KB ID 0001693
Problem
We mac users always get overlooked. If I had a pound for every time I’ve heard ‘Yeah we don’t support macs?” I would be a rich man. But thankfully this makes us work things out for ourselves usually!
So recently I did a article Azure: Point To Site VPN (Remote Access User VPN) but what if you want to use the same solution for a remote mac user?
Solution
Firstly you will want to download the VPN package (and have a valid client/user certificate, [see the link above]).
Obviously the installer is for Windows, but within the ZIP file you download, it has a copy of the XML file with the settings in it, and a copy of the Root CA certificate you used.
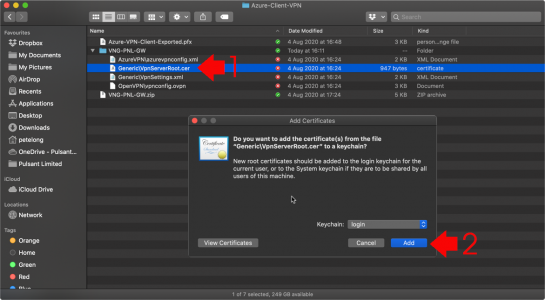
So your first job is to ‘import‘ the client certificate, it will be in PFX format, (if you followed my instructions), so you will need to supply the password you specified when creating the PFX file (not the mac password), when prompted to install it (double click on it).
The engineer in me isn’t quite sure why the client needs the Root CA certificate on it, (because that’s not how certificates work!) But Microsoft insist it’s necessary, so also double click and install the Root CA Certificate, (it’s inside the VPN Package).
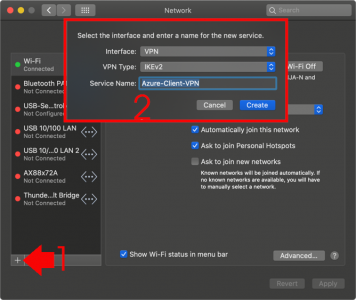
You don’t need to install VPN software onto the mac, (it has its own built in). Click the Apple Logo > System Preferences > Network > Add > Interface = VPN > VPN Type = IKEv2 > Service Name = Azure-Client-VPN > Create.
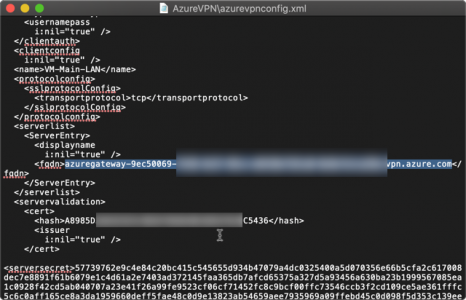
Now open the XML file from within you VPN client software ZIP file, and locate the FQDN of the ‘Gateway’ address in Azure > Copy it to the clipboard.
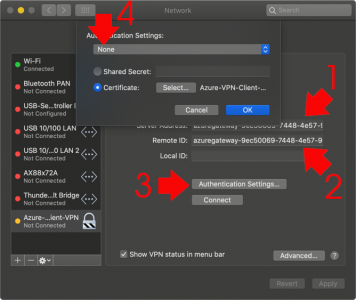
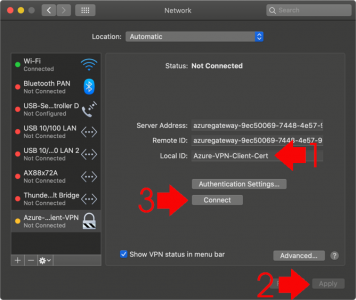
Paste the server address into BOTH Server Address AND Remote ID > (Leave Local ID blank for now) > Authentication Settings
WARNING: I’m using mac OS Catalina, so I choose ‘None’ (NOT CERTIFICATE). But for mac OS Mojave (and older) CHOOSE CERTIFICATE). It’s a bug that causes an error (see below) if you don’t.
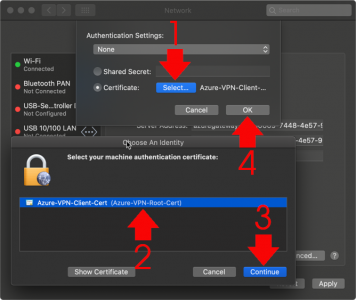
Select > Choose the CLIENT certificate you imported earlier, (Take note of the name in brackets, this is the common name on the certificate). You will need this in a minute! > Continue > OK.
