AnyConnect Group Authentication With Cisco ISE and Downloadable ACLs (Part 1)
KB ID 0001155
Problem
To be honest it’s probably a LOT easier to do this with Dynamic Access Policies, but hey, if you have ISE then why not use it for RADIUS, and let it deploy downloadable ACL’s to your remote clients and give them different levels of access, based on their group membership.
I’m going to keep things simple, I will have a group for admins that can access anything, and a group for users that can only RDP to internal servers.
I always assume things will break, so I’m also going to create a local user on the ISE deployment, so if Active Directory is down I will have a user account I can use to gain full access in the event of an emergency.
Solution
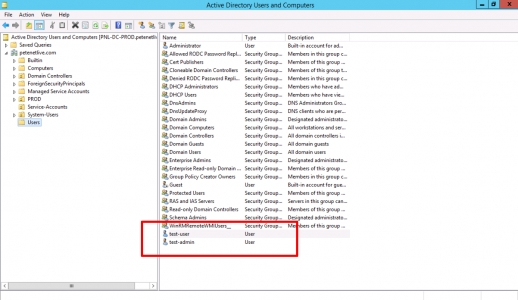
In production you will have plenty of users, but to test Im going to create a test user, and a test admin user.
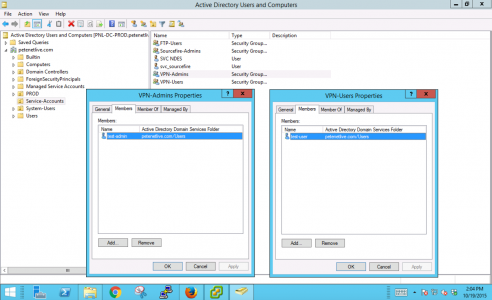
Then put those users in an appropriate Active Directory security group, (here I’m using VPN-Users and VPN-Admins).
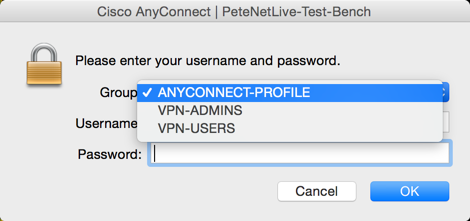
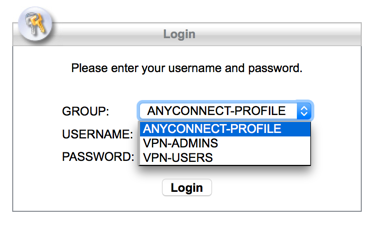
Now you will also need a ‘Tunnel-Group and a matching Group-Policy on the ASA to map the user groups to. That way, when a user connects they can pick the appropriate tunnel group like so;
So what I’ve done is setup AnyConnect and configured it properly, (see article below) then I’ve simply ‘cloned‘ the tunnel group, and group policy to create a VPN-ADMIN and VPN-USERS tunnel-group ,and a group-policy. So my ASA config is as follows;
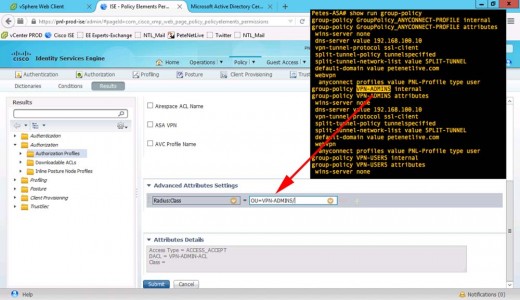
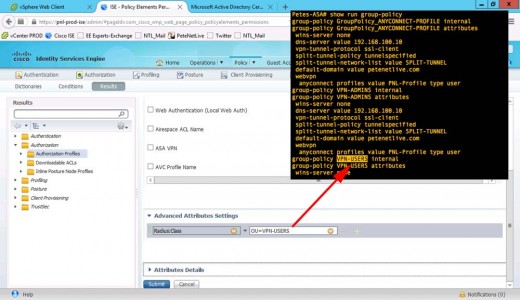
1. Show run ip local pool Petes-ASA# show run ip local pool ip local pool ANYCONNECT-POOL 192.168.101.1-192.168.101.254 mask 255.255.255.0 Petes-ASA# 2. Show Group-Policy Petes-ASA# show run group-policy group-policy GroupPolicy_ANYCONNECT-PROFILE internal group-policy GroupPolicy_ANYCONNECT-PROFILE attributes wins-server none dns-server value 192.168.100.10 vpn-tunnel-protocol ssl-client split-tunnel-policy