KB ID 0001240
Problem
Note: To add new subnets to an AnyConnect Remote Access VPN, see the following article instead;
Cisco ASA – Adding New Networks to AnyConnect VPNs
I see this get asked in forums A LOT, so I though I’d get around to getting it written up. If you have an existing VPN to a remote site and then need to add another network how do you do it?
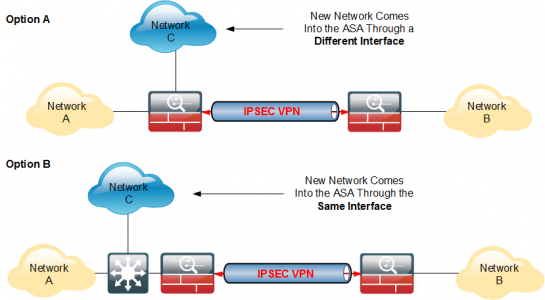
Well that depends on where the new network is, and how it’s entering the firewall, these diagrams can be either way round, but the new network will either be coming into the ASA on the same interface (i.e you’ve spun up a new network for phones, or a new department etc.) Or the traffic will be coming into the ASA through a different interface, (like a DMZ, or partner network).
Note: The process for adding the new network is the same for both, BUT depending on which interface the new traffic is coming in on, this will change your NAT command.
Solution
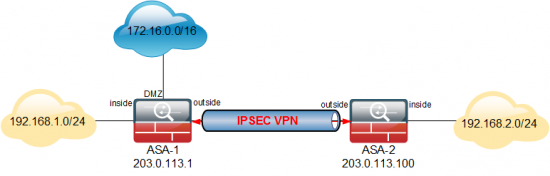
Option A: New Network is on a Different Interface
Let’s flesh our diagram out a bit, to make things easier to explain;
Tasks on ASA-1
- Locate the ACL that’s handling the site to site VPN and add the new network to it.
- Locate the NAT Exemption for the site to site VPN and add a new one for the new interface.
Locate the ACL that’s handling the VPN: This will be declared in the crypto map that points to the other ASA (203.0.113.100)
ASA-1# show run crypto map
crypto map PNL-MAP 1 match address VPN-BACKUP-TRAFFIC
crypto map PNL-MAP 1 set pfs
crypto map PNL-MAP 1 set peer 123.123.123.123
crypto map PNL-MAP 1 set ikev1 transform-set ESP-AES-128-SHA
crypto map PNL-MAP 1 set security-association lifetime kilobytes unlimited
crypto map PNL-MAP 2 match address VPN-INTERESTING-TRAFFIC
crypto map PNL-MAP 2 set pfs
crypto map PNL-MAP 2 set peer 203.0.113.100
crypto map PNL-MAP 2 set ikev1 transform-set VPN-TRANSFORM
crypto map PNL-MAP interface outsideFrom the output above we can see that the ACL for this VPN is called VPN-INTERESTING-TRAFFIC, yours, probably, will have a less friendly name. Let’s see what that’s doing.
ASA-1# show run access-list VPN-INTERESTING-TRAFFIC
access-list VPN-INTERESTING-TRAFFIC extended permit ip object Obj-Local-LAN object Obj-Remote-LANAgain I’ve got nice neat groups, yours may simply have the networks listed, let’s check those objects marry up with the subnets we expect.
ASA-1# show run object id Obj-Local-LAN object network Obj-Local-LAN subnet 192.168.1.0 255.255.255.0 ASA-1# show run object id Obj-Remote-LAN object network Obj-Remote-LAN subnet 192.168.2.0 255.255.255.0
So now create an object for the new network and add it to the existing ACL.
ASA-1# configure terminal ASA-1(config)# object network Obj-DMZ-LAN ASA-1(config-network-object)# subnet 172.16.0.0 255.255.0.0 ASA-1(config-network-object)# access-list VPN-INTERESTING-TRAFFIC extended permit ip object Obj-DMZ-LAN object Obj-Remote-LAN
Now just the NAT exception to do, let’s find the NAT exemption;
ASA-1(config)# show run nat
nat (inside,outside) source static any any destination static Obj-ANYCONNECT-SUBNET Obj-ANYCONNECT-SUBNET no-proxy-arp route-lookup
nat (inside,outside) source static Obj-Local-LAN Obj-Local-LAN destination static Obj-Remote-LAN Obj-Remote-LAN no-proxy-arp route-lookup
!
object network Server
nat (inside,outside) static interface service tcp 3389 3389
!
object network OBJ-ANY
nat (inside,outside) dynamic interfaceNow as this traffic is actually coming though the DMZ interface (not the inside interface) we add our new object in and exempt it from NAT like so
ASA-1(config)# nat (DMZ,outside) source static Obj-DMZ-LAN Obj-DMZ-LAN destination static Obj-Remote-LAN Obj-Remote-LAN no-proxy-arp route-lookupTasks on ASA-2
- Locate the ACL that’s handling the site to site VPN and add the new network to it.
