KB ID 0000842
Problem
In the following procedure I’m using Window Server 2012, and Windows 8 Enterprise, I am NOT configuring for Windows 7 so I don’t need to worry about PKI and certificates. (Other than the one the direct access server uses for https identification).
I’m not adding in any Application or Infrastructure servers, this is just a basic run through on setting up Direct Access to get you up and running.
Solution
Step 1 Create Direct Access Group
You can of course accept the default of allowing access to the domain computers group, but I would like to tie things down a little further.
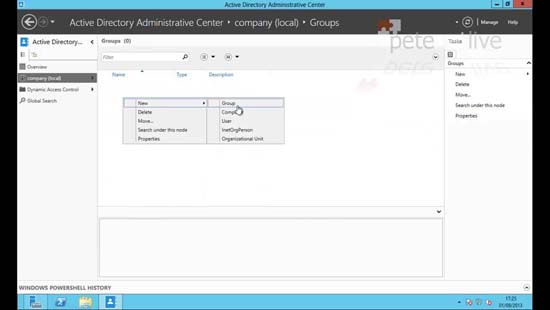
1. Server Manager> Tools > Active Directory Administrative Center > Select the OU (or create one) where you want to create the group.
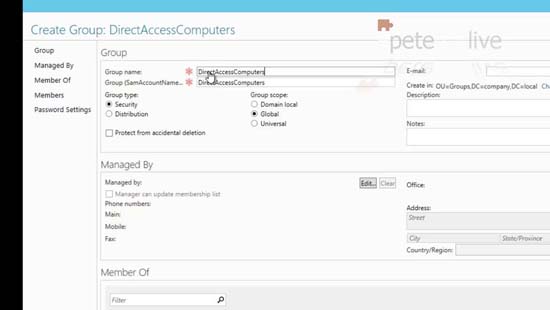
2.Give the group a sensible name like DirectAccessComputers.
