KB ID 0001490
Problem
I’m seeing more and more people asking questions in forums about FTD, so I thought it was about time I looked at it. Cisco ASA 5500-X firewalls can now be re-imaged to run the FTD software. The thinking is that the FTD will merge the Cisco ASA product and the FirePOWER product into one unified operating system. Then that is managed by FDM (FirePOWER Device Manager), basically a web management GUI.
Solution
Warning; Take a full backup of the ASA config, and save a copy of the activation key! (If you ever want to re-image it back to normal ASA code you will need these!)
The re-imaging is done in ROMMON, so before you start you need to ensure your ROMMON is 1.1.8 or newer. You can get that information with a show module command;
Petes-ASA# show module
Mod Card Type Model Serial No.
---- -------------------------------------------- ------------------ -----------
1 ASA 5506-X with FirePOWER services, 8GE, AC, ASA5506 JAD2143XXXX
sfr FirePOWER Services Software Module ASA5506 JAD2143XXXX
Mod MAC Address Range Hw Version Fw Version Sw Version
---- --------------------------------- ------------ ------------ ---------------
1 6cb2.aede.0106 to 6cb2.aede.010f 2.0 1.1.8 9.8(1)
sfr 6cb2.aede.0105 to 6cb2.aede.0105 N/A N/A 6.2.0-362
Mod SSM Application Name Status SSM Application Version
---- ------------------------------ ---------------- --------------------------
sfr ASA FirePOWER Up 6.2.0-362
Mod Status Data Plane Status Compatibility
---- ------------------ --------------------- -------------
1 Up Sys Not Applicable
sfr Up Up
Petes-ASA#
What if yours isn’t?
Don’t panic! Download the firmware upgrade from Cisco, pop it in a TFTP server, and load it into the firewall, then run the upgrade, with the following two commands;
copy tftp://{IP-Of-TFTP-Server}/asa5500-firmware-1108.SPA disk0:asa5500-firmware-1108.SPA
upgrade rommon disk0:/asa5500-firmware-1108.SPA
Download FTD Software
You need two pieces of software, a boot image (.pkg), and an install package. (.lbff).
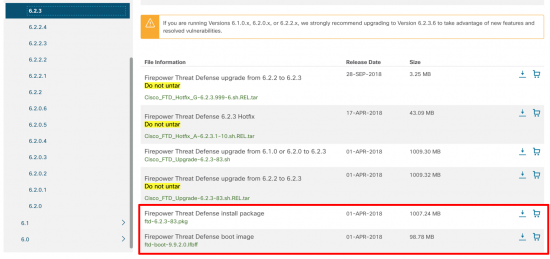
Note: You can install the boot image via TFTP but the main package needs to be deployed to the firewall via HTTP, FTP, or HTTPS
Boot the ASA into ROMMON
Power cycle the firewall and with a console cable attached press Esc when prompted, this will drop you into ROMMON mode.
Cisco Systems ROMMON, Version 1.1.8, RELEASE SOFTWARE Copyright (c) 1994-2015 by Cisco Systems, Inc. Compiled Thu 06/18/2015 12:15:56.43 by builders Current image running: Boot ROM0 Last reset cause: PowerOn DIMM Slot 0 : Present Platform ASA5506 with 4096 Mbytes of main memory MAC Address: 6c:b2:ae:de:01:06 Use BREAK or ESC to interrupt boot. Use SPACE to begin boot immediately. Boot interrupted. rommon 1 >
Set the ASA FTD Boot Image
As mentioned above I’m doing this via TFTP, on the Asa 5506-x (all variants), 5508-X, and 5526-X you need to connect the Management interface to the network with the TFTP server. For the target ASA firewalls you can specify which interface you are using like so (“rommon #1> interface gigabitethernet0/0″).
Set the basic networking requirements, specify the boot file, then use the ‘set‘ command to view the settings, and ‘sync‘ to commit that to memory. It’s also a good idea to make are you can ping the TFTP server, (Windows firewall off first though!)
rommon 1 > address 10.254.254.99 rommon 2 > netmask 255.255.255.0 rommon 3 > server 10.254.254.112 rommon 4 > gateway 10.254.254.112 rommon 5 > file ftd-boot-9.9.2.0.lfbff rommon 6 > set ADDRESS=10.254.254.99 NETMASK=255.255.255.0 GATEWAY=10.254.254.112 SERVER=10.254.254.112 IMAGE=ftd-boot-9.9.2.0.lfbff CONFIG= PS1="rommon ! > " rommon 6 > sync rommon 7 > ping 10.254.254.112 Sending 10, 32-byte ICMP Echoes to 10.254.254.112 timeout is 4 seconds !!!!!!!!!! Success rate is 100 percent (10/10)
Execute the download/install of the boot image, (tftpdnld command);
rommon 12 > tftpdnld
ADDRESS: 10.254.254.99
NETMASK: 255.255.255.0
GATEWAY: 10.254.254.112
SERVER: 10.254.254.112
IMAGE: ftd-boot-9.9.2.0.lfbff
MACADDR: 6c:b2:ae:de:01:06
VERBOSITY: Progress
RETRY: 40
PKTTIMEOUT: 7200
BLKSIZE: 1460
CHECKSUM: Yes
PORT: GbE/1
PHYMODE: Auto Detect
Receiving ftd-boot-9.9.2.0.lfbff from 10.254.254.112!!!!!!!!!!!!!!!!!!!!!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
File reception completed.
