KB ID 0001137
Problem
I’ve followed your Reverse Route Injection article and its not working? This email dropped in my mailbox a while back As it turns out the article I had written was for OSPF, and this chap was using EIGRP. So I ran it up with EIGRP as well to test.
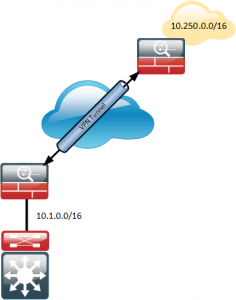
Heres my topology, I want to inject the route for the remote site, into my internal EIGRP routing table.
Solution
Assuming EIGRP is already setup between the ASA and the LAN (i.e. Core Switch).
ASA Petes-ASA# show run router ! router eigrp 20 no auto-summary network 10.1.0.0 255.255.0.0 passive-interface default no passive-interface inside redistribute static ! Switch Core-SW#show run | sec router router eigrp 20 network 10.1.0.0 0.0.255.255 network 10.2.0.0 0.0.255.255 network 10.3.0.0 0.0.255.255 no auto-summary
Also assuming you already have a site to site VPN established and working.
Petes-ASA# show cry isakmp IKEv1 SAs: Active SA: 1 Rekey SA: 0 (A tunnel will report 1 Active and 1 Rekey SA during rekey) Total IKE SA: 1 1 IKE Peer: 192.168.249.254 Type : L2L Role : responder Rekey : no State : MM_ACTIVE Petes-ASA# show cry ipsec sa interface: outside Crypto map tag: CRYPTO-MAP, seq num: 1, local addr: 192.168.253.254 access-list VPN-INTERESTING-TRAFIC extended permit ip 10.1.0.0 255.255.0.0 10.250.0.0 255.255.0.0 local ident (addr/mask/prot/port): (10.1.0.0/255.255.0.0/0/0) remote ident (addr/mask/prot/port): (10.250.0.0/255.255.0.0/0/0) current_peer: 192.168.249.254 #pkts encaps: 4, #pkts encrypt: 4, #pkts digest: 4 #pkts decaps: 4, #pkts decrypt: 4, #pkts verify: 4
Show the Cryptomap, then add the RRI.
Petes-ASA# show run crypto crypto ipsec ikev1 transform-set VPN-TRANSFORM esp-aes-256 esp-sha-hmac crypto map CRYPTO-MAP 1 match address VPN-INTERESTING-TRAFIC crypto map CRYPTO-MAP 1 set pfs crypto map CRYPTO-MAP 1 set peer 192.168.249.254 crypto map CRYPTO-MAP 1 set ikev1 transform-set VPN-TRANSFORM crypto map CRYPTO-MAP interface outside crypto ikev1 enable outside crypto ikev1 policy 10 authentication pre-share encryption aes-256 hash sha group 2 lifetime 86400 Petes-ASA# configure terminal Petes-ASA(config)# crypto map CRYPTO-MAP 1 set reverse-route Petes-ASA(config)#
Create a ‘Prefix-List’ for the routes to inject (i.e the remote LAN at the other end of the VPN tunnel).
Petes-ASA(config)# prefix-list PL-VPN-ROUTES description Route-Map For Injecting Remote VPN Routes Petes-ASA(config)# prefix-list PL-VPN-ROUTES seq 5 permit 10.250.0.0/16
Create a ‘route-map’ to inject your prefix-list.
Petes-ASA(config)# route-map RM-VPN-ROUTES permit 10 Petes-ASA(config-route-map)# match ip address prefix-list PL-VPN-ROUTE Petes-ASA(config-route-map)# set metric 1200 Petes-ASA(config-route-map)# exit Petes-ASA(config)# route-map RM-VPN-ROUTES deny 100
With the tunnel up check your internal routing table;
Update: As pointed out by SteveH
You’ve missed the route-map off the re-distribute command,
router eigrp 20
redistribute static route-map RM-VPN-ROUTES
Core-SW#show ip route
Codes: C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route
Gateway of last resort is 10.1.1.1 to network 0.0.0.0
10.0.0.0/16 is subnetted, 4 subnets
C 10.2.0.0 is directly connected, GigabitEthernet2/0
C 10.3.0.0 is directly connected, GigabitEthernet3/0
C 10.1.0.0 is directly connected, GigabitEthernet1/0
D EX 10.250.0.0 [170/28416] via 10.1.1.1, 00:00:02, GigabitEthernet1/0
D*EX 0.0.0.0/0 [170/28416] via 10.1.1.1, 00:00:02, GigabitEthernet1/0
Related Articles, References, Credits, or External Links
Cisco ASA – Reverse Route Injection with OSPF

15/02/2016
I have two independent ASA’s, each with its own Internet connection, connected to a Catalyst 3750 which is the default gateway for the internal network. I have a remote ASA configured (crypto map with two peers, originate-only) to establish a site-to-site VPN to either ASA. Per your advice, I am using RRI over EIGRP to distribute my VPN nets internally and that appears to work great. What I’m missing is the default gateway (0.0.0.0/0). How can I also redistribute that? Should I add it to my existing Prefix List? Set up a separate Route Map? Skip EIGRP for that part and set static routes on the 3750? (I have one now, but obviously that doesn’t provide Internet failover.) For what it’s worth, the Internet connections on the ASA’s use PPPoE setroute so no static route defined by me, and the 3750 BASE image doesn’t support IP SLA. I thought about using a second static gateway with a higher metric, but I’m not sure if that is the best way to accomplish this.
15/02/2016
Hi,
Im assuming the default route on the 3750 is currently pointing to one of the ASA’s so you manually have to fail to over if you lose an ASA? If so simply put another default route with a higher metric to the other ASA?
Pete
15/02/2016
Thanks, you are correct. I was thinking about doing that, but concerned that failover wouldn’t occur without IP SLA tracking something beyond the device. If the ASA was available but the outside line down, wouldn’t the switch still attempt to send Internet traffic to it?
15/02/2016
I simply added 0.0.0.0/0 to my prefix list and it works! Thanks!
05/04/2016
You’ve missed the route-map off the re-distribute command,
router eigrp 20
redistribute static route-map RM-VPN-ROUTES
05/04/2016
Updated – Cheers M8y
P