KB ID 0001305
Problem
I’ve not used ADMT for ages, I’ve got a domain migration to do soon, so I thought I’d get on the bench and have a reminder. Although ADMT 3.2 was ‘re-jigged’ to support Server 2012 R2, I’m still going to install it on Server 2008 R2. I’ve got a test domain built to migrate from, and a new domain setup ready to migrate into.
- Old/Source Domain: olddomain.com
- Old/Source Domain Controller: Source-DC.olddomain.com
- New/Target Domain: newdomain.com
- New/Target Domain Controller: Target-DC.newdomain.com
Solution
ADMT – DNS Setup
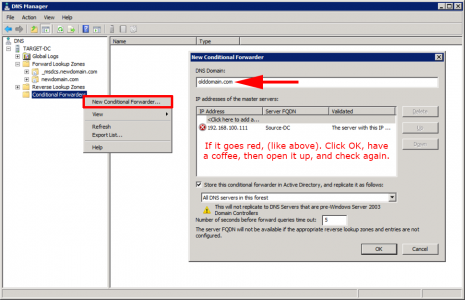
The old domain needs to be able to resolve names in the new domain, and the new domain needs to be able to resolve names in the old domain. To achieve this you need to setup ‘Conditional Forwarding’ in each domain for the other one.
Don’t worry if it looks like there’s a problem as long as the DNS servers can se each other, (and there’s no firewall in-between blocking TCP and UDP port 53). Just add in the DNS server give it a while then re-open the forwarders settings and it should have ‘gone-green’.
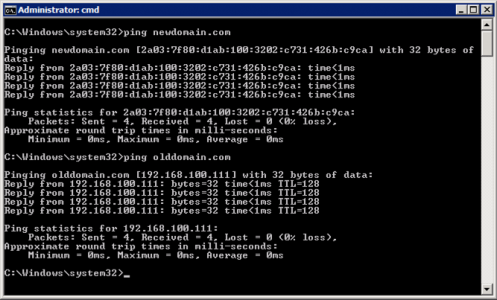
You can test it’s working by pinging BOTH the old and new domain names, in BOTH domains.
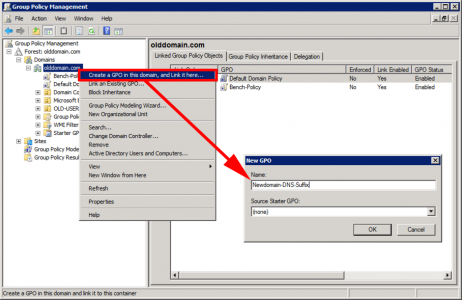
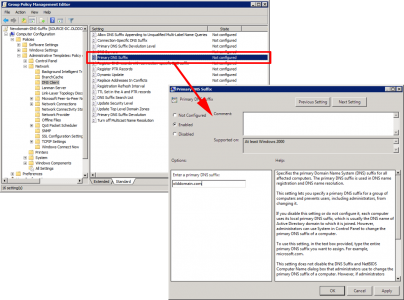
In addition, we want all machines (in both domains) to set their primary DNS Suffix, to their own domain, and their DNS suffix search list to look for their own domain first, then the other domain. The easiest way to do that is via group policy. On a domain controller > Administrative Tools > Group Policy Management Console.
It’s better practice to ‘link’ your policy to the actual OU that your computers are in, to keep things simple, (and because I’m lazy) I’m going to link my policy to the root of the domain.
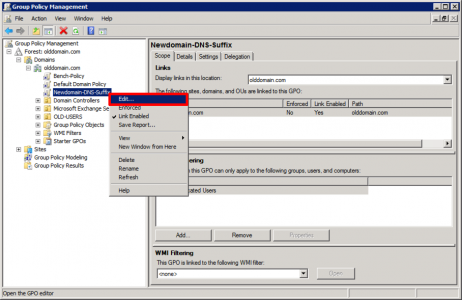
Edit the policy you have just created.
Navigate to;
Setting: Primary DNS Suffix: Set to current domain.
Setting: DNS Suffix Search List: Set to current domain ‘comma‘ other domain.
