Windows LAPS KB ID 0001822
Problem
We used to have Microsoft LAPS, now we have Windows LAPS! LAPS is a solution that lets’ you store admin passwords ‘elsewhere‘ be that in your local Active Directory or Azure Active Directory*. Unlike previously, where you had to deploy/install client software, it’s now built into Windows from the following versions.
- Windows 11 22H2 – April 11 2023 Update
- Windows 11 21H2 – April 11 2023 Update
- Windows 10 – April 11 2023 Update
- Windows Server 2022 – April 11 2023 Update
- Windows Server 2019 – April 11 2023 Update
*Note: Is in the pipeline at time of writing traditional (on-premises) AD only is supported.
The premise is that instead of having a single (easily compromised) local admin password (or DSRM password on a DC) for your assets you can have a different password (that can be controlled with a complexity policy) for each client/server and that password is stored securely in Active Directory, (as an attribute of the computer object).
| Backup to Azure AD | Backup to Local (On-Premises) AD | |
| Azure AD Joined | Yes | No |
| Local (On-Premises) Joined | No | Yes |
| Hybrid Joined | Yes (if not backed up to on-premises AD) | Yes (if not backed up to Azure AD) |
| Workplace Joined | No | No |
Solution: Windows LAPS
Firstly, FULLY update all the domain controllers in the domain.
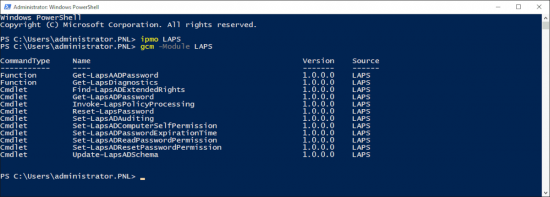
On a DC you can load the LAPS module and look at the commandlets.
ipmo LAPS gcm -Module
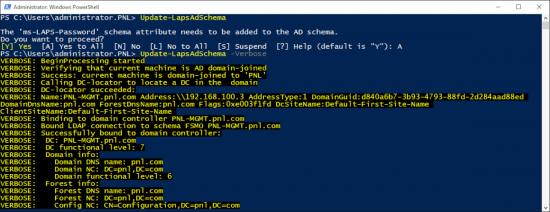
From these commandlets the first one we need to use is Update-LapsAdSchema, this will extend the active directory schema and add the LAPS attributes to the computer objects.
Update-LapsAdSchema
It will ask you con conform you can watch each step by pressing Y – or if you’re lazy (like me) simply press A {Enter}.
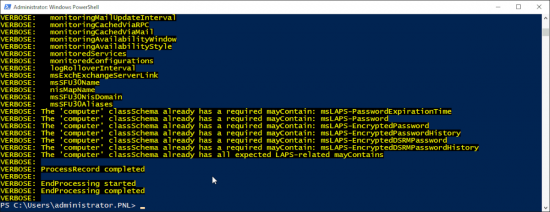
You can’t really see what it is doing, but if you’re interested, you can run the same command again with a -verbose switch on it to see exactly what going on.
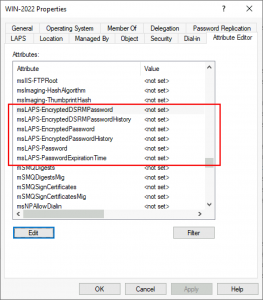
OK, but what has that done? Well as I said above, the computer objects have been extended and they now have ALL have the following attributes.
Note: Yes, there’s now a LAPS tab also, but there won’t be anything in there yet.
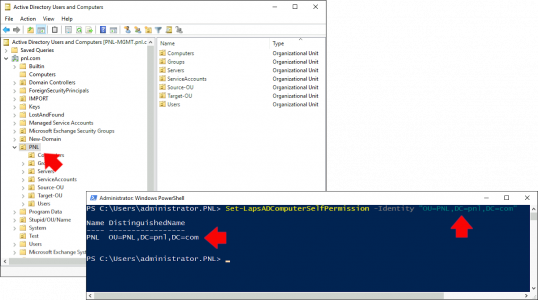
The next commandlet we need, Set-LapsADComputerSelfPermission, will grant the computer object the rights to manage its own LAPS password, You can set this on the root of the domain if you wish. Here I have all my computer objects in an OU called PNL so I’m applying that right at the TOP LEVEL OU, and it will apply to all children OUs.
