KB ID 0001721
Problem
A while ago I did a run through on site to site VPNs from Cisco ASA to Fortigate firewalls. Back then I said that the default settings were a bit ‘shoddy‘ and that I’d revisit it once I had more time.
What do you mean shoddy? Well, Cisco and Fortinet are both guilty of enabling ‘Everything’ to make the tunnel come up, so people can just use a wizard and not put to much thought into the process, for most people thats absolutely fine. However I’ve found ‘Many Times‘ I’ve been trying to put a VPN into third party and it’s like a game of ‘Encryption Bingo‘ e.g. ‘Can you change it from AES128 to AES256 and change the hash to SHA512‘, or ‘Do you not support elliptical curve’. Who are these people? Do they expect Tom Cruise to come rappelling out of a skylight to steal the details of their 2016 Christmas golf event!
I digress, so here’s how to set up a site to site VPN using IKEv2 with some weapons grade encryption. Here’s a pretty picture of what it will look like;
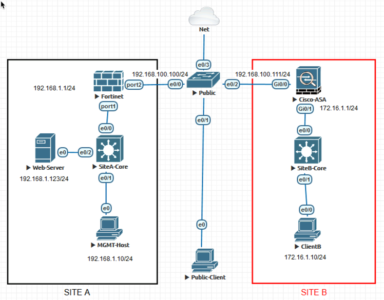
And here’s what my test bench topology looks like in EVE-NG.
Configuring the Fortigate for Site to Site VPN
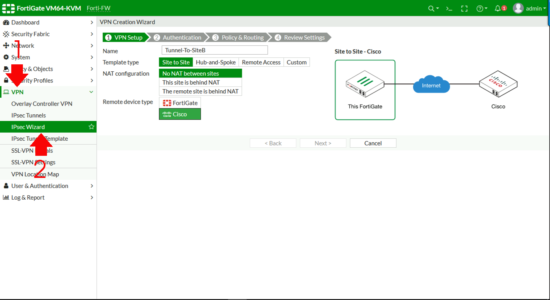
After saying don’t use the wizard, I’m going to use the wizard to do the Fortigate end, then I’ll edit the tunnel it creates and make it a bit more ‘fit for purpose’.
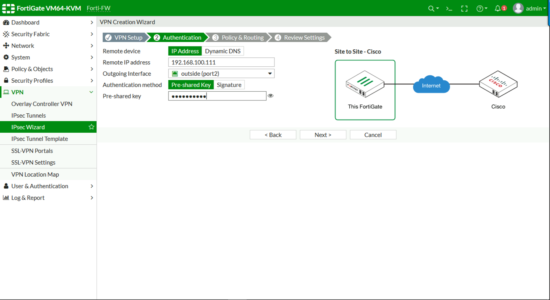
From the web management portal > VPN > IPSec Wizard > Give the tunnel a name > Change the remote device type to Cisco > Next.
Give it the ‘public’ IP of the Cisco ASA > Set the port to the ‘outside’ port on the Fortigate > Enter a pre-shared key, (text string, you will need to enter this on the Cisco ASA as well, so paste it into Notepad or something for later) > Next.
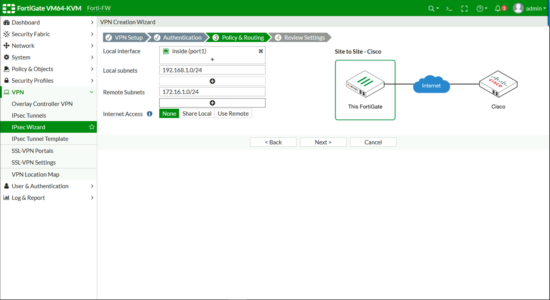
Local interface will be in the ‘inside’ interface on the Fortigate > Enter the local subnet(s) > Enter the remote (behind the ASA) subnet(s) > Next.
