KB ID 0001742
Problem
I was back on the tools again today setting up FortiGate Port Forwarding! This was for one of our partners that I have to do some remote work for, so I temporarily needed to get onto their servers. Normally I’d just SSL VPN in, (but that’s what I’m setting up!) So to get onto their servers I had to setup a port forward for RDP.
WARNING: Port forwarding RDP from ALL / Any is a BAD IDEA (Cryptolocker anyone?) So if you must port forward RDP, then lock it down to a particular source IP like I’m about to do.
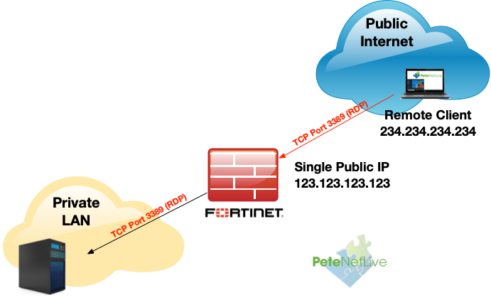
Fortigate Port Forwarding
The Process is;
- Setup a ‘Virtual IP’ (with port forward enabled)
- Create a ‘Virtual IP Group‘
- Allow traffic to the Virtual IP Group.
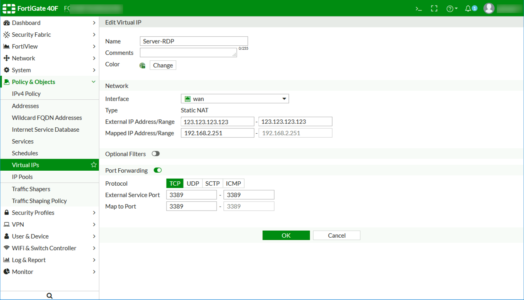
FortiGate Port Forwarding: Create a Virtual IP
Policy and Objects >Virtual IPs > Create New > Virtual IP.
Give it a sensible name > Set the interface to the outside/WAN interface > External IP set to the public IP address of the firewall* > Mapped IP address, set to the internal IP address of the server you are forwarding to > Enable ‘Port forwarding’ > Select TCP or UDP > Type in the port(s) you want to forward. Forwarding a range of ports is much easier on a FortiGate than ‘some other’ vendors! > OK.
*Note: I’m assuming if you are port forwarding you only have one public IP, (or you’ve ran out).
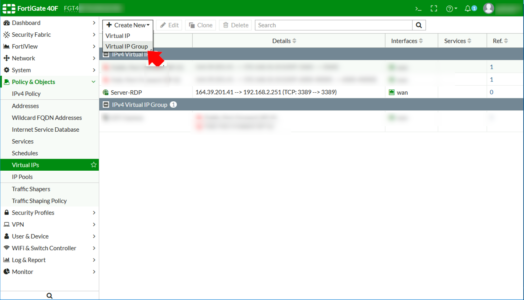
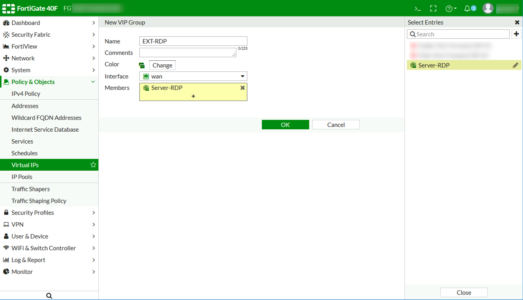
FortiGate Port Forwarding: Create a Virtual IP Group
From the Virtual IP menu > Create New > Virtual IP Group.
Give the group a name > Select the outside/WAN interface > Add in the Virtual IP you created above > OK.
FortiGate Port Forwarding: Fortigate Add an ‘Address’
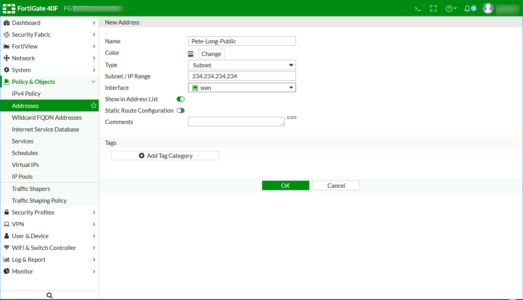
If you are port forwarding something like HTTP/HTTPS to a web server, or SMTP to a mail server you can skip this step. As per my warning above I’m restricting public access to one single public IP (mine). For most port forwarding scenarios you would set the source to ‘ALL‘.
Anyway for completeness here’s how to create an Address object. Policy & Objects > Addresses > Create New > Address.
Give it a recognisable name > Type=Subnet > Type the IP into the IP range box > Set the interface to outside/WAN > OK.
FortiGate Port Forwarding: Allow Port Forwarded Traffic
Policy and Objects > IPv4 Policy (or Firewall Policy on the newer firmware) > Create New.
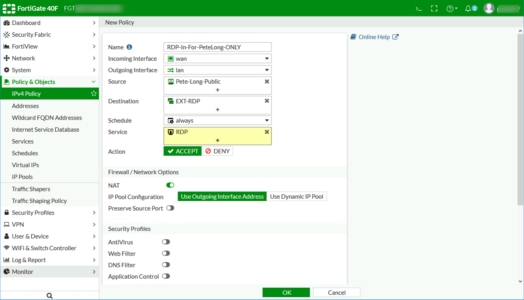
- Name: Something identifiable
- Incoming Interface: Outside / WAN
- Source: For RDP specify the single address you created above for all other port forwarding simply use ALL instead.
- Destination: Your Virtual IP Group
- Schedule: Always
- Service: RDP (or the port you are forwarding if different)
- Allow: Accept
Click OK.
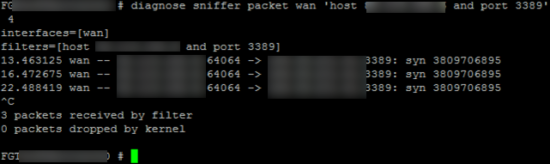
FortiGate Port Forwarding: Troubleshooting Port Forwarding
You can see what’s going on by using the packet sniffer in the firewall.
diagnose sniffer packet {interface} 'host {External IP} and port {Port Number}' 4
e.g.
diagnose sniffer packet wan 'host 234.234.234.234 and port 3389' 4
Note: In the example above I’m getting no return (ACK) traffic, (because the Windows firewall was on and dropping the traffic!) I diagnosed that by attempting to ping the server from the firewall (execute ping {internal IP address}) and failing to see a response!
Related Articles, References, Credits, or External Links
Fortigate: One to One (Static NAT)