Boot buffer bigbuf=348bd018
Boot image size = 103582240 (0x62c8a20) bytes
[image size] 103582240
[MD5 signaure] ea7d29ce6fb200a9a9be486e37c78136
LFBFF signature verified.
INIT: version 2.88 booting
Starting udev
Configuring network interfaces... done.
Populating dev cache
Detected PID ASA5506.
Found device serial number JAD2143XXXX.
Found USB flash drive /dev/sdb
Found hard drive(s): /dev/sda
fsck from util-linux 2.23.2
dosfsck 2.11, 12 Mar 2005, FAT32, LFN
There are differences between boot sector and its backup.
Differences: (offset:original/backup)
65:01/00
Not automatically fixing this.
/dev/sdb1: 53 files, 819023/1919830 clusters
Launching boot CLI ...
Configuring network interface using DHCP
Bringing up network interface.
Depending on your network, this might take a couple of minutes when using DHCP...
ifup: interface lo already configured
Using IPv4 address: 10.254.254.114
Using IPv6 address: fe80::6eb2:aeff:fede:105
Using DNS server: 8.8.8.8
Using DNS server: 8.8.4.4
Using default gateway: 10.254.254.1
INIT: Starting system message bus: dbus.
Starting OpenBSD Secure Shell server: sshd
generating ssh RSA key...
generating ssh ECDSA key...
generating ssh DSA key...
done.
Starting Advanced Configuration and Power Interface daemon: acpid.
acpid: starting up
acpid: 1 rule loaded
acpid: waiting for events: event logging is off
Starting ntpd: done
Starting syslog-ng:.
Starting crond: OK
Cisco FTD Boot 6.0.0 (9.9.2.)
Type ? for list of commands
ciscoasa-boot>
Now give the FTD some basic settings, you don’t actually have to give it an IP at this point. Obviously in a production environment, you would use your internal DNS and domain details .
ciscoasa-boot>setup Welcome to Cisco FTD Setup [hit Ctrl-C to abort] Default values are inside [] Enter a hostname [ciscoasa]: Petes-ASA Do you want to configure IPv4 address on management interface?(y/n) [Y]: N Do you want to configure static IPv6 address on management interface?(y/n) [N]: N Enter the primary DNS server IP address [8.8.8.8]: {Enter} Do you want to configure Secondary DNS Server? (y/n) [y]: Y Enter the secondary DNS server IP address [8.8.4.4]:{Enter} Do you want to configure Local Domain Name? (y/n) [n]: N Do you want to configure Search domains? (y/n) [n]:N Do you want to enable the NTP service? [Y]:Y Enter the NTP servers separated by commas: 194.35.252.7,130.88.202.49,93.93.131.118 Please review the final configuration: Hostname: Petes-ASA Management Interface Configuration IPv6 Configuration: Stateless autoconfiguration DNS Configuration: DNS Server: 8.8.8.8 8.8.4.4 NTP configuration: 194.35.252.7 130.88.202.49 93.93.131.118 CAUTION: You have selected IPv6 stateless autoconfiguration, which assigns a global address based on network prefix and a device identifier. Although this address is unlikely to change, if it does change, the system will stop functioning correctly. We suggest you use static addressing instead. Apply the changes?(y,n) [Y]: Y Configuration saved successfully! Applying... Restarting network services... Done. Press ENTER to continue...
This is the point where you need the main package file on either an http, https, or ftp site. I have a web server so that’s what I use. Note: This takes a while, best go get a coffee!
ciscoasa-boot>system install http://{IP-OF-SERVER}/ftd-6.2.3-83.pkg ######################## WARNING ############################ # The content of disk0: will be erased during installation! # ############################################################# Do you want to continue? [y/N] Y Erasing disk0 ... Extracting ... Verifying Downloading Extracting Package Detail Description: Cisco ASA-FTD 6.2.3-83 System Install Requires reboot: Yes Do you want to continue with upgrade? [y]: Y Warning: Please do not interrupt the process or turn off the system. Doing so might leave system in unusable state. Starting upgrade process ... Populating new system image Reboot is required to complete the upgrade. Press 'Enter' to reboot the system.
