FortiClient Azure KB ID 0001797
Problem
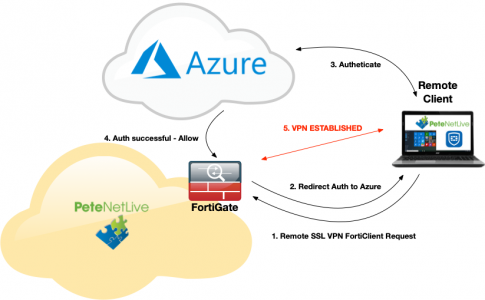
More and more people are using Azure as their primary identity provider, thanks in no small part to the massive success of Office/Windows 365. So if you want to provide a FortiGate/FortiClient SSL remote access VPN solution then securing it via Azure makes a lot of sense.
Multi Factor Authentication: If you have MFA on your Azure accounts then that’s a big box ticked for your accreditations and digital liability insurance also. This article does not cover enabling MFA in Azure, we are assuming you already have that enabled. I’ve covered that in other articles anyway, (use the search box above!)
Essentially your firewall will redirect authentication (via SAML) to Azure when you attempt to connect either via the web or tunnelled with the FortiClient.
Note: You can of course Use Azure MFA With Microsoft NPS (RADIUS) Server but this would require an additional server.
FortiClient Azure Authentication
FortiClient Azure Prerequisites
You will need an Azure subscription (a trial one is fine), obviously a FortiGate firewall, and a publicly signed certificate for the firewall (see below).
Note: Stop asking if you can use self signed certs – this one cost me six dollars! It needs to be publicly signed so Azure trusts it!
Add and Configure the FortiGate SSL VPN Application
From within your Azure tenancy, locate Enterprise applications and choose to add a new one.
Do a search for Forti and you should see the FortiGate SSL VPN application, select it.
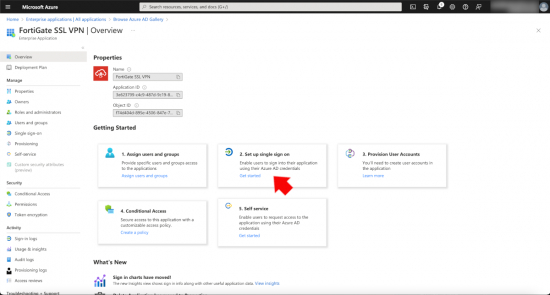
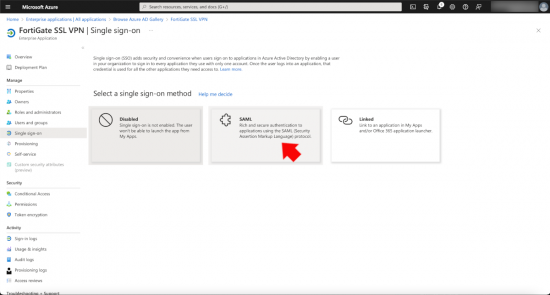
In the setup single sign on section, click ‘Get Started’.
Select SAML.
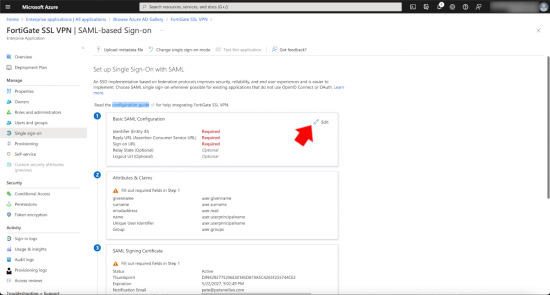
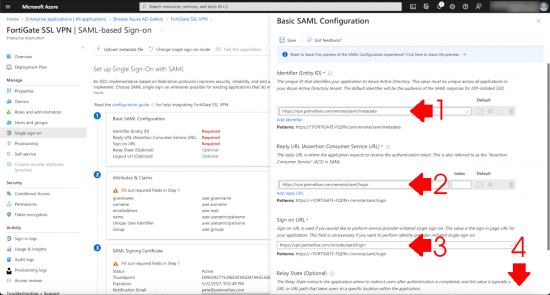
The ‘Vast Majority’ of the work that needs to be done will be done in here. In Section 1 (Basic SAML Configuration) you will enter FOUR URLs (these URLs will reside on your FortiGate).
