KB ID 0001244
Problem
This is pretty much PART TWO of two posts addressing the need to migrate away from SHA1 before February 2017. Back in PART ONE we looked at how to upgrade the ROOT CA. It does not matter if it’s an offline or online root CA the process is the same. In many organisations their PKI is multi tiered, they either have a RootCA <> SubCA, or a ROOTCA <> IntermediateCA <> IssuingCA. (which is actually two SubCA’s).
Below I’ll run though the process to upgrade the SubCA once the RootCA has already been done, Ill also look at how that’s going to affect things like NDES (Network Device Enrolment System).
Solution
Before we think about SubCA’s the RootCA needs to be upgraded first, if it’s offline bring it online and follow the steps outlined in the previous article.
Certificate Services – Migrate from SHA1 to SHA2 (SHA256)
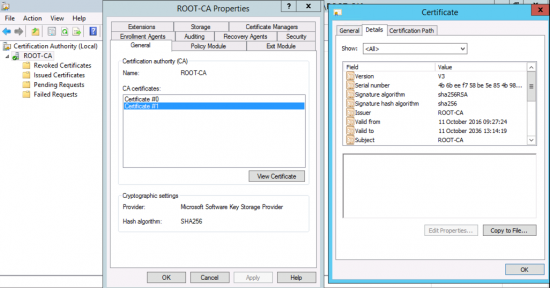
So your RootCA will now look like this before we start;
Note: If it’s normally offline leave it on, (we need it to issue the SubCA certificate).
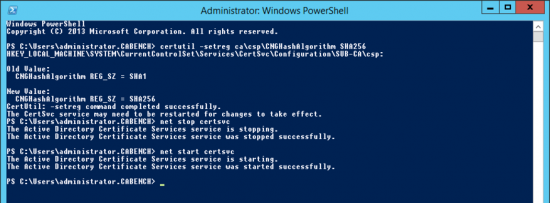
The command to change the CA from SHA1 to SHA256 is the same one we used on the RootCA, you will then need to restart the Certificate Services.
certutil -setreg ca\csp\CNGHashAlgorithm SHA256 net stop certsvc net start certsvc
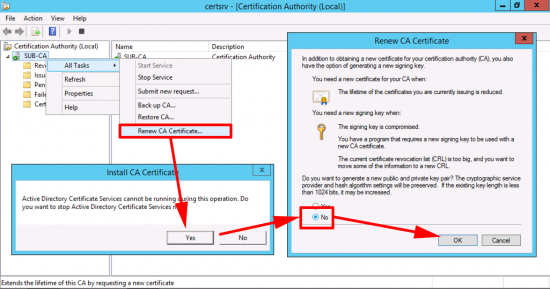
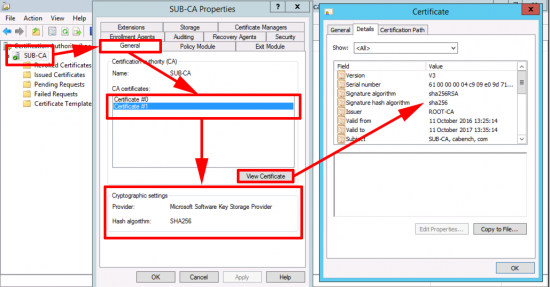
As with the RootCA, we need to re-generate the CA certificate.
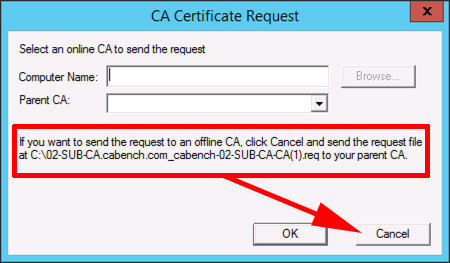
If your RootCA is online, and an Enterprise CA, you can submit the request directly to it, and skip the next few steps, but let’s take the ‘worst case’ scenario, and assume our Root CA is offline, (and even when online has no network connections) we have to do the submission manually, (via floppy disk).
Floppy Disks? What Year Is This? Well moving files between virtual machines is simple using virtual floppy disks, if you have physical machines, then you need to go hunting in drawers and cupboards!
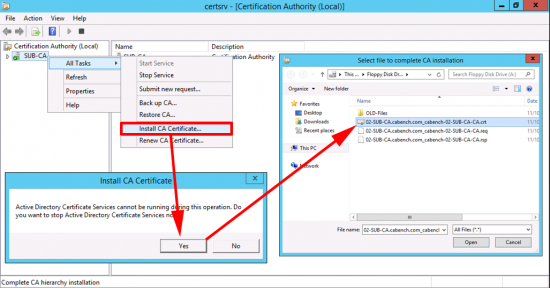
Either way, we are doing this manually so select CANCEL.
