KB ID 0001683
Problem
I had a call with a client last week, they are in one of my employer’s DCs, and their servers are behind a vASA. They had purchased some Meraki MX devices for their IT team who were working remotely (during the Covid-19 lockdown), and were struggling. Normally we would just suggest AnyConnect, but these guys were building new machines for their clients, and needed access directly to the domain from their home networks to facilitate this. So a Site-to-Site VPN was the ‘best fit’ for them.
But being home internet connections they were on DHCP for their public IP addresses. If we were all Meraki, then Meraki Auto VPN would have them up and running in no time. Conversely if they were all ‘proper’ Cisco we would be OK. In fact if they had static IP’s at home we would be OK.
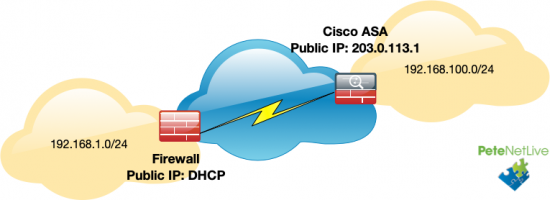
So how to setup a site-to-site VPN ‘into’ a Cisco ASA with a static IP, from another firewall with a dynamically assigned (DHCP) public IP?
I tested this firstly using a Cisco ASA at the ‘remote/dynamic’ end, then tested with a Meraki MX Device. But the methodology can be applied to any ISAKMP/IPSEC capable firewall with a dynamically assigned public IP that you want to establish a VPN into an ASA with a static IP address.
Solution
Step 1: Investigate Your Remote Device
Do your homework on the remote device, find out what it supports for VPN connectivity, you will need to answer the following questions;
- IKE Version: Does it use/support IKEv1 or IKEv2 (or both) Set the ASA config accordingly
- Phase 1 Encryption: What does it support? DES <- Don’t Use this if you can avoid it! 3DES, AES, AES-128, AES-192, AES-256 etc.
- Phase 1 Hashing: What does it support? MD5, SHA/SHA1, SHA256 etc.
- Phase 1 Diffie Hellman Group (for IKEv1): Group 1,2,5,14 etc.
- Lifetime: {in seconds}
- Pseudorandom function (for IKEv2): MD5, SHA1 or SHA256
- Phase 2 (IPSEC) Encryption: 3DES, AES, AES-128, AES-192, AES-256 etc.
- Phase 2 (IPSEC) Hashing: MD5, SHA1 or SHA254
- Phase 2 PFS: Off or DH1, DH2, DH5, or DH14 etc.
- Subnet on the remote site: Make sure it does not overlap with your central site, (or anyone else who will also be ‘dynamically’ connecting*).
- Pre-Shared-Key: MAKE SURE this is long/complicated and hard to guess.
*Note This may mean your remote sites may need to change their subnets so they don’t overlap!
Step 1 Configure the ‘Central’ ASA
I’ve covered IKEv1 VPNs and IKEv2 VPNs elsewhere on the site, feel free to go and see what what the following configuration is doing. For my Meraki Tunnel I’m going to use IKEv1, Phase 1 (3DES, SHA, Diffie Hellman Group 2, and a Lifetime of 86400 Seconds,) and Phase 2 (3DES, SHA and no PFS). Note: Some would consider this weak, but it’s the default setting on the remote device so lets keep it simple. In production you can slowly make phase1/2 more secure to your liking once you know it’s working.
Change the values in Red;
WARNING: If you already have a crypto map in use then change the keyword CRYPTO-MAP (below) to match yours. (Or all your VPNs will suddenly stop working!) Issue the command show run crypto map, if you’re unsure.
! object network OBJ-MainSite subnet 192.168.100.0 255.255.255.0 object network OBJ-RemoteSite-01 subnet 192.168.1.0 255.255.255.0 ! nat (inside,outside) source static OBJ-MainSite OBJ-MainSite destination static OBJ-RemoteSite-01 OBJ-RemoteSite-01 no-proxy-arp route-lookup ! crypto ikev1 policy 65535 authentication pre-share encryption 3des hash sha group 2 lifetime 86400 ! crypto ikev1 enable outside ! crypto ipsec ikev1 transform-set TS-IPSEC-VPN esp-3des esp-sha-hmac ! crypto dynamic-map DYNAMIC-CRYPTO-MAP 65535 set ikev1 transform-set TS-IPSEC-VPN crypto dynamic-map DYNAMIC-CRYPTO-MAP 65535 set reverse-route crypto map CRYPTO-MAP 65535 ipsec-isakmp dynamic DYNAMIC-CRYPTO-MAP crypto map CRYPTO-MAP interface outside ! tunnel-group DefaultL2LGroup ipsec-attributes ikev1 pre-shared-key V3ryL0ng&H@rd2Gue55 !