Change the values in red to match your own publicly resolvable FQDN, (which will match the CN on your certificate).
Identifier (Entity-ID)
https://vpn.petenetlive.com/remote/saml/metadata
Reply URL (Assertion Consumer Service URL)
https://vpn.petenetlive.com/remote/saml/login
Sign on URL (Yes it’s the same as the one above!)
https://vpn.petenetlive.com/remote/saml/login
Then scroll down.
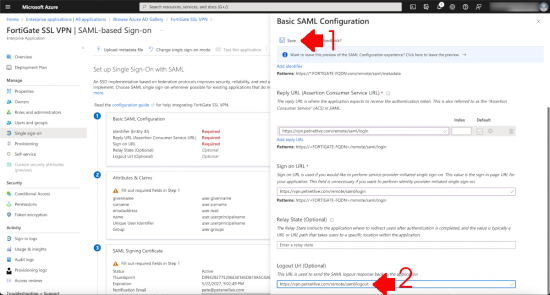
Log out URL
https://vpn.petenetlive.com/remote/saml/logout
Then SAVE.
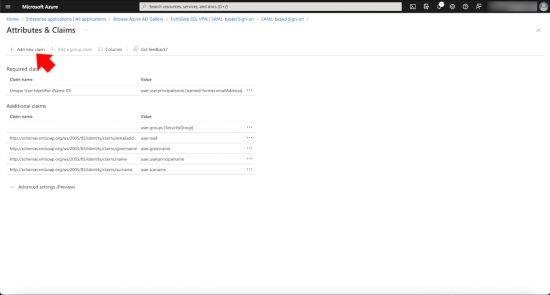
Section 2: Attributes and Claims, click edit.
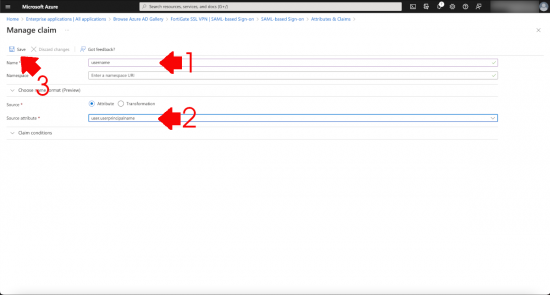
Add a new claim.
Name = username, Source attribute = user.userprinciplename > Save.
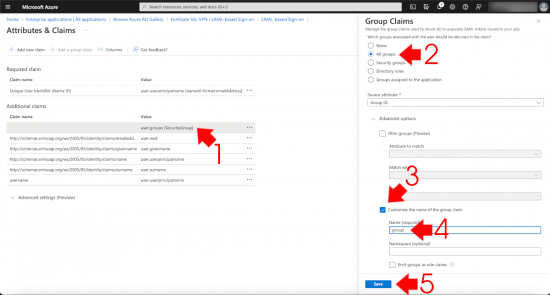
Select the existing user.groups value > Change it to ‘All Groups’ > Tick ‘Customise the same of the group claim’ > Set the name to group > Save.
Note: It can take little while for the main page to refresh .
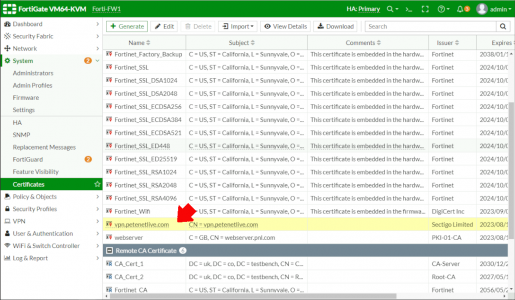
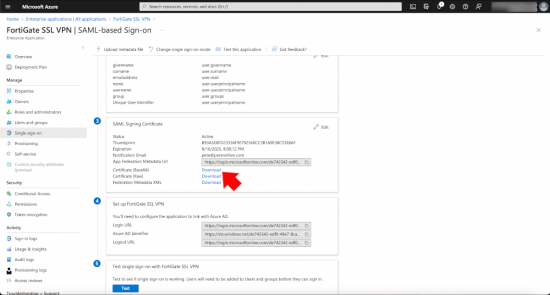
Section 3: SAML Signing Certificate. Download the Base64 version of the certificate.
