KB ID 0001128
Problem
Now you may be thinking, “If you have your own CA/PKI solution why would you need to create a Wildcard Certificate”? If you can generate as many certificates as you want whats the point? Well today I need to setup ADFS, WAG (Web Application Gateway), and Remote Desktop Services Gateway Server. To make the whole thing wok on my test bench would be a lot less hassle if I could just use one certificate for everything!
Solution
Process carried out on Windows Server 2012 R2
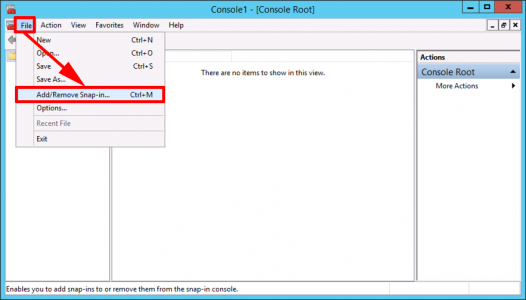
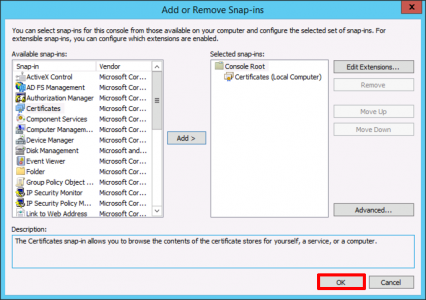
Windows Key +R > MMC > {Enter} > File > Add/Remove Snap-in.
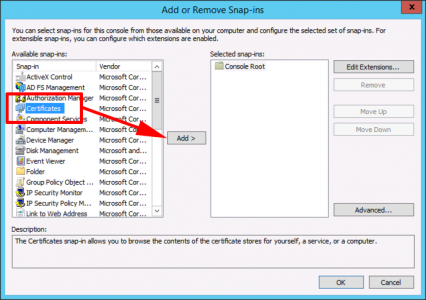
Certificates > Add.
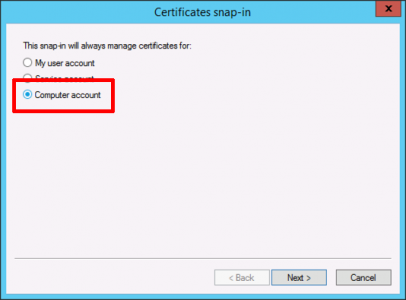
Computer account > Next.
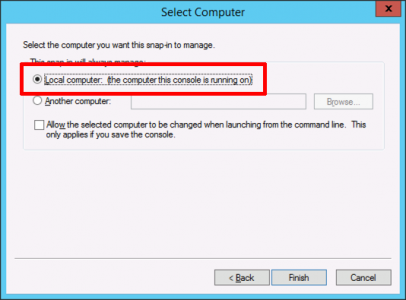
Local Computer > Finish.
OK.
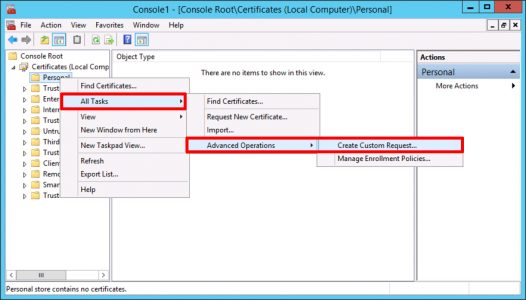
Certificates > Personal > Right Click > All Tasks > Advanced Operations > Create Custom Request.
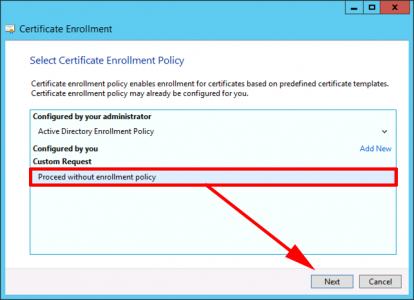
Proceed without enrolment policy > Next.