tunnelspecified split-tunnel-network-list value SPLIT-TUNNEL default-domain value petenetlive.com webvpn anyconnect profiles value PNL-Profile type user group-policy VPN-ADMINS internal group-policy VPN-ADMINS attributes wins-server none dns-server value 192.168.100.10 vpn-tunnel-protocol ssl-client split-tunnel-policy tunnelspecified split-tunnel-network-list value SPLIT-TUNNEL default-domain value petenetlive.com webvpn anyconnect profiles value PNL-Profile type user group-policy VPN-USERS internal group-policy VPN-USERS attributes wins-server none dns-server value 192.168.100.10 vpn-tunnel-protocol ssl-client split-tunnel-policy tunnelspecified split-tunnel-network-list value SPLIT-TUNNEL default-domain value petenetlive.com webvpn anyconnect profiles value PNL-Profile type user Petes-ASA# Show Tunnel Groups Petes-ASA# show run tunnel tunnel-group ANYCONNECT-PROFILE type remote-access tunnel-group ANYCONNECT-PROFILE general-attributes address-pool ANYCONNECT-POOL default-group-policy GroupPolicy_ANYCONNECT-PROFILE tunnel-group ANYCONNECT-PROFILE webvpn-attributes group-alias ANYCONNECT-PROFILE enable tunnel-group VPN-ADMINS type remote-access tunnel-group VPN-ADMINS general-attributes address-pool ANYCONNECT-POOL default-group-policy VPN-ADMINS tunnel-group VPN-ADMINS webvpn-attributes group-alias VPN-ADMINS enable tunnel-group VPN-USERS type remote-access tunnel-group VPN-USERS general-attributes address-pool ANYCONNECT-POOL default-group-policy VPN-USERS tunnel-group VPN-USERS webvpn-attributes group-alias VPN-USERS enable Petes-ASA#
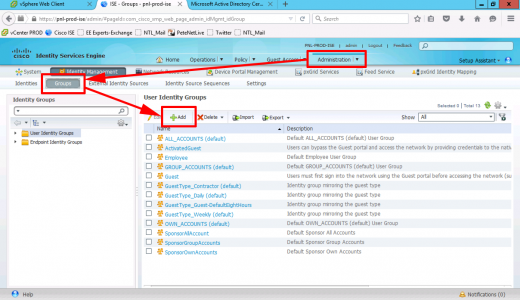
Create a Local Admin Group in Cisco ISE
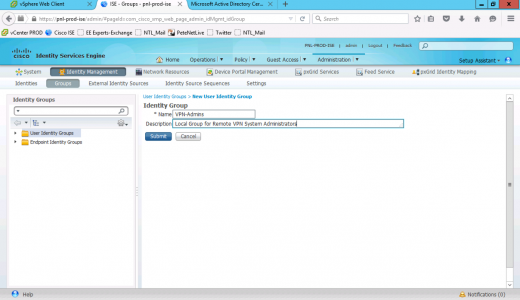
On your Cisco ISE Deployment > Identity Management > Groups > Add.
Give the group a name and optional description > Save.
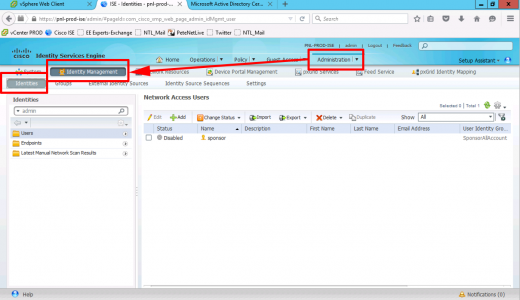
To create an admin user > Administration > Identity Management > Identities > Add.
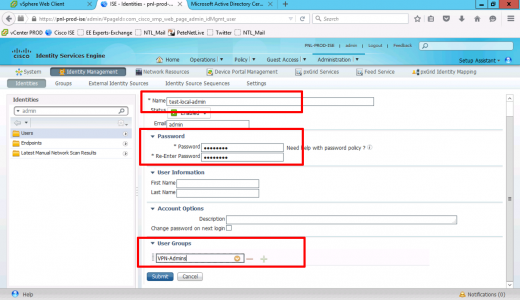
Create the new admin user > set the password > add the user to the group you create above.