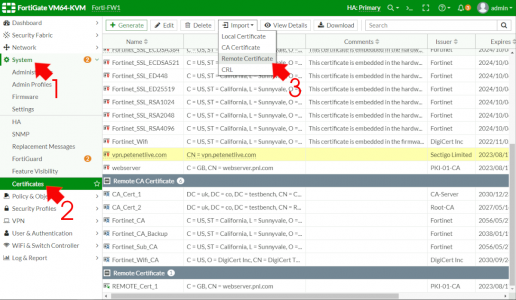
Back on your FortiGate > System > Certificates > Import > Remote Certificate.
If you can’t see certificates click here.
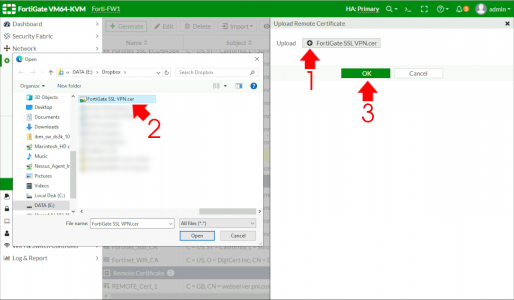
Browse to and upload the certificate you just dowloaded.
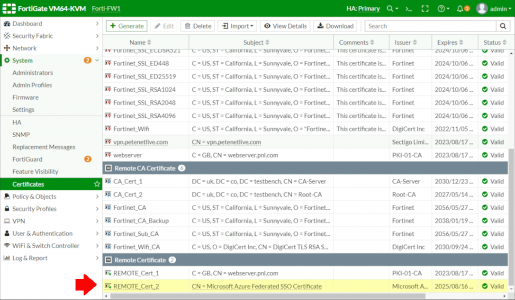
Make a note of the certificate name, in this case it’s REMOTE_Cert_2 (You will need this later).
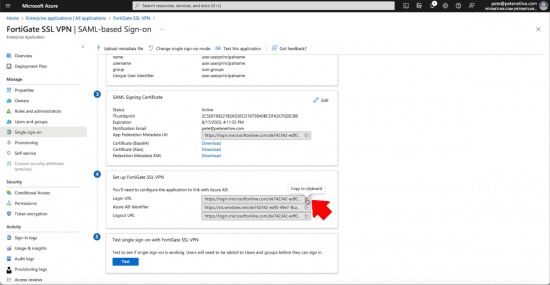
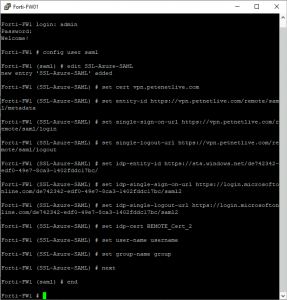
Section 4: Setup FortiGate SSL VPN. In this section there are three URLs that you need to take a copy of (they are used in the code block you will post into the FortiGate.
You now have all the elements you need to paste the following code block into your FortiGate, the following elements IN RED should be changed to match yours.
set-cert is the NAME that the FortiGate has given to its public cert, (mine’s the same as its common name, yours may be something else!)
entity-id, single-sign-on-url, and single-log-out-url are the URLs you pasted into section 1 (above).
idp-entity-id, idp-single-sign-on-url, and idp-single-log-out-url are the URLs you copied out of section 4 (above).
idp-cert is the NAME that the FortiGate has given to the cert you dowloaded from section 3 (above)
user-name and group-name are the attributes and claims you setup in section 2 (above).
