KB ID 0001716
Problem
If you have a host that you want to be able to access from the outside of the firewall e.g. a webserver then this is the process you want to carry out. I didn’t find this process particularly intuitive and it highlighted why I don’t like GUI management interfaces, (in 6.4 the menu names have changed, this rendering a million blog pages inaccurate!)
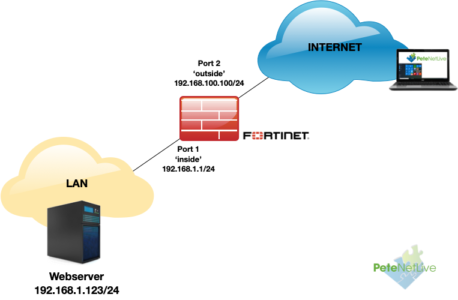
I’m setting this up in EVE-NG on the work bench and this is what I’m trying to achieve;
So to access my web server from ‘outside‘ the firewall I need to give it a NATTED ‘public‘ address on 192.168.100.0/24. Here the server is on the LAN if yours is in a DMZ then substitute the DMZ interface for the inside one I’m using.
Solution
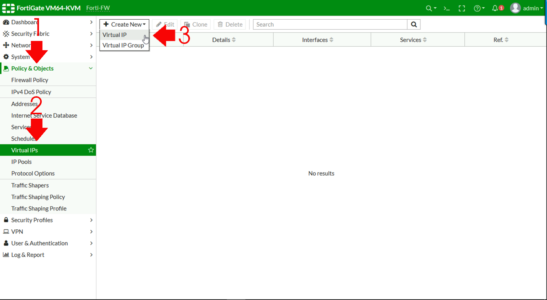
First task is to create a ‘Virtual IP‘, this will be the ‘public IP‘ that the web server will use. From the management interface > Policy and Objects > Virtual IPs > Create New > Virtual IP
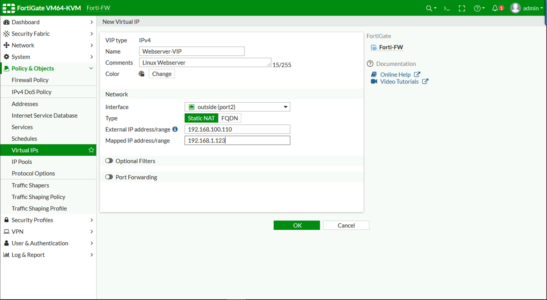
‘Give it a sensible name, and add a comment if you wish > Set the interface to the public facing port > Type, set to ‘Static NAT‘ > External IP, (although it says range just type in the single public IP) > Internal IP = Enter the LAN IP > OK.
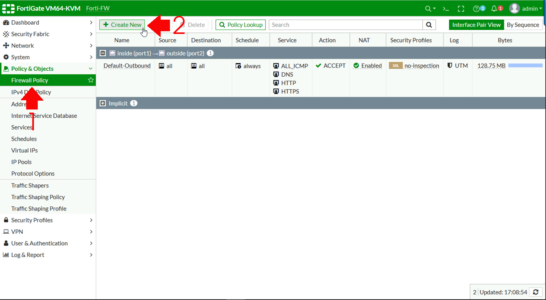
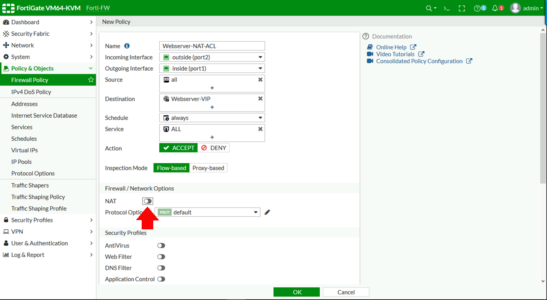
Firewall Policy > Create New.
Note: If your firewall is older then 6.4 the tab is called ‘IPv4 Policy‘
Give the entry a name > Incoming interface = the public interface > Outgoing Interface = the inside/LAN interface > Source = ALL > Destination = SET TO YOUR VIRTUAL IP > Schedule = Always > Service = ALL (though you can of course select http and or https in production) > DISABLE NAT. (Trust me I know that makes no sense) > OK.
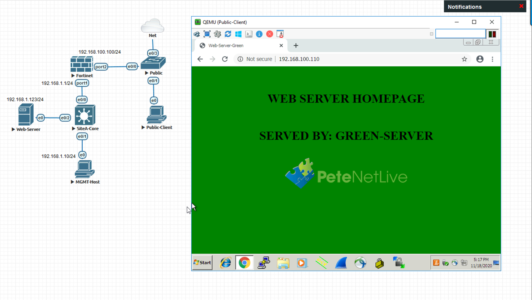
Just to prove this is not all ‘Smoke and Mirrors‘ here’s my topology running in EVE-NG, and my external host (Named: Public-Client) Browsing to 192.168.100.110, and the Fortigate translates that to 192.168.1.123
Related Articles, References, Credits, or External Links
EVE-NG Deploying Fortigate v6 Firewalls
TinyCore Linux: Build a ‘Persistent’ Web Server

19/11/2020
Hope to see more posts on FortiGate! Love this site!
20/11/2020
They are in the pipeline, thanks Tom
23/11/2020
hahaha
Apparently, like me, they got tired of suffering with ASA.
Good job!
24/11/2020
I’m admitting defeat! Cisco are their own worst enemy.
01/09/2021
Thank you, Great recipe for making a nodesb publicly available.
Note:
NAT should be enabled though.
25/09/2021
What about outbound static NAT? I need the outbound traffic to have the same IP.
27/09/2021
It will?
02/02/2023
Excellent article. Good job! Thank you