KB ID 0001593
Problem
Note: To add new subnets to a traditional Site to Site VPN, see the following article instead;
Cisco ASA – Adding New Networks to Existing VPNs
I see this get asked in online forums A LOT. If you have an existing AnyConnect VPN setup, and then need to add another network how do you do it?
Well that depends on where the new network is, and how it’s entering the firewall, these diagrams can be either way round, but the new network will either be coming into the ASA on the same interface (i.e you’ve spun up a new network for phones, or a new department etc), or the traffic will be coming into the ASA through a different interface, (like a DMZ, or partner network).
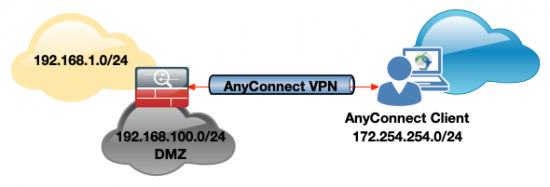
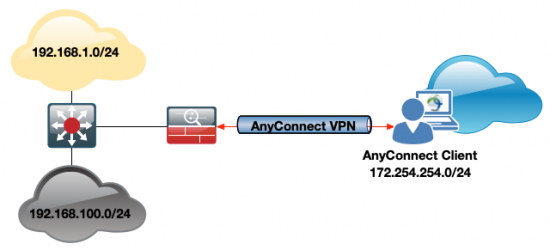
Option A: New Network is on another interface;
Option B: New Network is on existing (inside) interface;
Note: The process for adding the new network is the same for both, BUT depending on which interface the new traffic is coming in on, this will change your NAT command.
Warning: For this process to work you must already have a setup and working AnyConnect deployment!
Solution
Option A: New Network is on a Different Interface
Tasks on ASA
- Locate the NAT Exemption for the AnyConnect traffic, and add a new one on the SAME interface.
- If using Split Tunneling add the new network to the Spit Tunnel ACL
Locate the Nat Exception (or NO NAT on old Cisco Money) that prevents the AnyConnect traffic form getting NATTED.
ASA-1(config)# show run nat
nat (inside,outside) source static any any destination static Obj-ANYCONNECT-SUBNET Obj-ANYCONNECT-SUBNET no-proxy-arp route-lookup
nat (inside,outside) source static Obj-Local-LAN Obj-Local-LAN destination static Obj-Remote-LAN Obj-Remote-LAN no-proxy-arp route-lookup
!From the output above we can see that the Nat exemption for the existing traffic is highlighted, we simply need to add another one, for the new interface (which we will call dmz).
Note: I’m using any, yours might be using a specific object or object-group, if so, you will need to create new objects or object groups for the new network(s), for the next step, I’m sticking with any!
ASA-1# configure terminal ASA-1(config)# nat (dmz,outside) source static any any destination static Obj-ANYCONNECT-SUBNET Obj-ANYCONNECT-SUBNET no-proxy-arp route-lookup
Now let’s see if we are using split tunnelling;
ASA-1# show run group-policy
group-policy DfltGrpPolicy attributes
webvpn
customization value Portal
group-policy GroupPolicy_AnyConnectVPN internal
group-policy GroupPolicy_AnyConnectVPN attributes
wins-server none
dns-server value 192.168.1.10 192.168.1.11
vpn-tunnel-protocol ssl-client ssl-clientless
split-tunnel-policy tunnelspecified
split-tunnel-network-list value SplitTunneling
default-domain value petenetlive.com
webvpn
anyconnect profiles value AnyConnect type user
customization value Portal
group-policy GroupPolicy3 internal
group-policy GroupPolicy3 attributes
vpn-tunnel-protocol ikev1
group-policy GroupPolicy2 internal
group-policy GroupPolicy2 attributes
vpn-filter value ACL_Filter
vpn-tunnel-protocol ikev1
group-policy GroupPolicy1 internal
group-policy GroupPolicy1 attributes
vpn-tunnel-protocol ikev1
webvpn
customization value PulsantPortalSo we are using split tunnelling, and our split tunnel ACL is called SplitTunneling.
ASA-1# show run access-list SplitTunneling
access-list SplitTunneling standard permit 192.168.1.0 255.255.255.0Now simply just add the new subnet;
ASA-1(config)# access-list SplitTunneling standard permit 192.168.100.0 255.255.255.0Option B: New Network is on the Same Interface
Tasks on ASA
- Locate the NAT Exemption for the AnyConnect traffic, and add a new one for the new interface.