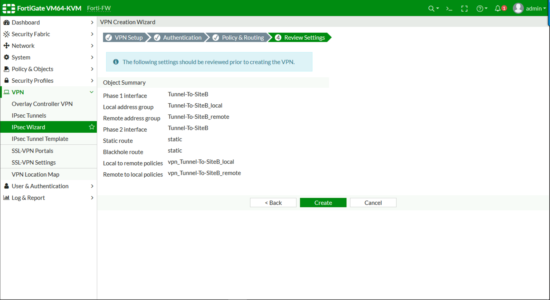
Review the settings > Create.
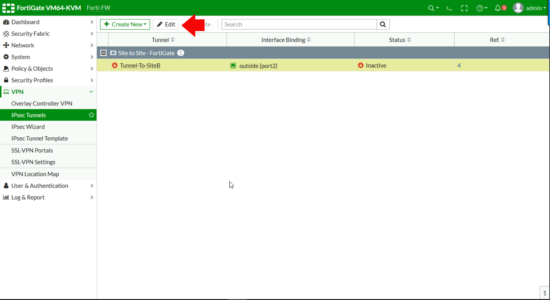
Select IPSec Tunnels > Select the new tunnel > Edit.
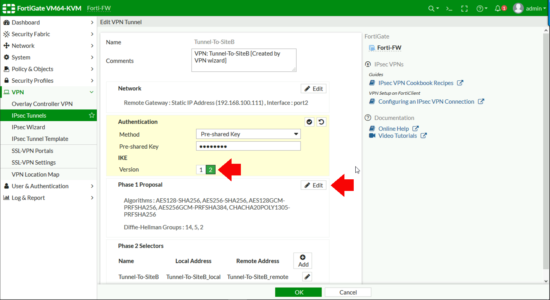
In the Authentication Section > Edit > Change the IKE Version to 2 > Edit the Phase 1 Proposal.
Note: If you can’t see this option, change the tunnel type to custom.
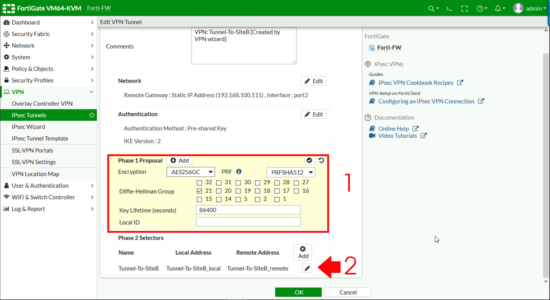
Delete all the factory ones and add one for;
- Encryption: AES256GC
- PRF: PRFSHA512
- Diffie-Helman Group: 21
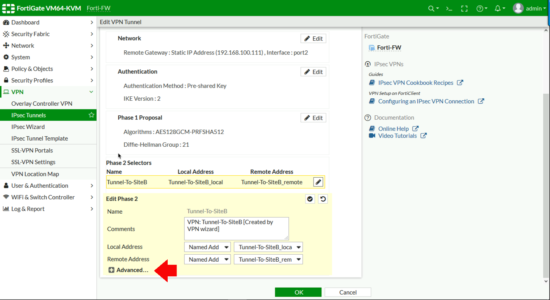
Then under Phase 2 Selectors click the pencil icon to edit.
Advanced.
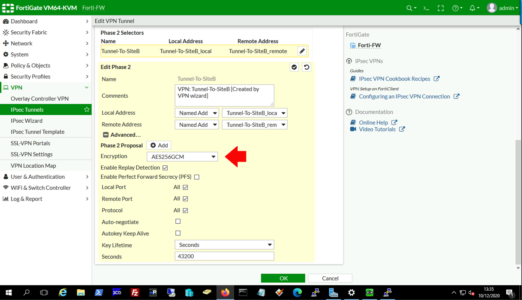
Remove any existing Phase 2 proposals, add a new one
Encryption: AES256GCM
Click OK to close.
Manually Configuring the Cisco ASA For Site to Site VPN
Manual VPN via CLI
We all know real men work at command line, paste this in, boom done!