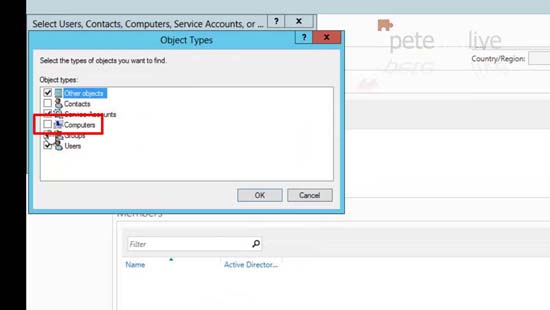
3. Remember when you try and ‘add’ members it will by default NOT have computers listed you will need to add them in.
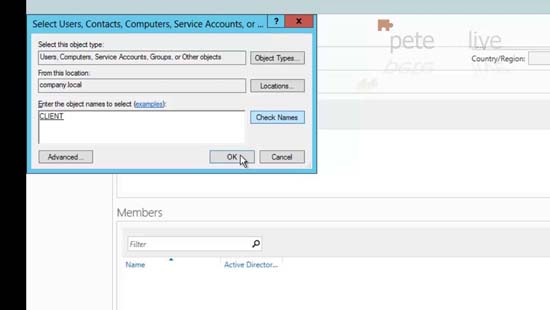
4. Add in your computer objects as required.
Step 2 Install Direct Access
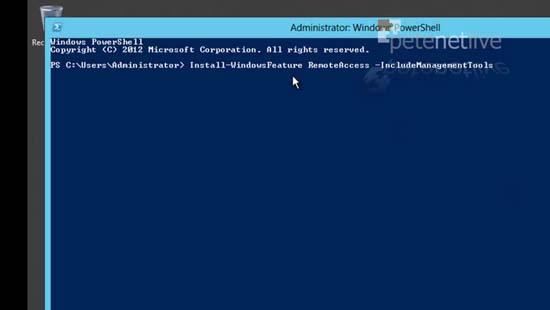
5. You can simply execute the following command;
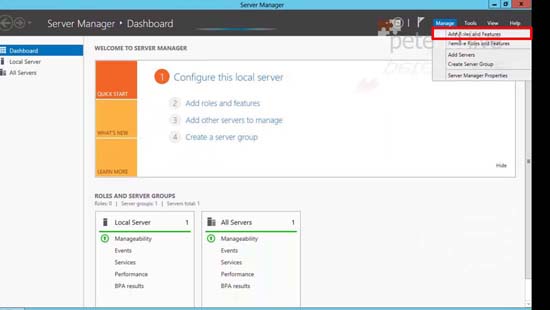
6. Or from Server Manager > Tools > Add Roles and Features.
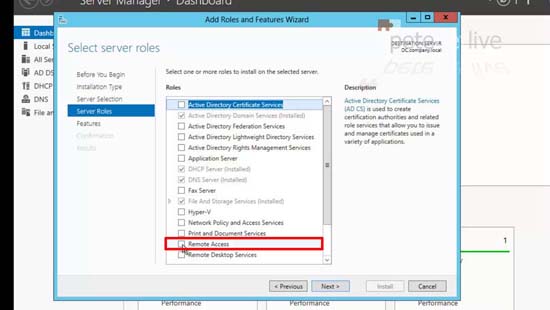
7. Simply add in ‘Remote Access’ and accept all the defaults.
Step 3 Configure Remote Access
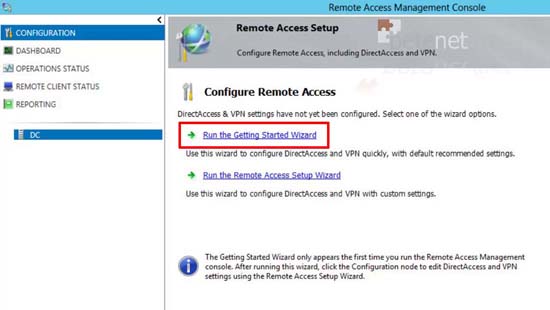
8. Once installed launch Remote Access Management.
9. Run the getting stated wizard.
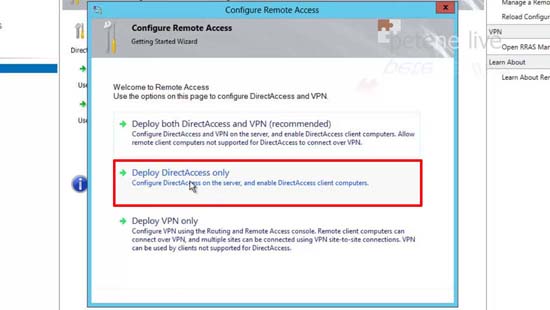
10. Deploy Remote Access Only (I’m not deploying VPNs).
11. Select how the server will be deployed, mine has a single NIC and I’m going to port forward TCP Port 443 (https) to it from the firewall. Enter its Publicly addressable name > Next > Finish.
Note: If you get an error see here.