Step 3: Configure the Remote (DHCP) Firewall
If the remote end was going to be another Cisco ASA, here’s the config;
object network OBJ-MainSite subnet 192.168.1.0 255.255.255.0 object network OBJ-RemoteSite subnet 192.168.100.0 255.255.255.0 ! access-list VPN-INTERESTING-TRAFFIC extended permit ip object OBJ-RemoteSite object OBJ-MainSite nat (inside,outside) source static OBJ-RemoteSite OBJ-RemoteSite destination static OBJ-MainSite OBJ-MainSite no-proxy-arp route-lookup ! crypto ikev1 policy 10 authentication pre-share encryption 3des hash sha group 2 lifetime 86400 ! crypto ikev1 enable outside ! crypto ipsec ikev1 transform-set VPN-TRANSFORM esp-3des esp-sha-hmac ! crypto map CRYPTO-MAP 1 match address VPN-INTERESTING-TRAFFIC crypto map CRYPTO-MAP 1 set peer 203.0.113.1 crypto map CRYPTO-MAP 1 set ikev1 transform-set VPN-TRANSFORM crypto map CRYPTO-MAP interface outside ! tunnel-group 203.0.113.1 type ipsec-l2l tunnel-group 203.0.113.1 ipsec-attributes pre-shared-key V3ryL0ng&H@rd2Gue55 isakmp keepalive threshold 10 retry 2
Note For IKEv2 sample ASA Configs, Click Here
However if the remote end was going to be a Meraki Device.
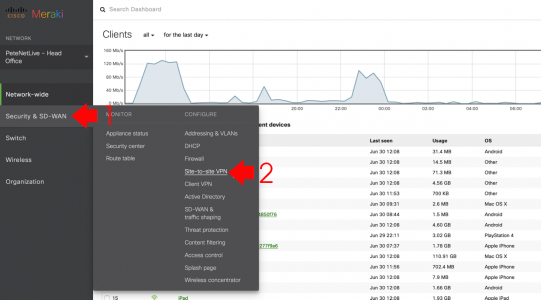
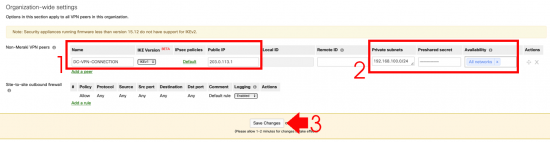
Log into the Meraki Portal, and select your ‘customer’ (if you have more than one) > Security & SD WAN > Site-to-Site VPN.
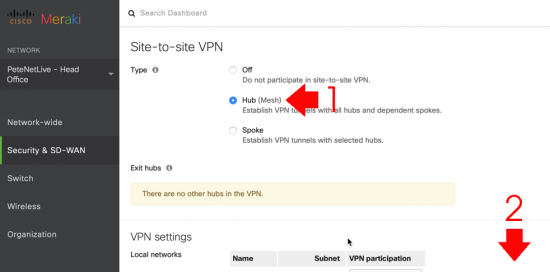
Type: Hub > Scroll down.
Non-Meraki VPN Peers > Add a peer.
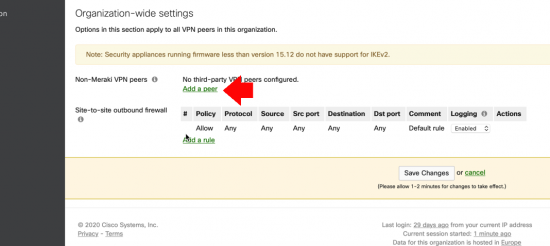
- Name: Give it a sensible name.
- IKE Version: IKEv1 (Note some versions don’t support IKEv2).
- Public IP :Of the ASA.
- Private Subnets: The subnet(s) behind the ASA.
- Availability: ‘All Networks’ Unless you want to filter it.
- Save.
Note: Should you wish to change any phase1/phase2 settings, click the link that says ‘Default‘ under IPSec policies.
Related Articles, References, Credits, or External Links
Special thanks to Paul White for putting me on the right road, and to Andrew Dorrian for taking the time to test the Meraki VPN config for me.

03/07/2020
If the remote end (DHCP) was an ASA use the command
crypto isakmp identity hostname
The ASA will send the hostname and domain as identifier and you can create a seperate tunnel-group for every remote office with DHCP and you can have seperate keys.
In the main ASA.
tunnel-group firewallx.domain.local ipsec-attributes
ikev1 pre-shared-key V3ryL0ng&H@rd2Gue5
Remote ASA
hostname firewallx
domain-name domain.local
crypto isakmp identity hostname
17/03/2021
Hi,
Can it be done vice-versa, so MX has static IP and ASA is dynamic?
19/03/2021
I don’t think so – though I’ll happily be proved wrong?
16/06/2022
Thank you very much Pete.
This was the best document and explained very well with a sample configuration.
I resolved my issue which otherwise we may have had to purchase additional hardware to make it to work.
22/12/2022
Is this possible to do using a VTI (route-based)? The hub has a static WAN IP, but the branch office has a main ISP and a backup ISP, and both are dynamic WAN IPs and the ISP will not allow static IPs on either for some reason.
I ask because the branch office has a Sophos XGS firewall that connects to our ASA at the main office, and it’s currently using a policy-based VPN, but the XGS at the branch office does not handle VPN failback very well between the two ISPs.