KB ID 0001677
Problem
Sorry it’s taken me a while to get round to this, every time I do some work on the firewall I need to kill the internet at home, and I’ve got a wife and two daughters, who live online! So if you follow the site you will know I’ve got a Cisco Firepower 1010 device, and I’ve been looking at it running the ASA code.
Now here’s how to ‘re-image’ the device with the FTD (Firepower Threat Defence) operating system.
Warning this can take a while, if you are performing this in production equipment, plan in at least a couple of hours downtime.
Solution
Firstly this is a lot easier than it was on the old ASA 5500-x platform, If you have ever updated the OS on a Cisco ASA, then the process is pretty much the same.
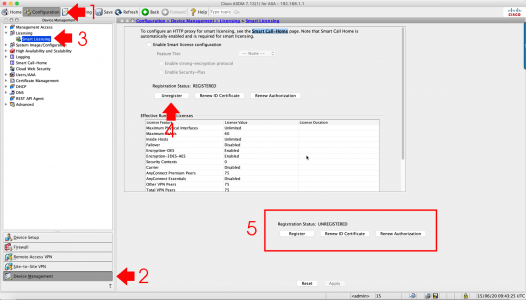
Before proceeding, you need to unregister the firewall from its Smart Licence (assuming it’s registered correctly). You can do this with the following command;
licence smart deregister
Or from the ASDM;
Then connect the firewall via console cable, I’m going to copy the operating system in from a TFTP server on my mac, (you can use FTP or HTTP if you prefer).
Petes-ASA# copy tftp flash Address or name of remote host []? 192.168.1.20 Source filename []? cisco-ftd-fp1k.6.6.0-90.SPA Destination filename [cisco-ftd-fp1k.6.6.0-90.SPA]? {Enter}
Accessing tftp://192.168.1.20/cisco-ftd-fp1k.6.6.0-90.SPA...!!!!!!!!!!!!!!!! !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! Verifying file disk0:/cisco-ftd-fp1k.6.6.0-90.SPA... Writing file disk0:/cisco-ftd-fp1k.6.6.0-90.SPA... 1097176240 bytes copied in 331.300 secs (3314731 bytes/sec) Petes-ASA#
Now we simply need to set the image as the primary boot OS.
Petes-ASA# configure terminal ciscoasa(config)# boot system disk0:/cisco-ftd-fp1k.6.6.0-90.SPA The system is currently installed with security software package 9.13.1.2, which has: - The platform version: 2.7.1.107 - The CSP (asa) version: 9.13.1.2 Preparing new image for install... !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! Image download complete (Successful unpack the image). Attention: If you proceed, the system will be re-imaged and then reboot automatically. All existing configuration will be lost and the default configuration will be applied. Installation of version 6.6.0-90 will do the following: - upgrade to the new platform version 2.8.1.105 - upgrade to the CSP FTD version 6.6.0-90 Do you want to proceed? [confirm] {Enter}
The firewall will install the new OS then reboot itself, it will take a while, be patient! Once rebooted the FTD software will ask you to login, the default username and password is admin and Admin123, upon logging in, you are asked to change the password.
firepower login: admin Password: Admin123 Successful login attempts for user 'admin' : 1 Copyright 2004-2020, Cisco and/or its affiliates. All rights reserved. Cisco is a registered trademark of Cisco Systems, Inc. All other trademarks are property of their respective owners. Cisco Fire Linux OS v6.6.0 (build 37) Cisco Firepower 1010 Threat Defense v6.6.0 (build 90) Hello admin. You must change your password. Enter new password: {new-password} Confirm new password: {new-password} Your password was updated successfully. Cisco Firepower Extensible Operating System (FX-OS) Software TAC support: http://www.cisco.com/tac Copyright (c) 2009-2019, Cisco Systems, Inc. All rights reserved. The copyrights to certain works contained in this software are owned by other third parties and used and distributed under license.
Now you can carry out an initial configuration of the Firepower.
firepower# connect ftd
Here I set the basic IPv4 settings, and tell the firewall it will be managed locally via FDM (Firepower Device Manager), that’s the web management interface on the device, rather than FMC (Firepower Management Center) a separate management appliance.
You must accept the EULA to continue.
Press to display the EULA:
End User License Agreement
Effective: May 22, 2017
This is an agreement between You and Cisco Systems, Inc. or its affiliates
("Cisco") and governs your Use of Cisco Software. "You" and "Your" means the
individual or legal entity licensing the Software under this EULA. "Use" or
"Using" means to download, install, activate, access or otherwise use the
Software. "Software" means the Cisco computer programs and any Upgrades made
PRESS THE SPACE BAR A LOT!
---------------Output removed for the sake of Brevity---------------------
mentioned are the property of their respective owners. The use of the word partner does not imply a partnership relationship between Cisco and any other company. (1110R) Please enter 'YES' or press Enter to AGREE to the EULA: YES System initialization in progress. Please stand by. You must configure the network to continue. You must configure at least one of IPv4 or IPv6. Do you want to configure IPv4? (y/n) [y]: y Do you want to configure IPv6? (y/n) [y]: n Configure IPv4 via DHCP or manually? (dhcp/manual) [manual]: {Enter} Enter an IPv4 address for the management interface []: 10.254.254.254 Enter an IPv4 netmask for the management interface []: 255.255.255.0 Enter the IPv4 default gateway for the management interface [data-interfaces]: 10.254.254.1 Enter a fully qualified hostname for this system [firepower]: FTD-1 Enter a comma-separated list of DNS servers or 'none' [208.67.222.222,208.67.220.220]: 8.8.8.8,8.8.4.4,194.168.4.100 Enter a comma-separated list of search domains or 'none' []: {Enter} If your networking information has changed, you will need to reconnect. Setting DNS servers: 8.8.8.8 8.8.4.4 194.168.4.100 No domain name specified to configure. Setting hostname as FTD-1 Setting static IPv4: 10.254.254.254 netmask: 255.255.255.0 gateway: 10.254.254.1 on management0 Updating routing tables, please wait... All configurations applied to the system. Took 3 Seconds. Saving a copy of running network configuration to local disk. For HTTP Proxy configuration, run 'configure network http-proxy' Manage the device locally? (yes/no) [yes]: {Enter} Configuring firewall mode to routed Update policy deployment information - add device configuration Successfully performed firstboot initial configuration steps for Firepower Device Manager for Firepower Threat Defense. >
At this point I reboot the unit, but be prepared, it can take a LONG time before it comes back online, (wait at least 40 minutes).
IMPORTANT you have configured the IP address on the MANAGEMENT interface (1) , to configure further, and complete the Firepower 1010 initial setup, connect to any one of the LAN interfaces (2), and navigate to https://192.168.1.1 (you should get an DHCP address, if you don’t, then you’ve not waited long enough!)
Related Articles, References, Credits, or External Links
Cisco FPR – Re-image from FTD to ASA Code


17/01/2024
great !!!!
batter than Cisco Gudie
thank you
11/03/2025
For more information about reimaging from ASA to FTD, see the video: https://youtu.be/HYKaJyJAy3E