KB ID 0001717
Problem
Continuing with my ‘Learn some Fortigate‘ theme’. One of the basic requirements of any edge firewall is site to site VPN. As the bulk of my knowledge is Cisco ASA it seems sensible for me to work out how to VPN both those firewalls together, like so;
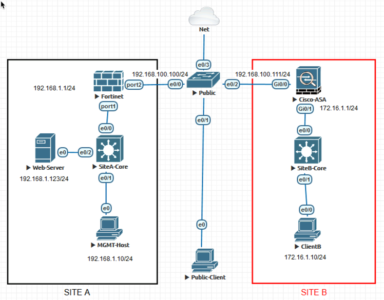
Well that’s the pretty picture, I’m building this EVE-NG so here’s what my workbench topology looks like;
Disclaimer (Read First! Especially before posting any comments!)
Fortinet prides itself on you not needing to use the CLI, (until you actually need to use the CLI of course!) But both ends are configured using the GUI and ASDM. This is designed for the ‘Let’s just make it work, who cares what’s going on under the hood‘ generation. Which means it enables IKEv1 NOT IKEv2 on the Fortigate, and BOTH IKEv1 and IKEv2 gets enabled on the Cisco ASA. Couple that with all the weak Crypto sets that get enabled, because someone might have a hardware firewall from 1981 or something! So in production I’d consider doing things a little more manually. I will post another article on the same subject, but then I’ll make the tunnel as secure as I can, (watch this space). This is an exercise in getting the tunnel up and making it work.
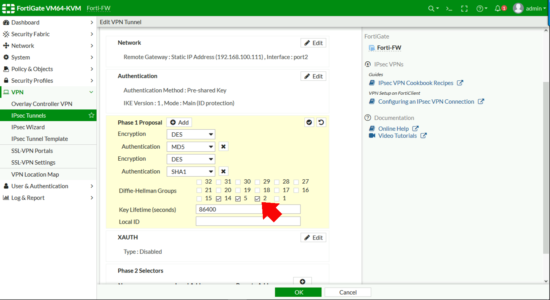
Tech Note: If you just use both wizards it wont work, thankfully I could debug the tunnel on the Cisco ASA to work out why. Fortinet sets all the DH groups to 5, and Cisco sets them all to 2. And Fortinet enables PFS and Cisco don’t. (They do on older versions of the OS, but not on the newer ones).
Create IKE/IPSec VPN Tunnel On Fortigate
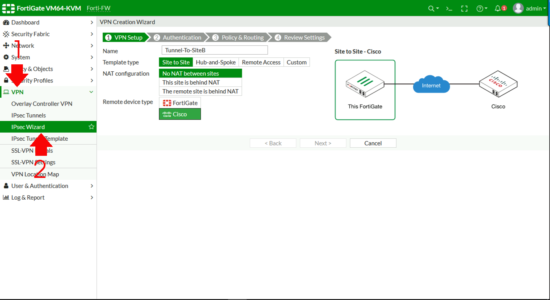
From the web management portal > VPN > IPSec Wizard > Give the tunnel a name > Change the remote device type to Cisco > Next.
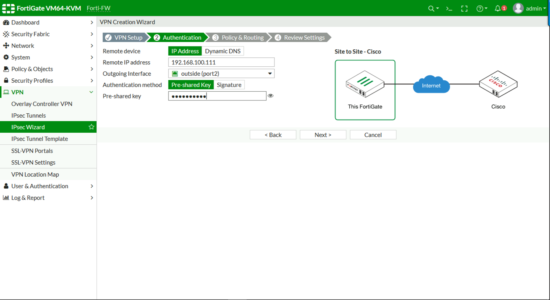
Give it the ‘public’ IP of the Cisco ASA > Set the port to the ‘outside’ port on the Fortigate > Enter a pre-shared key, (text string, you will need to enter this on the Cisco ASA as well, so paste it into Notepad or something for later) > Next.
Local interface will be in the ‘inside’ interface on the Fortigate > Enter the local subnet(s) > Enter the remote (behind the ASA) subnet(s) > Next.
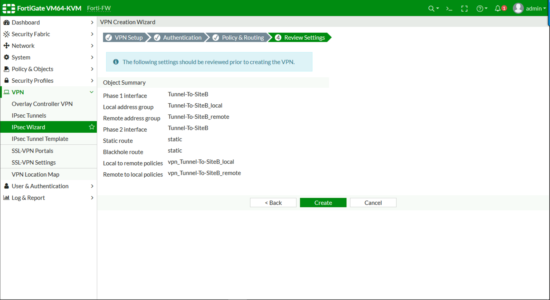
Review the settings > Create.
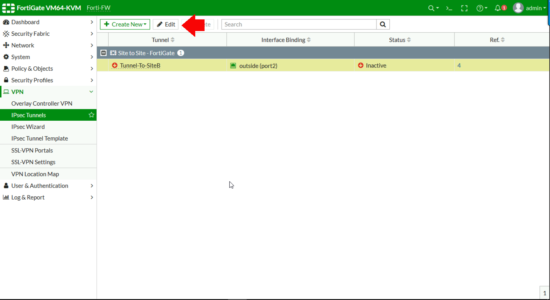
Select IPSec Tunnels > Select the new tunnel > Edit.