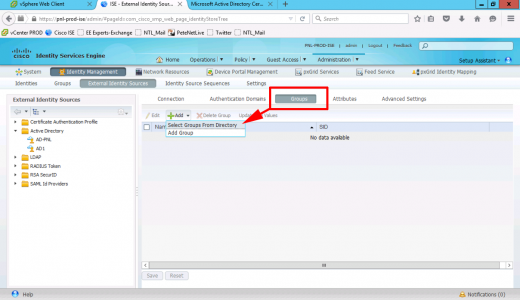
Adding Domain Groups To Cisco ISE
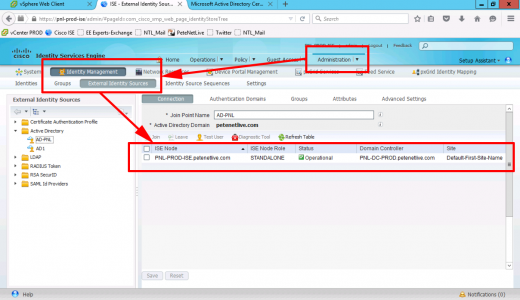
I’m assuming you have joined ISE toActive Directory > To check Administration > Identity Management > External Identity Sources > Ensure the domain is joined and operational.
Groups > Add.
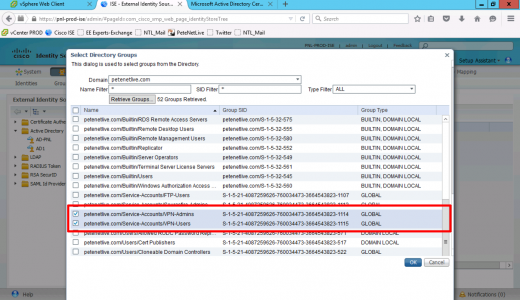
Locate and add the groups you created above.
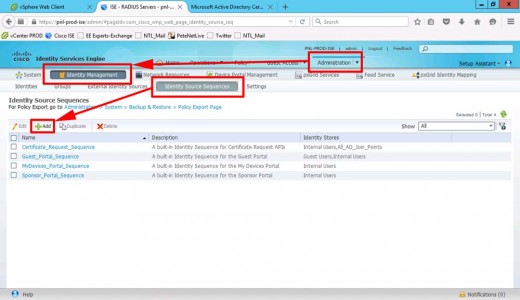
Add An Active Directory Identity Source Sequence
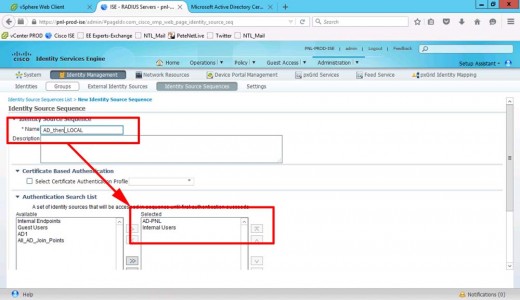
We need to authenticate against our AD, but we want it to fail back to the ISE local database, (for our local admin). To do that we use and identity source sequence. Administration > Identity Management > Identity Source Sequence > Add.
Give the sequence a name and add your AD and Internal Users.
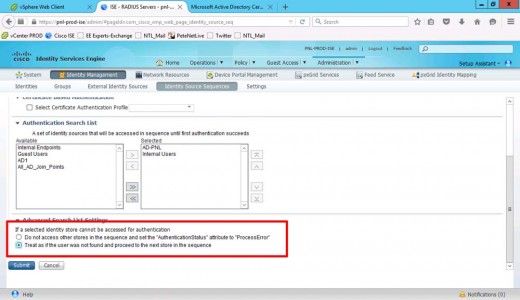
MAKE SURE you select ‘Treat as if the user was not found and proceed to the next store in the sequence’ > Submit.
Add Cisco ASA to Cisco ISE as a RADIUS Device.
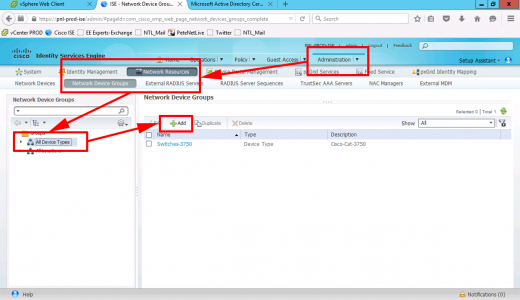
Administration > Network Resources > Network Device Groups > All Device Types > Add.