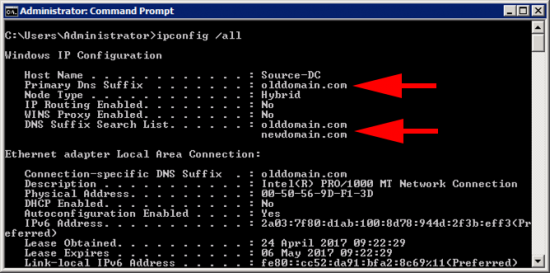
Then wait or Force a Group Policy Update, to test visit a machine and issue an ‘ipconfig /all‘ command;
Above: you can see both the policies have taken effect.
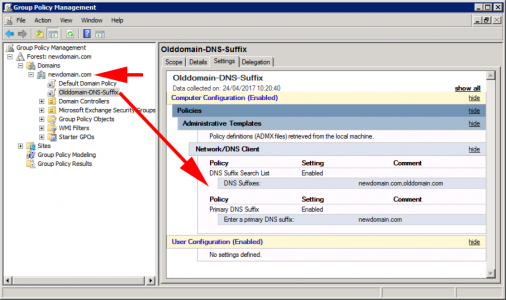
Repeat the procedure in the new domain, (but the domain names will be the opposite way round) like so;
ADMT – Creating Domain Trust
Both domains need to trust each other for the migration to take place. If you have two simple domains like I do a “two way domain trust” is fine. You would only need a ‘forest-trust‘ if you were migrating from/to root and sub domains for example.
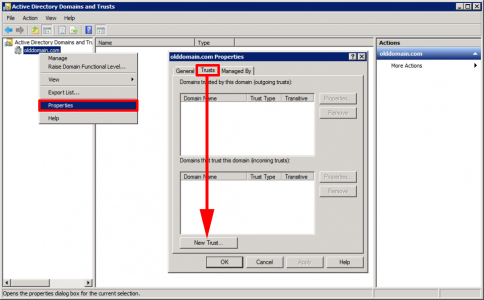
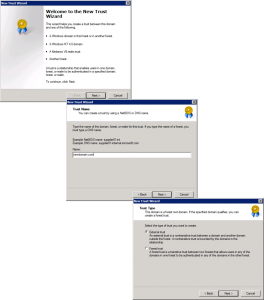
As the name implies Trusts are setup from Administrative tools > Active Directory Domains and Trusts. You can setup the whole thing from one domain, below I’m creating it in the old domain.
Welcome Screen = Next > Provide the name to the ‘other’ domain > Next > External Trust > Next.
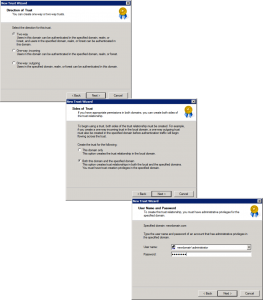
Two Way > Next > Both this domain and the specified domain > Next > Provide administrative credentials for the ‘other’ domain > Next.
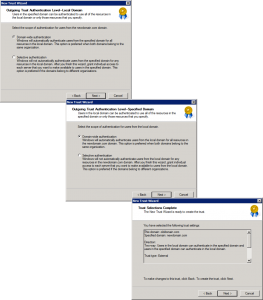
Domain wide authentication > Next > Domain wide authentication > Next > Next.
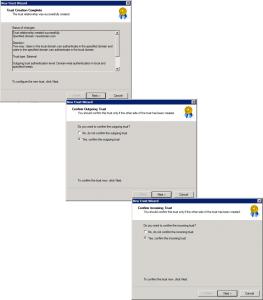
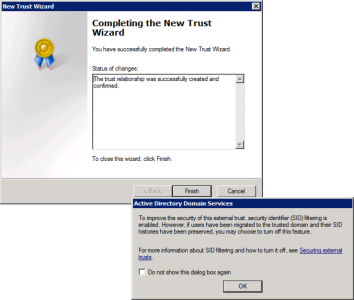
Next > Yes. Confirm outgoing trust > Next > Yes. Confirm incoming trust > Next.
Finish > READ the warning about SID history, we will have to mess about with SID History filtering a bit further on > OK.
This step is not really necessary, (it’s just for peace of mind). I do this in BOTH domains and validate each trust, (so you will do this four times).
Select the trust > Properties > Validate > Type in credentials > OK > Type in Credentials > OK > OK.
