KB ID 0001686
Problem
This brings me to the end of my recent FTD articles. Although this is not a complete run though of all the capabilities, it will point you in the right direction to enable;
Solution
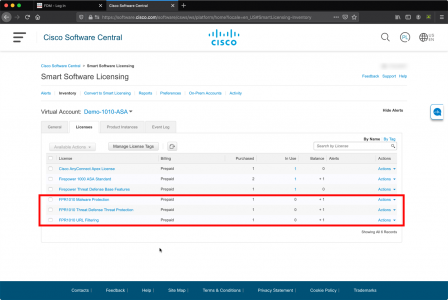
Each of these is a ‘Licensed Feature‘ which means it’s going to cost you. Not only that, but you need to have the licences in your Cisco Smart Account before you start.
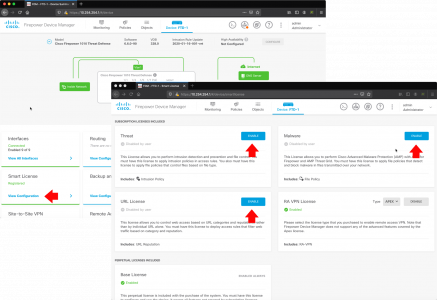
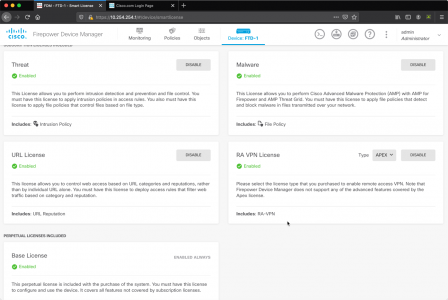
Connect to the FTD via the FDM web console. > Smart Licence > View Configuration > Enable Threat, Malware, and URL License.
Make sure it looks like this, before proceeding.
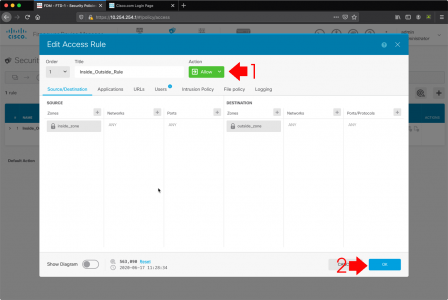
Mines got a ‘vanilla’ (factory default) policy, (allow everything out). But it’s set to TRUST, you need to change that to ALLOW, (you can’t do advanced inspection while it’s set to trust) > OK.
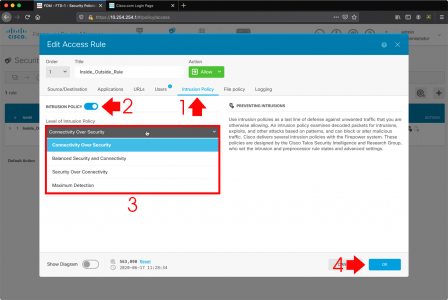
FTD: Enable IDS/IPS Intrusion Policy
With a policy access rule selected > Intrusion Policy > Enable > Select the level you want (they are pretty self explanatory, and if you have worked with Cisco IDS before you will be familiar) > OK.
Note: By default the FTD will be in IPS mode (prevention), If you want to change to IDS mode (detection). Then select policies > Security Policies > Intrusion > Inspection Mode > Edit > Chose ‘detection’ > OK
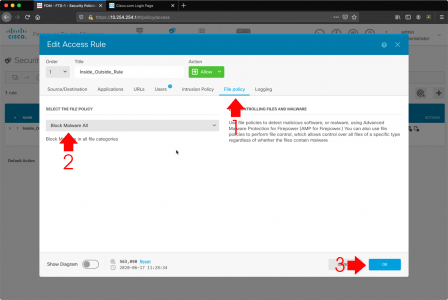
FTD: Enable AMP Policy
While in the access policy > File Policy > Block Malware All > OK.
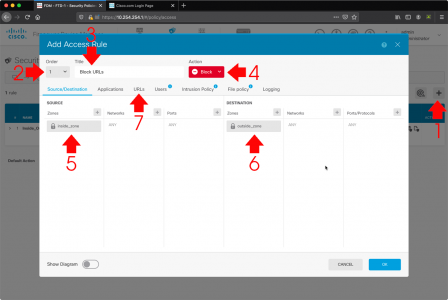
FTD: Enable URL Filtering Policy
Now we need to create a new access rule and set its action to BLOCK. Create (add) a new access rule > Make sure it is ABOVE your default TRUST or ALLOW rule > Give it a name > Set the action to BLOCK > Then I’m simply adding the inside zone as the source, and the outside zone as the destination > URLs.
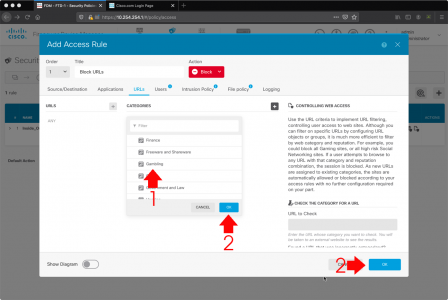
Then simply add in either the individual URLs you want to block. Or (more sensibly) the URL Category, i.e. Adult, Social Networking, or Gambling etc. you want to block > OK > OK.
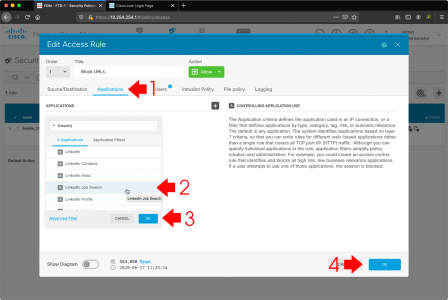
FTD: Enable Application Inspection (AVC)
Cisco have had AVC for a long time, but not many people use it, it’s the ability to perform up-to layer 7 (application layer) inspection and blocking. So let’s say you want to let your employees use LinkedIn but you don’t want them to use the job search, you can block that, or you want to block BitTorrent traffic, you can also do that with AVC. There are thousands of different options.
Like URL filtering you need to enable this on an access rule that’s set to BLOCK (here I’m lazily adding to the same one as my URL blocking, I suggest in production you create one just for AVC).
DONT FORGET: No changes will be applied untill you save and deploy the changes. (WHICH TAKES AGES!)
Related Articles, References, Credits, or External Links
Cisco Firepower 1010 Configuration