config user saml edit SSL-Azure-SAML set cert vpn.petenetlive.com set entity-id https://vpn.petenetlive.com/remote/saml/metadata set single-sign-on-url https://vpn.petenetlive.com/remote/saml/login set single-logout-url https://vpn.petenetlive.com/remote/saml/logout set idp-entity-id https://sts.windows.net/de742342-edf0-49e7-8ca3-1402fddc17bc/ set idp-single-sign-on-url https://login.microsoftonline.com/de742342-edf0-49e7-8ca3-1402fddc17bc/saml2 set idp-single-logout-url https://login.microsoftonline.com/de742342-edf0-49e7-8ca3-1402fddc17bc/saml2 set idp-cert REMOTE_Cert_2 set user-name username set group-name group next end
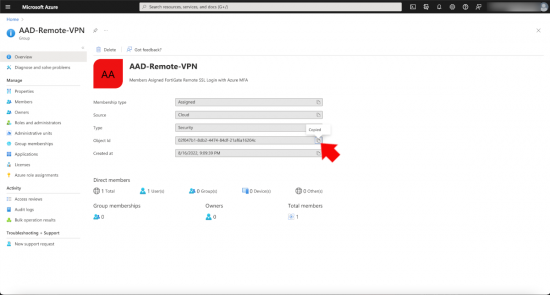
Azure Groups
You will need a group in Azure created with the users that you wish to be able to authenicate into to the remote VPN. Take a copy of its Object ID (you will need that shortly).
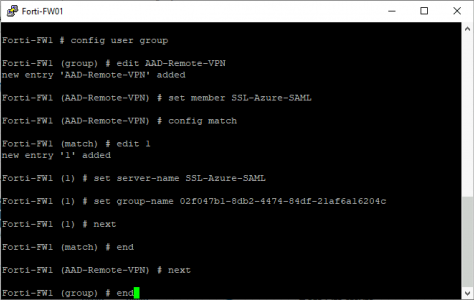
With that object ID you can create a ‘Group’ on the FortiGate with the following code block
config user group edit AAD-Remote-VPN set member SSL-Azure-SAML config match edit 1 set server-name SSL-Azure-SAML set group-name 02f047b1-8db2-4474-84df-21af6a16204c next end next end
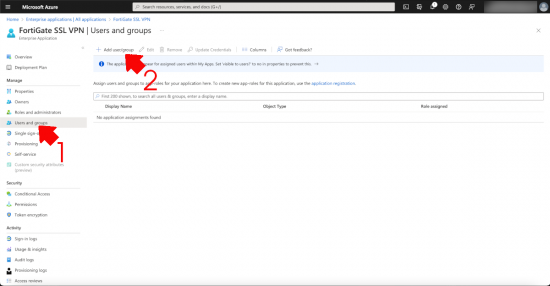
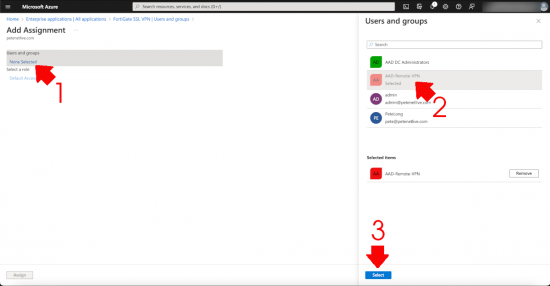
You will also need to add this group (In Azure) into the FortiGate SSL VPN application > users and groups > add user/group.
Click ‘None Selected” > Select your user group > Select.
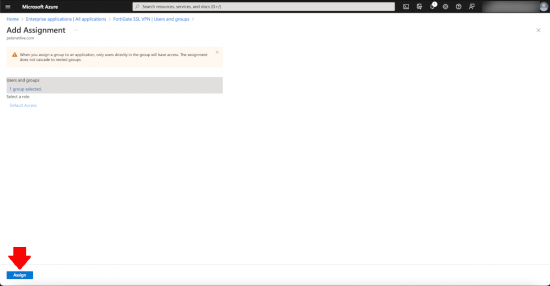
Heed the warning! No nested groups, which is a little annoying, but you can’t say they didn’t warn you > Accept.