ADMT – Users / Admins and Rights Assignment
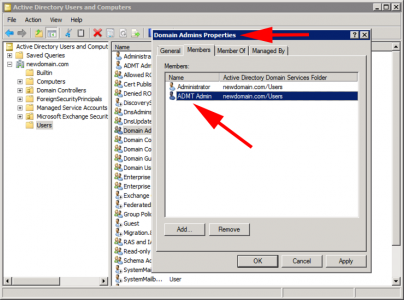
Create the user that will do all the hard work in the NEW domain. Then add that user to the domain admins group (again in the NEW domain).
Username: ADMTAdmin (Can be anything you want, but I’ll refer to this username throughout).
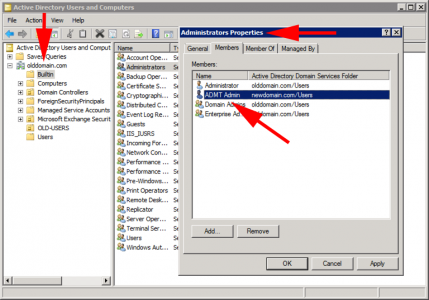
Over in the OLD domain, you won’t be able to add your ADMT user into the domain admins group, you need to add the ADMTAdmin account from the NEW domain into the Builtin\Administrators group on the OLD domain.
Additionally: the ADMTAdmin user needs to have local administrative rights to all the machines in the OLD domain. The easiest way to do that is again with a group policy.
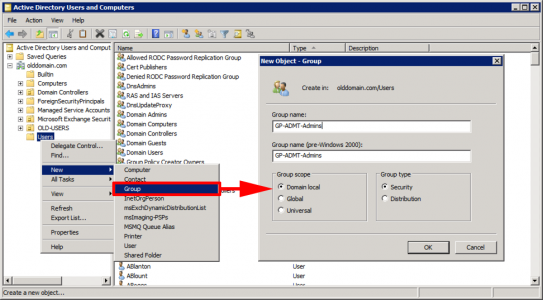
In the OLD domain create a group, (Type: Domain Local)
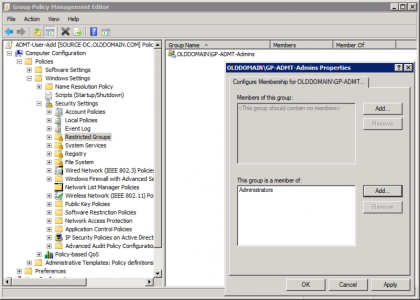
Group Name: GP-ADMT-Admins, (again you can call it something else if you want).
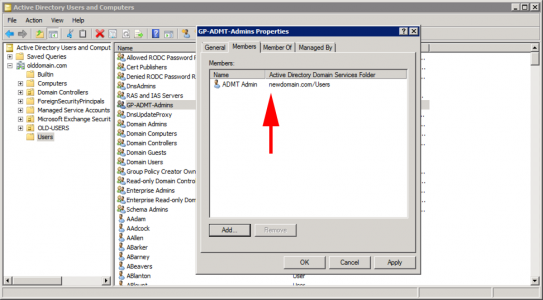
Add your ADMTAdmin account to this group, (Note: I like to add the domain admin account for the NEW domain as well, though that’s not necessary).
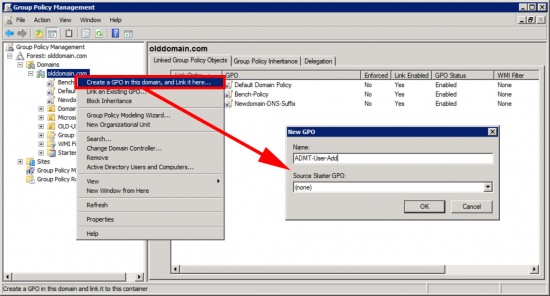
On a domain controller > Administrative Tools > Group Policy Management Console.
Once Again: It’s better practice to ‘link’ your policy to the actual OU that your computers are in, to keep things simple, (and because I’m lazy) I’m going to link my policy to the root of the domain.
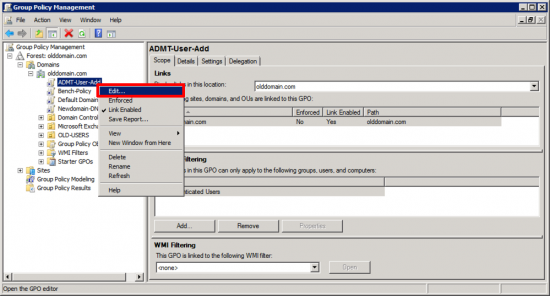
Edit the policy you have just created;
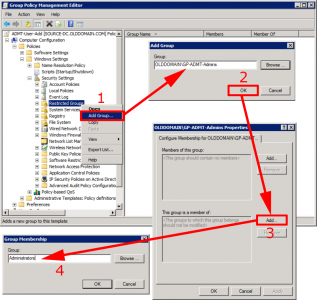
Navigate to;
Add Group > Select GP-ADMT-Admins > OK > Add (bottom option) > Administrators > OK.
