KB ID 0001681
Problem
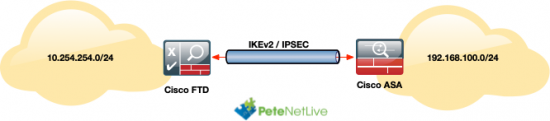
While working out how to create a VPN on the Cisco FTD (Firepower 1010), I thought I might as well set it up to the Cisco ASA that I have in the Data Center on my test network. This is what I’m connecting;
Create Site to Site VPN On Cisco FTD (using FDM)
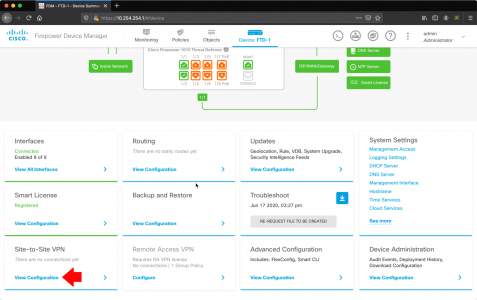
Using a web browser connect to the devices FDM > Site to Site VPN > View Configuration.
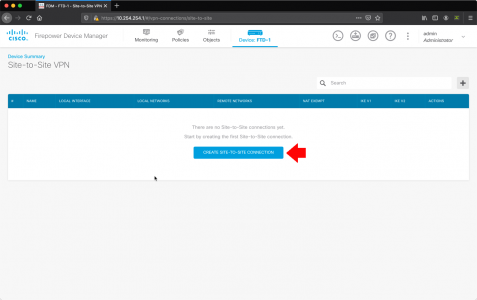
Create Site-to-site-connection.
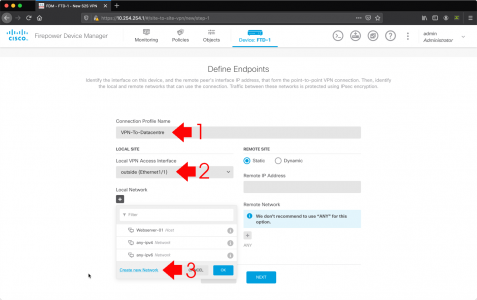
- Connection profile name: Something sensible like VPN-To-HQ or VPN-To-Datacentre.
- Local VPN Access Interface: outside.
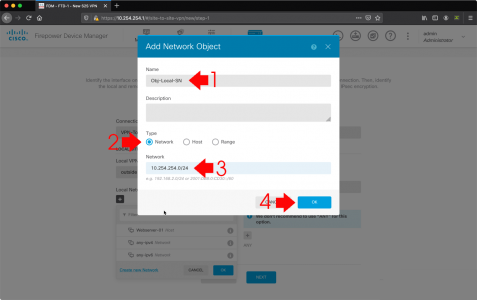
- Local Network: Crete new network.
- Name: This will be your local LAN so give it a recognisable name.
- Type: Network
- Network: Your local (behind the FTD) network i.e. 10.254.254.0/24
- OK.
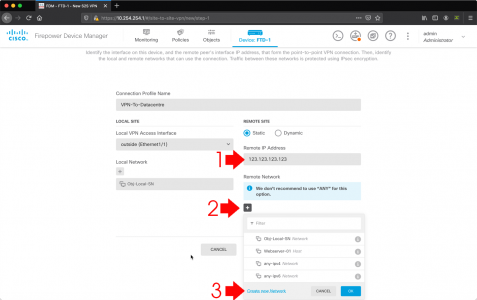
- Remote IP Address: The public IP address of the other device (in my case the Cisco ASA).
- Remote Network: Add
- Crete new network
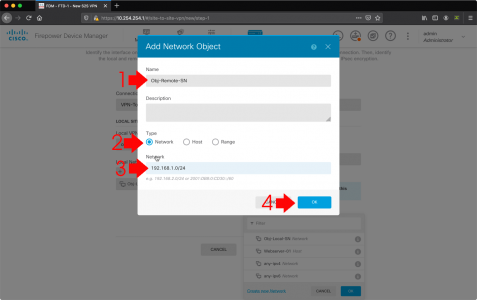
- Name: This will be the remote sites LAN so give it a recognisable name.