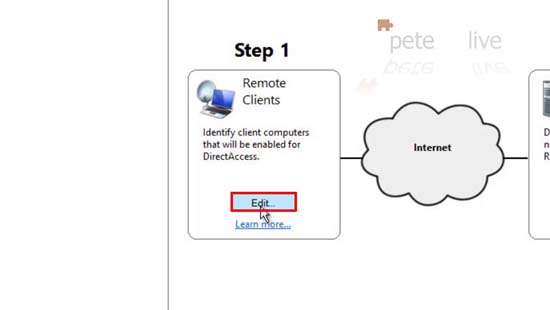
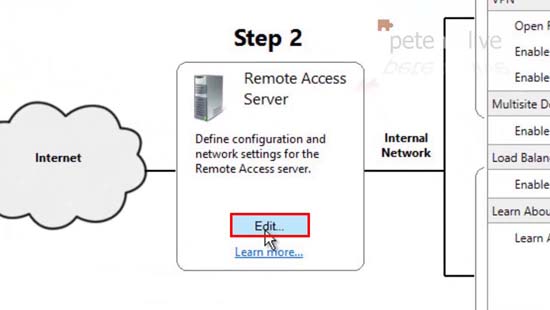
12. Configure Remote Clients > Edit.
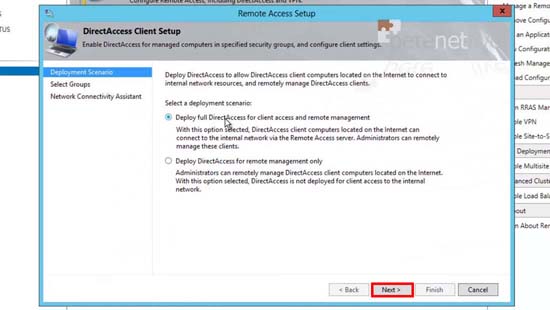
13. I want both options > Next
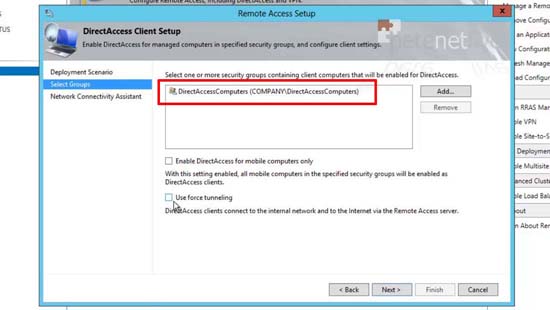
14. Remove the domain computers and add in the group we created above. Untick the ‘mobile only’ option.
Note: Force Tunnelling means that the remote clients will access the internet though YOUR corporate network. This is only a good idea if you have internet filtering, AV or NAP that you want to take advantage of. (It’s literally the exact opposite of split tunnelling).
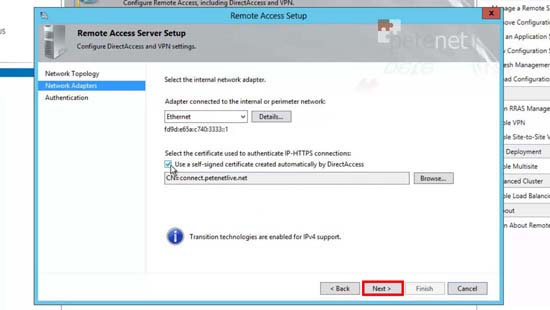
15. Remote Access Server > Edit.
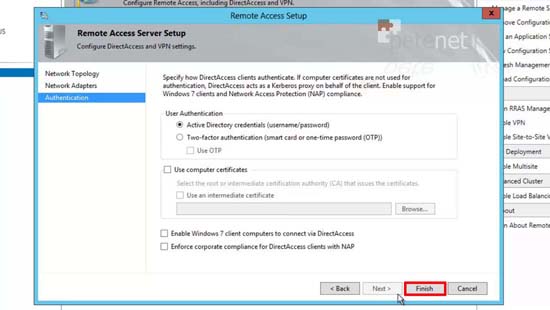
16. Select an existing Cert or create a new one > Next.
17. Remember I’m just using Windows 8, if you see the Windows 7 box and think “ooh I’ll tick that!” Then you need to start using certificates > Finish.