Setup correctly it should look like this;
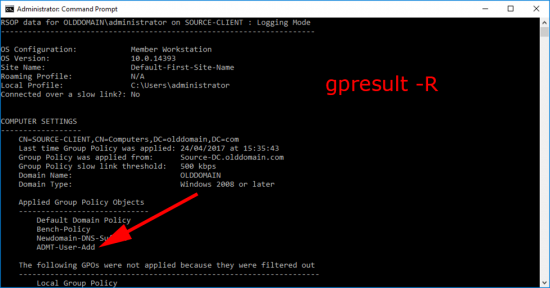
To Test: On a client Open an administrative command window > and run ‘gpresult-R’.
Or the best test is, make sure that the GP-ADMT-Admins group is actually in the local admins group.
ADMT – Database Requirements
OK, a lot of posts say don’t install ADMT/SQL on a domain controller. That’s not strictly true, you can install ADMT and SQL on a domain controller, in fact that’s what Im going to do (there are a few commands and extra steps that I will point out below).
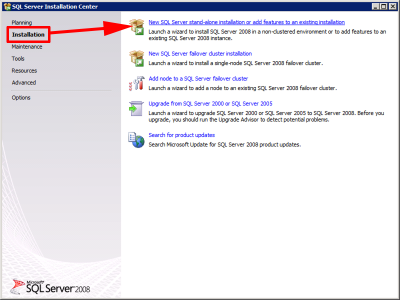
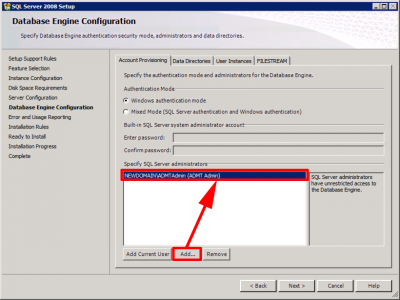
You can you use full blown SQL if you like, but it’s just as easy to use SQL Express 2008 SP1 > Download and run > Instalation > New SQL Server stand-alone installation or add features to an existing installation.
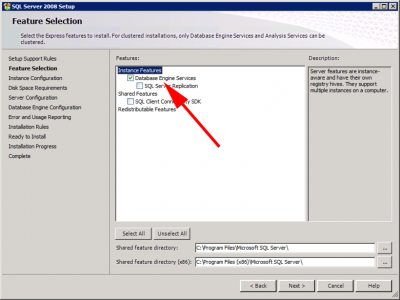
Accept the defaults > In feature Installation select ‘Database Engine Services’.
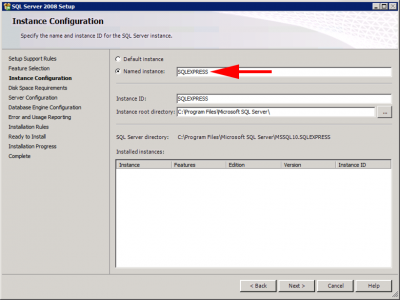
Accept the named instance ‘SQLExpress’.
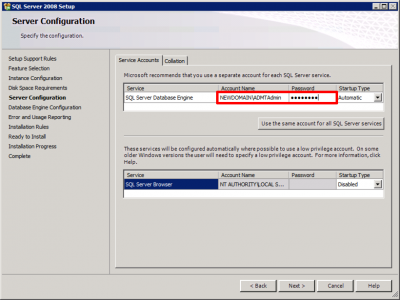
Keep accepting defaults until you get to ‘Server configuration‘ page, add in the ADMTAdmin account.
Then add in your ADMTAdmin account again. (Once again theres nothing wrong with adding the domain admin account as well).