- If using Split Tunneling add the new network to the Spit Tunnel ACL
Locate the Nat Exception (or NO NAT on old Cisco Money) that prevents the AnyConnect traffic form getting NATTED.
ASA-1(config)# show run nat
nat (inside,outside) source static any any destination static Obj-ANYCONNECT-SUBNET Obj-ANYCONNECT-SUBNET no-proxy-arp route-lookup
nat (inside,outside) source static Obj-Local-LAN Obj-Local-LAN destination static Obj-Remote-LAN Obj-Remote-LAN no-proxy-arp route-lookup
!From the output above we can see that the Nat exemption for the existing traffic is highlighted, IMPORTANT: Because I’m using any, (yours might be using a specific object or object-group), I DONT NEED TO ADD ANYTHING as any covers the newly added subnet. if you didn’t use any, then you will need to create new objects or object groups for the new network(s), for the next step, I’m sticking with any! then
ASA-1# configure terminal ASA-1(config)# object network Obj-New-LAN ASA-1(config-network-object)# subnet 192.168.100 255.255.255.0 ASA-1(config-network-object)#nat (inside,outside) source static Obj-New-LAN Obj-New-LAN destination static Obj-ANYCONNECT-SUBNET Obj-ANYCONNECT-SUBNET no-proxy-arp route-lookup
Now let’s see if we are using split tunnelling;
ASA-1# show run group-policy
group-policy DfltGrpPolicy attributes
webvpn
customization value Portal
group-policy GroupPolicy_AnyConnectVPN internal
group-policy GroupPolicy_AnyConnectVPN attributes
wins-server none
dns-server value 192.168.1.10 192.168.1.11
vpn-tunnel-protocol ssl-client ssl-clientless
split-tunnel-policy tunnelspecified
split-tunnel-network-list value SplitTunneling
default-domain value petenetlive.com
webvpn
anyconnect profiles value AnyConnect type user
customization value Portal
group-policy GroupPolicy3 internal
group-policy GroupPolicy3 attributes
vpn-tunnel-protocol ikev1
group-policy GroupPolicy2 internal
group-policy GroupPolicy2 attributes
vpn-filter value ACL_Filter
vpn-tunnel-protocol ikev1
group-policy GroupPolicy1 internal
group-policy GroupPolicy1 attributes
vpn-tunnel-protocol ikev1
webvpn
customization value PulsantPortalSo we are using split tunnelling, and our split tunnel ACL is called SplitTunneling.
ASA-1# show run access-list SplitTunneling
access-list SplitTunneling standard permit 192.168.1.0 255.255.255.0Now simply just add the new subnet;
ASA-1(config)# access-list SplitTunneling standard permit 192.168.100.0 255.255.255.0Related Articles, References, Credits, or External Links
NA

24/09/2020
Hi Pete, I love your documents and they have been very helpful.
Are you able to do something similar, but…. setup the VPN on the internal network going from say an INSIDE_STAFF or INSIDE_CONTRACTORS interfaces to the DMZ interface?
The reason is that you might want to use VPN to allow ‘certain’ users to access resources in the DC i.e. databases
Thank you
Heino
28/09/2020
Not really sure what you are asking but It sounds like you want to allow specific users to specific networks? This is best achieved with DAP (Dynamic Access Policies). I’ve written this up elsewhere (use the search function). But essentially if you want bob and Steve to access the SQL server on Network x, create an ACL that allows IP from any to Network X, then create a DAP that says if you are Bob or Steve apply the ACL you just created. then the ACL gets downloaded to them dynamically.
06/02/2023
Hey Pete, this was helpful to gain access to additional subnets in the office.
Question, to take this a step further, how would you build the route so the anyconnect user could connect to a remote site in the site to site tunnel?
for example,
you have 2 sites (A & B) with a ikev2 site to site tunnel.
you have a user use anyconnect to connect to site A and he needs to hit a server in site B (within the site to site tunnel).
07/02/2023
Look at the hairpinning (Spoke to Spoke) article 🙂
18/09/2023
Hi Pete;
Thanks for this – very helpful.
I now can access servers in the DMZ from AnyConnect clients but any of these servers also can connect to the AnyConnect clients. This is not desired. Any suggestions to prevent this ? Thank you
19/09/2023
Use an ACL inbound on the DMZ interface?