- Type: Network
- Network: The remote (behind the ASA) network i.e. 192.168.100.0/24
- OK.
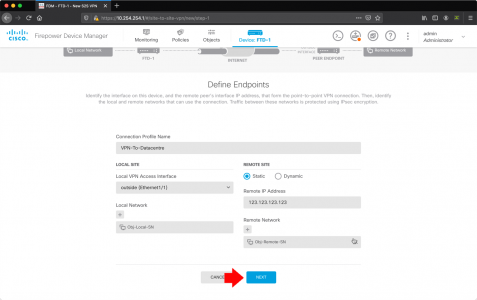
Check the settings are correct > Next.
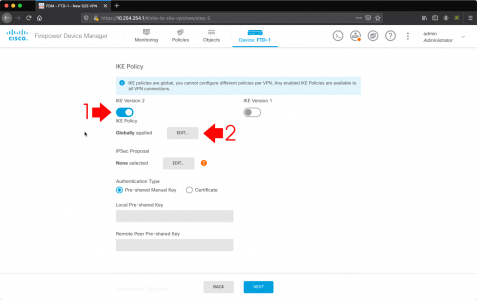
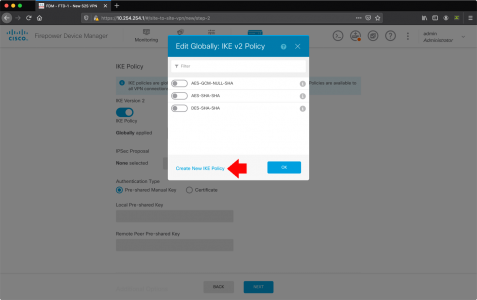
I’m using IKEv2 (if your ASA is older than version 8.4 you will need to use IKEv1) > IKE Version 2 Globally Applied > Edit.
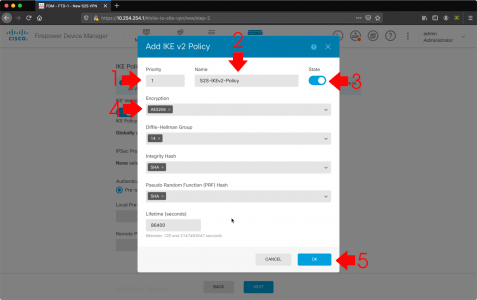
Create new IKE Policy.
- Priority: 1
- Name: S2S-IKEv2-Policy
- Encryption: DES Really! (Why is that the default?) Remove DES and replace with AES256
I leave the rest of the settings as they are some people might not like Sha1 if you want to change it to sha254 for example then do so, but remember to change it on the IKEv2 policy on the ASA also. Also DON’T CONFUSE PRF with PFS, we will get the chance to set PFS later. > OK.
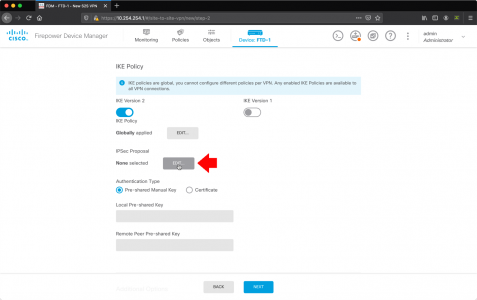
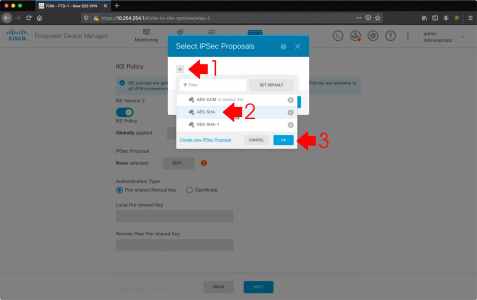
IPsec Proposal > Edit.
Add in AES-SHA > OK.