- Locate the NAT Exemption for the site to site VPN and add the new network to it.
Locate the ACL that’s handling the VPN: This will be declared in the crypto map that points to the other ASA (203.0.113.1)
ASA-2# show run crypto map
crypto map outside_map 1 match address outside_cryptomap_1
crypto map outside_map 1 set pfs
crypto map outside_map 1 set peer 203.0.113.1
crypto map outside_map 1 set ikev1 transform-set VPN-TRANSFORM
crypto map outside_map interface outsideFrom the output above we can see that the ACL for this VPN is called outside_cryptomap_1 . Let’s see what that’s doing.
ASA-2# show run access-list outside_cryptomap_1
access-list outside_cryptomap_1 extended permit ip object Obj-Local-LAN object Obj-Remote-LANI’ve got nice neat groups, yours may simply have the networks listed, let’s check those objects mary up with the subnets we expect.
ASA-2# show run object id Obj-Local-LAN object network Obj-Local-LAN subnet 192.168.2.0 255.255.255.0 ASA-2# show run object id Obj-Remote-LAN object network Obj-Remote-LAN subnet 192.168.1.0 255.255.255.0
So now create an object for the new network and add it to the existing AC.L
ASA-2# configure terminal ASA-2(config)# object network Obj-DMZ-LAN ASA-2(config-network-object)# subnet 172.16.0.0 255.255.0.0 ASA-2(config-network-object)# access-list outside_cryptomap_1 extended permit ip object Obj-Local-LAN object Obj-DMZ-LAN
Now just the NAT exception to do, let’s find the NAT exemption;
ASA-2(config)# show run nat
nat (inside,outside) source static Obj-Local-LAN Obj-Local-LAN destination static Obj-Remote-LAN Obj-Remote-LAN no-proxy-arp route-lookup
!
object network Obj-ANY
nat (inside,outside) dynamic interfaceNow simply add the new object we created above as an extra NAT exemption.
ASA-1(config)# nat (inside,outside) source static Obj-Local-LAN Obj-Local-LAN destination static Obj-DMZ-LAN Obj-DMZ-LAN no-proxy-arp route-lookupDON’T FORGET to save the config on both firewalls with a ‘write mem‘ command!
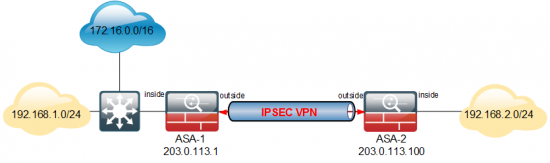
Option B: New Network is on the Same Interface
Let’s flesh our diagram out a bit, to make thinks easier to explain;
Tasks on ASA-1
- Locate the ACL that’s handling the site to site VPN and add the new network to it.
- Locate the NAT Exemption for the site to site VPN and add the new network to it.
Locate the ACL that’s handling the VPN: This will be declared in the crypto map that points to the other ASA (203.0.113.100)
ASA-1# show run crypto map
crypto map PNL-MAP 1 match address VPN-BACKUP-TRAFFIC
crypto map PNL-MAP 1 set pfs
crypto map PNL-MAP 1 set peer 123.123.123.123
crypto map PNL-MAP 1 set ikev1 transform-set ESP-AES-128-SHA
crypto map PNL-MAP 1 set security-association lifetime kilobytes unlimited
crypto map PNL-MAP 2 match address VPN-INTERESTING-TRAFFIC
crypto map PNL-MAP 2 set pfs
crypto map PNL-MAP 2 set peer 203.0.113.100
crypto map PNL-MAP 2 set ikev1 transform-set VPN-TRANSFORM
crypto map PNL-MAP interface outsideFrom the output above we can see that the ACL for this VPN is called VPN-INTERESTING-TRAFFIC, yours ,probably, will have a less friendly name. Let’s see what that’s doing.
ASA-1# show run access-list VPN-INTERESTING-TRAFFIC
access-list VPN-INTERESTING-TRAFFIC extended permit ip object Obj-Local-LAN object Obj-Remote-LANAgain I’ve got nice neat groups, yours may simply have the networks listed, let’s check those objects mary up with the subnets we expect.