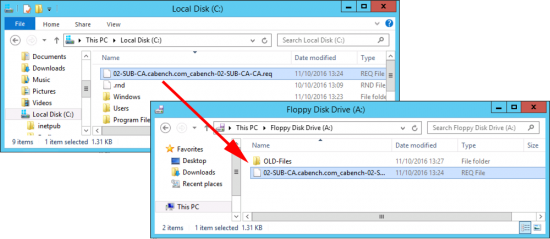
Copy your certificate request from the root of the system drive to your floppy drive.
Then present the floppy to your RootCA, and issue the following command;
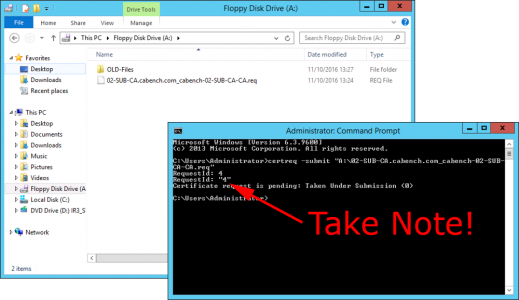
certreq -submit "A:\02-SUB-CA.cabench.com_cabench-02-SUB-CA-CA.req"
You will be given a ‘RequestID‘, write it down, (you will need it in a minute). Leave the command window open!
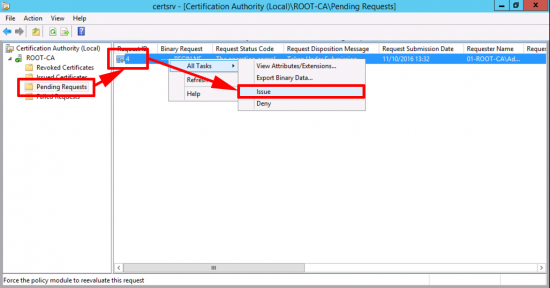
In the Certificate Services Management Console > Open ‘Pending Requests’ > Locate the RequestID number you noted above, and issue the certificate.
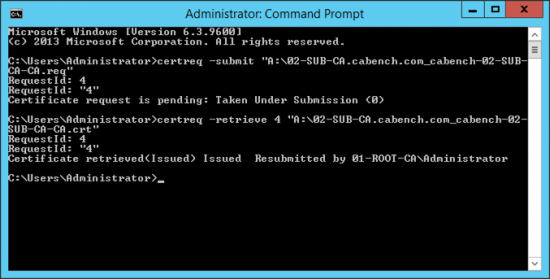
Back at your command window, retrieve the certificate with the following command, (use the RequestID again);
certreq -retrieve 4 “A:\02-SUB-CA.cabench.com_cabench-02-SUB-CA-CA.crt”
Take your floppy back to the SubCA, and install the certificate. (Change file types to ‘All Files’).
Now your SubCA is using a SHA256 certificate.
Repeat the process for any further SubCA’s
I Use NDES How Will That Be Affected?
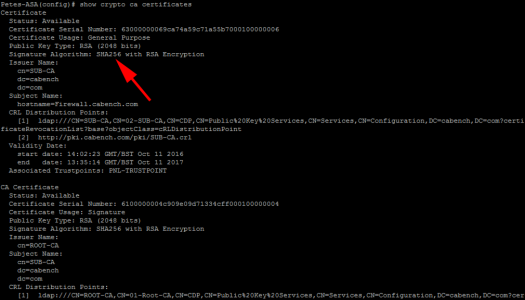
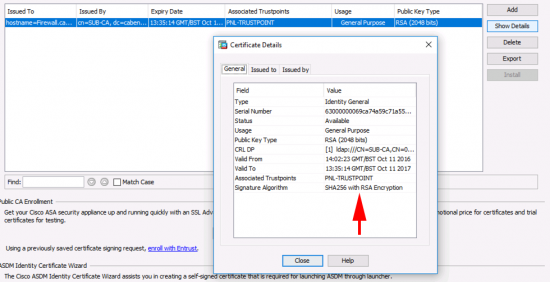
Having had problems with certificates and NDES before, I was concerned about this the most, because I have to look after a lot of Cisco equipment, that gets certs from NDES, (or SCEP if you prefer). I’m happy to say NDES worked fine with SHA256 certificates. Below I successfully issued certs to a Cisco ASA (Running 9.2(4)).
Related Articles, References, Credits, or External Links
Certificate Services – Migrate from SHA1 to SHA2 (SHA256)
Windows Server 2012 – Install and Configure NDES
Cisco ASA – Enrolling for Certificates with NDES
Cisco IOS – Enrolling for Certificates with NDES

23/11/2018
Hi,
I have RADIUS authentication using computer certificates deployed with auto enroll. Will these affected by migration from SHA1 to SHA2? Should I revoke the already deployed certificates and issue new ones?
Thanks!
23/11/2018
No already issued certificated are still trusted, because the older less secure CA certificate is still in date, and still trusted.
19/08/2019
Hi, I have a question regarding Cisco ASA using NDES/SCEP with our internal CA. We are looking to migrate our two-tier PKI to SHA256. But before we do we need to make sure we can still validate the already issued SHA1 client/user certificates on the field devices that connect to the Cisco ASA. My understanding is that I’ll need to import the new SHA256 signed CA certificates (Root & SubCA) into the ASA trustpoint. But I don’t think the new CA certs will be able to validate the previous SHA1 client certs on the field devices. Or can it still be validated if I renew the CA certs with the same key pair?