FortiGate SSL VPN
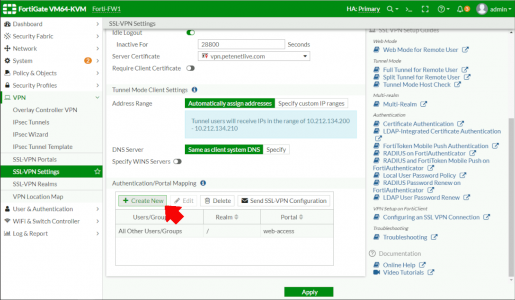
I’m going to use the basic settings to get this up and running, VPN > SSL VPN Settings > Listen on Interfaces (set to the outside facing interface (that the certificate name points to!) Server Certificate set to your publicly signed certificate > Scroll down.
Note: If you see a warning about not having configured SSL policy, dont worry we will fix that in a moment.
Create New.
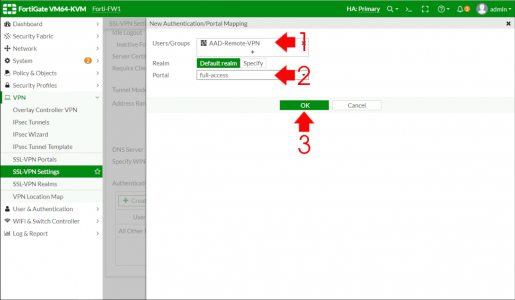
Select the AAD user group (we created with the second code block) and set the Portal, (here I’m using full access so the remote client can use the web, or full tunnel options) > OK.
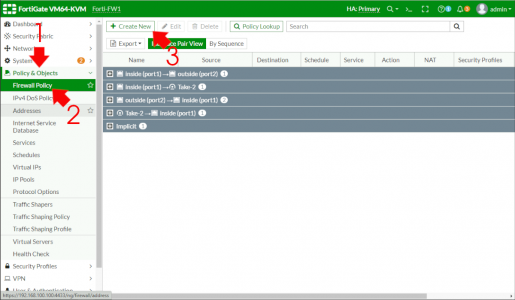
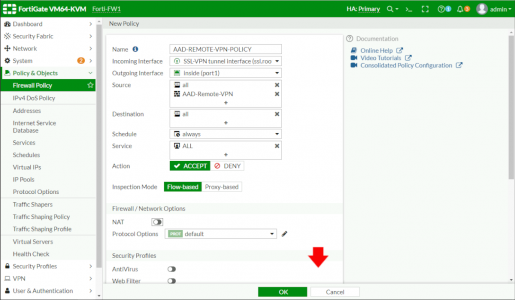
Policy & Objects > Firewall Policy > Create New.
Give the policy a sensible name > Incoming Interface will be SSL-VPN (Not outside!) > Outgoing interface is usually the inside (unless you have DMZs etc) > Source, add in All and your AAD-Group you created with the second code block above > DISABLE NAT > Scroll down.
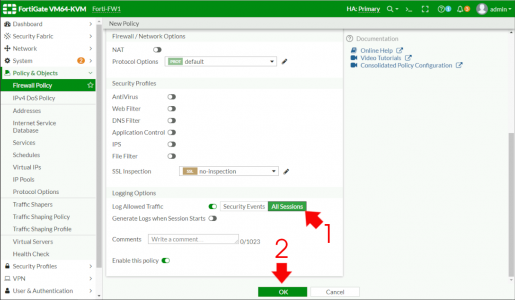
Change Logging to ‘All sessions’ (Note: once fully deployed, you can change this to security events) > OK.
Note: It may error at this point if the portal you have chosen, (in this case full-access) has split tunnelling enabled, you can either disable split tunnelling on the portal, or change All in the destination section to a particular subnet on the the LAN).
Testing Forti Web SSL With Azure
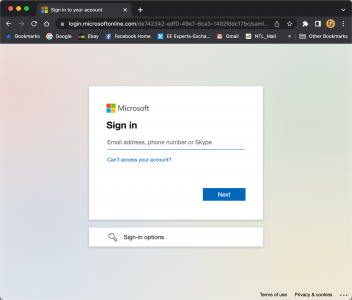
From an external client connect the web address of your FortiGate, all being well it should redirect you to Azure, (or your ADFS portal if you use ADFS).
