KB ID 0001242
Problem
Post By: Daniel Newton
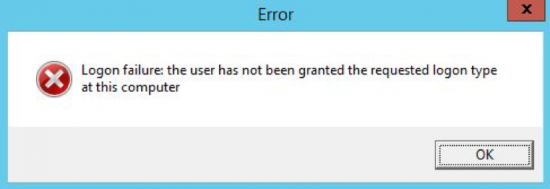
I was configuring a ADCS (Active Directory Certificate Services) on a DC (Domain Controller) for a client today and wanted to setup web-enrolment. I gave the Certificate Service User permissions to the IIS_USRS Group and everything was going well. Then, this error popped up when assigning the service account in setup.
Solution
This can be easily fixed, just follow these instructions and then you will be cooking on gas! (Remember I am on a domain controller)
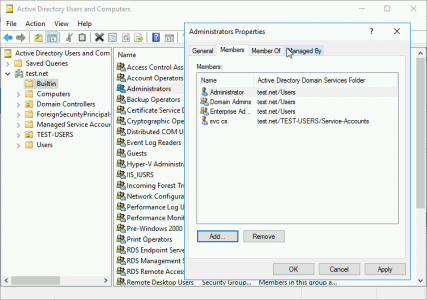
Go to Active Directory Users and Computers (dsa.msc) Locate the ‘Builtin’ container > then the Administrators group > and add your server account.
REALY: Yes, you need the right to ‘Log on Locally’, and remember this is a Domain Controller, try adding that right manually though GPO, its restricted.
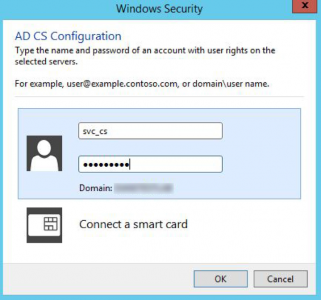
So, when you try and authenticate for the Service Account in setup, it will come up with no errors
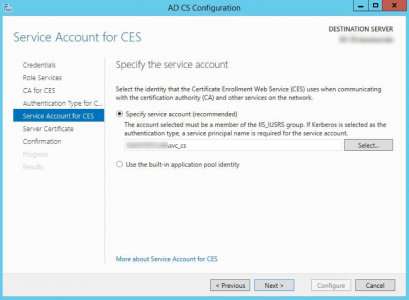
To prove that it’s not all smoke and mirrors, here is the user authenticated,
Related Articles, References, Credits, or External Links
NA

19/01/2017
This worked!! Thank you!
28/01/2017
Your most welcome! 🙂
16/04/2019
You are crazy, adding this to Domain Admins destroys the whole purpose of service accounts with least privileges. This is very bad practise.
16/04/2019
Hi Martin,
Thanks for the feedback, I had to check this as it was a guest post. The crux of the problem here is, this role is being deployed on a DC, which I would rather not do, but Daniel does specify this. Also the service account does need to be a member of builtin\administrators, and not domain admins. I would rather have the role on a member server and then simply grant ‘log on as a service’ and ‘log on locally’ but the latter is not available on a DC.
Regards
16/02/2020
Put the service account into the ‘Server Operators’ group. That group also has log-on-locally permissions on DCs.
23/05/2022
Hi, the wizard actually tells you what to do. The user account should be added to the IIS_IUSRS group. By default, this group is granted “Log on as a batch job” in the Default Domain Controller Policy. This should be sufficient, no need to add the account to domain admins, enterprise admins or administrators!
10/10/2023
That does not work. I tried that too, also tried granting other access rights through local security policy for the DC.
I think key to this would be the fact that it is a DC. DCs have different access rights compared to other domain members.
The authentication may be a red herring as the svc account only needs to be a member of the IIS_IUSRS local group. So, the service is likely to still operate properly post-configuration if the svc account is removed from the builtin\administrators group.