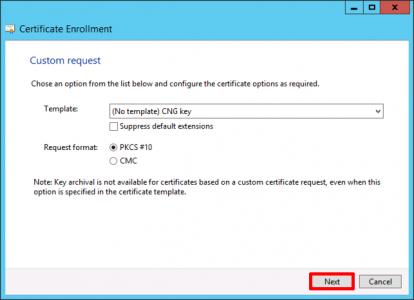
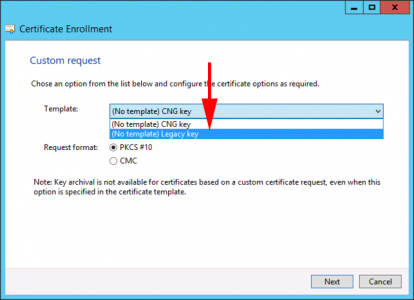
In nearly every case you can accept the default of ‘(No template) CNG Key’ However some applications (Particularly Active Directory Federation Services), need to user an older set of Cryptographic Service Providers (CSP’s). If that is the case change the option to ‘(No Template) Legacy Key’. > Next.
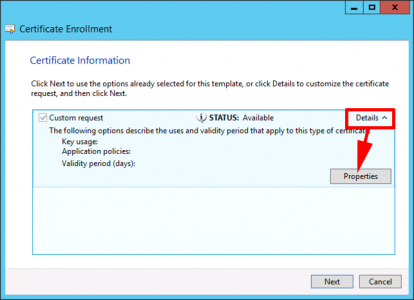
Details > Properties.
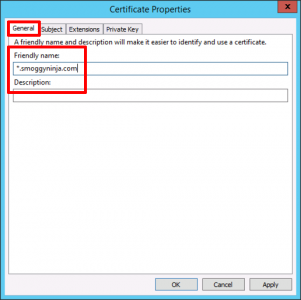
General Tab: Friendly Name > *.{your domain}.
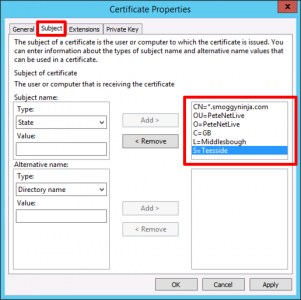
Subject Tab: Ensure the Common Name (CN) is set to *.{your domain} > Enter the rest of your details as shown.
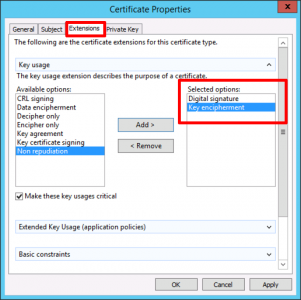
Extensions Tab: Add in Digital Signature and Key Encipherment.
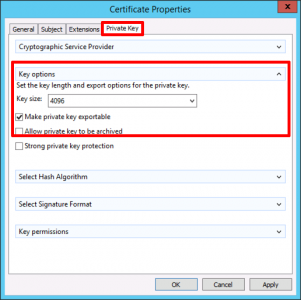
Private Key: Key Size=4098 > Make private key exportable > Apply > OK.
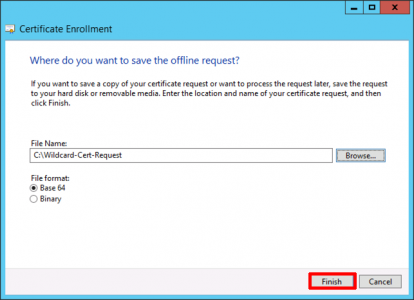
Save the certificate request > Finish >Leave the Certificate console open, (you will need it later).
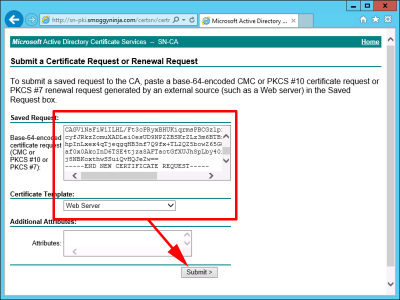
Locate the certificate request you just saved > Open it with Notepad > Select ALL the text and copy it to the clipboard.
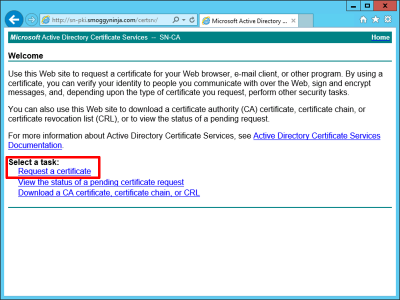
Open the web enrolment portal of your certificate services server (https://server.domain.com/certsrv) > Request a certificate.
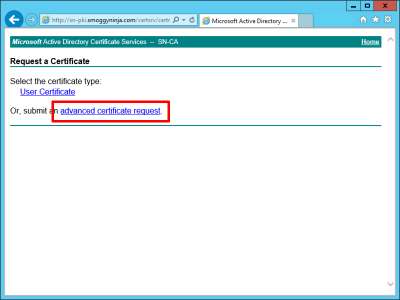
Advanced Certificate Request.
