KB ID 0001680
Problem
You have a Cisco FTD device that you manage via FDM, and you would like to setup port forwarding. In the example below I will forward TCP Port 80 (HTTP) traffic from the outside interface of my FTD Device (Firepower 1010) to an internal web server on 10.254.254.212
Solution (Step 1: Create an FTD NAT Policy)
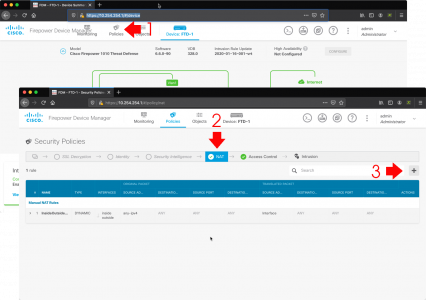
Using a web browser connect to the FDM > Polices > NAT > Add.
Set the following options;
- Title: Give the NAT rule a title e.g. Webserver-01
- Create Rule for: Manual NAT
- Status: Enable
- Placement: Above a Specific Rule
- Rule: InsideOutsideNATRule
- Type: Static
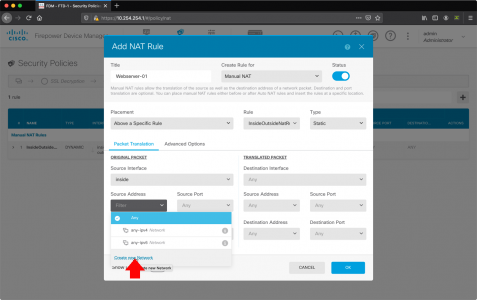
- Original Packet: Source Interface: inside
- Original Packet: Source Address: Select ‘Create New Network’
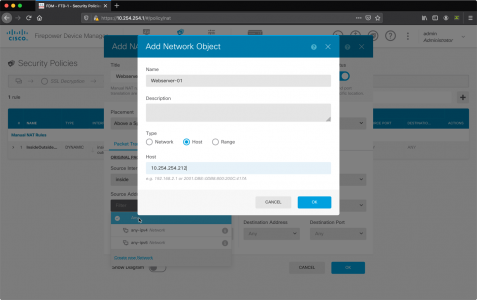
In the Add new Network Object Window;
- Name: Name of the server/object you are port forwarding to e.g. Webserver-01
- Host: IP address of the server/object you are port forwarding to
- OK
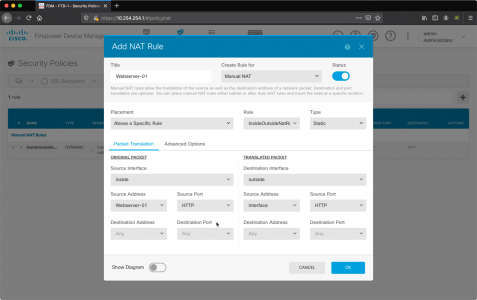
Back At the NAT Rule Window;
- Source Address: Ensure it’s set to the object you just created
- Original Packet: Source Port: HTTP (or whatever port you wish to forward)
- Translated Packet: Destination Interface: outside
- Translated PacketSource Address: Interface
- Translated Packet: Source Port:HTTP (or whatever port you wish to forward)
- OK.
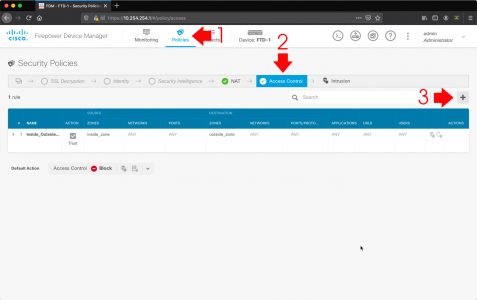
Solution (Step 2: Create an FTD Access Control Policy Rule)
Policies > Access Control > Add.
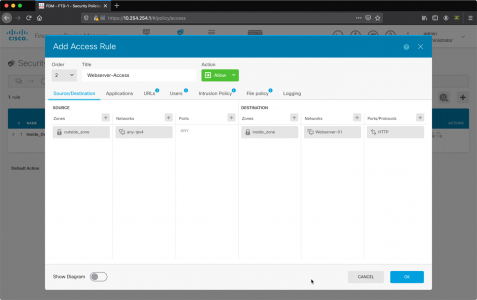
Set the access rule as follows;
- Title: Give the access rule a title e.g. Webserver-Access
- Source Zone: outside_zone
- Source Networks: any-ipv4
- Source Ports: ANY
- Destination Zone: inside_zone
- Destination Networks: The Object you created (above)
- Destination: Ports/Protocols: HTTP
- OK
You can expand the rule, and see a diagram version if you wish.
