KB ID 0001783
Problem
If you want to employ the IPS service of a FortiGate firewall then you need a license for that privilege. At the time of writing you can get IPS as part of the following subscription licenses;
- Enterprise Protection
- SMB Protection (Only on firewalls SMALLER than 100F)
- Unified Threat Protection (UTP)
- Advanced Threat Protection (ATP)
But Forti love to change the names of things, so double check with your vendor.
Fortigate IPS (A Quick Tour)
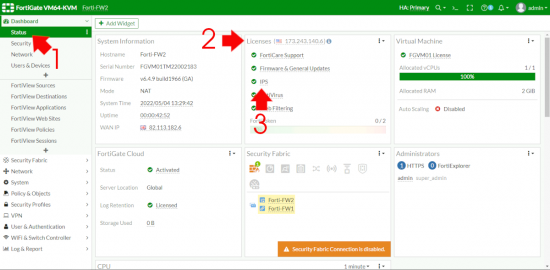
OK let’s see if we have a valid IPS Licence. Dashboard > Status > Licences > IPS > If it’s green and ticked we are good.
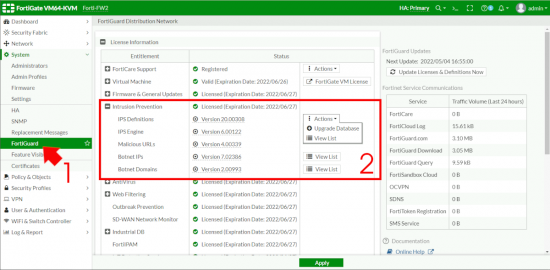
Now let’s make sure all our Intrusion Prevention definitions and engines etc are all up to date.
Note: Notice the Malicious URLs – I’ll mention that again in a minute.
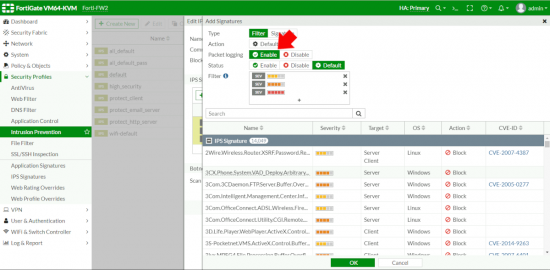
The next couple of steps are purely informational, (so you can understand how IPS works, and how everything hangs together). Go to Security Profiles > IPS Signatures. Spend a few minutes looking at this page so you will better understand how they are applied. First each one is assigned a Severity,
1. Informational (green) 2. Low (blue) 3. Medium (yellow) 4. High (orange) 5. Critical (red).
In addition it’s given a Target (Server, Client , or BOTH), and an applicable OS, Action is set by default to BLOCK or PASS
Note: You can also find specific CVE-IDs (if applicable) for each signature, this will hyperlink to the info for that CVE, but also lets you quickly check you are protected against a new CVE, (you can type them in the search section).
Why is all that important? Well if you know that then, how the IPS profiles work is pretty self explanatory, it uses all the above to group signatures together by severity, target and OS, which enable you to make your own very granular profiles (if you wanted to).
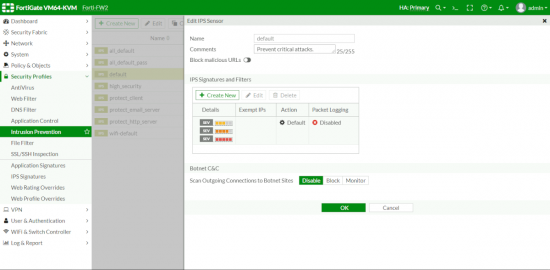
So let’s have a look at them, Security Profiles > Intrusion Protection.
To take a look at each one, select it and edit, to be honest most of the time you will be wanting default or all_default though (as you can see there are specific profiles for web servers and mail servers etc.
Note: Remember I mentioned the Suspicious URLs above? This is where you can enable that if you wish, be aware this is a dynamic list of URLs that you cannot edit (or whitelist) you need to make a request to FortiNet if you want to remove a URL from it. The documentation says;
“To use this IPS signature to block malicious URLs, select Block malicious URLs. This feature uses a local malicious URL database on the FortiGate to assist in drive-by exploits detection. The database contains all malicious URLs active in the last one month, and all drive-by exploit URLs active in the last three months. The number of URLs controlled are in the one million range.“
Also Note: Logging is disabled by default, (more on that in a minute).
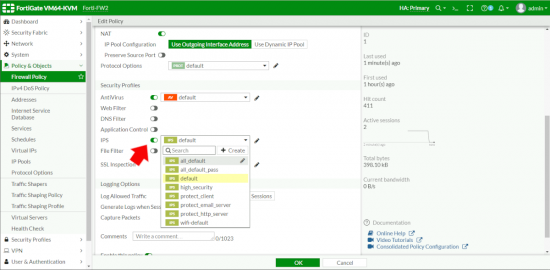
Enable FortiGate IPS
To actually enable IPS is simple, in any normal Firewall Policy (or IPv4 Policy if you’re on ‘old code’) you enable the IPS Policy you require inside it like so.
Testing FortiGate IPS
Do a search for this and the web is full of articles on creating a custom signature adding that to a policy then testing it, which is a bit ‘bobbins’ IMHO. It’s an IPS, let’s put on our black hat and do something nefarious to make sure it’s working, (obviously ask a grown ups permission before launching attacks on your own network, and don’t send your IT security manager to PeteNetLive to complain, because I’ll just laugh at them).
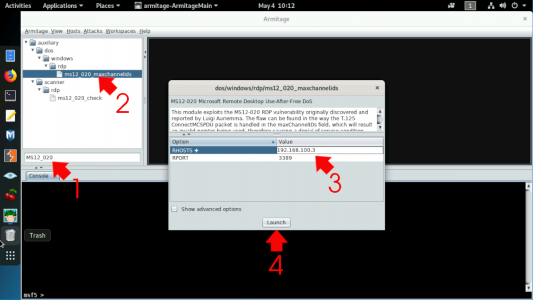
OK, really straight forward, I’ve got KALI Linux running Armitage (a Metasploit tool) on my LAN. Which I’m going to use to attack a Windows server that’s sat just outside my FortiGate. Using a known RDP vulnerability. But first let’s enable logging on our IPS Profile.
Edit the policy (make sure it’s the one that’s actually getting inspected!) Enable packet logging > OK.
Launch Armitage, connect using the default settings, search for MS12_020 and you should see it listed (as shown) > Double click it > Enter the IP of the server to attack > Launch. After some code scrolls by eventually it will probably say ‘RDP service unreachable‘ (because our IPS has earned its wages).
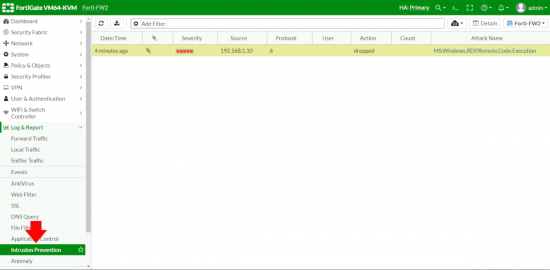
Note: At this point I’d say go and have a coffee, IPS blocks instantaneously, but it takes a couple of minutes for it to appear in the logs.
Log and Report > Intrusion Prevention > Boom ‘time for tea and medals!’ (remember give it a few minutes). Dont forget to go back and disable logging on your IDS Policy.
Related Articles, References, Credits, or External Links
NA