Another option is to build a parallel PKI with SHA256 to issue new SHA256 signed certs and leave the old PKI for existing SHA1 certs. Then I would add another trustpoint on the ASA for issuing new SHA256 certs. Is the ASA smart enough to know which trustpoint to use to validate and authenticate client/user?
And would you have any articles or references on how to configure the Windows domain/environment to have two Enterprise PKIs? Obviously the old SHA1 is there solely to validate/authenticate while the new SHA2 is the only one that will issue certificates for the enterprise.
Really appreciate your help!
Thanks!
20/08/2019
I have not done this, so I can’t comment, but I would urge you to build it in EVE-NG and test it first!
P
07/10/2019
Hi,
Once the rootCA which in my case is a offline root standalone CA is upgraded to SHA2 using your other guide, when it comes to our online issuing enterprise CA, do we have to follow the floppy disk guide or will the issuing CA be able to get this from the root ca (as it is not a enterprise CA but rather Standalone CA)?
So to confirm, we have a offline CA currently SHA1 and 2008r2 and also a online issuing CA again SHA1 and 2008r2.
I am also looking into migrating to server 2019 for both these boxes but to keep the same hostname. Would I do the SHA1 to SHA2 after migration or before
Many thanks
07/10/2019
Yes, your methodology is sound! you can then issue a ‘SubCA’ cert to the online CA, either by floppy, or cheekily attaching a network card temporarily! You can them migrate to a more modern OS.
P
08/10/2019
Hi Pete,
Thanks for the reply. I have virtual machines and am thinking down the lines of attaching a network card, copying the request to a folder on the root ca and once I have submitted and retrieved the certificate to copy the folder to the subCA and finish off the request. Hopefully that sounds about right.
Another question, I have seen your youtube video on the migration of CA from 2008 to 2019, does the server name have to remain the same as I have watched some which state the server name stays the same whereas your video shows a different server name and you add the old server name into the reg key before import. Which is the better solution?
08/10/2019
Attaching a vmnic is no problem at all, just remove it when you have finished, I’ve done the same myself many times.
Server name doesn’t not have to remain the same it’s the CA name you move, not the server name, you can keep the same server name but the means downtime as you cant have them both online at the same time, I never keep the server name the same, I really don’t see the point.
08/10/2019
Thanks for your response, much appreciated.
08/10/2019
Hi Pete,
On a separate note, I have gone through Microsoft migration plan and they only show up to 2012, can you directly upgrade to 2019 or do you have to hop to 2012 and then to 2019?
Thanks in advance
08/10/2019
You can go 2008 > 2019 and 2012 > 2019 and 2016 > 2019:)
08/10/2019
Final question hopefully 😉 have you come across the following issue when directly migrating from 2008 to 2016/2019 and missing the 2012 server:
“Unfortunately we cannot migrate the CA database directly from Server 2008 to Server 2016 because the JET database engine changed so much between the two versions that if we restore the backup we get a JET version error at startup and the CA won’t start.”
08/10/2019
Ive never had that problem.
14/10/2019
Hi Pete
The ROOT migration to SHA-2 went without problems.
My Sub CA is CSP and not KSP. It’s running Windows 2016, and earlier I migrated from Server 2018R2.
Will I have to go through the same procedure as for the ROOT-CA to prepare it for KSP, and then start on Part 2 ?
Best Regards
Brian
14/10/2019
I Don’t tend to upgrade to KSP unless I have a reason to, as I once did that for a client and their entire NDES country wide deployment would have gone down if I hadn’t noticed that is didn’t support strong cryptography.
21/10/2019
Hi Pete,
I am looking at the upgrade of the CA servers, I have everything in place ready for the migration from 2008r2 to 2019. However one question has popped up, should there be a GPO which is being used for CA, I have gone through all and cannot find any which has the root ca in the trusted root certification Authorities gpo folder. If there is no GPO, how are machines requesting certificates when expired and also how are new laptops which are built getting a certificate?
Thanks
21/10/2019
You can install certificates and trusted authorities via GPO, but you only need to do that if they are not YOUR CA’s So in nearly every situation NO you don’t need a GPO.
To answer your question they get the settings from Active Directory, the CA is a defined AD object 🙂 On a domain member open an administrative command prompt and issue the following command;
certutil –config – -pingThat’s how!
21/10/2019
Thanks Pete. I was thinking down the lines of stopping the GPO from publishing to all machines just in case during migration all machines start re-requesting certificates. However I guess it does not work in that manner.
How does a computer request a new cert if it has expired or due to expire, is there some sort of autoenroll policy within AD, does AD show those machines with the certs?
21/10/2019
That depends, is they are set to auto enroll for computer/user certificates then theres a time frame in the certificate template that handles when it should poll for renewal.