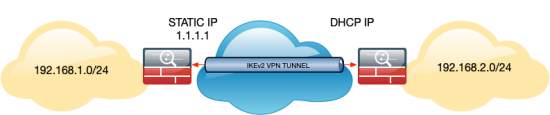
KB ID 0001602
Problem
Site to Site VPNs are easy enough, define some interesting traffic, tie that to a crypto map, that decides where to send the traffic, create some phase 1 and phase 2 policies, wrap the whole lot up in a tunnel-group, and you’re done! But there needs to be a ‘peer address‘ in the crypto map, and if one end of the VPN is on DHCP that address is likely to change, so you cant supply that?
The solution is quite simple, Cisco had to address this years ago when they had remote IPSec VPN clients, you use a Dynamic Cryptomap, and because you can’t have a tunnel group either, you use the DefaultL2LGroup, (this gets used when a specific IP address is not defined).
Note: If you have many remote sites using DHCP why not consider configuring EZVPN instead?
Static IP ASA Config
Use the following, change the values in red, to suit your own requirements;
! object network OBJ-MAIN-SITE-LAN subnet 192.168.1.0 255.255.255.0 ! object network OBJ-REMOTE-SITE-LAN subnet 192.168.2.0 255.255.255.0 ! access-list VPN-INTERESTING-TRAFFIC extended permit IP object OBJ-MAIN-SITE-LAN object OBJ-REMOTE-SITE-LAN nat (inside,outside) source static OBJ-MAIN-SITE-LAN OBJ-MAIN-SITE-LAN destination static OBJ-REMOTE-SITE-LAN OBJ-REMOTE-SITE-LAN ! crypto ipsec IKEv2 ipsec-proposal IPSEC-PROP-1 protocol esp encryption aes-256 protocol esp integrity sha-1 ! crypto dynamic-map DMAP-VPN 10 set IKEv2 ipsec-proposal IPSEC-PROP-1 crypto dynamic-map DMAP-VPN 10 set reverse-route ! crypto map outside_map 999 ipsec-isakmp dynamic DMAP-VPN crypto map outside_map interface outside ! crypto IKEv2 policy 2 encryption aes-256 integrity sha512 group 24 prf sha512 lifetime seconds 86400 ! crypto IKEv2 enable outside ! group-policy GP-SITE-2-SITE internal group-policy GP-SITE-2-SITE attributes vpn-idle-timeout none vpn-session-timeout none vpn-filter none vpn-tunnel-protocol IKEv2 tunnel-group DefaultL2LGroup general-attributes default-group-policy GP-SITE-2-SITE tunnel-group DefaultL2LGroup ipsec-attributes IKEv2 remote-authentication pre-shared-key Password123 IKEv2 local-authentication pre-shared-key Password123 !
Dynamic IP ASA Config
As above, change the values in red, to suit your own requirements, (this is essentially just a normal site to site IKEv2 config!)
! object network OBJ-REMOTE-SITE-LAN subnet 192.168.2.0 255.255.255.0 ! object network OBJ-MAIN-SITE-LAN subnet 192.168.1.0 255.255.255.0 ! access-list VPN-INTERESTING-TRAFFIC extended permit IP object OBJ-REMOTE-SITE-LAN object OBJ-MAIN-SITE-LAN nat (inside,outside) source static OBJ-REMOTE-SITE-LAN OBJ-REMOTE-SITE-LAN destination static OBJ-MAIN-SITE-LAN OBJ-MAIN-SITE-LAN ! crypto ipsec IKEv2 ipsec-proposal IPSEC-PROP-1 protocol esp encryption aes-256 protocol esp integrity sha-1 ! crypto map outside_map 1 match address VPN-INTERESTING-TRAFFIC crypto map outside_map 1 set pfs group5 crypto map outside_map 1 set peer 1.1.1.1 crypto map outside_map 1 set IKEv2 ipsec-proposal IPSEC-PROP-1 crypto map outside_map interface outside ! crypto IKEv2 policy 2 encryption aes-256 integrity sha512 group 24 prf sha512 lifetime seconds 86400 ! crypto IKEv2 enable outside ! group-policy GroupPolicy_1.1.1.1 internal group-policy GroupPolicy_1.1.1.1 attributes vpn-tunnel-protocol IKEv2 tunnel-group 1.1.1.1 type ipsec-l2l tunnel-group 1.1.1.1 general-attributes default-group-policy GroupPolicy_1.1.1.1 tunnel-group 1.1.1.1 ipsec-attributes IKEv2 remote-authentication pre-shared-key Password123 IKEv2 local-authentication pre-shared-key Password123 !
Related Articles, References, Credits, or External Links
NA