KB ID 0001152
Problem
When I first started doing Cisco remote VPNs, we had Server 2000/2003 and I used to use RADIUS with IAS. Then Microsoft brought out 2008/2012 and RADIUS via NAP. Because I fear and loath change I swapped to using Kerberos VPN Authentication for a while. I had to put in an ASA5512-X this weekend and the client wanted to allow AnyConnect to a particular Domain Security Group “VPN-Users”, so I thought I would use LDAP for a change.
The process is to setup AAA for LDAP, then create an ‘Attribute map’ for the domain group, and then map that group to a particular ASA Tunnel Group/ASA Group Policy. Though to be honest if you have multiple groups and want to assign different levels of access (i.e. different ACLs etc.) then using a blend of LDAP and Cisco Dynamic Access Policies (DAP) is a lot simpler.
I’ll post both options, and you can take your pick
Solution
Firstly you need to create a ‘service account’ in Active Directory that the ASA will use, it only need to be able to browse the AD, so a simple Domain User is fine.
Then create a user group that you want to grant AnyConnect Access to;
And, then create a test user and put that user in your domain group.
Configure the ASA for LDAP
Create an AAA LDAP Server Group > Add a Server > Put in the Config for that server like so;
CHANGE THE ENTRIES IN BOLD BELOW TO MATCH YOUR REQUIREMENTS Type help or '?' for a list of available commands. Petes-ASA> enable Password: ******** Petes-ASA# configure terminal Petes-ASA(config)# aaa-server PNL-LDAP-SERVER protocol ldap Petes-ASA(config-aaa-server-group)# aaa-server PNL-LDAP-SERVER (inside) host 192.168.100.10 Petes-ASA(config-aaa-server-host)# ldap-base-dn dc=pnl,dc=com Petes-ASA(config-aaa-server-host)# ldap-scope subtree Petes-ASA(config-aaa-server-host)# ldap-naming-attribute sAMAccountName Petes-ASA(config-aaa-server-host)# ldap-login-password P@assword123 Petes-ASA(config-aaa-server-host)# ldap-login-dn cn=asa,OU=ServiceAccounts,OU=PNL,dc=pnl,dc=com Petes-ASA(config-aaa-server-host)# server-type auto-detect Petes-ASA(config-aaa-server-host)# exit Petes-ASA(config)# exit Petes-ASA#
Now perform a test, and make sure it says “successful’
NOTE: HERE I'VE SET IT TO FALL BACK TO LOCAL AUTH IF THE LDAP SERVER IS DOWN! Petes-ASA# test aaa-server authentication PNL-LDAP-SERVER host 192.168.100.10 username administrator password P@ssword123 INFO: Attempting Authentication test to IP address (timeout: 12 seconds) INFO: Authentication Successful
Add LDAP Authentication For AnyConnect
I’m assuming you already have AnyConnect Setup? If not that’s fine simply follow the article below, which will set it up for LOCAL authentication, set it up and get it working then come back here.
Cisco ASA 5500 AnyConnect Setup From Command Line
To change authentication from LOCAL you make a change in the Tunnel-Group for you remote VPN connection, if you don’t know what the name of your tunnel group is ‘show run tun’ will list them. You add the authentication-server-group to the general-attributes section of the config, like so;
NOTE: HERE IT WILL FAIL BACK TO 'LOCAL' AUTH IF LDAP GOES DOWN (THIS IS GOOD!) Petes-ASA(config)# tunnel-group PNL-TG-ANYCONNECT-ACCESS general-attributes Petes-ASA(config-tunnel-general)# authentication-server-group PNL-LDAP-SERVER LOCAL Petes-ASA(config-tunnel-general)# exit Petes-ASA(config)# write mem Building configuration... Cryptochecksum: 30899474 8c9cd7c6 495be299 fd911bca 19681 bytes copied in 3.340 secs (6560 bytes/sec) [OK] Petes-ASA(config)#
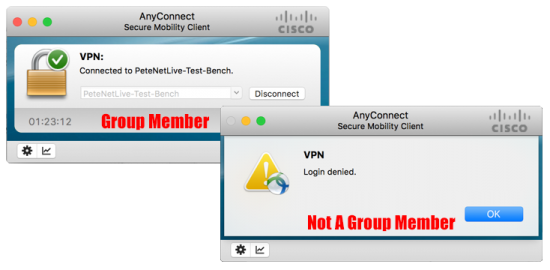
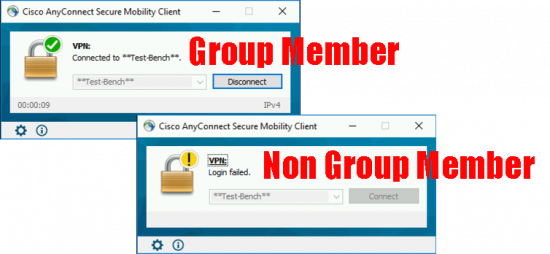
Note: At this point ALL DOMAIN USERS can successfully authenticate, to lock it down to one domain security group, either apply a Dynamic Access Policy (these can only be done in the ASDM). or skip further down, to edit and create your group-policies and use an attribute-map.