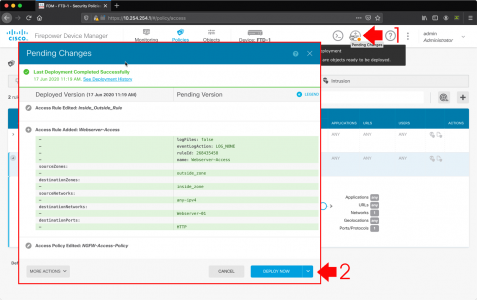
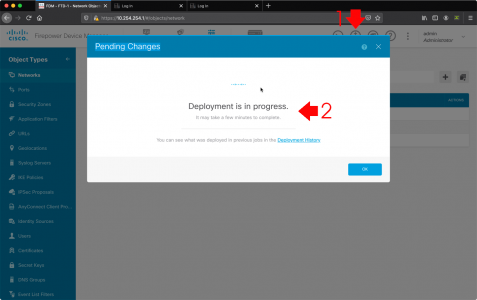
Pending Changes > Deploy Now.
Wait! The changes probably haven’t deployed yet, you can check progress by clicking the pending changes button again.
Related Articles, References, Credits, or External Links
NA


20/08/2020
Hi Pete,
I believe the NAT rule is incorrect, since you want to port forward from outside to inside, shouldn’t you invert the source and destination interface in the NAT rule ? ACL seems to go against the logic of the NAT rule …
Thank you
20/08/2020
Hi, I tested it and it worked? I’ll leave your comment, in case there is a problem.
18/02/2022
It worked because it’s precisely backwards. Instead of matching on the initial packets coming from the outside interface, which would be destined for the WAN IP of the router and have a destination port of 80 (HTTP), you are matching on the return packets of the internal destination server’s IP address which would have a source port of HTTP (80). Cisco does this in some of their documentation and it is a huge source of NAT confusion for new learners.
It would make more sense to setup the rule to match for packets coming in to the router on the outside interface (or any interface, which should also provide loopback access) destined for it’s WAN address and to a destination port, and then translate the destination address to the appropriate server on the inside interface.
10/03/2021
This is Cisco’s logic. His implementation works.
It’s whatever is going inside Cisco’s product designers that does not. My assumption is that they want to make things as complicated as possible so you can get one of their expensive contracts or hire someone with a CCNA. In any other product out in the market has a very simple interface where there is no way you can confuse this information. But that is not the case with Cisco, of course.
30/10/2020
Hello,
Many thanks for your tuto! Have you an idea on how to use another IP available on the outside interface ?
eg. :
outside : 1.1.1.1/24 (your methode use the interface IP “1.1.1.1”)
If I wan forward a port from the IP 1.1.1.2 to an inside IP ?
And for abuse a little : if you also know the method to dedicate an outside IP to an inside device.
eg. :
inside device : 2.2.2.100/22 (use the ouside IP “1.1.1.3” for any outgoing traffic)
09/09/2022
Did anyone manage to make NAT rule on other IP that WAN IP of firepower? It should be easy as chosing different object with external IP within range of WAN instead of “interface” object. Can’t get this working.
24/07/2021
What do I change if I want to take port 1225 and send it to an internal server port 225?
23/08/2022
umm this did not work for me on my cisco fdm 7.1.0.1-28, I had to do it the other way around .. If anyone else stumbles across this article, you would need to have:
Original Packet:
source interface: outside
Destination address: interface
Destination port: your port
Translated packet:
destination interface: inside
source address: interface
Destination address: inside network object
Destination port: inside port
01/11/2024
@ventura you. you are god. This config as mentioned by ventura allowed me to set up an OpenVPN server. I placed the NAT rule for allowing OpenVPN UDP port 1194 to the server running the VPN as a manual static type above auto NAT rules. where the inside network object is the OpenVPN server. Iam also using VLANs to manage security so instead of the destination interface being inside i specified my vpn vlan.
10/05/2025
I have some doubt about “source address: interface” into the translated Packet (i think should be “original” not “interface”)
22/03/2025
This is perfect solution for the problem , I spent two weeks to solve and I get this is perfect
08/04/2025
I spent a couple weeks wrestling with this because every other forum, AI (GPT & Grok) and even Cisco documentation told me to configure these rules opposite; according to logic. I’m running 7.4.2.2-28. THANK YOU!