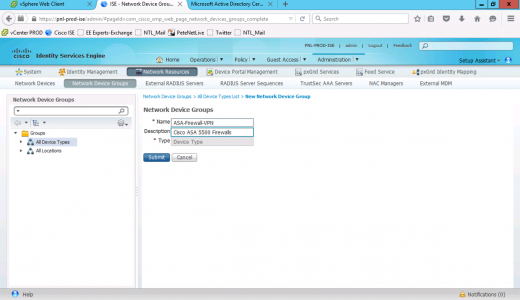
Add a device GROUP for your ASA(s) > Submit.
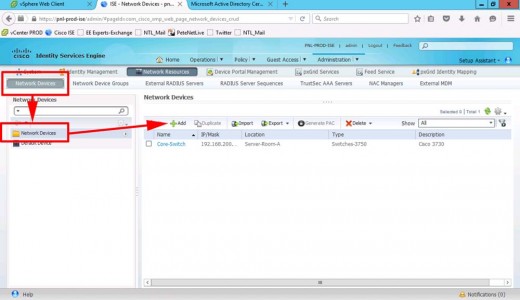
Administration > Network Resources > Network Devices > Add.
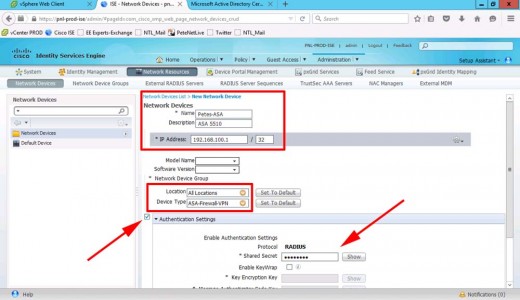
Add in the ASA > Provide its IP address, and add it to the group you created above > Set a RADIUS Shared Secret > Submit.
The shared secret must be the same on the ASA in the AAA config, like so;
Petes-ASA(config)# aaa-server Cisco-ISE protocol radius Petes-ASA(config-aaa-server-group)# aaa-server Cisco-ISE host 192.168.100.11 Petes-ASA(config-aaa-server-host)# key 123456 Petes-ASA(config-aaa-server-host)# radius-common-pw 123456 Petes-ASA(config-aaa-server-host)# exit Petes-ASA(config)#
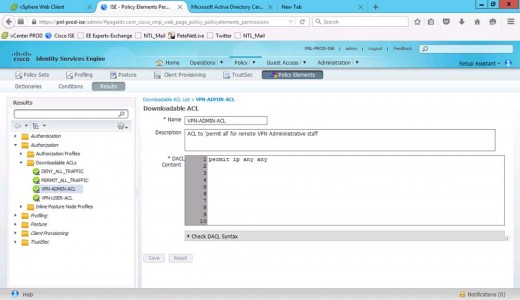
Cisco ISE Create Downloadable Access Control Lists DACL
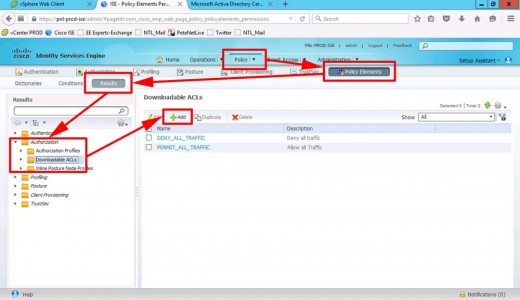
Policy > Policy Elements > Results > Authorisation > Downloadable ACL’s > Add.
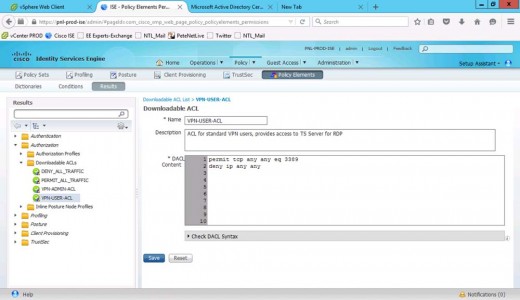
Create an ACL for our VPN-USER group, that will only allow RDP (TCP 3389) > Submit.
Repeat the process to create an ACL that allows everything, (for our VPN-ADMINS) > Submit.
