KB ID 0001142
Problem
This is part of a larger piece of work Im putting together on publishing Remote Desktop Services with Microsoft Web Application Proxy.
This article is simply to guide you though the process of installing the Web Application Proxy role. In a later article I will run though configuring it to work with Active Directory Federation Services, and Remote Desktop Services, to present secure RemoteApps.
Solution
Before You Start: This is a secure web proxy so that means certificates, I find it a lot easier to use wildcard certs for this sort of thing, The best solution is to buy one from a vendor, or you can create your own wildcard certificate.
You will need a Server deployed to install this on, preferably a non-domain joined computer that resides in a DMZ (this is a secure deployment, if you want to put it on your LAN, then why not just point external clients directly at your Remote Desktop Services Web Access server and forget WAP?)
You will also need to have deployed ‘Active Directory Federation Services‘ in you LAN, and TCP port 443 (Https) needs to be open from the WAP server to the ADFS server.
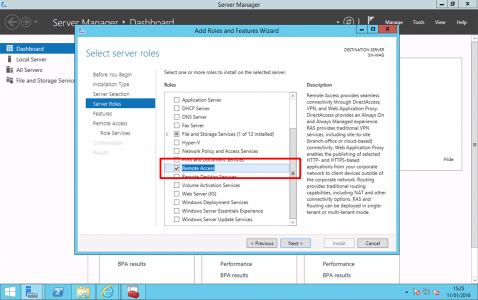
Server Manager > Manage > Add Roles and Features > Next > Next > Select the server > Next > Server Roles > Select Remote Access > Next > Next >Next.
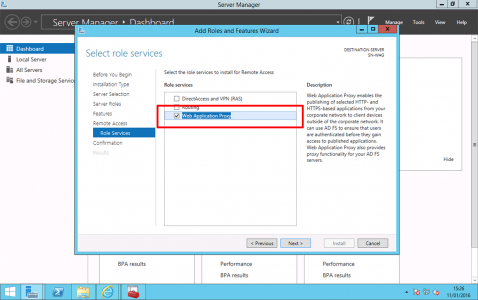
Select Web Application Proxy only > Accept all the defaults and install the role.
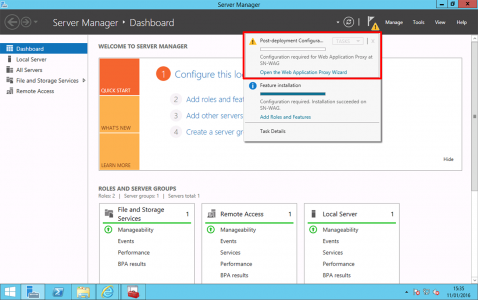
Launch the Post-Deployment configuration wizard.
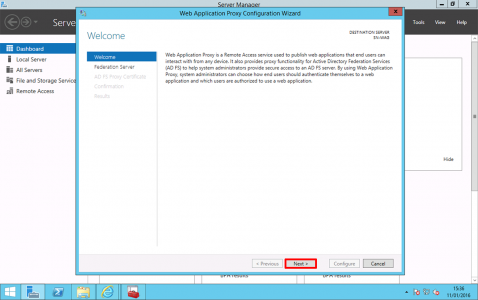
Next.
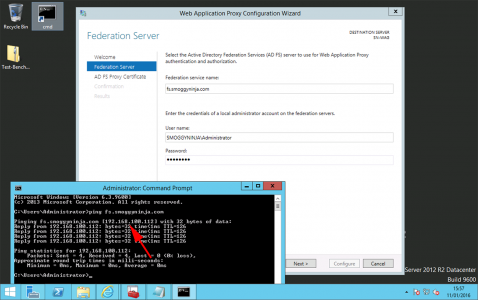
Type in the name of your AD federated SERVICE > And supply credentials to be able to access that server > Next.
Note: As you can see below I can resolve the name of the federation service “fs.smoggyninja.com”, from my DMZ server, it’s easier to just put an entry in the WAP servers hosts file rather than open DNS to the LAN, (or you can register it in public DNS of course!) Below you can see I’ve been able to ping the federation server, normally you would not be able to, (from the DMZ), I simply opened ICMP/Ping for testing, as stated (above), you only need https open > Next.
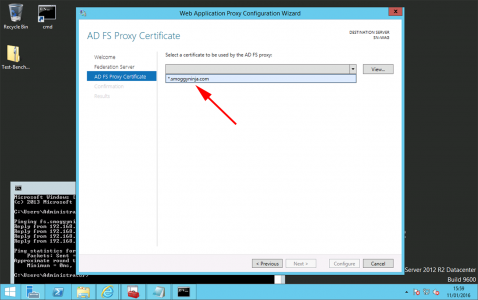
Select the certificate you are going to use.
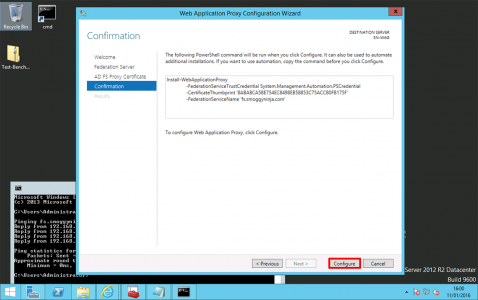
Configure.
Close.
The ‘Remote Access Management Console’ should open, if not launch it from administrative tools.
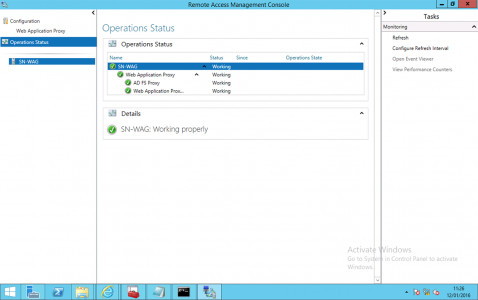
Select Operational Status and all the services should be ‘Green’.
That’s the role installed, now you just need to setup a publishing rule to publish the service you want to present. In my case thats Remote Desktop Web Access. Which I will cover in the next article.
Related Articles, References, Credits, or External Links
NA