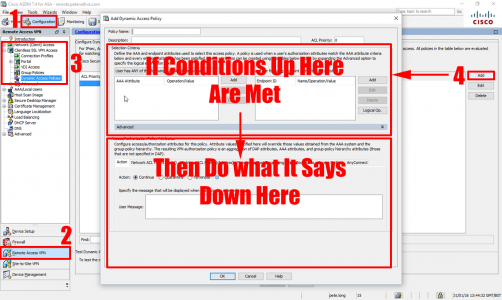
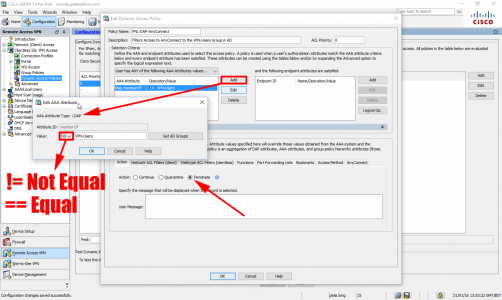
Cisco ASDM Configure Dynamic Access Policies
Connect to the ASDM > Configuration > Remote Access VPN > Dynamic Access Policies > Add.
Add an LDAP Condition > IF NOT a member (or not equal to member) > Insert domain security group. Then set the condition to ‘Terminate’.
Configure Group Access via Attribute Map
As already pointed out I’m assuming you already have AnyConnect in and working, so you will have both a Group-Policy your users are using, and a tunnel-group configured, we will make some changes to those. if you don’t know thew name of your configured group-policy or tunnels group the following two commands will tell you;
- To see your tunnel group(s): show run tun
- To see your group-policy(s): show run group-policy
Note: If you have many, simply connect with a user, then run show vpn-sessiondb det anyconnect to get the details.
Firstly create a NEW group-policy that blocks access (this will become the default).
Petes-ASA(config)# group-policy ANYCONNECT-NO-ACCESS internal Petes-ASA(config)# group-policy ANYCONNECT-NO-ACCESS attributes Petes-ASA(config-group-policy)# vpn-simultaneous-logins 0 Petes-ASA(config-group-policy)# exit
Then we will change your EXISTING group-policy to change the simultaneous login threshold
Petes-ASA(config)# group-policy GroupPolicy_ANYCONNECT-PROFILE attributes Petes-ASA(config-group-policy)# vpn-simultaneous-logins 3 Petes-ASA(config-group-policy)# exit
Then we will change your EXISTING tunnel-group to change the authentication method, and set the default group-policy to ‘deny’. Note: Ive added the ASA’s local user database as a fall-back in case the LDAP server(s) are down/not-contactable.
Petes-ASA(config)# tunnel-group ANYCONNECT-PROFILE general-attributes Petes-ASA(config-tunnel-general)# authentication-server-group PNL-LDAP-SERVER LOCAL Petes-ASA(config-tunnel-general)# default-group-policy ANYCONNECT-NO-ACCESS Petes-ASA(config-tunnel-general)# exit
Create an Attribute map, that matches the AD group that has your ‘allowed’ users in it.
Petes-ASA(config)# ldap attribute-map AM-ANYCONNECT-USERS Petes-ASA(config-ldap-attribute-map)# map-name memberOf Group-Policy Petes-ASA(config-ldap-attribute-map)# map-value memberOf CN=VPN-Users,OU=Groups,OU=PNL,DC=pnl,DC=com GroupPolicy_ANYCONNECT-PROFILE Petes-ASA(config-ldap-attribute-map)# exit
Finally add that Attribute map, to the LDAP server you created earlier.
Petes-ASA(config)# aaa-server PNL-LDAP-SERVER (inside) host 192.168.100.10 Petes-ASA(config-aaa-server-host)# ldap-attribute-map AM-ANYCONNECT-USERS
Then test;
Related Articles, References, Credits, or External Links
Cisco AnyConnect – Allow Domain Password Change via LDAP
Thanks to Ben Monroe, who emailed me as the original article was lacking the Attribute Map section. I had omitted it originally and stuck with DAP, primarily because I could not get LDAP group authentication to work! I still prefer DAP as a solution, but for the sake of completeness I revisited this, and added the complete LDAP procedure.

10/06/2016
Hi,
Thanks for the article, but I have one question, from the configuration I do not see how actually asa checks that authenticating user is a member of VPNUser group.. Any ideas?
