14-sha1,diffie-hellman-group1-sha1 -o Ciphers=+aes128-cbc,3des-cbc,aes192-cbc,aes256-cbc -o PubkeyAcceptedAlgorithms=+ssh-rsa -o HostkeyAlgorithms=+ssh-rsa
The format of that page is weird in that it looks like you have to check the “Disable pseudo-terminal allocation” checkbox above it enable the “Additional SSH Options” field but I’ve verified it is not required.
No editing conf files needed and you can enable this on a per connection basis right from within the Royal TSX app. Easy Peezy.
02/04/2024
This looks like an outstanding Tip! I use RoyalTSX myself so I’ll give it a whirl after my next upgrade. Thanks for posting.
P
28/06/2024
Insane that in 2024, on IOS-XE 17.2.3, that Cisco still doesn’t support anything more secure than SHA1….
13/02/2025
I just did a fresh install of MacOS 15.3.1 and this method doesn’t seem to work any more. I had to add the HostkeyAlgorithms and KexAlgorithms lines to the ~/.ssh/config file and then it allowed me to ssh to older devices again.
14/02/2025
I’m running 15.3.1 and I’m still using this procedure?
P
01/03/2025
I tried it on Windows, but without success. I got new error 😀
03/03/2025
This is for macOS look for the Windows article, search is top right of the page
26/05/2025
How can I fix this error? I did what was said on this page, and it still did not help. Mac os version sequoia 15.5
Unable to negotiate with x.x.x.x port 22: no matching key exchange method found. Their offer: diffie-hellman-group-exchange-sha1,diffie-hellman-group1-sha1
30/05/2025
This is what I saved in a file to reference and it is correctly working, your file has to look just like this to work. macOS 15.5 confirmed
sudo nano /etc/ssh/ssh_config
# Port 22
Ciphers aes128-ctr,aes192-ctr,aes256-ctr,aes128-cbc,3des-cbc
MACs hmac-md5,hmac-sha1,hmac-sha2-256,umac-64@openssh.com
# EscapeChar ~
# Tunnel no
# TunnelDevice any:any
# PermitLocalCommand no
# VisualHostKey no
# ProxyCommand ssh -q -W %h:%p gateway.example.com
# RekeyLimit 1G 1h
# UserKnownHostsFile ~/.ssh/known_hosts.d/%k
Host *
SendEnv LANG LC_*
HostkeyAlgorithms ssh-dss,ssh-rsa
KexAlgorithms +diffie-hellman-group1-sha1,diffie-hellman-group14-sha1
To back up:
sudo cp /etc/ssh/ssh_config /etc/ssh/ssh_config.bak
To restore file:
sudo rm /etc/ssh/ssh_config
sudo mv /etc/ssh/ssh_config.bak /etc/ssh/ssh_config
sudo cp /etc/ssh/ssh_config /etc/ssh/ssh_config.bak
18/08/2025
This config changes has saved me in the past. I had an issue awhile back, and had taken it into the Apple Store for a “factory clean”. When I got it back it was like a new MacBook Pro. but ssh no longer worked for me.
In the ssh config, I went through the steps, but it is still not working. I am on Sequoia 15.6. if that matters.
What I get:
no matching key exchange method found. Their offer: diffie-hellman-group-exchange-sha1,diffie-hellman-group14-sha1
current settings in the ssh config:
# Port 22
Ciphers aes128-ctr,aes192-ctr,aes256-ctr,aes128-cbc,3des-cbc
MACs hmac-md5,hmac-sha1,hmac-sha2-256,umac-64@openssh.com
# EscapeChar ~
# Tunnel no
# TunnelDevice any:any
# PermitLocalCommand no
# VisualHostKey no
# ProxyCommand ssh -q -W %h:%p gateway.example.com
# RekeyLimit 1G 1h
# UserKnownHostsFile ~/.ssh/known_hosts.d/%k
Host *
SendEnv LANG LC_*
HostkeyAlgorithms ssh-dss,ssh-rsa
KexAlgorithms +diffie-hellman-group1-sha1,diffie-hellman-group14-sha1
What am I missing?
19/08/2025
This SSH error:
no matching key exchange method found. Their offer: diffie-hellman-group-exchange-sha1,diffie-hellman-group14-sha1
means that the SSH client you’re using doesn’t support the key exchange algorithms offered by the server. These algorithms are considered weak or deprecated, especially in modern SSH clients that disable them by default for security reasons.
Add
Host legacy-host
KexAlgorithms +diffie-hellman-group14-sha1
To your SSH file (see the screenshot above) (Which I CAN SEE you’ve done, so something else is stopping you)
What does
ssh -oKexAlgorithms=+diffie-hellman-group14-sha1 user@host
Give you?
20/08/2025
This was the response I received
The authenticity of host ‘x.x.x.x (x.x.x.x)’ can’t be established.
RSA key fingerprint is SHA256:HcO5+D9Ag3NY8OAQ6S+T1KHnmKmERZtBQxuYY7u5iY8.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
I tried and succeeded in connecting to the equipment.
21/08/2025
That’s normal behaviour – you are just accepting the cert to connect. It won’t ask next time.
P
23/09/2025
On macOS 26 Tahoe, ssh-dss (DSA) keys are no longer supported.
Edit your SSH config file via Terminal and remove ssh-dss from the HostKeyAlgorithms line — e.g., change HostKeyAlgorithms +ssh-dss,ssh-rsa to HostKeyAlgorithms +ssh-rsa — to restore SSH connectivity.
Works again using Royal TSX.