Put the Common Name from the certificate into the Local ID section > Apply > Connect.
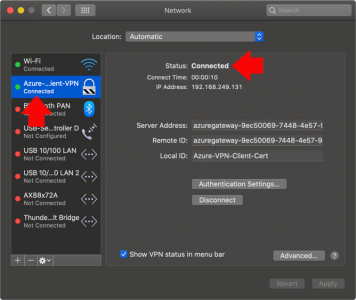
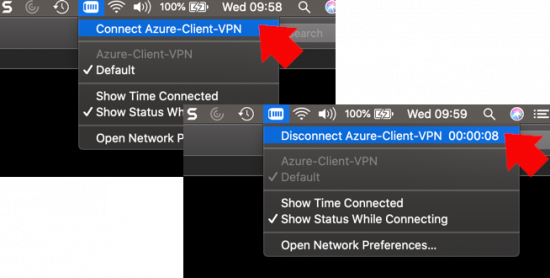
All being well it should connect, (though it may prompt for you to enter your user password). BY DEFAULT the option ‘Show VPN Status in Menu Bar‘ should be ticked, if it isn’t then tick it.
With that option ticked, you can connect and disconnect the VPN quickly without needing to go back into System Preferences like so;
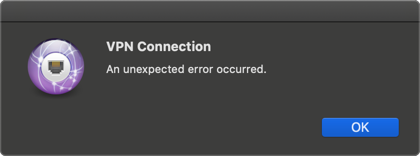
Error: VPN Connection, ‘An unexpected error occurred’
Remember above when I said choose ‘None‘ for Catalina, NOT certificate? Well this is what happens if you choose certificate!
Related Articles, References, Credits, or External Links
NA



13/01/2021
Does this work for P2S VPNs that are OpenVPN-based? I know there is an OpenVPN client for macOS but I’ve not got it to work on Windows so not sure it’s do-able on macOS either.
14/01/2021
I’ve never tried is Ross, but I’ll open it up for comment?
10/02/2021
Quote:
The engineer in me isn’t quite sure why the client needs the Root CA certificate on it, (because that’s not how certificates work!) But Microsoft insist it’s necessary…
Most likely this is necessary because it’s a self-signed certificate, so your OS won’t trust it by default unless you add it to the root certificate store (or intermediate). That’s why you need to install it.
Good explanation, glad I’ve found your website!
10/02/2021
Hi Wouter,
The remote client would only need a CA cert if it needed to authenticate the Gateway in Azure, in our example the gateway in Azure needs to authenticate the the certificate on the remote client. IT (The Azure End) needs the CA certificate to check that, the remote client does not need to trust the authority that issued the certificate it’s using.
11/02/2021
Hi PeteLong,
I’ve only real experience with using certificates on websites, for which the client does need to trust the certificate issuer.
Still learning 🙂
Thanks for your clarification!
11/02/2021
No worries, typically the remote host only needs a CA Cert, if it does host validations against the gateway. If you do LDAPS lookups into AD from Duo, or RSA, or FortiGate, theres an usually an extra box to tick if you want to validate the device that’s doing the authentication also.
02/02/2022
Any idea on how one might push this via Intune?
Thank you!
04/02/2022
I do not, but I’ll happily post your question….
08/03/2022
Hi, I followed your guide step by step, copying and pasting powershell scripts, but I cannot get Point to Site VPN working on Mac.
I tried on two different mac (One on Catalina, the other one on Monterey), and from different wi-fi networks and mobile hotsposts.
When I click on “Connect” it tries to connect for a while and then it ends with “The VPN Server did not respond”.
Do you have any clue about what can be the issue?
Many many thanks in advance!
20/05/2024
same here. Have you solved your issue?
09/03/2022
OF COURSE I had to read the “An unexpected error occurred” section! Thank you so much for assuming that idiots like me skip over important details and included this error message 😀
Worked like a charm (if you actually read it ..), thanks a lot!
31/03/2022
Do you know why you would be unable to select the certificate and get a message saying “No machine certificates” found when setting the authentication settings? I’ve imported both certificates to ‘login’ on Keychain but am unable to select one to authenticate with. In Keychain there’s a message saying “certificate is not standards compliant” – wonder if this is causing the issue of being unable to select one.
31/03/2022
If you import the cert into ‘System Keychain’ does that fix the problem?