DDoS KB ID 0001926
DDoS Problem
If you’ve ever had a website grind to a halt or watched a critical service vanish mid-operation, chances are you’ve felt the sting of a Denial of Service (DoS) attack. In today’s hyper-connected world, Distributed Denial of Service (DDoS) attacks are not just a nuisance, they’re a strategic weapon used to cripple infrastructure, extort businesses, and disrupt entire economies.
Having spent three decades deploying infrastructure from SME setups to Tier IV data centres, I’ve seen DDoS evolve from script-kiddie mischief, to nation-state level disruption. This article breaks down the mechanics, types, symptoms, and mitigation strategies of DDoS attacks in plain English.
What Is a DDoS Attack?
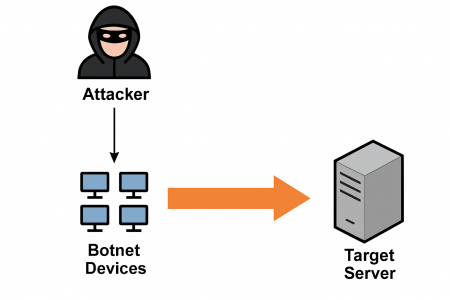
A Distributed Denial of Service (DDoS) attack is a coordinated attempt to make a system, service, or network resource unavailable, by overwhelming it with traffic from multiple sources.
Unlike a simple DoS attack (which might come from a single IP), DDoS attacks leverage botnets, which are networks of compromised devices (PCs, IoT gadgets, even smart fridges) to flood the target.
Why DDoS Matters
-
Downtime: E-commerce sites lose thousands per minute.
-
Reputation: Customers don’t forgive outages easily.
-
Security: DDoS is often a smokescreen, for deeper breaches, and to maks other attack vectors.
Attack Vectors
DDoS attacks come many flavours. Here are the main ones:
-
Volumetric Attacks: UDP floods, ICMP floods. Aim: saturate bandwidth.
-
Protocol Attacks: SYN floods, fragmented packets. Aim: exhaust server resources.
-
Application-Layer Attacks: HTTP GET/POST floods. Aim: crash web apps.
-
Amplification Attacks: DNS/NTP reflection. Small request → massive response.
-
Multi-Vector Attacks: Combine the above for maximum chaos.
| Type | Target Layer | Example | Impact |
|---|---|---|---|
| Volumetric | Network | UDP Flood | Bandwidth exhaustion |
| Protocol | Transport | SYN Flood | Server resource drain |
| Application Layer | Application | HTTP GET Flood | Web server crash |
| Amplification | Mixed | DNS Reflection | Traffic multiplication |
Signs You’re Under DDoS Attack
-
Sluggish network performance.
-
Website(s) intermittently crashing.
-
Sudden traffic spikes from odd geo locations.
-
Surge in spam, or malformed requests.
Real-World Examples
GitHub (2018): In February 2018, GitHub was hit by what was then the largest recorded DDoS attack, peaking at 1.35 Tbps. The attackers exploited misconfigured memcached servers, a caching system designed for speed but vulnerable when exposed to the public internet. By spoofing GitHub’s IP address and sending small queries to these servers, they triggered responses amplified up to 50 times the original size. Despite the sheer volume, GitHub’s response was swift. Within minutes, they rerouted traffic through Akamai’s scrubbing centres, which filtered out malicious packets. The site was down for only five minutes, showcasing the importance of automated mitigation and upstream partnerships.
Dyn (2016): On 21 October 2016, DNS provider Dyn was targeted by a massive DDoS attack using the Mirai botnet, which had infected thousands of IoT devices—baby monitors, IP cameras, routers, using default credentials. The attack overwhelmed Dyn’s DNS infrastructure, disrupting access to major platforms including Twitter, Netflix, Reddit, PayPal, and Spotify.The attack came in three waves, affecting users across Europe and North America. It exposed the fragility of DNS as a single point of failure and highlighted the dangers of insecure IoT devices. The Mirai botnet’s source code was later released publicly, leading to a surge in copycat attacks.
Cloudflare (2023): In 2023, Cloudflare faced a series of hyper-volumetric DDoS attacks, including one that peaked at 201 million HTTP requests per second—nearly 8× larger than their previous record. These attacks exploited a vulnerability in the HTTP/2 protocol, known as Rapid Reset, allowing attackers to overwhelm servers with minimal resources. Cloudflare’s automated defences mitigated over 8.7 million network-layer attacks that year, and their response to the HTTP/2 exploit involved industry-wide collaboration and rapid patching. This incident underscored the evolving sophistication of DDoS threats and the need for proactive protocol-level security.
DDoS Mitigation Techniques
-
Rate Limiting: Throttle excessive requests.
-
WAFs (Web Application Firewalls): Block malicious HTTP traffic.
-
Geo/IP Blocking: Filter traffic by origin.
-
Anycast Routing: Distribute load globally.
-
Scrubbing Centres: Clean traffic before it hits you, or redirect affected traffic for ‘scrubbing” i.e. F5 Silverline services.
-
CDNs: Offload content delivery.
-
Cloud DDoS Protection: Services like Cloudflare, Akamai, AWS Shield.
Best Practices
-
Patch systems regularly.
-
Use redundant infrastructure.
-
Monitor traffic anomalies.
-
Deploy layered protection.
-
Have a response plan—before you need it.
Legal & Ethical Aspects of DDoS
Yes, DDoS is illegal. In the UK, it’s covered under the Computer Misuse Act 1990.
Future Trends
-
AI-Driven Attacks: Smarter, adaptive botnets.
-
5G & IoT: More devices = bigger botnets.
-
Ransom DDoS: Pay up or stay offline.
-
Attack-as-a-Service: Cheap, scalable, anonymous.
DDoS isn’t going away. If anything, it’s getting nastier. Whether you’re running a small business or managing enterprise infrastructure, resilience starts with awareness. Review your defences, test your response plans, and don’t wait for the outage to learn the lesson.
Really good site, showing live DDoS attacks (https://www.digitalattackmap.com/)
Related Articles, References, Credits, or External Links
Understanding the Evolving Threat of DDoS