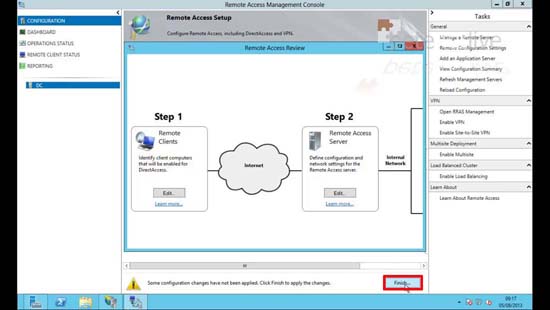
18. Finish.
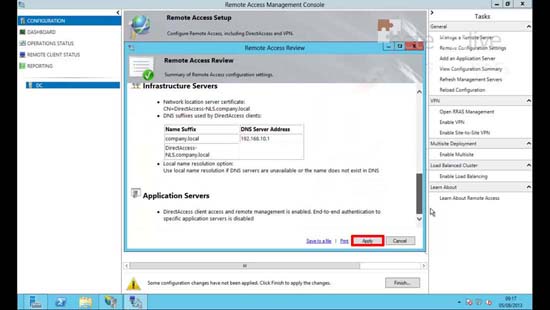
19. Review the settings > Apply.
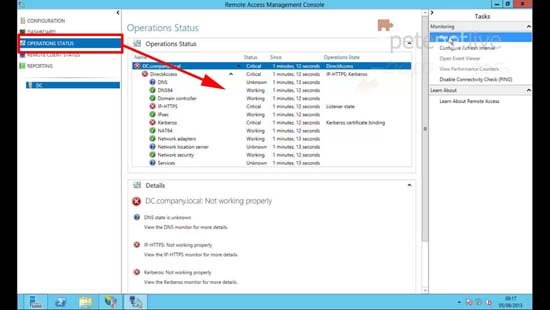
20. Operation Status.
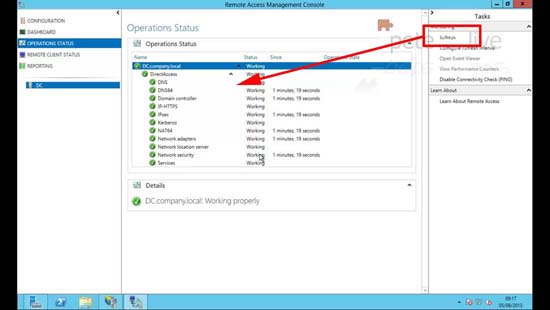
21. Press Refresh until all the services are green.
Step 4 Configure Clients
The title is a misnomer and to be honest there is no configuration to be done, but they have to get the settings through group policy, so log then onto the domain.
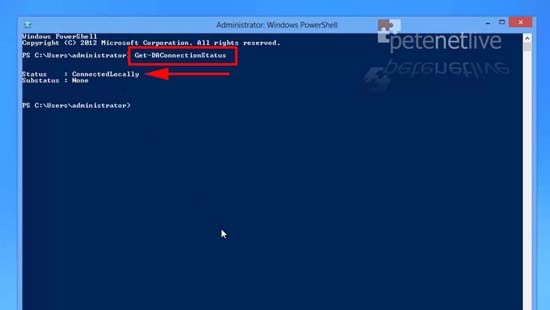
22. A quick simple check is to run the following command;
Note: If you get an error message make sure you are not using Windows 8 Pro see here.
23. The client knows it’s ‘inside’ the LAN, because it has a Name Resolution Policy Table and it can see your internal DNS, you can prove this with the following command;
Step 5 Test Clients Externally
Note: Before you proceed your Direct access server needs to be publicly available via the name you specified on the certificate in step 11, and needs to have https open to it.
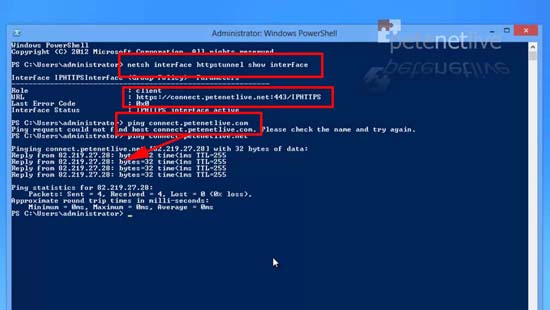
25. Whilst out on the internet you can test your remote client by first making sure it’s pointing to the correct place;
This should give the the URL that is on the certificate you specified in step 11, when you ping it by name you should expect a reply (unless ICMP has been blocked by your edge device).