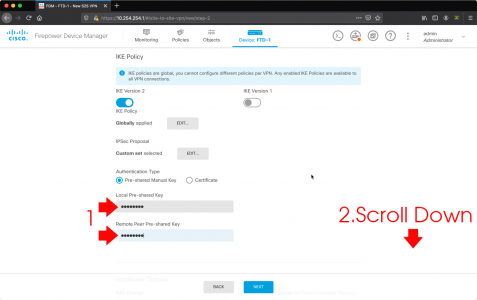
Enter (and confirm) the local and remote Pre-Shared Key (I usually set these the same, but they don’t have to be). Scroll down.
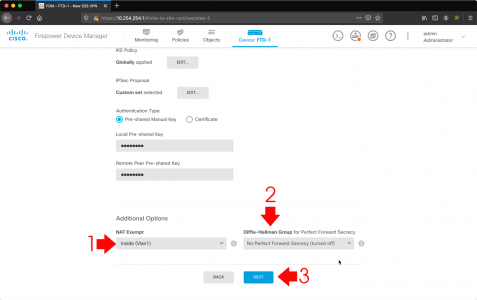
- Nat Exempt: inside
- Diffie Helman Group for Perfect Forward Secrecy (PFS): Leave disabled.
- Next
Review the settings > Finish.
FTD VPN One Way VPN Traffic Warning!
At this point if you configure the ASA, the tunnel will come up, and if you’re behind the FTD everything will work. But If you’re behind the ASA and you want to talk to anything behind the FTD, it wont work. This confused me for a while, I could ping from my house to my servers at the DC but they could not ping me!
Resolution: What you need to do is (on the FTD) ALLOW traffic ‘inbound’ on the outside interface, for the subnet behind the ASA. (Yes that’s bobbins I know, it should do that for you, but at the moment it does not).
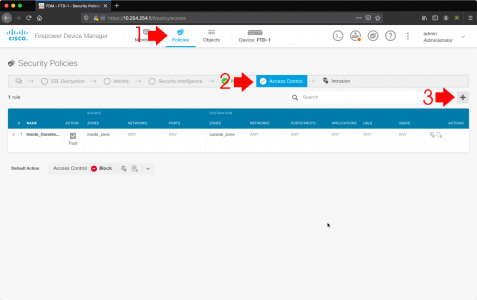
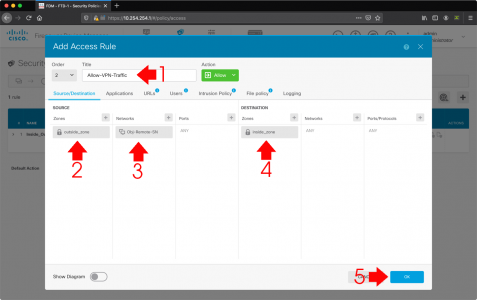
Policies > Access Control > Add.
- Title: Allow-VPN-Traffic
- Source Zone: outside_zone
- Source Networks: The Network behind the ASA
- Source Ports: ANY
- Destination Zone: inside_zone
- Destination Networks: ANY
- Destination Ports/Protocols: ANY
- OK
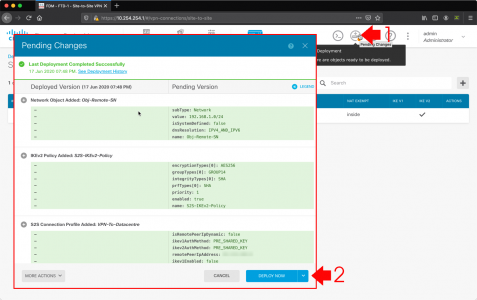
Pending changes > Deploy Now.
It can take a while to deploy, I recheck pending changes, and wait until it says it’s finished.
