KB ID 0001140
Problem
The actual configuration of ADFS depends largely on what you intend to do with it. Here I’m using it to broker connections from my Microsoft Web Application Proxy. This article is just to ‘join the dots’ and covers just the installation of the role itself.
Solution
Before you Start: Make sure you have a certificate ready to use for ADFS. I typically use a wildcard cert for this, it’s better if you have purchased one, or if you use certificate services, here’s how to create a wildcard certificate.
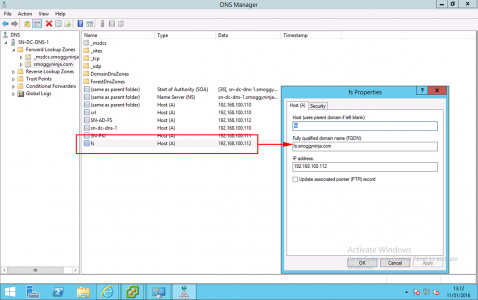
Note: You can add adfs.{your-domain} to your wildcard as a SAN, (Subject Alternative Name), Also add certauth.adfs.{your-domain}. Yes, even on a wildcard certificate!
For example: adfs.petenetlive.com and certauth.adfs.petenetlive.com.
You can either create a service account for ADFS to run under, or use a GROUP MANAGED SERVICE ACCOUNT.
What’s a Group Managed Service Account?
It’s an AD object that acts as a service account, and you don’t need to worry about entering a password for it.
Create a Group Managed Service Account
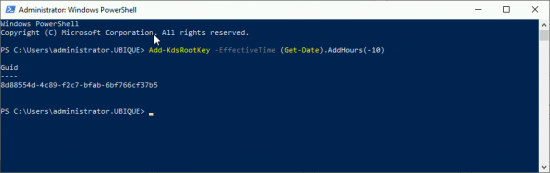
Before you can have a GSMA account you need a KDS Root Key in active Directory, to set that up, execute the following command;
If you have only one domain controller; Add-KdsRootKey –EffectiveTime ((get-date).addhours(-10)) If you have more than one domain controllers; Add-KdsRootKey –EffectiveImmediately If you use the second option you must then WAIT 10 HOURS!
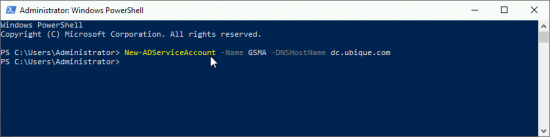
Then go to a Domain Controller, and issue the following command;
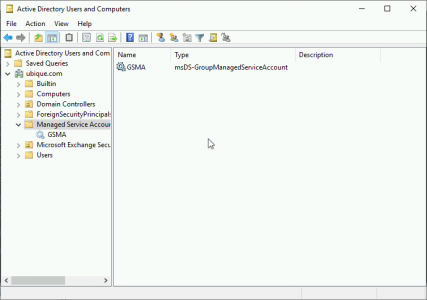
New-ADServiceAccount -Name {Account-Name} -DNSHostname {DNS/DC-Name}In case you are interested, you will then see it appear in Active Directory.
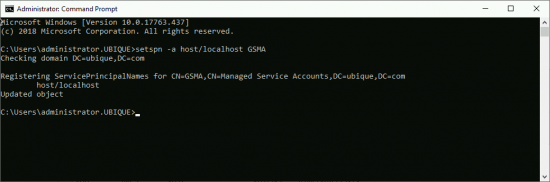
Then ON the ADFS Server, run the following command;
setspn -a host/localhost {GSMA-Account-Name}Deploying Active Directory Federation Services
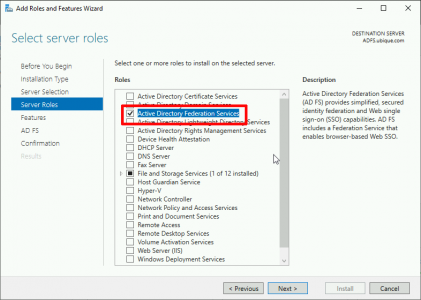
Server Manager > Manage > Add Roles and Features > Next > Next > Select the server > Next > Server Roles > Select Active Directory Federation Services > Accept all the defaults and install the role.
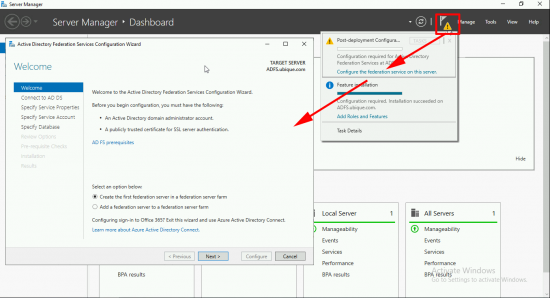
Launch the configuration wizard > Create the first federation server in a federation farm > Next.