WARNING: If your ASA already has a crypto map then use the name of that map rather than CRYPTO-MAP (as below) or all your existing VPNs will break!
! crypto ikev2 policy 5 encryption aes-gcm-256 integrity null group 21 prf sha512 lifetime seconds 86400 crypto ikev2 enable outside ! object network OBJ-SITE-B subnet 172.16.1.0 255.255.255.0 object network OBJ-SITE-A subnet 192.168.1.0 255.255.255.0 ! access-list VPN-INTERESTING-TRAFFIC extended permit ip object OBJ-SITE-B object OBJ-SITE-A ! nat (inside,outside) source static OBJ-SITE-B OBJ-SITE-B destination static OBJ-SITE-A OBJ-SITE-A no-proxy-arp route-lookup ! tunnel-group 192.168.100.100 type ipsec-l2l tunnel-group 192.168.100.100 ipsec-attributes ikev2 remote-authentication pre-shared-key 123456 ikev2 local-authentication pre-shared-key 123456 isakmp keepalive threshold 10 retry 2 ! crypto ipsec ikev2 ipsec-proposal VPN-FORTIGATE protocol esp encryption aes-gcm-256 protocol esp integrity null ! crypto map CRYPTO-MAP 1 match address VPN-INTERESTING-TRAFFIC crypto map CRYPTO-MAP 1 set peer 192.168.100.100 crypto map CRYPTO-MAP 1 set ikev2 ipsec-proposal VPN-FORTIGATE crypto map CRYPTO-MAP interface outside !
Manual VPN via ASDM
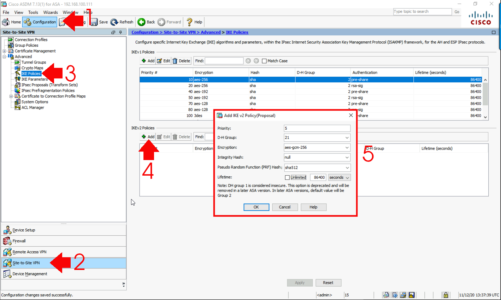
You can do the first couple of steps together, but I like to do the Phase1 and Phase 2 proposals first, then tie it all up at the end. Configuration > Site to Site VPN > Advanced > IKE Policies > IKEv2 Policies > Add.
- Priority: 5
- D-H Group: 21
- Encryption: AES-GCM-256
- Integrity Hash: null (GCM protocols don’t need an integrity hash)
- Pseudo Random Function (PRF) Hash: sha512
OK > Apply
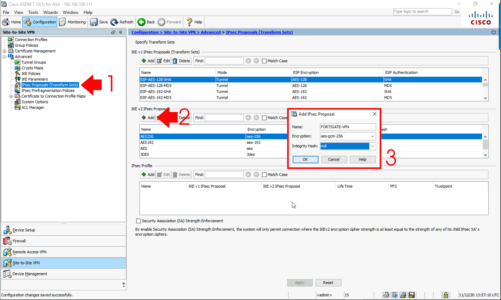
Now for Phase 2 (On a Cisco ASA that’s defined with a ‘transform set’). IPsec Proposals (Transform Sets) > IKEv2 > Add.
- Name: FORTIGATE-VPN
- Encryption: aes-gcm-256 (NOT aes-gmac-256, or this will happen and you will look stupid.)
- Integrity Hash: null (again not required for GCM protocols).
OK > Apply
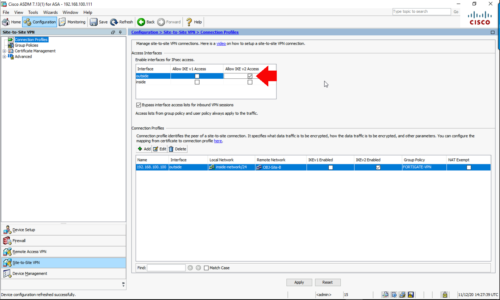
Connection Profiles > Tick IKEv2 on the OUTSIDE interface to enable it.