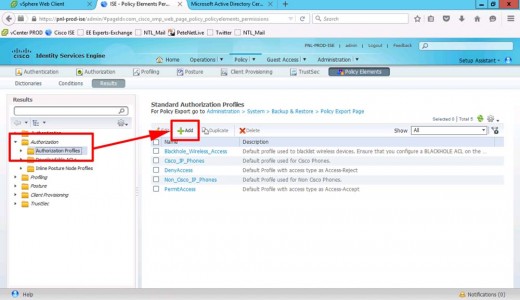
Cisco ISE Create Authorisation Profiles
Policy > Policy Elements > Results > Authorisation > Authorisation Profiles > Add.
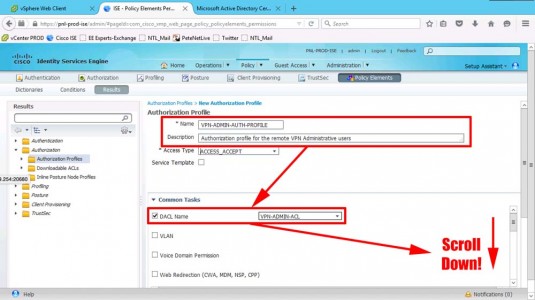
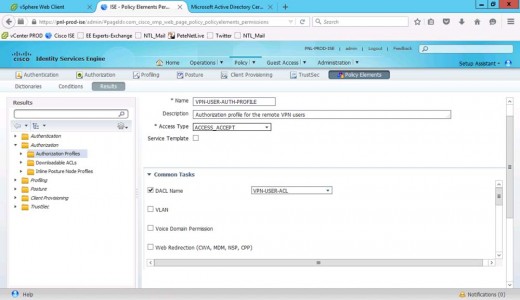
Create a profile for VPN-ADMINS > Set the correct DACL.
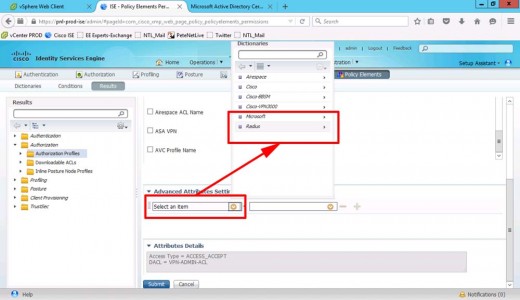
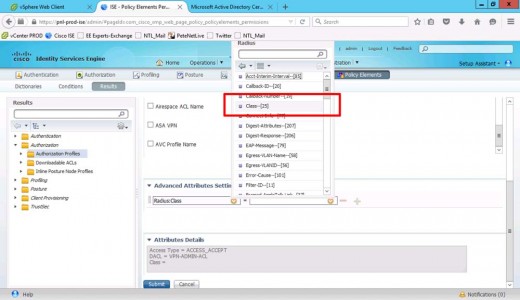
Set the advanced attributes > Change to RADIUS.
Class-25
Set the OU to equal the group-policy that you want the ASA to apply > Submit.
Create another profile for your VPN-USERS > Set the correct ACL.
RADIUS > Class-25 > OU set to the group-policy on your ASA for the normal users > Submit.
Cisco ISE Enable Policy Sets
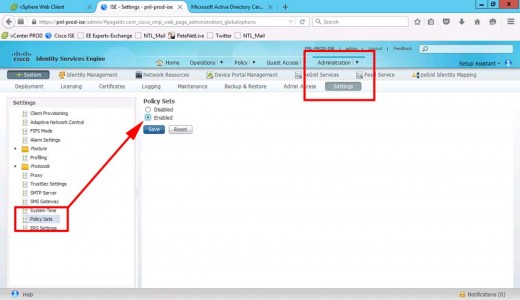
Note: only available on newer versions of ISE: Administration > System > Settings > Policy Sets > Enabled > Submit.
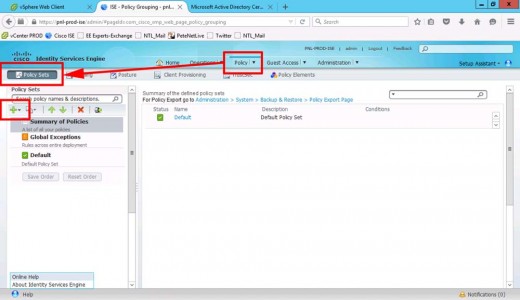
Policy > Policy Sets > Add.
Continue to PART TWO
Related Articles, References, Credits, or External Links
AnyConnect Group Authentication With Cisco ISE and Downloadable ACLs (Part 2)
Cisco ASA 5500 AnyConnect Setup From Command Line