Well, it’s telling us to reboot so let’s do so! After its backup you can login and specify the correct settings for the FTD/Management Interface. (Note the FTD Default username and password!)
Cisco ASA5506-X Threat Defense v6.2.3 (build 83) firepower login: admin Password: Admin123 Copyright 2004-2018, Cisco and/or its affiliates. All rights reserved. Cisco is a registered trademark of Cisco Systems, Inc. All other trademarks are property of their respective owners. Cisco Fire Linux OS v6.2.3 (build 13) Cisco ASA5506-X Threat Defense v6.2.3 (build 83) You must accept the EULA to continue. Press to display the EULA: {Enter} End User License Agreement Effective: May 22, 2017 This is an agreement between You and Cisco Systems, Inc. or its affiliates ("Cisco") and governs your Use of Cisco Software. "You" and "Your" means the <-------Output omitted - For the sake of Brevity --------> partner does not imply a partnership relationship between Cisco and any other company. (1110R) Please enter 'YES' or press to AGREE to the EULA: {Enter} System initialization in progress. Please stand by. You must change the password for 'admin' to continue. Enter new password: Password123 Confirm new password: Password123 You must configure the network to continue. You must configure at least one of IPv4 or IPv6. Do you want to configure IPv4? (y/n) [y]: Y Do you want to configure IPv6? (y/n) [n]: N Configure IPv4 via DHCP or manually? (dhcp/manual) [manual]:{Enter} Enter an IPv4 address for the management interface [192.168.45.45]: 10.254.254.253 Enter an IPv4 netmask for the management interface [255.255.255.0]:{Enter} Enter the IPv4 default gateway for the management interface [data-interfaces]: 10.254.254.254 Enter a fully qualified hostname for this system [firepower]: PNL-FirePOWER Enter a comma-separated list of DNS servers or 'none' [208.67.222.222,208.67.220.220]: 8.8.8.8,8.8.4.4 Enter a comma-separated list of search domains or 'none' []:{Enter} If your networking information has changed, you will need to reconnect. DHCP Server Disabled The DHCP server has been disabled. You may re-enable with configure network ipv4 dhcp-server-enable For HTTP Proxy configuration, run 'configure network http-proxy' Manage the device locally? (yes/no) [yes]: yes Configuring firewall mode to routed Update policy deployment information - add device configuration Successfully performed firstboot initial configuration steps for Firepower Device Manager for Firepower Threat Defense.
That’s us done for the conversion! You can now connect the the firewall with a web browser, (remember you just changed the password!)
Related Articles, References, Credits, or External Links
NA

09/11/2018
Hi Pete,
Great and useful post as usual mate.
You note “This is the point where you need the mail package file”. I think you meant some word other than “mail” there.
10/11/2018
Cheers Marvin (always a pleasure) – Typo fixed! (All the best techies can’t type).
15/11/2018
But should you do this is the question. Is the maturity of FTD at the level where it replaces reliably all major feature of legacy ASA code?
I haven’t personally used FTD yet in production but saw many complaints about the product. Slow upgrades are the most common issue reported. Upgrading legacy ASA code was 10-20 minute process. How long is that process with FTD?
16/11/2018
Honest answer, “No FTD is terrible” (if you are proficient with a Cisco firewall), I would NEVER think of putting one in production, my support team would have my head!
28/08/2019
if you dont specify ip address of management server during setup how does your tftp server or http server/ftp server send the image to the ASA FTD. Does it retain its original inside ip address?
Also, how is the conversion process different if you are managing the ASA 5506 Firepower through FMC?
28/08/2019
Without a server address the whole process won’t work, this is the SAME process for imaging any ASA that either does not have an operating system, or cannot boot from a corrupt one. ROMMON needs the Tftp server address or the process will fail.
28/08/2019
How long will the conversion take. What about the ASA Config, and Firepower Policies, do those get merged too, or do you have to reconfigure from scratch.
28/08/2019
Everything will get wiped so take a copy of your ASA activation code in case you ever want to revert back again (show version). Takes about 40 minutes or so.
P
10/12/2020
PeteLong, you mentioned in a comment a few years ago that FTD was terrible and you’d never put them in production. What about now? I’m considering converting our ASAs /w FirePower Services to FTDs because of the enhanced inoperability with SecureX. Also, is it possible to do this conversion WITHOUT Rommon? It will be difficult to get a console connection set up to some of my remote sites.
11/12/2020
Still I’m not sold, My firm consider them so bad that for now if clients insist on Cisco we sell the FPR firewall models (running ASA code). For everyone else, we will mov them to Fortigate.
06/07/2023
perfect guide. thank you