ASA-1# show run object id Obj-Local-LAN object network Obj-Local-LAN subnet 192.168.1.0 255.255.255.0 ASA-1# show run object id Obj-Remote-LAN object network Obj-Remote-LAN subnet 192.168.2.0 255.255.255.0
So now create an object for the new network and add it to the existing ACL
ASA-1# configure terminal ASA-1(config)# object network Obj-Local-LAN-2 ASA-1(config-network-object)# subnet 172.16.0.0 255.255.0.0 ASA-1(config-network-object)# access-list VPN-INTERESTING-TRAFFIC extended permit ip object Obj-Local-LAN-2 object Obj-Remote-LAN
Now just the NAT exception to do, let’s find the NAT exemption;
ASA-1(config)# show run nat
nat (inside,outside) source static any any destination static Obj-ANYCONNECT-SUBNET Obj-ANYCONNECT-SUBNET no-proxy-arp route-lookup
nat (inside,outside) source static Obj-Local-LAN Obj-Local-LAN destination static Obj-Remote-LAN Obj-Remote-LAN no-proxy-arp route-lookup
!
object network Server
nat (inside,outside) static interface service tcp 3389 3389
!
object network OBJ-ANY
nat (inside,outside) dynamic interfaceNow add the new subnet in as an additional NAT exemption.
ASA-1(config)# nat (inside,outside) source static Obj-Local-LAN-2 Obj-Local-LAN-2 destination static Obj-Remote-LAN Obj-Remote-LAN no-proxy-arp route-lookupTasks on ASA-2
- Locate the ACL that’s handling the site to site VPN and add the new network to it.
- Locate the NAT Exemption for the site to site VPN and add the new network to it.
Locate the ACL that’s handling the VPN: This will be declared in the crypto map that points to the other ASA (203.0.113.1)
ASA-2# show run crypto map
crypto map outside_map 1 match address outside_cryptomap_1
crypto map outside_map 1 set pfs
crypto map outside_map 1 set peer 203.0.113.1
crypto map outside_map 1 set ikev1 transform-set VPN-TRANSFORM
crypto map outside_map interface outsideFrom the output above we can see that the ACL for this VPN is called outside_cryptomap_1 . Let’s see what thats doing.
ASA-2# show run access-list outside_cryptomap_1
access-list outside_cryptomap_1 extended permit ip object Obj-Local-LAN object Obj-Remote-LANI’ve got nice neat groups, yours may simply have the networks listed, let’s check those objects marry up with the subnets we expect.
ASA-2# show run object id Obj-Local-LAN object network Obj-Local-LAN subnet 192.168.2.0 255.255.255.0 ASA-2# show run object id Obj-Remote-LAN object network Obj-Remote-LAN subnet 192.168.1.0 255.255.255.0
So now create an object for the new network and add it to the existing ACL
ASA-2# configure terminal ASA-2(config)# object network Obj-Remote-LAN-2 ASA-2(config-network-object)# subnet 172.16.0.0 255.255.0.0 ASA-2(config-network-object)# access-list outside_cryptomap_1 extended permit ip object Obj-Local-LAN object Obj-Remote-LAN-2
Now just the NAT exception to do, lets find the NAT exemption;
ASA-2(config)# show run nat
nat (inside,outside) source static Obj-Local-LAN Obj-Local-LAN destination static Obj-Remote-LAN Obj-Remote-LAN no-proxy-arp route-lookup
!
object network Obj-ANY
nat (inside,outside) dynamic interfaceNow simply add the new object we created above as an extra NAT exemption.
ASA-2(config)# nat (inside,outside) source static Obj-Local-LAN Obj-Local-LAN destination static Obj-Remote-LAN-2 Obj-Remote-LAN-2 no-proxy-arp route-lookupDON’T FORGET to save the config on both firewalls with a ‘write mem‘ command!
Related Articles, References, Credits, or External Links
NA

21/07/2020
I just want to say thank you for all your hard work. You are really good at explaining things. I hope you are proud of you because you should be. Thank you once again and please continue sharing.
21/07/2020
Thanks Mao – Glad I could help
07/08/2020
Amazing
05/02/2023
Just a comment – the link for “Cisco ASA – Adding New Networks to AnyConnect VPNs” is recursive and not to your AC thread. I believe it should go to post 1593 Adding New Networks to Cisco AnyConnect VPNs?
07/02/2023
Thanks Brian – Fixed.