KB ID 0001772
Problem
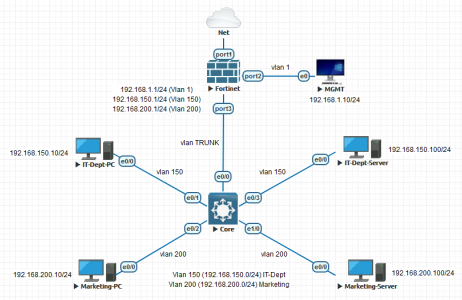
I was asked by a colleague at work the other day, can we replace the Cisco firewalls with FortiGate firewalls for a client? As a business we are heading towards Forti, but before I said yes I wanted to know what the firewall was actually doing before I said yes. On closer inspection the firewall in question didn’t appear to be doing anything too scary, but I did notice that the LAN interface was sub-interfaced to the various internal VLANs. I didn’t know how FortiGate handled this, so I fired it up on the test bench to test FortiGate Sub Interfaces.
So I needed to create TWO sub interfaces on the FortiGate (on port3).
Creating FortiGate Sub Interfaces
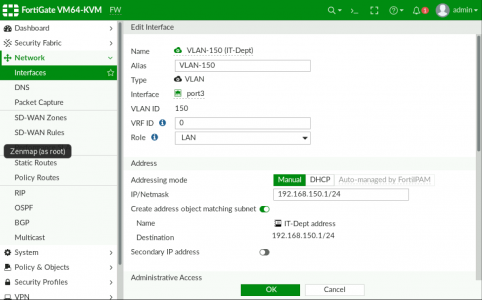
Simply put, on a FortiGate if you want what a Cisco engineer would refer to as a ‘sub interface‘, then you simply add a VLAN interface to a physical interface. Like so, Network > Interfaces > {Physical Interface} > Create New > Interface.
Give the new interface a name (and alias if required) > Interface Type should be VLAN > Select the parent physical interface > Add the VLAN ID (Tag) and specify an IP address of the interface.
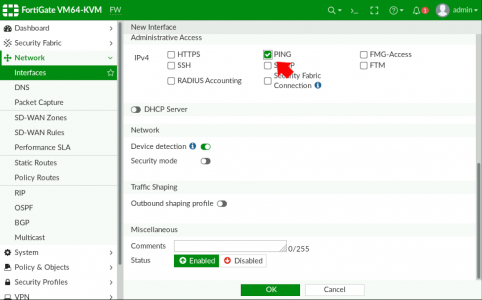
Just for testing I’ll allow PING, on the VLAN interface also > OK.
Repeat the procedure to add further sub interfaces (VLANs).
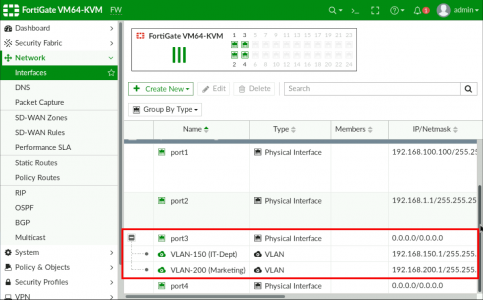
Remember this is just a ‘Router on a stick‘ configuration, to further allow traffic to the internet, (or between VLANs) you still need to add that traffic to the firewall policy to let the traffic through, (it is a firewall after all!)
Setting up Switches for FortiGate Sub Interfaces?
I’ve probably got this covered elsewhere on the site, but the core switch is Cisco so I just created a trunk port, and allowed ALL VLANs, (because I’m lazy, in production, you might want to lock that down a little!)
! interface Ethernet0/0 switchport trunk encapsulation dot1q switchport mode trunk ! interface Ethernet0/1 switchport access vlan 150 switchport mode access ! interface Ethernet0/2 switchport access vlan 200 switchport mode access ! interface Ethernet0/3 switchport access vlan 150 switchport mode access ! interface Ethernet1/0 switchport access vlan 200 switchport mode access no cdp enable !
My Switch isn’t Cisco it’s HP/Aruba! Then you simply TAG the VLANs required to the uplink see this article.
Related Articles, References, Credits, or External Links
NA