KB ID 0000948
Problem
To get your ASA 5500 firewall to enroll, and obtain a certificate from a Windows Server running NDES, this is the procedure you need to follow.
Solution
When dealing with certificates, it’s important that your firewall is maintaining the correct time. You can set this manually, but I’d recommend setting up NTP.
Cisco ASA – Configuring for NTP
1. Make sure the firewall can contact the NDES server, below I ping its IP address (192.168.1.10) . Then set a hostname and domain name for the firewall. These are required to generate an RSA Key-pair on the firewall before we start.
Petes-ASA# ping 192.168.1.10 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 192.168.80.130, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms Petes-ASA# configure terminal Petes-ASA(config)# hostname Firewall Firewall(config)# domain-name testbench.local Firewall(config)# crypto key generate rsa modulus 2048 INFO: The name for the keys will be: <Default-RSA-Key> Keypair generation process begin. Please wait... Firewall(config)#
2. Create a set of CA settings (a trustpoint), then authenticate to it.
Firewall(config)# crypto ca trustpoint PNL-TRUSTPOINT Firewall(config-ca-trustpoint)# enrollment url http://192.168.1.10/CertSrv/mscep/mscep.dll Firewall(config-ca-trustpoint)# revocation-check crl Firewall(config-ca-trustpoint)# enrollment retry count 3 Firewall(config-ca-trustpoint)# enrollment retry period 5 Firewall(config-ca-trustpoint)# fqdn Firewall.testbench.local Firewall(config-ca-trustpoint)# crypto ca authenticate PNL-TRUSTPOINT INFO: Certificate has the following attributes: Fingerprint: 0454b8f4 73374de8 2fb034cb b887b1d4 Do you accept this certificate? [yes/no]: yes Trustpoint CA certificate accepted.
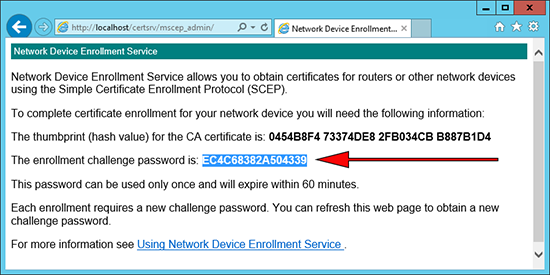
3. If your NDES Server requires a password you can embed that.
NDES Server Removing or Enforcing Passwords
If you require a password you can obtain it from the NDES Server using the following URL.
http://{IP-or-name-of-NDES-server}/CertSrv/mscep_admin
This is the password you need to enter.
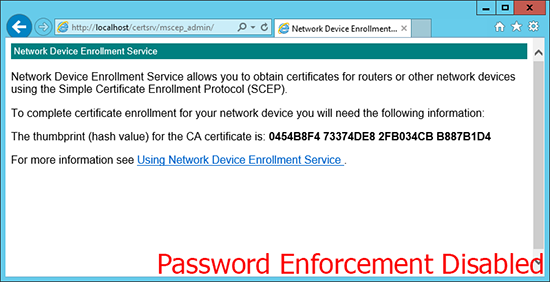
If it looks like (below), then password enforcement has been disabled, and you can skip the next step.
Firewall(config)# crypto ca trustpoint PNL-TRUSTPOINT Firewall(config-ca-trustpoint)# password EC4C68382A504339
4. Enroll for a certificate.
Firewall(config)# crypto ca enroll PNL-TRUSTPOINT % % Start certificate enrollment .. IF YOU SUPPLIED A PASSWORD YOU WILL NOT BE ASKED THE FOLLOWING % Create a challenge password. You will need to verbally provide this password to the CA Administrator in order to revoke your certificate. For security reasons your password will not be saved in the configuration. Please make a note of it. Password: ******** Re-enter password: ******** % The fully-qualified domain name in the certificate will be: Firewall.testbench.local % Include the device serial number in the subject name? [yes/no]: yes % The serial number in the certificate will be: 123456789AB Request certificate from CA? [yes/no]: yes % Certificate request sent to Certificate Authority Firewall(config)# The certificate has been granted by CA! Firewall(config)#
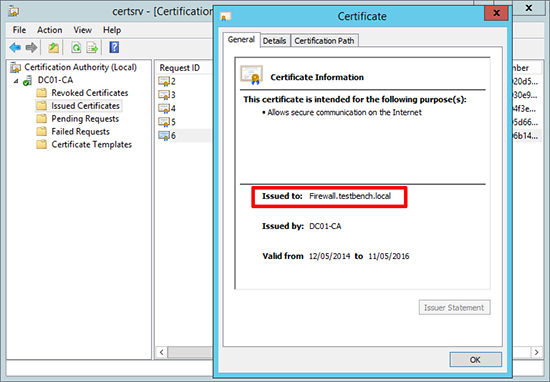
5. If you have a look on the Certificate Server you will also see that the certificate has been issued.
Remember: We set the device to check the Certificate Servers CRL, make sure that’s setup properly, and the device can resolve its name.
Windows Certificate Services – Setting up a CRL
Related Articles, References, Credits, or External Links
Windows Server 2012 – Install and Configure NDES