Kind regards,
10/06/2016
With LDAP alone, It wont work, you need the DAP as well (Cisco might argue) but I’d ask them to show me a working LDAP only config before I would believe them 🙂
P
07/01/2021
Hi
how can we configure two ldap server for anyconnect users. For example
If ldap-server1 fails the asa should reach to ldap-server2
Thanks
11/01/2021
Just define another LDAP server in the LDAP AAA group.
19/07/2016
Great 🙂
I checked Cisco how to guides, it confused me 🙂
Yours one: Simple and clear 🙂
Thanks a lot!!!
13/01/2017
It works! I was trying to map ldap attribute 2 days until I foud this article! it took me 2 min 🙂
thanks!!
15/01/2017
Amazing article! The documentation and the threads in Cisco’s forum are so confusing. This article is spot on! Thank you.
15/01/2017
ThanQ 🙂
24/05/2017
All I can say is thanks! Wasted two days on trying to get ASA LDAP Attribute Mapping working. DAP is the way to go. Followed PeteLongs steps and in 2 minutes we are up and running using AD Group authentication for VPN! I can see many other policies that we can now set as well. Thanks once again for your post!
27/05/2017
No problem, thanks for the feedback.
P
31/05/2017
I wish Google had put your page at the top of the search results. Like everyone else, I have been struggling with LDAP Mapping, but your explanation is easy and makes perfect sense. Thanks for publishing this.
31/05/2017
ThanQ – I wish I was also at the top 🙂
08/06/2017
I need multiple Group-Profile match and authenticate with different LDAP group. Any idea?
Thanks
12/06/2017
A Better solution is to use RADIUS then (depending on the group membership) pass the group policy back in the RADIUS reply.
Pete
07/09/2018
How do I add this DAP to a specific group policy and not to others
For instance, I only want this DAP to apply to a specific remote access vpn tunnel profile/group-policy
I have multiple tunnel-profiles and group-policy
Does this one DAP apply to one tunnel-profile/group policy both for client/clientless ssl vpns?
10/09/2018
You can’t unfortunately they are global 🙁
21/09/2018
If I have two ISPs with different IP address can I use both of them to access remote vpn ?
Or only one IP aadress can work.
21/09/2018
Great Question! You can access AnyConnect via either public IP, you would need to have both IP addresses registered against the public domain name. And you would need to enable it on both interfaces, and have mirrored NAT rules. (unless you had (inside, any) and not (inside,outside) for example).
P
14/03/2019
I need to allow users to change their passwords at the VPN login screen. And to let them know their password is expiring in x days. They already log in using their domain account.
15/03/2019
I’ve added the link to the bottom of the page.
Pete
17/06/2019
FYI – DAP is incompatible with DUO SAML MFA. We’re now trying to tear down our DAP policy to make our ASA usable with DUO.
09/09/2019
Awesome article. Thank you so much for your knowledge.
20/02/2020
Unfortunately the cli part doesn’t work.
As soon as I put ANYCONNECT-NO-ACCESS in no one can connect.
24/03/2020
Pls verify that your group-policy contains vpn-simultaneous-logins 3 (or more)
otherwise the value from default-group-policy ANYCONNECT-NO-ACCESS is inherited.
16/03/2020
Hello there!
This is the best website in the world 🙂 Thank you!
A side question, what about lockout login in this configuration? I mean how to prevent brute force?
It seems that setting in the AAA “max fail attempts” = 3 is not working, I can brute it…
17/03/2020
If you are using LDAP you need to set the password and lockout policy on the domain.
16/03/2020
Question.
If they have a license in place that limits the amount of users that can connect, does using LDAP change that? Would they be able to have, say, 20 users connect when their license says they are limited to 4?
17/03/2020
No AnyConnect licence usage is concurrent 🙂 Sorry.
31/03/2020
This worked great!! Thanks for providing these easy to follow steps. The one issue I had was mapping the AD group. We have a space in the group’s DN so I had to put quotes around it to make it work properly.
Example: map-value memberOf “CN=Group Name with Space,OU=Groups,DC=Company,DC=net” Group-PolicyName
08/04/2020
Hi!
When using an AD-group for VPN access, do you know if it is possible to use subgroups under that group?
I have tried and it didn’t work but I wonder if there is a way to make ASA search recursively.
And thanks for a great post 🙂
08/04/2020
With LDAP probably not, though with NAP/RADIUS it should work?
09/06/2020
Hi Pete
I followed the steps to integrate it with Freeipa(LDAP).
I could successfully authenticate all users.
But the Group filter is not working.
I am getting login failed on all users.
So, the situation is like either all will authenticate or none.
Kindly advise.