Set-LapsADComputerSelfPermission -Identity "OU=PNL,DC=pnl,DC=com"Setting Windows LAPS Settings via Group Policy
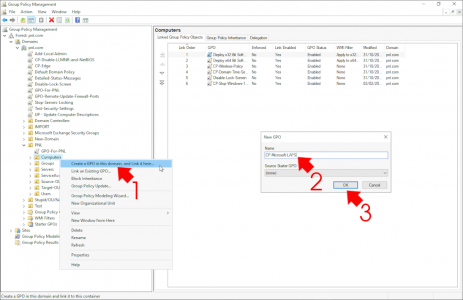
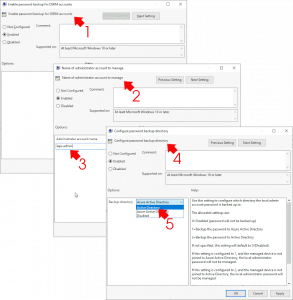
Create a new GPO (or edit an existing one) that links to the OU where your COMPUTER objects live. (remember if managing DSRM passwords you will also need to link the policy to the Domain Controllers OU also).
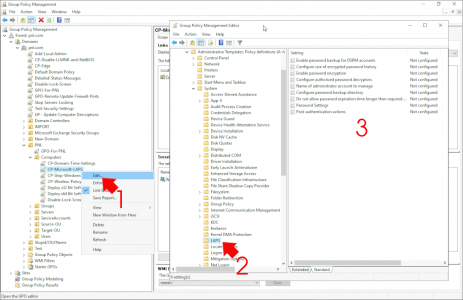
Edit the Policy and navigate to;
Computer configuration > Policies > Administrative Templates > System > LAPS
Note: If you have a LAPS folder directly under Administrative Templates, that’s for the older Microsoft LAPS settings!
Policies to edit;
- Enable Password Backup for DSRM accounts : Enable
- Name of administrator account to manage : Enable > laps.admin
- Configure Password Backup Directory : Enable > Active Directory
Note: If you already have a local admin account, built into you master computer image for example, you can use that account instead.
Further policy to edit;
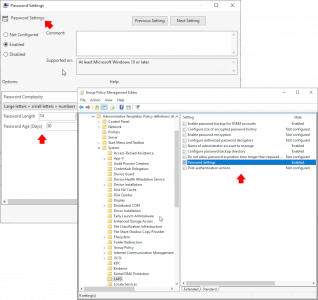
- Password settings : Enable > (I accept the defaults)
The screen shot below shows how the policy should look before you exit the group policy editor.
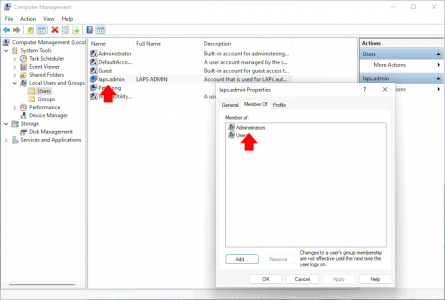
Windows LAPS Local Admin
Here I’ve manually created the local user, you can either roll this out by script, GPO, or building the account into the your default image for OS deployment.
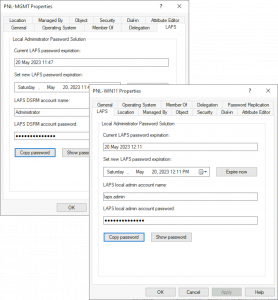
Retrieving Windows LAPS Passwords
Below you can see we can retrieve both a local Windows LAPS password for a client, or a DSRM password for a domain controller.
Simply click Show password and Copy password, and the password will be on the clipboard (as shown).
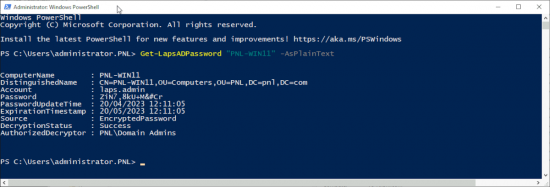
To get the password via PowerShell use the Get-LapsADPassword commandlet.
Get-LapsADPassword "PNL-Win11" -AsPlainTextTroubleshooting Windows LAPS
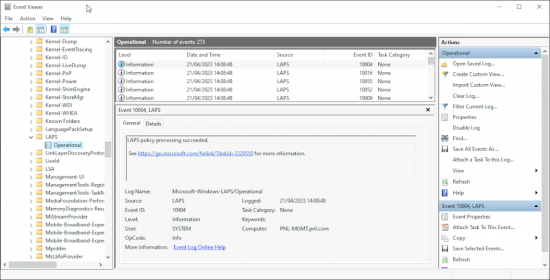
The update also allows you to view LAPS event logs in the Event Viewer, like so.
Interoperability Microsoft LAPS and Window LAPS
If you have the older Microsoft LAPS running (i.e. Your end clients have the LAPS client software being deployed to them, then when the Apr 23 LAPS update is deployed to them and used, BOTH Systems may stop working. To fix this you need to disable Legacy LAPS by setting the following registry key on your clients.
HKLM > Software > Microsoft > Windows > CurrentVersion > LAPS > Config
Create a new 32 bit DWORD value called BackupDirectory and set its value to 0 (zero).
Once the Azure AD element is fully released and supported, I’ll loop back and include that also.
Related Articles, References, Credits, or External Links
Microsoft LAPS – Deployment and Configuration
MS: What is Windows LAPS Overview