Provision authentication is successful, you should see something like this.
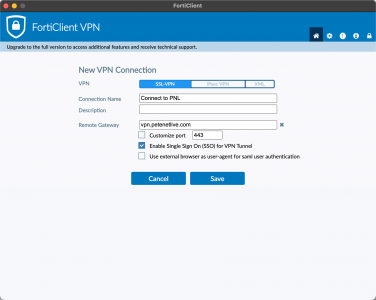
Testing FortiClient Azure SSL VPN With Azure
Install the FortiClient, (here I’m using the VPN only version). Give the connect a sensible name > Set the gateway to your public FQDN, and tick ‘Enable Single Sign On (SSO) for VPN Tunnel > Save.
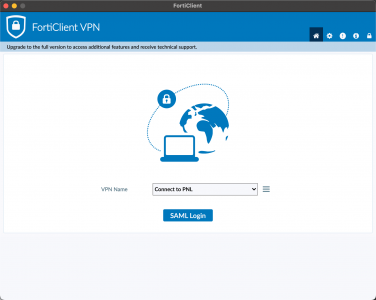
SAML Login
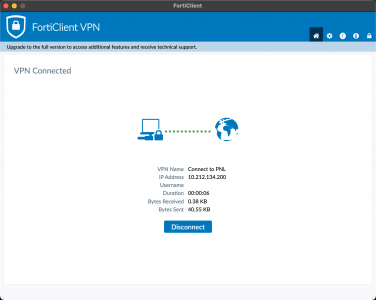
After your Microsoft authentication prompt appears, the client should connect successfully.
Related Articles, References, Credits, or External Links
Microsoft: Azure AD SSO with FortiGate
Fortinet: Configuring SAML SSO login for SSL VPN




18/08/2022
Great article as always Pete! Thanks for doing what you do.
18/08/2022
Thanks Chris!
P
18/04/2024
i have to make one addtion as below
To increase remote authentication timeout:
In the FortiGate CLI console, enter the following commands:
config system global
set remoteauthtimeout 60
31/08/2022
Nice writeup, do you know if a wildcard cert will work?
05/09/2022
Hi Brian – I’ve not personally tried it with a wildcard – but I see no reason at all why it would not work, I’ve had wildcards on my Hybrid Exchange servers Into O365, and they were fine!!
05/12/2022
Great article Pete,
Is this configuration only meant to include all users as a single Security Group who will use SSLVPN?
Do you know if group-specific access is possible?
i.e. Finance group have access to certain servers while IT group have access to other servers.
Do we need multiple enterprise applications, one for each group?
Or if it can be done with one FortiGate SSLVPN enterprise application in the AzureAD and then group mapping within that application and on the FortiGate.
13/12/2022
The Forti can do this – I prefer to create a portal for each user group, then just specify what internal assets each group has access to.
31/01/2024
I try to do this configuration but when I connect to the VPN or test with EntraID the retorn is:
Unable to establish VPN connection. The VPN server may be unreachable (-6005)
I review all the configurations.
20/04/2024
increase remote authentication timeout
with below
config system global
set remoteauthtimeout 60
06/09/2024
If I am publishing the VPN using an Alternate port, does that need to be specified in the Basic Saml Configuration fields in Entra ID?
i.e. if I am using port 12345 would I then use
https://vpn.company.com:12345/remote/saml/metadata
https://vpn.company.com:12345/remote/saml/login
https://vpn.company.com:12345/remote/saml/logout
10/09/2024
To be honest Ive not tried, though your methodology seems sound – let me know how you get on.
28/02/2025
I am using an alternate port of 4433 for client VPN’s. Has anyone tested this the Basic SAML config fields shown above and verify it worked?
https://vpn.company.com:4433/remote/saml/metadata
https://vpn.company.com:4433/remote/saml/login
https://vpn.company.com:4433/remote/saml/logout
27/05/2025
HI! My SAML (SSO) config using Forticlient is working perfect but I cannot disable the basic authentication, I mean “user and password” login. How can I disable this from Fortigate side to prevent users to login manually using their username and password?