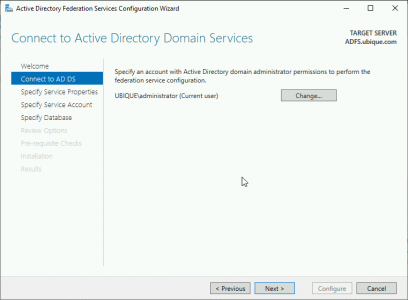
I’m setting this up while logged on as the domain administrator, so I’ll use that account to connect to AD > Next.
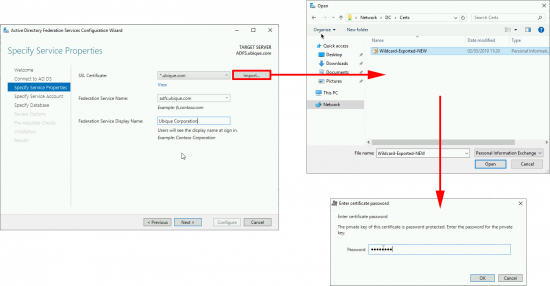
WARNING: If you use a wildcard cert like me it will choose the name of *.{domain-name}. THIS IS BAD! Change the federation service name to something sensible, like adfs.domain.com. The ‘Federation Service Display Name‘ is what will be shown to the users as they authenticate. > Next.
Make sure the federation server DNS name can be resolved in DNS! Remember if your Web Application Proxy server is in your DMZ, or outside the firewall, it will also need to be able to resolve this name, (I put them in the ‘hosts‘ file on my DMZ servers for this reason).
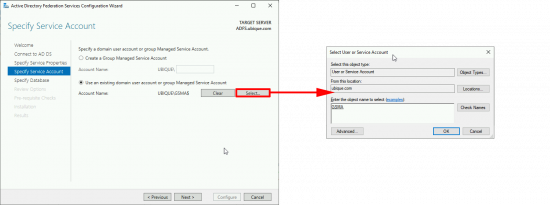
Enter your Group Managed Service Account, (created above) > Next.
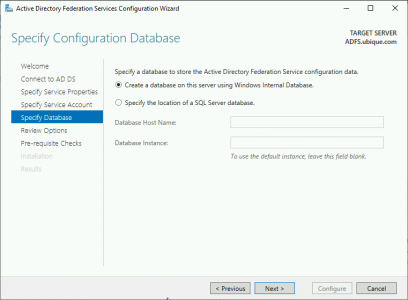
Create a database. (Note; If you are reinstalling it will discover any existing databases, and ask if you want to overwrite them) > Next.
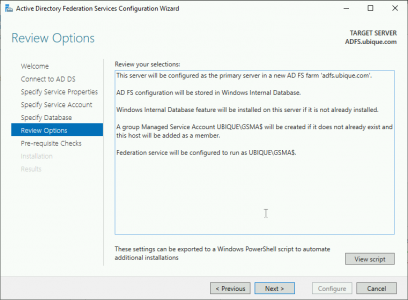
Next
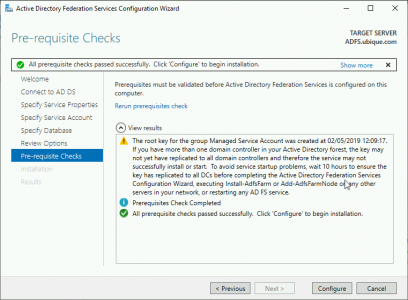
Configure.
Close. (Note: I’ve got some warnings but all is well, trust me!)
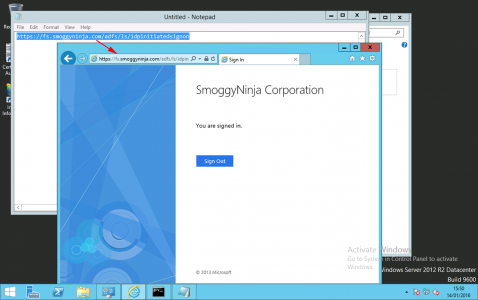
To test, open a web browser and go to https://{FQDN-Of FS-Service}/adfs/ls/idpinitiatedsignon and log in.
Note: If using Server 2016 or Server 2019, you have to enable this, or it will error! See the link below.
At this point, how you proceed depends on what you are using Active Directory Federation Services for. You would set up either a relying or a claims provider trust next.
As said above I’m using this for Web Application Proxy. When that article is complete, I’ll put the link at the bottom of this article.
Related Articles, References, Credits, or External Links
Publishing Remote Desktop Services With Web Application Gateway



27/11/2019
Hello,
i tried to install ADFS on server 2019 but i get error
“WARNING: The SSL certificate subject alternative names do not support host name ‘certauth.adfs.contoso.com’. Configuring certificate authentication binding on port ‘49443’ and hostname ‘adfs.contoso.com’.”
i am using a wildcard certificate and i used it on ADFS 3 with not a problem
29/11/2019
Add certauth.adfs.contoso.com as a SAN entry on the certificate, wildcards don’t cover sub domains.