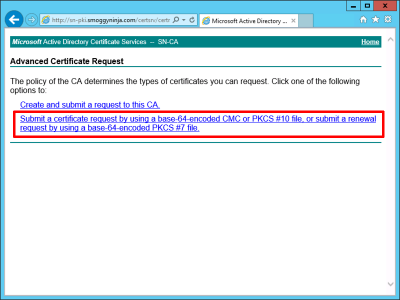
Submit a certificate request by using a base-64-encoded CMC or PKCS #10 file, or submit a renewal request by using a base-64-encoded PKCS #7 file.
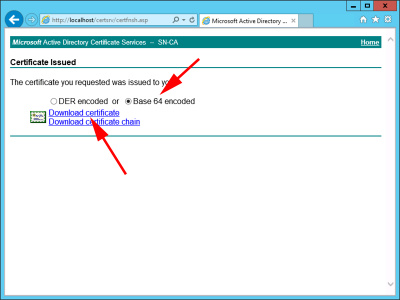
Paste in the Text > Certificate Template = Web Server > Submit.
Base 64 encoded > Download certificate.
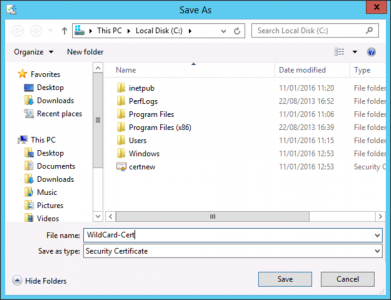
Save the certificate, and change its name from certnew > Save.
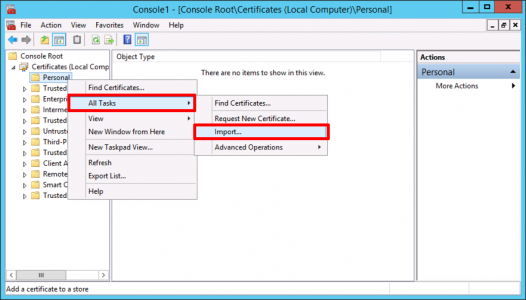
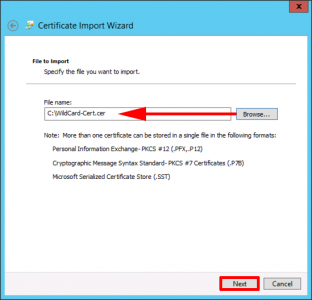
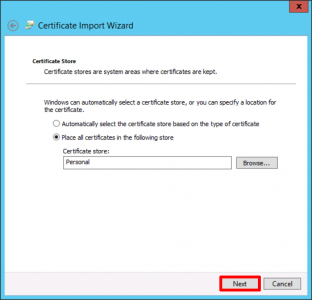
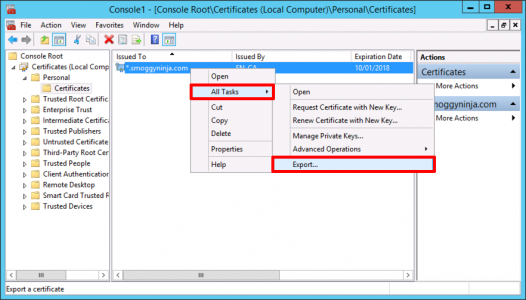
Back in the certificate console > Right Click ‘Persona’l > All Tasks > Import.
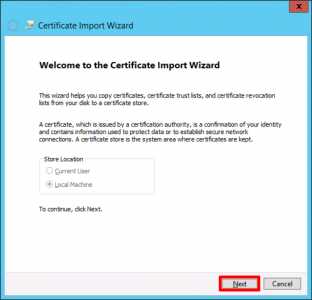
Next.
Navigate to the certificate you have just saved.
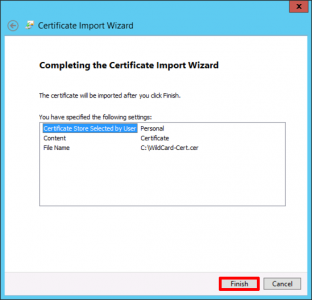
Next.
Finish.
Hopefully.
Now this may seem a little odd, but having just imported the certificate, to get it in PFX format you need to export it again. Right click the cert > All Tasks > Export.