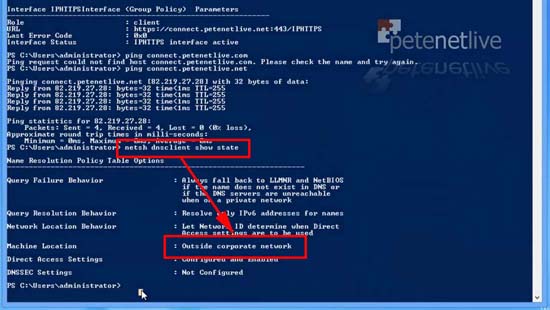
26. And to prove that the client knows it’s NOT on the corporate LAN execute the following;
27. So If i try to ping the internal FQDN of my Direct Access server it should respond (Note its IPv6 address will respond this is normal).
Note: Here I’ve only setup the one server, you can add more Infrastructure and Application servers in the Remote Access Management Console.
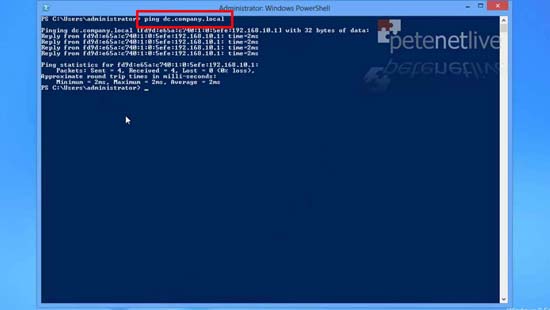
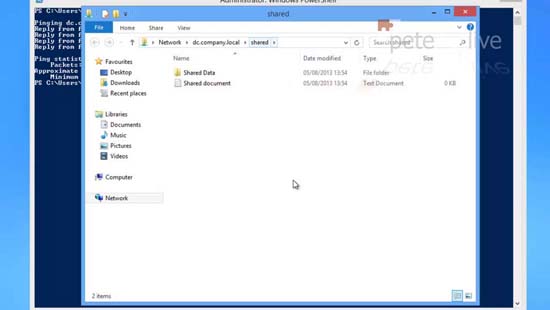
28. Because I can resolve that, I can access resources on that server like UNC paths.
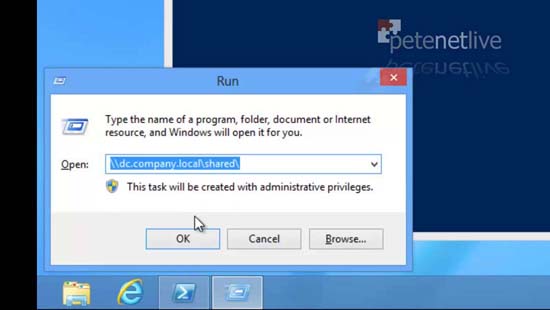
29. To access shared resources.
Step 6 Monitoring Remote Access Clients
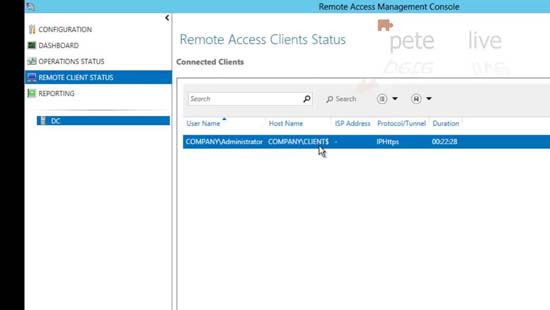
30. Back on the Direct Access server, you can see the remote clients under ‘Remote Client Status’.
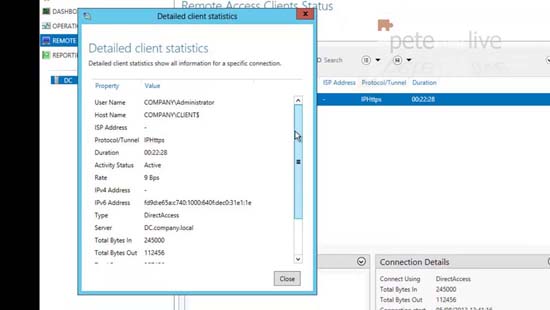
31. Right click each one for a more detailed view.
Related Articles, References, Credits, or External Links
NA