KB ID 0001658
Problem
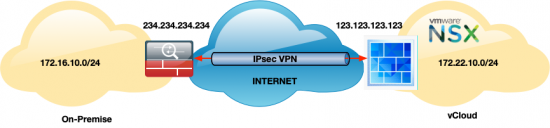
I was asked to setup a VPN to help out a colleague this week. When I had a look, one end turned out to be an Edge Gateway, I wasn’t that concerned, I’d done similar things in my prior role, I just didn’t have access to the vCloud or VMware at this datacenter.
Depite my best efforts on the ASA, the tunnel refused to come up, it took a little looking ‘under the covers’ to accurately diagnose the problem. But to save you my pain, I’ll post the setup of both ends so yours will be a little less stressful.
VMware Edge Gateway VPN Setup
Locate the Edge Gateway in vCloud Director > VPN > Create new VPN > Tick ‘Enable This VPN‘ configuration > Set the local and remote networks > Local ID is the local public IP of the Edge Gateway > Remote ID is the pubic IP of the Cisco ASA > Set the encryption protocol as AES256 > Copy the pre-shared-key (Warning: some browsers wont select all of the key, and you will end up characters short, make sure you have it all!) > OK.
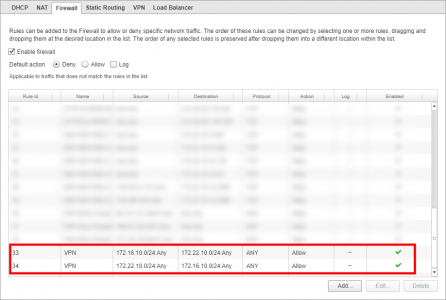
On the ‘Firewall’ Tab allow all traffic TO and FROM the remote subnet, (behind the Cisco ASA).
Note: There no need to make a NAT Exemption.
Cisco ASA VPN Setup (For Edge Gateway)
Note: The version of Edge Gateway I was using, was using (once AES256 is selected)
- IKE Version: 1
- Encryption:AES-256
- Hashing: SHA
- Diffie Hellman: Group 2
- Perfect Forward Secrecy: Enabled (group 2)
I’m aware that newer Edge Gateways support IKEv2 but debugging the incoming requests told me mine was using IKEv1.
crypto ikev1 enable outside ! crypto ikev1 policy 10 authentication pre-share encryption aes-256 hash sha group 2 lifetime 86400 ! object network OBJ-vCloud-SN subnet 172.16.10.0 255.255.255.0 object network OBJ-Site-SN subnet 172.22.10.0 255.255.255.0 ! access-list VPN-INTERESTING-TRAFFIC extended permit ip object OBJ-vCloud-SN object OBJ-Site-SN nat (inside,outside) source static OBJ-vCloud-SN OBJ-vCloud-SN destination static OBJ-Site-SN OBJ-Site-SN no-proxy-arp route-lookup ! tunnel-group 123.123.123.123 type ipsec-l2l tunnel-group 123.123.123.123 ipsec-attributes pre-shared-key gT65C9Muwjx4q73tXaxu9gge6psqyr83qcu93xL8xkdk594yzNgf4jeoj7ax85Nc isakmp keepalive threshold 10 retry 2 ! crypto ipsec ikev1 transform-set VPN-TRANSFORM esp-aes-256 esp-sha-hmac ! crypto map CRYPTO-MAP 1 match address VPN-INTERESTING-TRAFFIC crypto map CRYPTO-MAP 1 set pfs group2 crypto map CRYPTO-MAP 1 set peer 123.123.123.123 crypto map CRYPTO-MAP 1 set ikev1 transform-set VPN-TRANSFORM ! crypto map CRYPTO-MAP interface outside !
WARNING
Above assumes;
- Your interfaces are called inside, and outside.
- You DO NOT have any existing VPNs configured, (if you do, change the name of the CRYPTO-MAP (above) to match the name of your cryptomap and use a higher number, e.g. ‘outside_map 2‘).
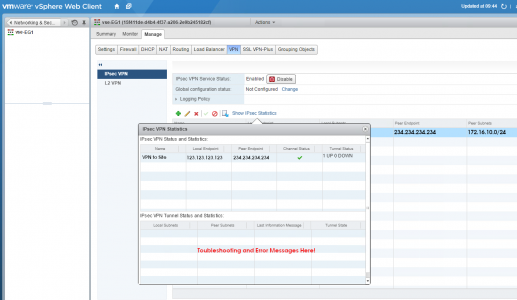
Troubleshooting Edge Gateway End of the VPN
You need access to the underlying VMware infrastructure > Select Networking and Security > Locate the NSX Edge > VPN > IPsec VPN > Show IPsec Statistics > Here you can see some meaningful error massages if theres a problem.
Troubleshooting Cisco ASA End of the VPN
I’ve covered this to death in the past, so rather than reinvent the wheel;
Troubleshooting Phase 1 Cisco Site to Site (L2L) VPN Tunnels
Troubleshooting Phase 2 Cisco Site to Site (L2L) VPN Tunnels
Related Articles, References, Credits, or External Links
NA