ADMT – Additional SQL Steps For Domain Controllers
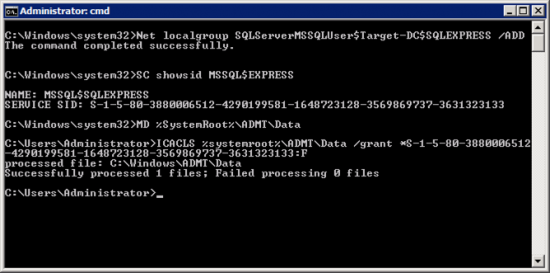
Open an administrative command window > and run the following commands;
NET LOCALGROUP SQLServerMSSQLUser$Target-DC$SQLEXPRESS /ADD SC SHOWSID MSSQL$SQLEXPRESS {Copy the SID to the clipboard you will need it in a minute} MD %SystemRoot%\ADMT\Data ICACLS %Systemroot%\ADMT\Data /grant *{Paste the SID from above}:F i.e. ICACLS %systemroot%\ADMT\Data /grant *S-1-5-80-3880006512-4290199581-1648723128-3569869737-3631323133:F
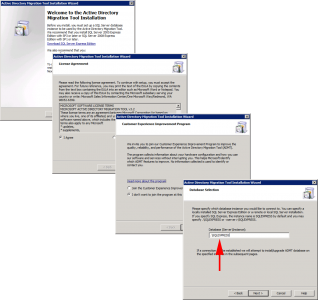
ADMT – Downloading and Installing ADMT
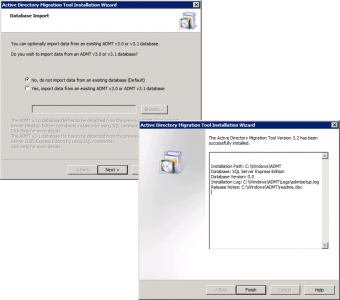
Download the ADMT software, if that link ever dies use this one. Download ADMT 3.2. Launch the installer and accept all the defaults until you get to database selection, use .SQLEXPRESS
No we don’t want to import and data from an existing database > Next > Finish.
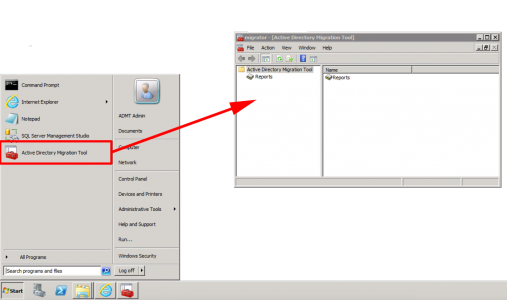
We can now open the ‘Active Directory Migration Tool’ management console.
In Part Two we will look at SID filtering, setup a password export server, and do some group policy work.
Related Articles, References, Credits, or External Links
NA




02/10/2017
“ifconfig /all” your showing your POSIX roots, Pete…shouldn’t that be ipconfig /all?
03/10/2017
Ha too many skills sets! Cheers!
14/12/2017
Where should ADMT be installed? In the source or the target domain?
14/12/2017
Target Domain 🙂
21/12/2017
Thank you 🙂
19/07/2018
Great tutorial, but I would rather deploy the ADMT_Admin User via GPP local users and groups, cause there you have the chance to just update the local group, Restricted Groups overwrite the current settings.
Cheers for this blog 🙂
14/12/2018
Hello,
Thanks a lot for you nice Howto 🙂
In my case the force Primary DNS Suffix on on SOURCE domain was not a good idea.
When I removed it, the migration worked. (I still forced it on target domain)
Before that I had a computer without trust relationship. SPN was empty in the target computer account and I had errors like “the name or security id sid of domain specified is inconsistent with the trust” when trying to login.
And “ERR2:7711 Unable to retrieve the DNS hostname for the migrated computer The ADSI property cannot be found in the property cache.” in the ADMT log.
Now it works 🙂
Kind regards Christian
21/09/2021
I’ve got a scenario where an external trust is configured and we’re scripting out the migration with ADMT. However, when triggering the migration. It fails stating the source domain functional level isn’t supported, which it is. The GUI migrates fine. Thoughts on what could be triggering this?
21/09/2021
Remember it’s a cranky old (server 2008) based tool, there will be something in there that’s broken and stopping you, and it probably wont get fixed! Sorry that’s not much help 🙁
22/09/2021
I used the SQLEXPRESS instance as described. A backwards / in the instruction hung me up for a few minutes. Just an FYI
“se ./SQLEXPRESS” should be .SQLEXPRESS
Thanks for all you do!
23/04/2024
Awesome tutorial, thanks so much for this …