KB ID 0001613
Problem
This popped up in the forums last night, if you have a Workgroup*, (non domain joined) machine, the profile of the network card keeps switching from Private to Public.
*Note: A domain joined machine, automatically will set it’s network profile to ‘Domain‘.
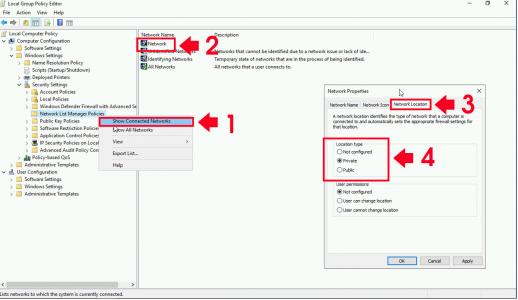
Option 1: Set the Network Profile using Local Group Policy
Hit Windows Ker + R to open Run prompt, and type gpedit.msc
Navigate to
Computer Configuration > Windows Settings > Security Setting > Network List Manager Policies
Note: To show networks currently connected, right-click Network List Manager Policies in the left pane and choose Show Connected Networks, (or all networks if it’s not currently not connected!)
Then Go to Network Location tab and change the Location type from Public to Private.
Close the policy editor and then force a policy update.
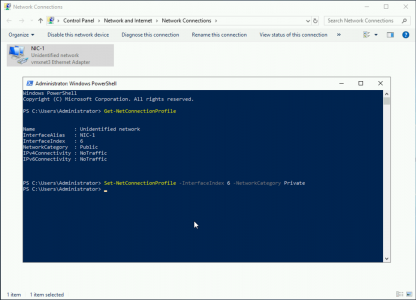
Option 2: Set the Network Profile using Powershell
Execute the following command to list the network connections;
Get-NetworkConenctionProfile
Take a note of the Interface Index (in the example below that is ‘6’. Then set the profile of that interface with the following command;
Set-NetConenctionProfile -InterfaceIndex 6 -NetworkCategory PrivateRelated Articles, References, Credits, or External Links
Credit to David Johnson for the Powershell!

13/11/2019
Excellent – thank you! Have you ever seen either the Public or Private profiles being incorrectly selected when the device should be connected to a domain?
13/11/2019
I have not? do you have evidence of this?
P
23/11/2019
Thanks very much for the reply. Sorry about my tardiness in getting back to you.
I have only seen a handful of cases – all the devices were running Windows 10 1809. All occurred on boot up. The laptops would not connect to the domain using a wired connection (the walls ports were existing ports – the patching had not changed). They were showing as connected to e.g. Network rather than the domain name. We were able to sign into the devices as a local administrator using cached credentials and were able to point them back to the domain by using this guidance we found online:
HKEY_LOCAL_MACHINE –> SOFTWARE –> Microsoft –> Windows NT –> CurrentVersion –> NetworkList –> Profiles
Find the profile using ProfileName and change the Category DWORD to 2 for Domain.
Disable and re-enable the NIC.
I have not been able to figure out what caused it.
18/11/2021
I realize this is an old thread, but I’ve been dealing with this very topic since the issue began in 2008 when Vista/Server2008 introduced Network Location Awareness (NLA).
The NLA service periodically checks to verify that the computer is still on a known, recognized network. Unfortunately, especially in virtual environments, it cannot always accurately retrieve the required information.
When it cannot, it immediately (by design) sets the involved network connection’s firewall profile type to “Public” and sets the displayed network name to Unidentified or Unknown Network. This can be seen in Server Manager or in NCPA.CPL for the connection. Server Manager will also indicate that the Firewall Profile is set to Public.
That is done because NLA’s main purpose is to ensure than any unrecognized network is secured by the firewall’s most restrictive settings–i.e. those of the Public Profile. Bouncing the involved NIC generally corrects the issue for the time being, but doesn’t not fix the problem.
Since MS is the only one who can correct NLA’s code (they’ve had 13+ years to do so, but have not), the stock solution for fixed-location, stationary computers (servers, desktop workstations, etc., that will never be visiting any public network, for instance, in a coffee shop) is to synchronize the Domain and Public firewall profiles.
This can be done manually, if you have lots of time, or it can be done quickly and easily with PowerShell (Run as Administrator) using the following command while the computer is using the Domain Profile:
Get-NetFirewallRule -Enabled True | Set-NetFirewallRule -Profile Any
If you prefer, you can replace the term ‘Any’ (which covers all firewall profiles) with preferred specific profile names, separated by commas:
Example:
Get-NetFirewallRule -Enabled True |
Set-NetFirewallRule -Profile Domain, Public
This will not stop NLA from misdiagnosing the network location, but it will keep the misdiagnosis from making any difference to anyone who isn’t IT-OCD.
Hope this helps someone.
~Mike