Disable LLMNR and NetBIOS KB ID 0001816
Problem
LLMNR is a protocol that’s used both in IPv4 and IPv6 networks to provide name resolution (in the absense of DNS), the problem with it is that it is wide open to exploitation and can be used to perform a MITM attack on your network. NetBIOS is much older and asscociated with IPv4 networks only. Really old Microsoft OSs used to rely on it heavily, but these days its pretty much redundant*
*Note: Unless you have Windows Server NT/2000/2003 or Windows 2000/XP floating around, or some older flavours of Linux that need to talk to your Microsoft server estate, may still rely on NetBIOS.
NetBIOS itself is not actually a protocol (depending on who you ask, let’s not have an argument) It’s actually much older than the old Windows systems that are synonymous with it’s use, the actual protocol that’s used is actually NetBEUI.
Solution: Disable LLMNR and NetBIOS
Step 1: Disable LLMNR
Disabling LLMNR is as easy as peas, theres a GPO setting for it, NetBIOS is more of a challenge because its enabled/disable against a network connection, each network conection on each machine has a differnet identifyer in the registry, so we can even use a GPP and set the registry key. The only way to do this practically is with a script thats called from Group Policy that disables NetBIOS on ALL network cards.
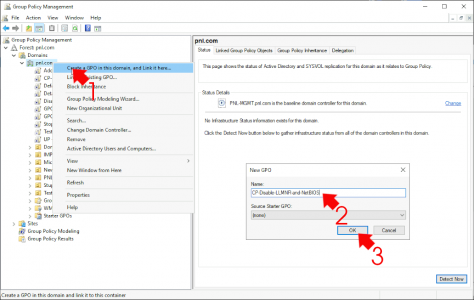
Create (or edit an existing) Group Policy object that is linked to the OU that you computers are in.
Navigate to;
Computer Configuration > Policies > Administrative Templates > Network > DNS Client > Turn off Multicast name resolution
Enable the Policy > Apply > OK.
Step 2: Disabling NetBIOS (For Static IP Clients)
Remember this protocol is pretty much dead not, but it is worth just firing up WireShark and having a sniff round the network to make sure nothing is still using it to be on the safe side.
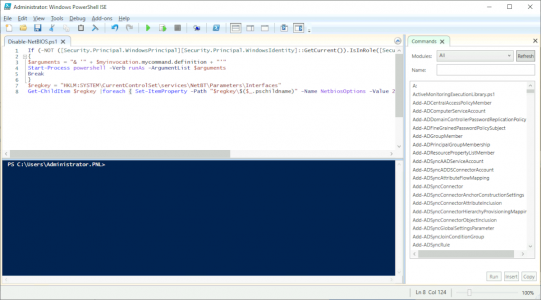
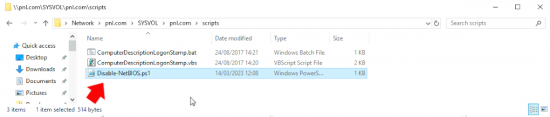
Copt the following Powershell Script
If (-NOT ([Security.Principal.WindowsPrincipal][Security.Principal.WindowsIdentity]::GetCurrent()).IsInRole([Security.Principal.WindowsBuiltInRole] "Administrator"))
{
$arguments = "& '" + $myinvocation.mycommand.definition + "'"
Start-Process powershell -Verb runAs -ArgumentList $arguments
Break
}
$regkey = "HKLM:SYSTEM\CurrentControlSet\services\NetBT\Parameters\Interfaces"
Get-ChildItem $regkey |foreach { Set-ItemProperty -Path "$regkey\$($_.pschildname)" -Name NetbiosOptions -Value 2 -Verbose}
Note: Before you all start emailing in, yes it does a credentials check to make sure you have the right to perform the change – and yes I am aware startup script run under the system account (so theres no need to do this) but people can use this script universally, If I leave that in.
Save the script somewhere that’s shared, or simply \\{Domian-Name}\Sysvol\{Domain-Name}\Scripts
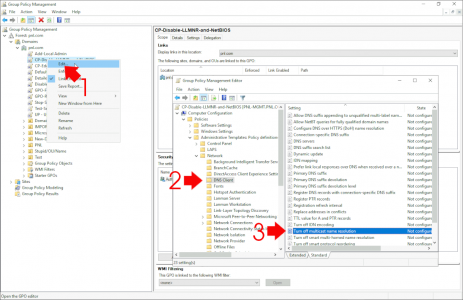
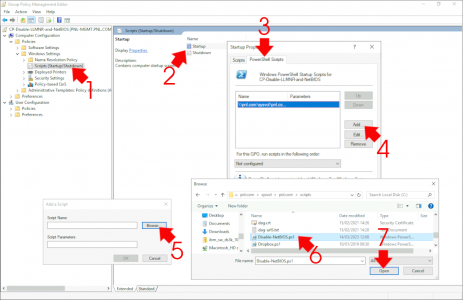
Then back in you group policy managment console, navigate to.
Computer Configuration > Policies > Windows Settings > Scripts (Startup/Shutdown) > Startup
Add a New Script > PowerShell Scripts > Add > Browse > MAKE SURE you browse to the network location of the script > Open > OK > Apply > OK.
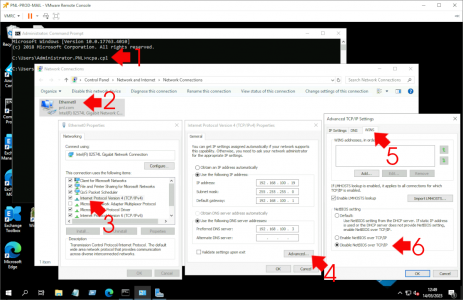
To Test: Go to a client this policy is applied to, and look at its network card properties, it should show “Disable NetBIOS over TCP/IP“.
Step 3: Disabling NetBIOS (For DHCP Clients)
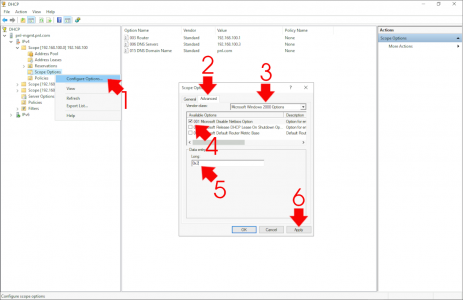
If your end clients get their IP addresses form a DHCP server, you can disable this (PER SCOPE) on your DHCP server. Locate the scope you want to work on > Scope Options > Configure Options > Advanced >Microsoft Windows 2000 options > Tick Option 001 > Change the entry to 0x2 > Apply > OK.
Related Articles, References, Credits, or External Links
NA


11/07/2024
Why not use the following setting?
Computer Configuration > Administrative Templates > Network > DNS Client > Configure NetBIOS settings
11/07/2024
Hi Simon – Has that been depreciated? Cant see that on my Test Network? That option is not there for me.
11/07/2024
That’s a new setting introduced with Windows 11:
https://techcommunity.microsoft.com/t5/core-infrastructure-and-security/windows-10-or-windows-11-gpo-admx-an-update/ba-p/3703548
Did you update your ADMX or only checked locally on the device?
25/03/2025
Thank you for posting this link, basically everything else I found on turning off NETBIOS was wrong and this admx update provided the option to do it in GPO in seconds. You are a rockstar.
05/03/2025
For disabling LLMNR, Turn off smart multi-homed name resolution is the name of the setting in GPO in Server 2019.