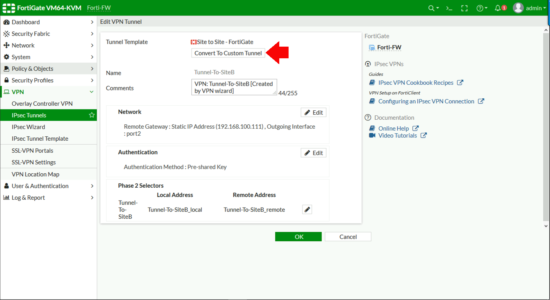
Convert to Custom Tunnel.
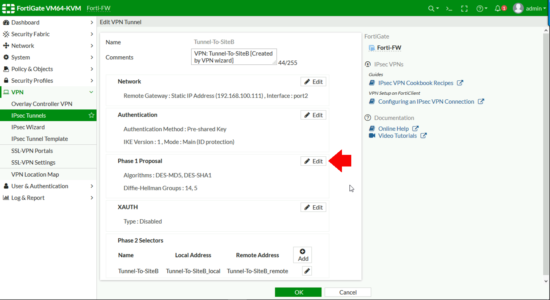
Phase 1 Proposal > Edit.
Add in Diffie Hellman Group 2
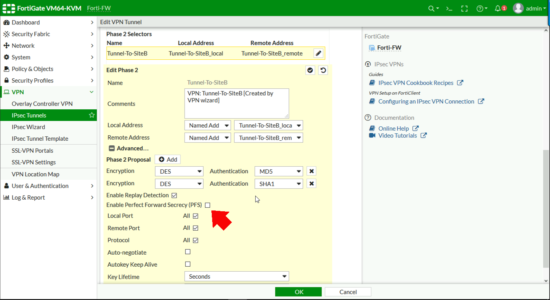
Phase 2 Selectors > Edit > Advanced > Untick Enable Perfect Forward Secrecy > OK.
Create IKE/IPSec VPN Tunnel On Cisco ASA (ASDM)
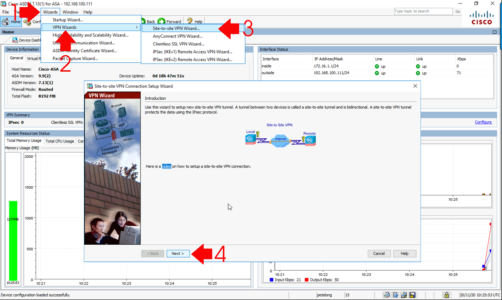
Connect to the ASDM > Wizards > VPN Wizards > Site-to-Site VPN Wizard > Next.
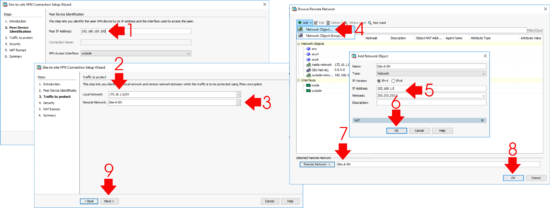
You should already have an object for your Local Network add that in > Then add in a new Network Object for the remote (behind the Fortigate) subnet. MAKE SURE that the new object is selected as the Remote Network > Next.
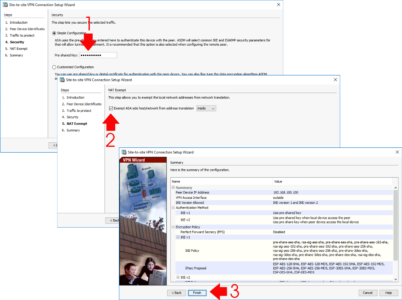
Enter the Pre-Shared key you used (above) > Next > Tick to DISABLE NAT > Next > Finish.
Tech Note: Look at all those Ciphers/Hashing/Additional Protocols that are about to be turned on! 🙁 That’s why I work at command line.
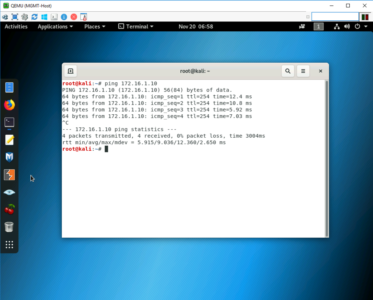
Finally you will need to send some traffic over the tunnel to ‘bring it up’.
If you have a problem, see the debugging/troubleshooting links below.
Related Articles, References, Credits, or External Links
Troubleshooting Phase 1 Cisco Site to Site (L2L) VPN Tunnels
Troubleshooting Phase 2 Cisco Site to Site (L2L) VPN Tunnels



30/03/2021
Does Fortigate support feature to announce networks it learned as a part of phase 2 IPSec Tunnel? Something like Cisco Reverse Route Injection (RRI)?
Thank you!
30/03/2021
Hi Yes it does, I’ve not implemented it myself, and information is a bit sketchy.