Next
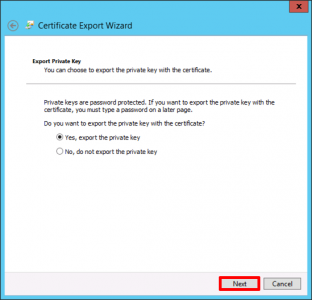
Yes, export the private key > Next.
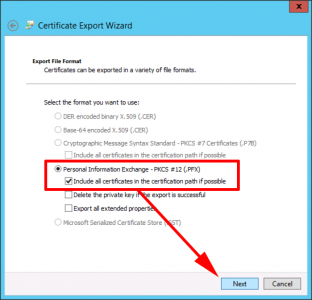
Personal Information Exchange > Next.
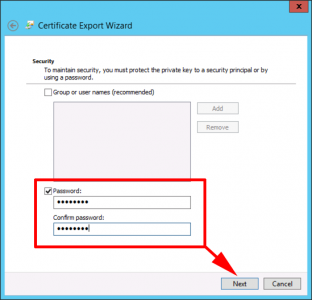
Enter and re-type a password (You will need this to import the certificate so remember it) > Next.
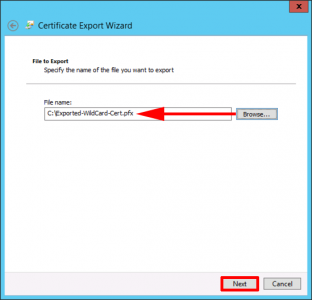
Save it somewhere you can find it > Next.
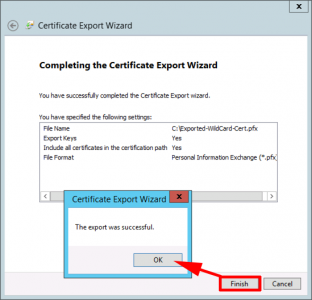
Finish > OK.
Related Articles, References, Credits, or External Links
NA

06/11/2017
Thank you for this!
29/07/2019
I have followed your instructions several times making sure I am not missing any steps.
All works beautifully until I reach your step :”
Paste in the Text > Certificate Template = Web Server > Submit.”
In this step I don’t have a Certificate Template field.
Any suggestions, please?
Thanks.
30/07/2019
The field is not there at all? (try a different browser, from a different machine.) Or Web Server template is missing? https://www.petenetlive.com/KB/Article/0001552
29/04/2018
Hi,
I followed your guide to create a wildcard on my internal CA for use with some of my web servers, but am having an issue;
When I add the exported PFX to my remote desktop deployment, Chrome gives me an untrusted error saying “ERR_CERT_COMMON_NAME_INVALID”
When I look at the certificate info from Chrome, it says issued to *.domain.com, and I am accessing from rd.domain.com
Any thoughts on why it is giving me a common name mismatch error when I can see it does match?
Cheers
Eds
01/05/2018
Yes this is a common ‘bug’ in Chrome. Google the error.
P
29/01/2021
Add the SAN for DNS with the same wildcard info (eg. *.domain.com)
27/04/2022
Hi,
Thanks for the post.
What exactly do you mean Jeremy? should I just add the *.domain.local to my DNS server? since it has a lot of records and I’ve more than 1 web server it doesn’t screw up all my A records?
30/04/2019
Great article, please ad how to extend certificate to 5 years..
01/05/2019
Set the certificate lifetime on the certificate template.
22/08/2019
Worked well up to the point of getting it signed. Doesn’t seem to like the asterick in the subject name
Microsoft Active Directory Certificate Services — ServerName Home
Certificate Request Denied
Your certificate request was denied.
Your Request Id is 0. The disposition message is “Error Parsing Request The request subject name is invalid or too long. 0x80094001 (-2146877439)”.
Contact your administrator for further information.
————–
Windows Server 2008R2 certificate services may be the issue but not sure. Have you ran across this?
27/08/2019
I’ve not, check all the tributes on your cert request, in case you have entered something incorrect (i.e. more than two letters in the country code.) Also you see that error if the CN matches the CA name?
28/10/2019
followed your steps. IE and chrome and edge all say “DLG_FLAGS_SEC_CERT_CN_INVALID”.
which is the exact same result i got earlier from simply requesting a “Common Name=*.domain.com” certificate of the “web server” template with the gui MMC console.
30/10/2019
Do you trust the RootCA and all the intermediate CAs (if there are any?)