KB ID 0001210
Problem
This week I’ve been working on changing the site over to https. Buying a digital certificate used to be an expensive long winded affair, but not anymore. A quick internet search turned up a 3 year SSL certificate for less than 15 quid.
Getting the certificate was the easy bit, getting it installed so that Apache would use it was another ‘challenge’. On a scale of one to ten, I’m about a three (on a good day) with Linux!
Before you start, you need to generate a CSR and send that to whoever you are going to buy your cert from
Linux (CentOS 7) Generating CSR (Certificate Signing Requests)
What about free Certs? There are some firms that offer free certs, some require you to install software that updates the cert every ninety days, other have a short lifespan. I’m not usually one to spend any money but for a fiver a year, why not?
Solution
Your certificate vendor will sent you your certificate, it will probably come with at least one other cert. In my case it came with three other CA Certs (a RootCA and two Intermediate CA Certs). If you are unfamiliar with certificates, here’s the two golden certificate rules;
- You MUST trust the authority (CA), that issued the certificate, or issued the cert to the CA that issued the cert etc.
- The NAME on the certificate, either the Common Name (CN), or the Subject Alternative Name (SAN). MUST match the address you are going to.
What you will find with these <ahem> cheaper certificates, is that you trust a CA, and that CA issues another CA Certificate, (to a subordinate CA), that Issues another CA Certificate (To a Subordinate CA), and that CA issues your certificate. All these certificates form a ‘chain’ and it looks like this;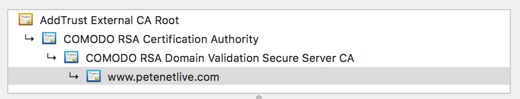
OK why is that important? Well to trust your certificate, your visitors, (and Apache) need to be able to see all the certificates in this chain, right back to the RootCA certificate at the top (which they will trust, or there’s not much point selling them!)
Some vendors will give you a certificate bundle, mine did not so I had to make one (this is not hard to do, see below). But now when you make that certificate bundle, you will have a better understanding of what you are doing, (putting all the CA certs in the chain order, into one file).
Installing SSL Certificates Into Apache
Before you start you may need to install mod_ssl ‘yum install mod_ssl’ will do that 🙂
First you need to copy all the files into CentOS, I created a folder in ‘/etc/ssl/’ called ‘localcertificates’ and copied in the domain cert, the key file (that got generated when I made the CSR – See the link above). And I’ve copied in all the CA Certificates. (I use FileZilla to do this because it’s free, and easy to use).
Now Log into your CentOS server via SSH and navigate to this directory, then use the ‘CAT’ command to make a certificate bundle with all your CA Certificates, (notice the order, SubCA2 > SubCA1 > RootCA). Note: Your certificates will probably have different names.
cd /etc/ssl/localcerts cat COMODORSADomainValidationSecureServerCA.crt COMODORSAAddTrustCA.crt AddTrustExternalCARoot.crt > My-CA.ca-bundle
Now in the same directory you will have another file called My-CA.ca-bundle. To get Apache to use the certificates you need to edit the httpd.conf file. In CentOS 7 that usually lives in ‘/etc/httpd/conf’. I use nano because it’s easier to edit files with, (yum install nano). Im also going to back-up the config up as well, in case something goes wrong!
cd /etc/httpd/conf cp httpd.conf httpd.conf-old nano httpd.conf
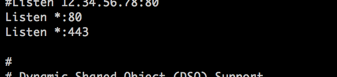
Locate the part of the file that says ‘Listen *.80’ and place a line below it that says ‘Listen *.443’.
Scroll to the end of the file and paste in the following, (change the filenames to match your own).
<VirtualHost *:443>
SSLEngine On
SSLCertificateFile /etc/ssl/localcerts/your-file.crt
SSLCertificateKeyFile /etc/ssl/localcerts/your-file.key
SSLCertificateChainFile/etc/ssl/localcerts/My-CA.ca-bundle
ServerAdmin admin@your-domain.com
ServerName www.your-site.com
DocumentRoot /var/www/html
ErrorLog /var/www/logs/error.log
CustomLog /var/www/logs/access.log combined
</VirtualHost>
Note: Make Sure the Logs folder exists in /var/www if you use the same paths as me! Also SSLCertificateChainFile will change in newer versions of Apache to SSLCACertificatePath.
You can now restart Apache and browse to https://www.your-site.com. It can take a little while before it’s back up!
apachectl restart apachectl status
Everything’s Broken Help!!
This is why we backed up the config, first if there’s a problem ‘apache status’ usually says ‘theres a problem on line XYZ of the httpd.conf file’, if you open it in a text editor that will point you to a resolution. If all else fails, you can restore the original config like so;
cd /etc/httpd/conf cp httpd.conf-old httpd.conf apachectl start apachectl status
How To Redirect All HTTP Traffic to HTTPS in Apache?
That’s even easier, if you have a virtual host for poor 80 already setup in https.conf then just add ‘ Redirect / https://www.your-site.com/’ to it. I did not, but adding one did not break/affect my site at all. After the text you pasted in above for the virtualhost for SSL just paste in a new one for http (TCP port 80).
<VirtualHost *:80> ServerName www.your-site.com DocumentRoot /var/www/html ErrorLog /var/www/logs/error80.log CustomLog /var/www/logs/access80.log combined Redirect / https://www.your-site.com/ </VirtualHost>
Related Articles, References, Credits, or External Links
NA