30/07/2020
Is anyone else having issues with the fact that OpenLDAP will return memberOf only if it explicitly queried:
[admin@ldap]$ ldapsearch -x -h localhost -x -b ‘dc=ps,dc=my,dc=com’ “uid=dms.user” memberOf
version: 1
dn: uid=dms.user,ou=dms,ou=People,dc=ps,dc=my,dc=com
***************************************************
memberOf: cn=DMS_Group,ou=Groups,dc=ps,dc=my,dc=com
***************************************************
or if a “+” is specified to return operation attributes:
[admin@ldap]$ ldapsearch -x -h localhost -x -b ‘dc=ps,dc=my,dc=com’ “uid=dms.user” “+”
version: 1
dn: uid=dms.user,ou=dms,ou=People,dc=ps,dc=myf,dc=com
structuralObjectClass: inetOrgPerson
creatorsName: cn=Manager,dc=ps,dc=my,dc=com
…
entryCSN: 20200729010355.226357Z#000000#000#000000
modifyTimestamp: 20200729010355Z
***************************************************
memberOf: cn=DMS_Group,ou=Groups,dc=ps,dc=my,dc=com
***************************************************
modifiersName: cn=Manager,dc=ps,dc=my,dc=com
entryDN: uid=dms.user,ou=dms,ou=People,dc=ps,dc=my,dc=com
subschemaSubentry: cn=Subschema
hasSubordinates: FALSE
Our Network Admin (and the Cisco engineer) insist that the problem is OpenLDAP as “This works on our *MS ACTIVE DIRECTORY* lab”
Is there any way to have the ASA query for these operational attributes? We cannot be the only entity that needs to assign users to access policies from LDAP…
25/08/2020
Is the ldap-login-password the password that was created with the ServiceAccount?
27/08/2020
Yes
03/09/2020
Hi PeteLong,
This is excellent Doc and Would wish your Blogs will be on top!
Aside this I have a query that What else if we have two or more VPN-Profiles and wish to connect specific group to specific profile only?
Thank you in Advance!
08/09/2020
Yes, I’d use Dynamic Access Policies for that, then members of different groups get different Cisco ASA group-policies.
16/09/2020
Hello Pete. I love your guides. Do you have a guide for Dynamic Access Policy in relation to Radius? We manage an ASA for a company and their DAP is locking us out. They use LDAP whereas we use radius and where are having issues attempting to find what would be used for the = or != Attribute ID in the drop down where you choose from radius or LDAP. We examined debugs hoping to gleam some information but are not having much luck. Any info with this issue would be most helpful. Thank you for your awesome blogs.
17/09/2020
I’ve never really mixed Radius and DAP, I suspect strange things would happen 🙂 But I’ll approve the comment, and see if anyone has any thoughts.
P
09/10/2020
Thanks Pete!! This is an excellent guide!! I was having the hardest time with LDAP Mapping and then I found your page and this article and now everything is much more clear. Thanks again!!
09/10/2020
Glad to help 🙂
09/10/2020
Hi Pete,
Thanks a lot for posting such great articles.
I have a query related to fallback – if LDAP servers fail and LOCAL auth is used for fallback – is there a way that the user gets notified to use LOCAL auth instead of his AD account.
I read in a Cisco article that we can keep the username and password in LOCAL DB similar to AD so that users do not notice but in real world managing the LOCAL DB passwords to be same as AD is not going to be a good option.
Thanks.
09/10/2020
ASFAIK: The only indication an end user will get it it takes a LOT longer, (Because they have to wait for the AAA to time out, before it falls back to LOCAL). And yes managing LOCAL and AAA accounts to be the same is cumbersome.
09/01/2021
If i have a same username in two domains, both in same AD. one user is connected to a separate tunnel but the second user is not able to connect to a separate tunnel. Why?
11/01/2021
If both users have the same sAMAccountName that’s your problem.
12/01/2021
Very Good Article, but unfortunately does not work for me. I put in the various configuration steps but it always defaults to the default policy. I am also using Certificates with Certificate mapping which works but I want to use specific Group policies for LDAP Membership. Is this possible?
23/06/2021
How would we set this up for secured LDAPS requests over 636/tcp instead of unsecured plaintext LDAP over 389/tcp?
23/06/2021
aaa-server LDAP (inside) host server.petenetlive.com
server-port 636
ldap-base-dn dc=petenetlive,dc=com
ldap-scope subtree
ldap-naming-attribute uid
ldap-login-password *****
ldap-login-dn cn=pete.long,dc=petenetlive,dc=com
ldap-over-ssl enable
or something like that.
You may need to import the CA certificate into the ASA, and make sure your time sync is correct as well 🙂
P
23/06/2021
Hey Pete, how do we configure this for secured LDAPS over 636/tcp?
11/05/2022
Even in 2022 this is still a valuable article. I’m always forgetting one of the steps, so I should probably bookmark this page 🙂