Connection Profile > Add
- Peer IP: (Public address of the Fortigate)
- Local Network: Add in the network behind the ASA.
- Remote Network: You may need to add an object-group for the remote network (behind the Fortigate).
- Group Policy Name: FORTIGATE_VPN
- Local Passphrase: An alphanumeric string of characters (it’s a pre-shared key it must match the one you set on the Fortigate).
- Remote Passphrase: Set the same at the local passphrase.
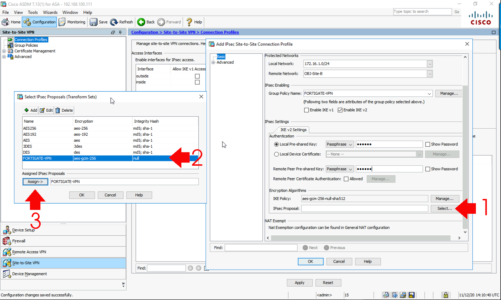
Scroll down.
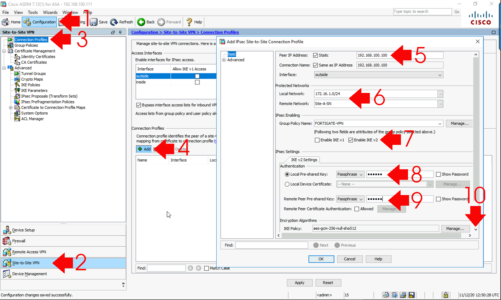
Make sure your IKE Phase 1 policy is in the list, (you may have many) > IPSec proposal > Select > locate yours and add it in > OK > OK > Apply.
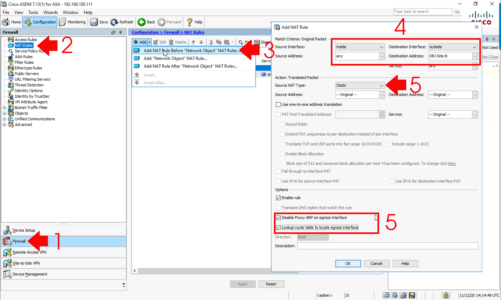
The last thing to do is make sure that the traffic travelling over the VPN DOES NOT get NAT translated > Firewall > NAT Rules > Select the top one > Add >Add Nat Rule Before.
- Source Interface: inside
- Destination Interface: outside
- Source Address: any
- Destination Address: {The group you created above for the network address behind the Fortinet}
- Source NAT Type: Static
- Disable Proxy ARP : Tick
- Lookup Route Table: Tick
OK > Apply
Don’t forget to save the changes > File > Save Running configuration to flash
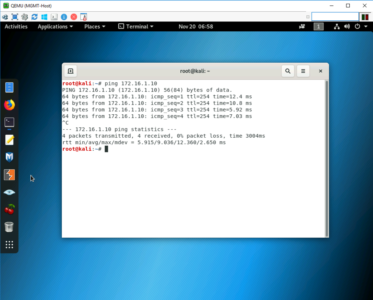
Finally send some interesting traffic across the VPN to bring up the tunnel.
Related Articles, References, Credits, or External Links
NA


27/03/2023
Do you know which special characters are not allowed by the FortiGate? We recently converted our Firepower to a FortiGate, and one of the tunnels terminated to a Cisco ASA. This tunnel failed authentication, and after troubleshooting it and re-entering the PSK multiple times, we decided to remove all special characters. Tunnel came immediately up. Given the time we were doing the conversion and given this was one of our vendors, we elected to keep the key the way it was. Now, another conversion is coming up with 30+ IPsec tunnels, and I’m conconerned about multiple tunnels have that [unknown to me] special character in it.
Thanks for your website. It’s been invaluable to me.
28/03/2023
Docuemtnation says ASCII charecters are supported.