Create ASA Config for VPN to Cisco FTD
I’ve covered Cisco ASA IKEv2 VPN configs elsewhere, so I’ll just post the config here and you can change the details (in red) and copy and paste it into your ASA.
object network OBJ-SITE-A subnet 192.168.100.0 255.255.255.0 object network OBJ-SITE-B subnet 10.254.254.0 255.255.255.0 ! access-list VPN-INTERESTING-TRAFFIC extended permit ip object OBJ-SITE-A object OBJ-SITE-B ! nat (inside,outside) source static OBJ-SITE-A OBJ-SITE-A destination static OBJ-SITE-B OBJ-SITE-B no-proxy-arp route-lookup ! crypto ipsec ikev2 ipsec-proposal VPN-TRANSFORM protocol esp encryption aes-256 protocol esp integrity sha-1 ! crypto map CRYPTO-MAP 1 match address VPN-INTERESTING-TRAFFIC crypto map CRYPTO-MAP 1 set peer 2.2.2.2 crypto map CRYPTO-MAP 1 set ikev2 ipsec-proposal VPN-TRANSFORM crypto map CRYPTO-MAP interface outside ! crypto ikev2 policy 10 encryption aes-256 integrity sha group 14 prf sha lifetime seconds 86400 crypto ikev2 enable outside ! tunnel-group 2.2.2.2 type ipsec-l2l tunnel-group 2.2.2.2 ipsec-attributes ikev2 remote-authentication pre-shared-key cisco123 ikev2 local-authentication pre-shared-key cisco123 !
Troubleshooting and debugging FTD VPN
All the traditional command line tools we used to use for VPN troubleshooting are available to you, you will need to SSH into the ‘Management Port’ before you can use them though! Or you can simply do the debugging and troubleshooting on the ASA!
Troubleshoot phase 1 (IKE)
show crypto isa debug crypto ikev2 protocol
Troubleshoot phase 2 (IPSec)
show crypto ipsec sa debug crypto ipsec 255
Related Articles, References, Credits, or External Links
NA


29/09/2021
Hi Petenelive,
I find your site super useful for finding solutions not found elsewhere.
I am on your tutorial “Cisco FTD Site to Site VPN” and I am blocked at the level of “IKE Policy – Additional Options”. You selected “inside (Vlan1)”, but you don’t show how you created this section. Can you help me ?
Thank you so much
Hacen
29/09/2021
Hi Hacen,
Thats just my inside interface?
08/10/2021
Thanks you
04/02/2022
Pete,
As always, great and informative help guide. You’re a great resource for a newby. Thank you.
My question is this, once the Tunnel is built, is there a way to reset the tunnel through the FMC?
The ASA makes this very easy with the “Logout” option inside the Monitoring section of the ASA but the FMC doesn’t seem to have the same kind of easy. I don’t have control of the other side of the tunnel or I would do something like that in my situation. Where I only have the FMC and need to bounce or reset the tunnel I’m not finding a way to do that.
Thank you.
Dave
10/06/2022
My VPN connection is up, but for some reason, from the FTD network, I can only ping the ASA inside interface; I can’t access or ping anything but the ASA IP? From the ASA network, I can access the FTD and everything on this network?
10/06/2022
These symptoms usually indicate a NAT problem?
P
15/02/2023
Hi Pete,
is it possible to use asdm for site to site vpn on fpr1010?
i had setup one between fpr1010 and asa5506 but can’t seem to ping on either sides and if i do packettracing, the asa side worked and it brings up the tunnels but on the fpr1010, the packet tracer keeps pointing to the access list which i compared with the asa and all checked out… can you recommend something to check? i have re done the tunnels twice same issue. thank you so much.
herman
20/02/2023
>>is it possible to use asdm for site to site vpn on fpr1010?
If it’s running ASA code? – the FPR can run FDM or ASA?
05/04/2023
Pete,
Thank you for this article. You have saved me more time than I care to admit and again here you do it again. I missed one step in allowing the VPN Traffic from the outside and here you had it laid out easy to follow. Thanks for writing these guides. You are doing a good work.
Cheers.
11/10/2024
I got this setup and working. However if the connection times out, it cannot be re-established from the ASA side using a ping test. I have to do a ping test from the FTD side and it will connect right up.